安装iptable
yum install iptables-services
[root@riyimei ~]# systemctl status iptables.serviceUnit iptables.service could not be found.[root@riyimei ~]# cd /etc/sysconfig[root@riyimei sysconfig]#[root@riyimei sysconfig]# ls -ltotal 84-rw-r--r--. 1 root root 436 Jan 11 13:44 anaconda-rw-r--r--. 1 root root 483 Jan 11 13:44 authconfigdrwxr-xr-x. 2 root root 43 Jan 11 13:41 cbqdrwxr-xr-x. 2 root root 6 Aug 9 2019 console-rw-r--r--. 1 root root 150 Aug 8 2019 cpupower-rw-------. 1 root root 110 Aug 9 2019 crond-rw-------. 1 root root 1390 Apr 11 2018 ebtables-config-rw-r--r--. 1 root root 73 Aug 9 2019 firewalldlrwxrwxrwx. 1 root root 15 Jan 11 13:42 grub -> ../default/grub-rw-r--r--. 1 root root 798 Aug 9 2019 init-rw------- 1 root root 2134 Apr 2 23:57 ip6tables-config-rw------- 1 root root 2116 Apr 2 23:57 iptables-config-rw-r--r--. 1 root root 903 Aug 6 2019 irqbalance-rw-r--r--. 1 root root 1733 Aug 8 2019 kdump-rw-r--r--. 1 root root 180 Jan 11 13:44 kernel-rw-r--r--. 1 root root 200 Oct 30 2018 man-dbdrwxr-xr-x. 2 root root 6 Aug 9 2019 modules-rw-r--r--. 1 root root 634 Aug 9 2019 netconsole-rw-r--r--. 1 root root 22 Jan 11 13:44 networkdrwxr-xr-x. 2 root root 4096 Jun 25 09:52 network-scripts-rw-r--r--. 1 root root 15 Aug 4 2017 rdisc-rw-r--r--. 1 root root 905 Aug 9 2019 readonly-root-rw-r--r--. 1 root root 196 Aug 6 2019 rsyslog-rw-r--r--. 1 root root 0 Jun 10 2014 run-partslrwxrwxrwx. 1 root root 17 Jan 11 13:42 selinux -> ../selinux/config-rw-r-----. 1 root root 506 Aug 9 2019 sshd-rw-r--r--. 