解题过程
IDA打开,发现目标程序进行了混淆,进一步分析,可以知道使用了ollvm进行了混淆。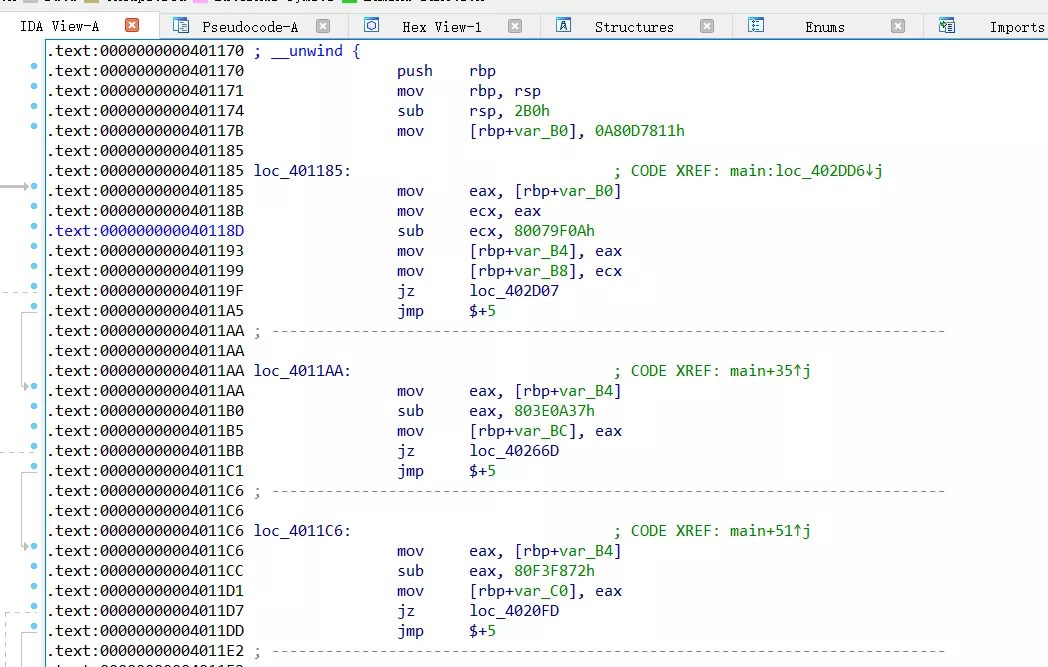
使用工具中的deflat.py脚本,去除混淆的代码。
python deflat.py shift_exercise 0x401170
去除之后,生成shift_exercise_recovered文件,IDA继续分析,仍然存在无用的控制流程。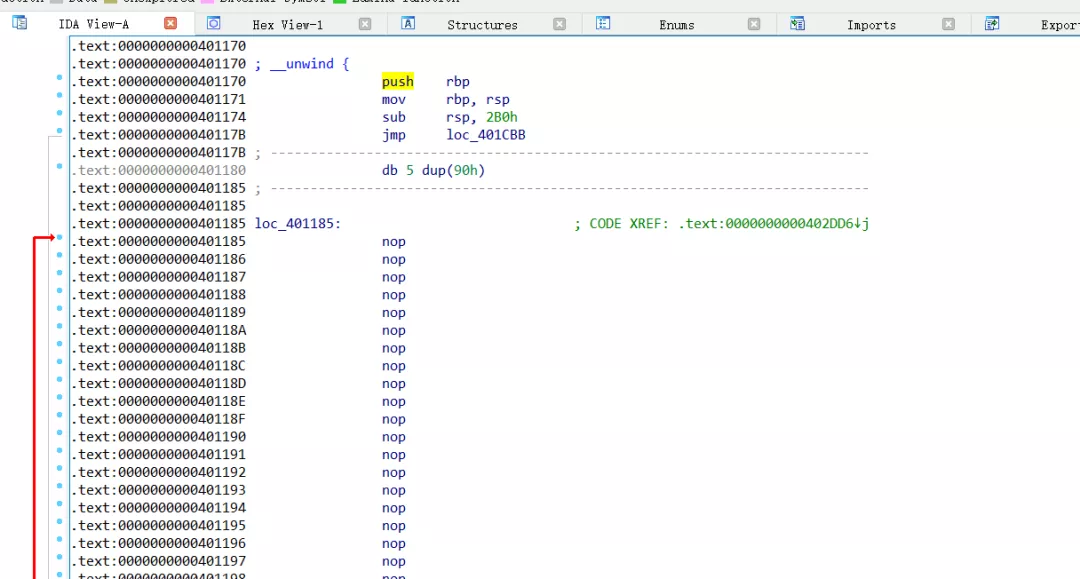
进一步使用IDA插件script.py进行处理,获得更为直观的伪代码。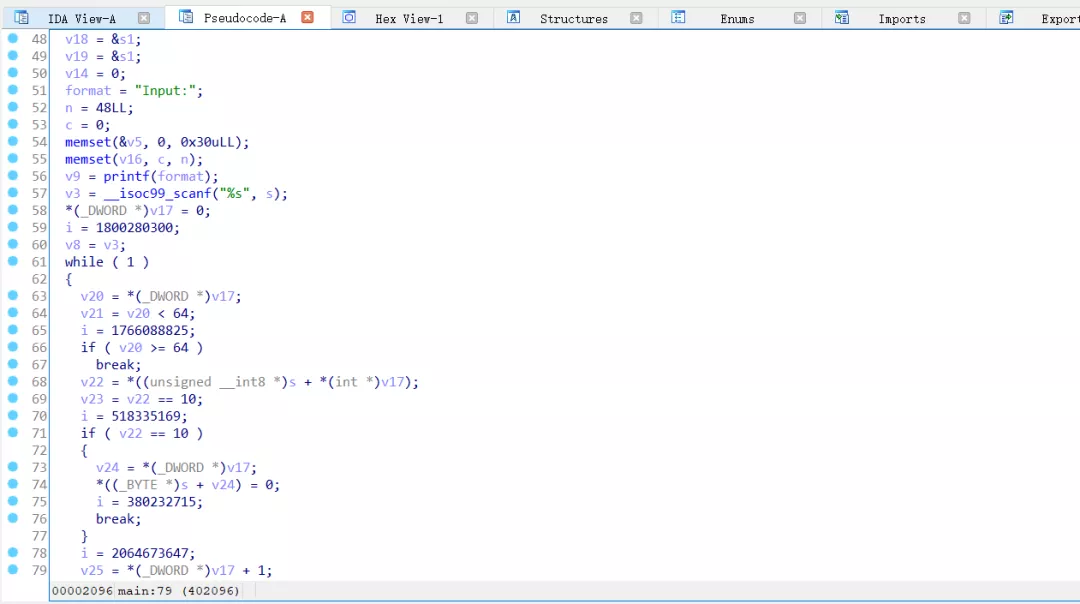
分析伪代码可以知道,该算法为修改过的crc64算法,依据加密算法,写出解密算法。
def multiply(multiplier_a, multiplier_b):tmp = [0] * 64res = 0for i in range(64):tmp[i] = (multiplier_a << i) * ((multiplier_b >> i) & 1)res ^= tmp[i]return resdef find_highest_bit(value):i = 0while value != 0:i += 1value >>= 1return idef divide(numerator, denominator):quotient = 0tmp = numeratorbit_count = find_highest_bit(tmp) - find_highest_bit(denominator)while bit_count >= 0:quotient |= (1<< bit_count)tmp ^= (denominator << bit_count)bit_count = find_highest_bit(tmp) - find_highest_bit(denominator)remainder = tmpreturn quotient, remainderdef reverse(x, bits):bin_x = bin(x)[2:].rjust(bits, '0')re_bin_x = bin_x[::-1]returnint(re_bin_x, 2)cipher = [0x32e9a65483cc9671, 0xec92a986a4af329c, 0x96c8259bc2ac4673,0x74bf5dca4423530f, 0x59d78ef8fdcbfab1, 0xa65257e5b13942b1]res = b""for a in cipher:d = 0xb1234b7679fc4b3drr = reverse(a, 64)rd = reverse((1<< 64) + d, 65)q, r = divide(rr << 64, rd)r = reverse(r, 64)for i in range(8):res += bytes([r & 0xff])r >>= 8print(res)print(res.decode())

