- Setting resource limits
- Sharing container memroy
- Setting users, permissions, and administrative privileges
- Granting access to specific Linux features
- Working with SELinux and AppArmor
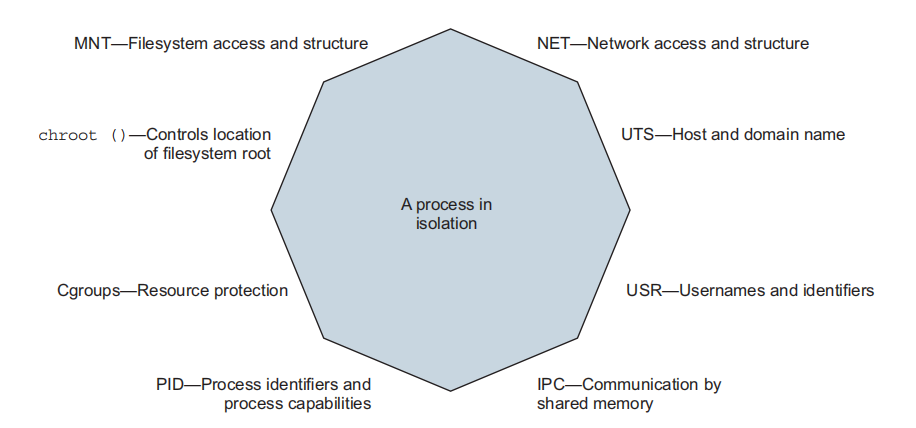
6.1 Setting resource allowance
6.1.1 Memory limits
docker container run -d --name ch6_mariadb \--memory 256m \--cpu-shares 1024 \--cap-drop net_raw \-e MYSQL_ROOT_PASSWORD=test \mariadb:5.5
6.1.2 CPU
docker container run -d -P --name ch6_wordpress \--memory 512m \# sets a relative process weight--cpu-shares 512 \--cap-drop net_raw \--link ch6_mariadb:mysql \-e WORDPRESS_DB_PASSWORD=test \wordpress:5.0.0-php7.2-apache
docker container run -d -P --name ch6_wordpress \--memory 512m--cpus 0.75 \--cap-drop net_raw \--link ch6_mariadb:mysql \-e WORDPRESS_DB_PASSWORD=test \wordpress:5.0.0-php7.2-apache
docker container run -d \--cpuset-cpus 0 \--name ch6_stresser dockerinaction/ch6_stresserdocker container run -it --rm dockerinaction/ch6_htop
6.1.3 Access to devices
docker container run -it --rm \--device /dev/video0:/dev/video0 \ubuntu:16.0.4 ls -al /dev
6.2 Sharing memory
6.2.1 Sharing IPC primitives between containers
docker container run -d -u nobody --name ch6_ipc_producer \--ipc shareable \dockerinaction/ch6_ipc -producerdocker container run -d -u nobody --name ch6_ipc_consumer \dockerinaction/ch6_ipc -consumer
docker container rm -v ch6_ipc_consumer docker container run -d --name ch6_ipc_consumer \ --ipc container:ch6_ipc_producer \ dockerinaction/ch6_ipc -consumer docker logs ch6_ipc_producerdocker logs ch6_ipc_consumer
6.3 Understanding users
6.3.1 Working with the run-as user
docker image pull busybox:1.29docker image inspect busybox:1.29docker inspect --format "{{.Config.User}}" busybox:1.29
6.3.2 Users and volumes
6.3.3 Introduction to the Linux user namespace and UID remapping
6.4 Adjusting OS feature access with capabilities
6.5 Running a container with full privileges
6.6 Strengthening containers with enhanced tools
6.6.1 Specifying additional security options
6.7 Building use-case-appropriate containers