1 root root 610 Oct 31 2018 wpa_supplicant[root@riyimei sysconfig]#[root@riyimei sysconfig]#[root@riyimei sysconfig]#[root@riyimei sysconfig]# yum install iptables-servicesLoaded plugins: fastestmirrorLoading mirror speeds from cached hostfile* base: mirrors.aliyun.com* extras: mirrors.aliyun.com* updates: mirrors.aliyun.comResolving Dependencies--> Running transaction check---> Package iptables-services.x86_64 0:1.4.21-34.el7 will be installed--> Finished Dependency ResolutionDependencies Resolved=======================================================================================================================================Package Arch Version Repository Size=======================================================================================================================================Installing:iptables-services x86_64 1.4.21-34.el7 base 52 kTransaction Summary=======================================================================================================================================Install 1 PackageTotal download size: 52 kInstalled size: 23 kIs this ok [y/d/N]: yDownloading packages:iptables-services-1.4.21-34.el7.x86_64.rpm | 52 kB 00:00:00Running transaction checkRunning transaction testTransaction test succeededRunning transactionInstalling : iptables-services-1.4.21-34.el7.x86_64 1/1Verifying : iptables-services-1.4.21-34.el7.x86_64 1/1Installed:iptables-services.x86_64 0:1.4.21-34.el7Complete![root@riyimei sysconfig]# ls -ltotal 92-rw-r--r--. 1 root root 436 Jan 11 13:44 anaconda-rw-r--r--. 1 root root 483 Jan 11 13:44 authconfigdrwxr-xr-x. 2 root root 43 Jan 11 13:41 cbqdrwxr-xr-x. 2 root root 6 Aug 9 2019 console-rw-r--r--. 1 root root 150 Aug 8 2019 cpupower-rw-------. 1 root root 110 Aug 9 2019 crond-rw-------. 1 root root 1390 Apr 11 2018 ebtables-config-rw-r--r--. 1 root root 73 Aug 9 2019 firewalldlrwxrwxrwx. 1 root root 15 Jan 11 13:42 grub -> ../default/grub-rw-r--r--. 1 root root 798 Aug 9 2019 init-rw------- 1 root root 635 Apr 2 23:57 ip6tables-rw------- 1 root root 2134 Apr 2 23:57 ip6tables-config-rw------- 1 root root 550 Apr 2 23:57 iptables-rw------- 1 root root 2116 Apr 2 23:57 iptables-config-rw-r--r--. 1 root root 903 Aug 6 2019 irqbalance-rw-r--r--. 1 root root 1733 Aug 8 2019 kdump-rw-r--r--. 1 root root 180 Jan 11 13:44 kernel-rw-r--r--. 1 root root 200 Oct 30 2018 man-dbdrwxr-xr-x. 2 root root 6 Aug 9 2019 modules-rw-r--r--. 1 root root 634 Aug 9 2019 netconsole-rw-r--r--. 1 root root 22 Jan 11 13:44 networkdrwxr-xr-x. 2 root root 4096 Jun 25 09:52 network-scripts-rw-r--r--. 1 root root 15 Aug 4 2017 rdisc-rw-r--r--. 1 root root 905 Aug 9 2019 readonly-root-rw-r--r--. 1 root root 196 Aug 6 2019 rsyslog-rw-r--r--. 1 root root 0 Jun 10 2014 run-partslrwxrwxrwx. 1 root root 17 Jan 11 13:42 selinux -> ../selinux/config-rw-r-----. 1 root root 506 Aug 9 2019 sshd-rw-r--r--. 1 root root 610 Oct 31 2018 wpa_supplicant[root@riyimei sysconfig]#
root@riyimei sysconfig]# systemctl restart iptables.service[root@riyimei sysconfig]# systemctl status iptables.service● iptables.service - IPv4 firewall with iptablesLoaded: loaded (/usr/lib/systemd/system/iptables.service; disabled; vendor preset: disabled)Active: active (exited) since Sat 2020-07-04 23:09:05 CST; 5s agoProcess: 5435 ExecStart=/usr/libexec/iptables/iptables.init start (code=exited, status=0/SUCCESS)Main PID: 5435 (code=exited, status=0/SUCCESS)Jul 04 23:09:05 riyimei systemd[1]: Starting IPv4 firewall with iptables...Jul 04 23:09:05 riyimei iptables.init[5435]: iptables: Applying firewall rules: [ OK ]Jul 04 23:09:05 riyimei systemd[1]: Started IPv4 firewall with iptables.[root@riyimei sysconfig]#
扩展
[root@riyimei ~]# ls /usr/lib64/xtables/libip6t_ah.so libip6t_SNPT.so libxt_addrtype.so libxt_dscp.so libxt_NFQUEUE.so libxt_statistic.solibip6t_DNAT.so libipt_ah.so libxt_AUDIT.so libxt_DSCP.so libxt_NOTRACK.so libxt_string.solibip6t_DNPT.so libipt_CLUSTERIP.so libxt_bpf.so libxt_ecn.so libxt_osf.so libxt_SYNPROXY.solibip6t_dst.so libipt_DNAT.so libxt_cgroup.so libxt_esp.so libxt_owner.so libxt_tcpmss.solibip6t_eui64.so libipt_ECN.so libxt_CHECKSUM.so libxt_hashlimit.so libxt_physdev.so libxt_TCPMSS.solibip6t_frag.so libipt_icmp.so libxt_CLASSIFY.so libxt_helper.so libxt_pkttype.so libxt_TCPOPTSTRIP.solibip6t_hbh.so libipt_LOG.so libxt_cluster.so libxt_HMARK.so libxt_policy.so libxt_tcp.solibip6t_hl.so libipt_MASQUERADE.so libxt_comment.so libxt_IDLETIMER.so libxt_quota.so libxt_TEE.solibip6t_HL.so libipt_MIRROR.so libxt_connbytes.so libxt_iprange.so libxt_rateest.so libxt_time.solibip6t_icmp6.so libipt_NETMAP.so libxt_connlabel.so libxt_ipvs.so libxt_RATEEST.so libxt_tos.solibip6t_ipv6header.so libipt_realm.so libxt_connlimit.so libxt_LED.so libxt_recent.so libxt_TOS.solibip6t_LOG.so libipt_REDIRECT.so libxt_connmark.so libxt_length.so libxt_rpfilter.so libxt_TPROXY.solibip6t_MASQUERADE.so libipt_REJECT.so libxt_CONNMARK.so libxt_limit.so libxt_sctp.so libxt_TRACE.solibip6t_mh.so libipt_SAME.so libxt_CONNSECMARK.so libxt_mac.so libxt_SECMARK.so libxt_u32.solibip6t_NETMAP.so libipt_SNAT.so libxt_conntrack.so libxt_mark.so libxt_set.so libxt_udp.solibip6t_REDIRECT.so libipt_ttl.so libxt_cpu.so libxt_MARK.so libxt_SET.solibip6t_REJECT.so libipt_TTL.so libxt_CT.so libxt_multiport.so libxt_socket.solibip6t_rt.so libipt_ULOG.so libxt_dccp.so libxt_nfacct.so libxt_standard.solibip6t_SNAT.so libipt_unclean.so libxt_devgroup.so libxt_NFLOG.so libxt_state.so[root@riyimei ~]#
加载模块
modprobe ip_tablesmodprobe iptable_filtermodprobe iptable_natmodprobe ip_conntrackmodprobe ip_conntrack_ftpmodprobe ip_nat_ftpmodprobe ipt_state
[root@riyimei ~]# cat /etc/redhat-releaseCentOS Linux release 7.7.1908 (Core)[root@riyimei ~]# lsmod |grep iptableiptable_nat 12875 0nf_nat_ipv4 14115 1 iptable_natiptable_filter 12810 1ip_tables 27126 2 iptable_filter,iptable_nat[root@riyimei ~]# lsmod |grep natnf_nat_ftp 12809 0nf_conntrack_ftp 18478 1 nf_nat_ftpiptable_nat 12875 0nf_nat_ipv4 14115 1 iptable_natnf_nat 26583 2 nf_nat_ftp,nf_nat_ipv4nf_conntrack 139224 7 nf_nat_ftp,nf_nat,xt_state,nf_nat_ipv4,xt_conntrack,nf_conntrack_ftp,nf_conntrack_ipv4ip_tables 27126 2 iptable_filter,iptable_natlibcrc32c 12644 3 xfs,nf_nat,nf_conntrack[root@riyimei ~]#
iptable 帮助
[root@riyimei ~]# iptables -hiptables v1.4.21Usage: iptables -[ACD] chain rule-specification [options]iptables -I chain [rulenum] rule-specification [options]iptables -R chain rulenum rule-specification [options]iptables -D chain rulenum [options]iptables -[LS] [chain [rulenum]] [options]iptables -[FZ] [chain] [options]iptables -[NX] chainiptables -E old-chain-name new-chain-nameiptables -P chain target [options]iptables -h (print this help information)Commands:Either long or short options are allowed.--append -A chain Append to chain--check -C chain Check for the existence of a rule--delete -D chain Delete matching rule from chain--delete -D chain rulenumDelete rule rulenum (1 = first) from chain--insert -I chain [rulenum]Insert in chain as rulenum (default 1=first)--replace -R chain rulenumReplace rule rulenum (1 = first) in chain--list -L [chain [rulenum]]List the rules in a chain or all chains--list-rules -S [chain [rulenum]]Print the rules in a chain or all chains--flush -F [chain] Delete all rules in chain or all chains--zero -Z [chain [rulenum]]Zero counters in chain or all chains--new -N chain Create a new user-defined chain--delete-chain-X [chain] Delete a user-defined chain--policy -P chain targetChange policy on chain to target--rename-chain-E old-chain new-chainChange chain name, (moving any references)Options:--ipv4 -4 Nothing (line is ignored by ip6tables-restore)--ipv6 -6 Error (line is ignored by iptables-restore)[!] --protocol -p proto protocol: by number or name, eg. `tcp'[!] --source -s address[/mask][...]source specification[!] --destination -d address[/mask][...]destination specification[!] --in-interface -i input name[+]network interface name ([+] for wildcard)--jump -j targettarget for rule (may load target extension)--goto -g chainjump to chain with no return--match -m matchextended match (may load extension)--numeric -n numeric output of addresses and ports[!] --out-interface -o output name[+]network interface name ([+] for wildcard)--table -t table table to manipulate (default: `filter')--verbose -v verbose mode--wait -w [seconds] maximum wait to acquire xtables lock before give up--wait-interval -W [usecs] wait time to try to acquire xtables lockdefault is 1 second--line-numbers print line numbers when listing--exact -x expand numbers (display exact values)[!] --fragment -f match second or further fragments only--modprobe=<command> try to insert modules using this command--set-counters PKTS BYTES set the counter during insert/append[!] --version -V print package version.[root@riyimei ~]#
表
raw —>mangle—>nat—>filter
[root@riyimei ~]# iptables -t raw -LChain PREROUTING (policy ACCEPT)target prot opt source destinationChain OUTPUT (policy ACCEPT)target prot opt source destination[root@riyimei ~]# iptables -t mangle -LChain PREROUTING (policy ACCEPT)target prot opt source destinationChain INPUT (policy ACCEPT)target prot opt source destinationChain FORWARD (policy ACCEPT)target prot opt source destinationChain OUTPUT (policy ACCEPT)target prot opt source destinationChain POSTROUTING (policy ACCEPT)target prot opt source destination[root@riyimei ~]# iptables -t nat -LChain PREROUTING (policy ACCEPT)target prot opt source destinationChain INPUT (policy ACCEPT)target prot opt source destinationChain OUTPUT (policy ACCEPT)target prot opt source destinationChain POSTROUTING (policy ACCEPT)target prot opt source destination[root@riyimei ~]#
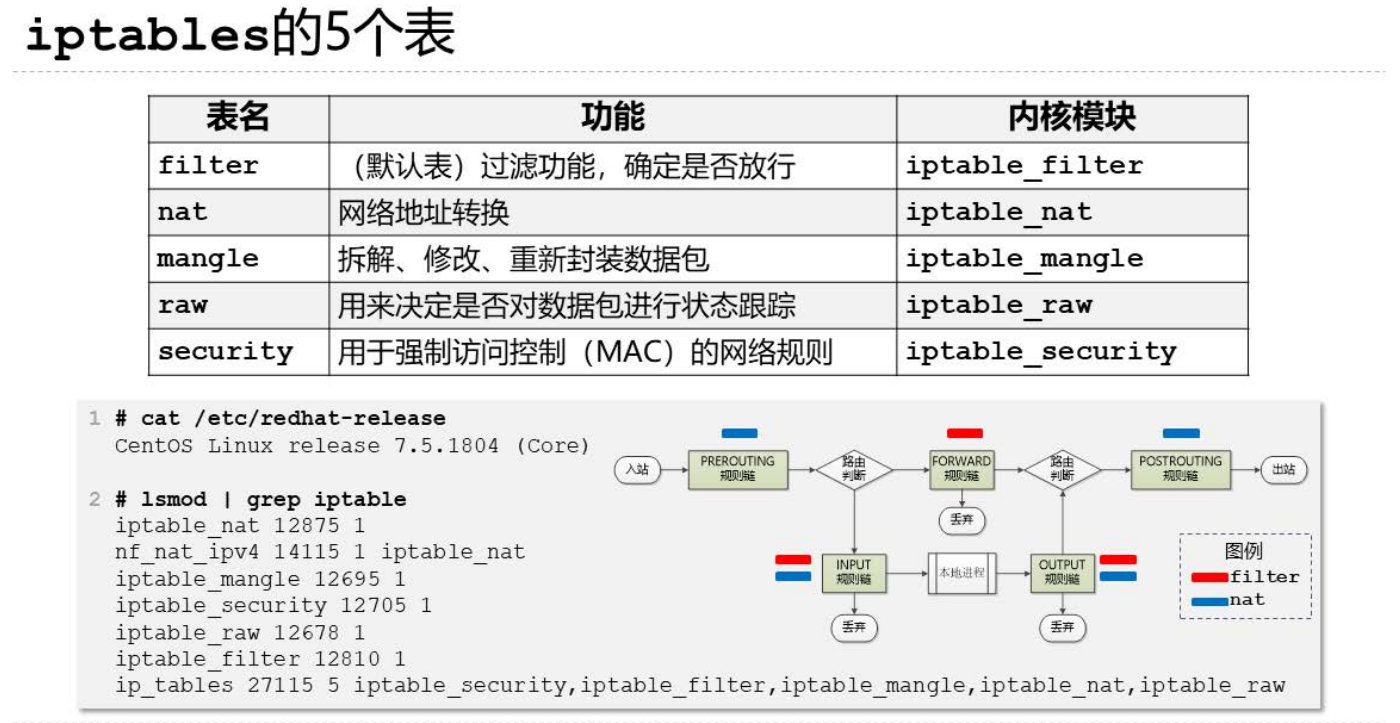
raw :主要做连接追踪
mangle:对数据包进行修改
nat:修改数据包的地址和端口
filter:实现对数据包的过滤
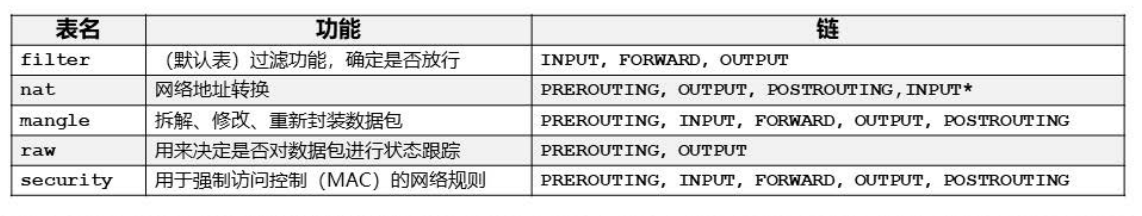
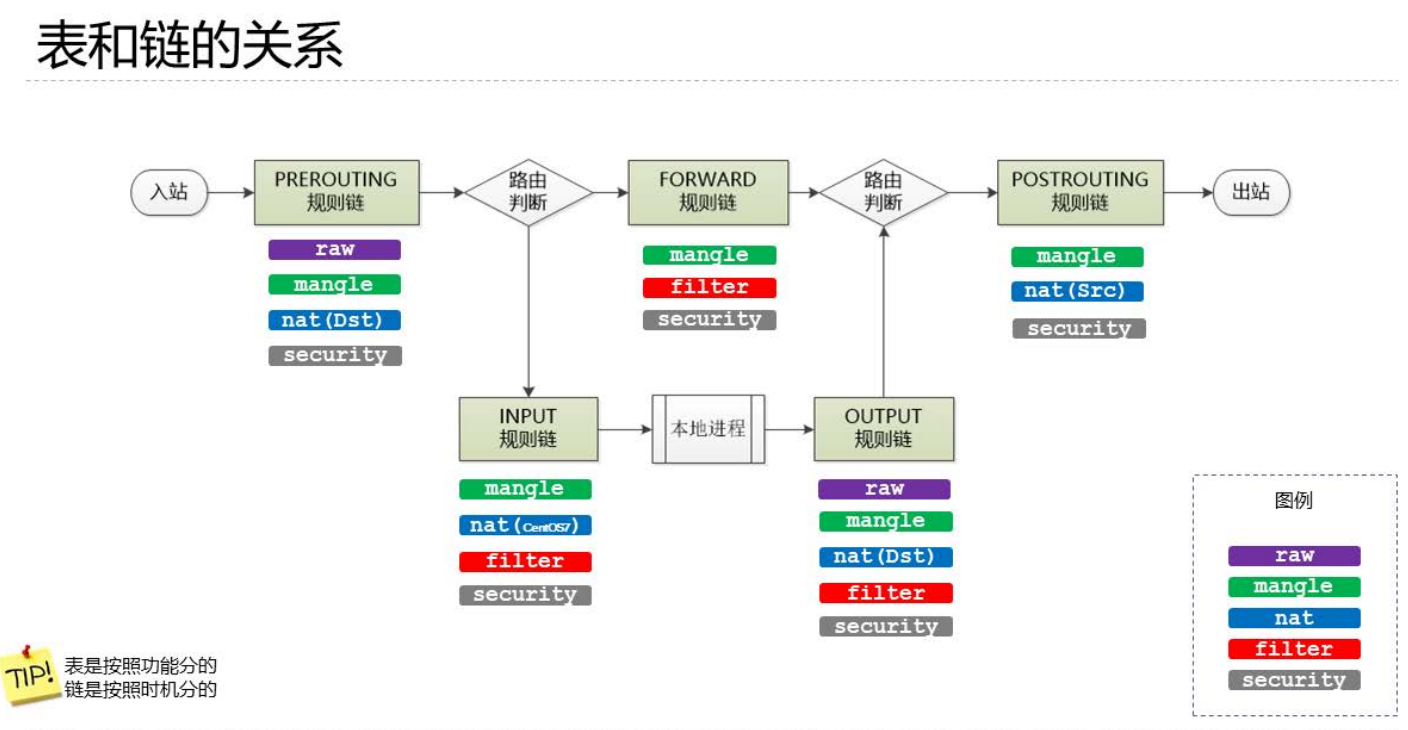
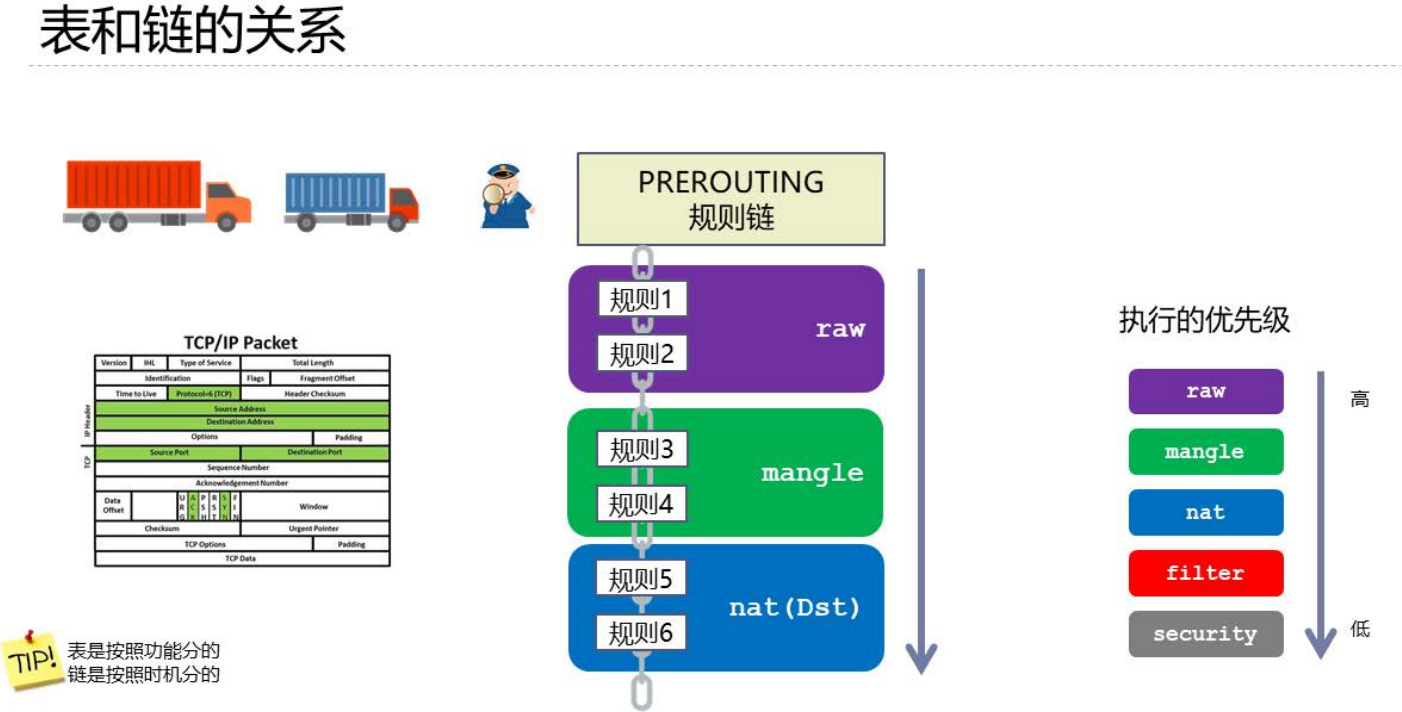
数据包流向
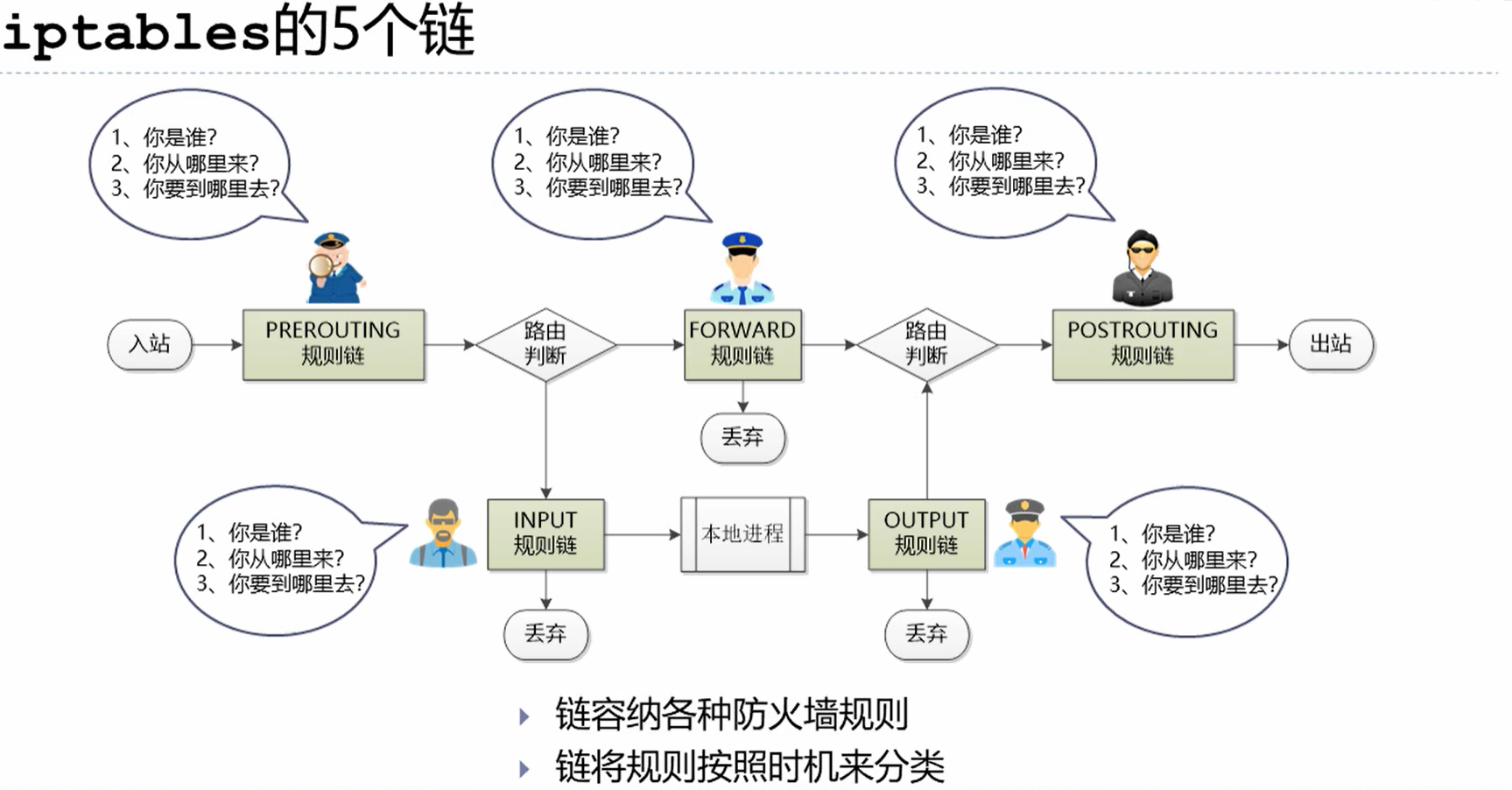
iptable语法

示例:

