升级 openssh 不影响加密算法
拒绝过程:
[boccfc@cl-prod-pats-bat-01 ~]$ sftp -oPort=2222 -vvv -oIdentityFile=id_ecdsa_pc_zhongyinxj_online -oKexAlgorithms=diffie-hellman-group18-sha512 pc_zhongyinxj@58.83.177.88OpenSSH_8.3p1, OpenSSL 1.1.1g 21 Apr 2020debug1: Reading configuration data /etc/ssh/ssh_configdebug1: /etc/ssh/ssh_config line 58: Applying options for *debug2: resolve_canonicalize: hostname 58.83.177.88 is addressdebug1: Authenticator provider $SSH_SK_PROVIDER did not resolve; disablingdebug2: ssh_connect_directdebug1: Connecting to 58.83.177.88 [58.83.177.88] port 2222.debug1: Connection established.debug1: identity file id_ecdsa_pc_zhongyinxj_online type -1debug1: identity file id_ecdsa_pc_zhongyinxj_online-cert type -1debug1: Local version string SSH-2.0-OpenSSH_8.3kex_exchange_identification: read: Connection reset by peerConnection reset by 58.83.177.88 port 2222Connection closed.Connection closed[boccfc@cl-prod-pats-bat-01 ~]$
通过过程:
[boccfc@ftp-ap01 ~]$ sftp -oPort=2222 -v -oIdentityFile=/home/boccfc/app/id_ecdsa_pc_zhongyinxj_online pc_zhongyinxj@58.83.177.88OpenSSH_7.4p1, OpenSSL 1.0.1e-fips 11 Feb 2013debug1: Reading configuration data /etc/ssh/ssh_configdebug1: /etc/ssh/ssh_config line 58: Applying options for *debug1: Connecting to 58.83.177.88 [58.83.177.88] port 2222.debug1: Connection established.debug1: key_load_public: No such file or directorydebug1: identity file /home/boccfc/app/id_ecdsa_pc_zhongyinxj_online type -1debug1: key_load_public: No such file or directorydebug1: identity file /home/boccfc/app/id_ecdsa_pc_zhongyinxj_online-cert type -1debug1: Enabling compatibility mode for protocol 2.0debug1: Local version string SSH-2.0-OpenSSH_7.4debug1: Remote protocol version 2.0, remote software version OpenSSH_6.6.1debug1: match: OpenSSH_6.6.1 pat OpenSSH_6.6.1* compat 0x04000000debug1: Authenticating to 58.83.177.88:2222 as 'pc_zhongyinxj'debug1: SSH2_MSG_KEXINIT sentdebug1: SSH2_MSG_KEXINIT receiveddebug1: kex: algorithm: curve25519-sha256@libssh.orgdebug1: kex: host key algorithm: ssh-rsadebug1: kex: server->client cipher: chacha20-poly1305@openssh.com MAC: <implicit> compression: nonedebug1: kex: client->server cipher: chacha20-poly1305@openssh.com MAC: <implicit> compression: nonedebug1: kex: curve25519-sha256@libssh.org need=64 dh_need=64debug1: kex: curve25519-sha256@libssh.org need=64 dh_need=64debug1: expecting SSH2_MSG_KEX_ECDH_REPLYdebug1: Server host key: ssh-rsa SHA256:XiO4YlCW3+hGari2n4YiL35pHNAl4guUQ/gOCt/bPYQdebug1: Host '[58.83.177.88]:2222' is known and matches the RSA host key.debug1: Found key in /home/boccfc/.ssh/known_hosts:1debug1: rekey after 134217728 blocksdebug1: SSH2_MSG_NEWKEYS sentdebug1: expecting SSH2_MSG_NEWKEYSdebug1: SSH2_MSG_NEWKEYS receiveddebug1: rekey after 134217728 blocksdebug1: SSH2_MSG_SERVICE_ACCEPT receiveddebug1: Authentications that can continue: publickey,gssapi-keyex,gssapi-with-mic,passworddebug1: Next authentication method: gssapi-keyexdebug1: No valid Key exchange contextdebug1: Next authentication method: gssapi-with-micdebug1: Unspecified GSS failure. Minor code may provide more informationNo Kerberos credentials available (default cache: KEYRING:persistent:310)debug1: Unspecified GSS failure. Minor code may provide more informationNo Kerberos credentials available (default cache: KEYRING:persistent:310)debug1: Next authentication method: publickeydebug1: Trying private key: /home/boccfc/app/id_ecdsa_pc_zhongyinxj_onlinedebug1: Authentication succeeded (publickey).Authenticated to 58.83.177.88 ([58.83.177.88]:2222).debug1: channel 0: new [client-session]debug1: Requesting no-more-sessions@openssh.comdebug1: Entering interactive session.debug1: pledge: networkdebug1: Sending environment.debug1: Sending env LANG = en_US.UTF-8debug1: Sending subsystem: sftpConnected to 58.83.177.88.sftp> exitdebug1: client_input_channel_req: channel 0 rtype exit-status reply 0debug1: channel 0: free: client-session, nchannels 1debug1: fd 0 clearing O_NONBLOCKTransferred: sent 2264, received 2732 bytes, in 2.1 secondsBytes per second: sent 1088.2, received 1313.2debug1: Exit status 0[boccfc@ftp-ap01 ~]$
故障定位:
还没有进入key交换过程、判断到网络
然后定位为什么被拒绝
追查到对端 对端server端设置了白名单 放行的IP地址不对,通过子网掩码换算出来的地址
[chroot@uat-nfs-server ~]$ sftp -oPort=22222 liwm@10.182.210.155kex_exchange_identification: Connection closed by remote hostConnection closed by 10.182.210.155 port 22222Connection closed.Connection closed[chroot@uat-nfs-server ~]$
[chroot@uat-nfs-server ~]$ sftp -P 22222 test@10.182.210.155Unable to negotiate with 10.182.210.155 port 22222: no matching key exchange method found. Their offer: diffie-hellman-group1-sha1,diffie-hellman-group14-sha1Connection closed.Connection closed[chroot@uat-nfs-server ~]$
[chroot@uat-nfs-server ~]$ sftp -oIdentityFile=/root/test.pub -oPort=22222 test@10.182.210.155load pubkey "/root/test.pub": Permission deniedload pubkey "/root/test.pub": Permission deniedUnable to negotiate with 10.182.210.155 port 22222: no matching key exchange method found. Their offer: diffie-hellman-group1-sha1,diffie-hellman-group14-sha1Connection closed.Connection closed[chroot@uat-nfs-server ~]$
[chroot@uat-nfs-server ~]$ sftp -oIdentityFile=/home/chroot/test.pub -oPort=22222 test@10.182.210.155load pubkey "/home/chroot/test.pub": invalid formatUnable to negotiate with 10.182.210.155 port 22222: no matching key exchange method found. Their offer: diffie-hellman-group1-sha1,diffie-hellman-group14-sha1Connection closed.Connection closed[chroot@uat-nfs-server ~]$ ssh -Q kexdiffie-hellman-group1-sha1diffie-hellman-group14-sha1diffie-hellman-group14-sha256diffie-hellman-group16-sha512diffie-hellman-group18-sha512diffie-hellman-group-exchange-sha1diffie-hellman-group-exchange-sha256ecdh-sha2-nistp256ecdh-sha2-nistp384ecdh-sha2-nistp521curve25519-sha256curve25519-sha256@libssh.orgsntrup4591761x25519-sha512@tinyssh.org[chroot@uat-nfs-server ~]$[chroot@uat-nfs-server ~]$ sftp -v -oIdentityFile=/home/chroot/test.pub -oPort=22222 test@10.182.210.155OpenSSH_8.3p1, OpenSSL 1.1.1g 21 Apr 2020debug1: Reading configuration data /etc/ssh/ssh_configdebug1: /etc/ssh/ssh_config line 58: Applying options for *debug1: Authenticator provider $SSH_SK_PROVIDER did not resolve; disablingdebug1: Connecting to 10.182.210.155 [10.182.210.155] port 22222.debug1: Connection established.load pubkey "/home/chroot/test.pub": invalid formatdebug1: identity file /home/chroot/test.pub type -1debug1: identity file /home/chroot/test.pub-cert type -1debug1: Local version string SSH-2.0-OpenSSH_8.3debug1: Remote protocol version 2.0, remote software version Serv-U_15.1.2.189debug1: no match: Serv-U_15.1.2.189debug1: Authenticating to 10.182.210.155:22222 as 'test'debug1: SSH2_MSG_KEXINIT sentdebug1: SSH2_MSG_KEXINIT receiveddebug1: kex: algorithm: (no match)Unable to negotiate with 10.182.210.155 port 22222: no matching key exchange method found. Their offer: diffie-hellman-group1-sha1,diffie-hellman-group14-sha1Connection closed.Connection closed[chroot@uat-nfs-server ~]$
故障2
debug1: Sending subsystem: sftp Received message too long 1416128883
拒绝:
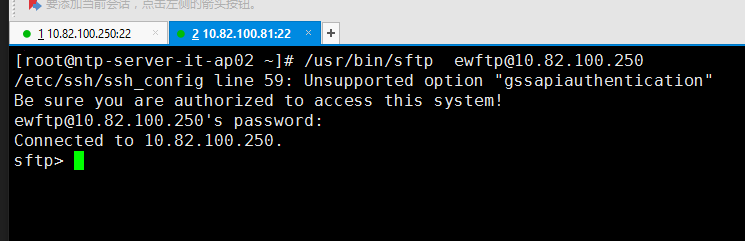
[chroot@ntp-server-it-ap02 ~]$ /usr/bin/sftp -v -oPort=22 -v ewftp@10.82.100.250OpenSSH_8.3p1, OpenSSL 1.1.1g 21 Apr 2020debug1: Reading configuration data /etc/ssh/ssh_configdebug1: /etc/ssh/ssh_config line 58: Applying options for */etc/ssh/ssh_config line 59: Unsupported option "gssapiauthentication"debug2: resolve_canonicalize: hostname 10.82.100.250 is addressdebug1: Authenticator provider $SSH_SK_PROVIDER did not resolve; disablingdebug2: ssh_connect_directdebug1: Connecting to 10.82.100.250 [10.82.100.250] port 22.debug1: Connection established.debug1: identity file /home/chroot/.ssh/id_rsa type 0debug1: identity file /home/chroot/.ssh/id_rsa-cert type -1debug1: identity file /home/chroot/.ssh/id_dsa type -1debug1: identity file /home/chroot/.ssh/id_dsa-cert type -1debug1: identity file /home/chroot/.ssh/id_ecdsa type -1debug1: identity file /home/chroot/.ssh/id_ecdsa-cert type -1debug1: identity file /home/chroot/.ssh/id_ecdsa_sk type -1debug1: identity file /home/chroot/.ssh/id_ecdsa_sk-cert type -1debug1: identity file /home/chroot/.ssh/id_ed25519 type -1debug1: identity file /home/chroot/.ssh/id_ed25519-cert type -1debug1: identity file /home/chroot/.ssh/id_ed25519_sk type -1debug1: identity file /home/chroot/.ssh/id_ed25519_sk-cert type -1debug1: identity file /home/chroot/.ssh/id_xmss type -1debug1: identity file /home/chroot/.ssh/id_xmss-cert type -1debug1: Local version string SSH-2.0-OpenSSH_8.3debug1: Remote protocol version 2.0, remote software version OpenSSH_8.3debug1: match: OpenSSH_8.3 pat OpenSSH* compat 0x04000000debug2: fd 3 setting O_NONBLOCKdebug1: Authenticating to 10.82.100.250:22 as 'ewftp'debug1: SSH2_MSG_KEXINIT sentdebug1: SSH2_MSG_KEXINIT receiveddebug2: local client KEXINIT proposaldebug2: KEX algorithms: curve25519-sha256,curve25519-sha256@libssh.org,ecdh-sha2-nistp256,ecdh-sha2-nistp384,ecdh-sha2-nistp521,diffie-hellman-group-exchange-sha256,diffie-hellman-group16-sha512,diffie-hellman-group18-sha512,diffie-hellman-group14-sha256,ext-info-cdebug2: host key algorithms: ecdsa-sha2-nistp256-cert-v01@openssh.com,ecdsa-sha2-nistp384-cert-v01@openssh.com,ecdsa-sha2-nistp521-cert-v01@openssh.com,ecdsa-sha2-nistp256,ecdsa-sha2-nistp384,ecdsa-sha2-nistp521,sk-ecdsa-sha2-nistp256-cert-v01@openssh.com,ssh-ed25519-cert-v01@openssh.com,sk-ssh-ed25519-cert-v01@openssh.com,rsa-sha2-512-cert-v01@openssh.com,rsa-sha2-256-cert-v01@openssh.com,ssh-rsa-cert-v01@openssh.com,sk-ecdsa-sha2-nistp256@openssh.com,ssh-ed25519,sk-ssh-ed25519@openssh.com,rsa-sha2-512,rsa-sha2-256,ssh-rsadebug2: ciphers ctos: chacha20-poly1305@openssh.com,aes128-ctr,aes192-ctr,aes256-ctr,aes128-gcm@openssh.com,aes256-gcm@openssh.comdebug2: ciphers stoc: chacha20-poly1305@openssh.com,aes128-ctr,aes192-ctr,aes256-ctr,aes128-gcm@openssh.com,aes256-gcm@openssh.comdebug2: MACs ctos: umac-64-etm@openssh.com,umac-128-etm@openssh.com,hmac-sha2-256-etm@openssh.com,hmac-sha2-512-etm@openssh.com,hmac-sha1-etm@openssh.com,umac-64@openssh.com,umac-128@openssh.com,hmac-sha2-256,hmac-sha2-512,hmac-sha1debug2: MACs stoc: umac-64-etm@openssh.com,umac-128-etm@openssh.com,hmac-sha2-256-etm@openssh.com,hmac-sha2-512-etm@openssh.com,hmac-sha1-etm@openssh.com,umac-64@openssh.com,umac-128@openssh.com,hmac-sha2-256,hmac-sha2-512,hmac-sha1debug2: compression ctos: none,zlib@openssh.com,zlibdebug2: compression stoc: none,zlib@openssh.com,zlibdebug2: languages ctos:debug2: languages stoc:debug2: first_kex_follows 0debug2: reserved 0debug2: peer server KEXINIT proposaldebug2: KEX algorithms: curve25519-sha256,curve25519-sha256@libssh.org,ecdh-sha2-nistp256,ecdh-sha2-nistp384,ecdh-sha2-nistp521,diffie-hellman-group-exchange-sha256,diffie-hellman-group16-sha512,diffie-hellman-group18-sha512,diffie-hellman-group14-sha256debug2: host key algorithms: rsa-sha2-512,rsa-sha2-256,ssh-rsa,ecdsa-sha2-nistp256,ssh-ed25519debug2: ciphers ctos: chacha20-poly1305@openssh.com,aes128-ctr,aes192-ctr,aes256-ctr,aes128-gcm@openssh.com,aes256-gcm@openssh.comdebug2: ciphers stoc: chacha20-poly1305@openssh.com,aes128-ctr,aes192-ctr,aes256-ctr,aes128-gcm@openssh.com,aes256-gcm@openssh.comdebug2: MACs ctos: umac-64-etm@openssh.com,umac-128-etm@openssh.com,hmac-sha2-256-etm@openssh.com,hmac-sha2-512-etm@openssh.com,hmac-sha1-etm@openssh.com,umac-64@openssh.com,umac-128@openssh.com,hmac-sha2-256,hmac-sha2-512,hmac-sha1debug2: MACs stoc: umac-64-etm@openssh.com,umac-128-etm@openssh.com,hmac-sha2-256-etm@openssh.com,hmac-sha2-512-etm@openssh.com,hmac-sha1-etm@openssh.com,umac-64@openssh.com,umac-128@openssh.com,hmac-sha2-256,hmac-sha2-512,hmac-sha1debug2: compression ctos: none,zlib@openssh.comdebug2: compression stoc: none,zlib@openssh.comdebug2: languages ctos:debug2: languages stoc:debug2: first_kex_follows 0debug2: reserved 0debug1: kex: algorithm: curve25519-sha256debug1: kex: host key algorithm: ecdsa-sha2-nistp256debug1: kex: server->client cipher: chacha20-poly1305@openssh.com MAC: <implicit> compression: nonedebug1: kex: client->server cipher: chacha20-poly1305@openssh.com MAC: <implicit> compression: nonedebug1: expecting SSH2_MSG_KEX_ECDH_REPLYdebug1: Server host key: ecdsa-sha2-nistp256 SHA256:vK5YbifEyx0aZhFqQU7qtFLFhc0Vz3HIM2aBEH2FoWodebug1: Host '10.82.100.250' is known and matches the ECDSA host key.debug1: Found key in /home/chroot/.ssh/known_hosts:8debug2: set_newkeys: mode 1debug1: rekey out after 134217728 blocksdebug1: SSH2_MSG_NEWKEYS sentdebug1: expecting SSH2_MSG_NEWKEYSdebug1: SSH2_MSG_NEWKEYS receiveddebug2: set_newkeys: mode 0debug1: rekey in after 134217728 blocksdebug1: Will attempt key: /home/chroot/.ssh/id_rsa RSA SHA256:nn24ysqxCkUv40izxDyijeF9+xhyDi81bf9mGVBEtoodebug1: Will attempt key: /home/chroot/.ssh/id_dsadebug1: Will attempt key: /home/chroot/.ssh/id_ecdsadebug1: Will attempt key: /home/chroot/.ssh/id_ecdsa_skdebug1: Will attempt key: /home/chroot/.ssh/id_ed25519debug1: Will attempt key: /home/chroot/.ssh/id_ed25519_skdebug1: Will attempt key: /home/chroot/.ssh/id_xmssdebug2: pubkey_prepare: donedebug1: SSH2_MSG_EXT_INFO receiveddebug1: kex_input_ext_info: server-sig-algs=<ssh-ed25519,sk-ssh-ed25519@openssh.com,ssh-rsa,rsa-sha2-256,rsa-sha2-512,ssh-dss,ecdsa-sha2-nistp256,ecdsa-sha2-nistp384,ecdsa-sha2-nistp521,sk-ecdsa-sha2-nistp256@openssh.com>debug2: service_accept: ssh-userauthdebug1: SSH2_MSG_SERVICE_ACCEPT receivedBe sure you are authorized to access this system!debug1: Authentications that can continue: publickey,passworddebug1: Next authentication method: publickeydebug1: Offering public key: /home/chroot/.ssh/id_rsa RSA SHA256:nn24ysqxCkUv40izxDyijeF9+xhyDi81bf9mGVBEtoodebug2: we sent a publickey packet, wait for replydebug1: Authentications that can continue: publickey,passworddebug1: Trying private key: /home/chroot/.ssh/id_dsadebug1: Trying private key: /home/chroot/.ssh/id_ecdsadebug1: Trying private key: /home/chroot/.ssh/id_ecdsa_skdebug1: Trying private key: /home/chroot/.ssh/id_ed25519debug1: Trying private key: /home/chroot/.ssh/id_ed25519_skdebug1: Trying private key: /home/chroot/.ssh/id_xmssdebug2: we did not send a packet, disable methoddebug1: Next authentication method: passwordewftp@10.82.100.250's password:debug2: we sent a password packet, wait for replydebug1: Authentication succeeded (password).Authenticated to 10.82.100.250 ([10.82.100.250]:22).debug2: fd 4 setting O_NONBLOCKdebug1: channel 0: new [client-session]debug2: channel 0: send opendebug1: Requesting no-more-sessions@openssh.comdebug1: Entering interactive session.debug1: pledge: networkdebug1: client_input_global_request: rtype hostkeys-00@openssh.com want_reply 0debug2: channel_input_open_confirmation: channel 0: callback startdebug2: fd 3 setting TCP_NODELAYdebug2: client_session2_setup: id 0debug1: Sending environment.debug1: Sending env LANG = en_US.UTF-8debug2: channel 0: request env confirm 0debug1: Sending subsystem: sftpdebug2: channel 0: request subsystem confirm 1debug2: channel_input_open_confirmation: channel 0: callback donedebug2: channel 0: open confirm rwindow 0 rmax 32768debug2: channel 0: rcvd adjust 2097152debug2: channel_input_status_confirm: type 99 id 0debug2: subsystem request accepted on channel 0Received message too long 1416128883Ensure the remote shell produces no output for non-interactive sessions.debug2: channel 0: read<=0 rfd 4 len -1debug2: channel 0: read faileddebug2: channel 0: chan_shutdown_read (i0 o0 sock -1 wfd 4 efd 6 [write])debug2: channel 0: input open -> draindebug2: channel 0: rcvd eofdebug2: channel 0: output open -> draindebug2: channel 0: obuf emptydebug2: channel 0: chan_shutdown_write (i1 o1 sock -1 wfd 5 efd 6 [write])debug2: channel 0: output drain -> closeddebug1: client_input_channel_req: channel 0 rtype exit-status reply 0debug1: client_input_channel_req: channel 0 rtype eow@openssh.com reply 0debug2: channel 0: rcvd eowdebug2: channel 0: rcvd closedebug2: channel 0: send eofdebug2: channel 0: input drain -> closeddebug2: channel 0: almost deaddebug2: channel 0: gc: notify userdebug2: channel 0: gc: user detacheddebug2: channel 0: send closedebug2: channel 0: is deaddebug2: channel 0: garbage collectingdebug1: channel 0: free: client-session, nchannels 1debug1: fd 0 clearing O_NONBLOCKTransferred: sent 2552, received 2452 bytes, in 0.1 secondsBytes per second: sent 49931.9, received 47975.3debug1: Exit status 1[chroot@ntp-server-it-ap02 ~]$
报错信息:
debug1: Sending subsystem: sftpReceived message too long 1416128883Ensure the remote shell produces no output for non-interactive sessions.
解决: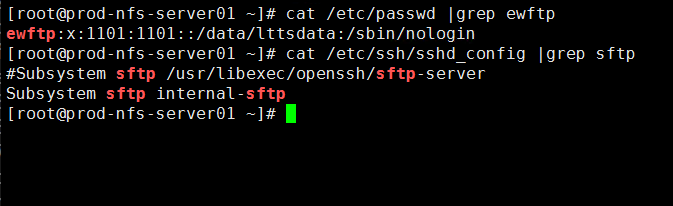
/sbin/nologin,所以导致你在进行SFTP的时候出现了这个问题
解决方案有以下两个:
(1)该用户需要修改用户权限,使用命令:usermod -s /bin/bash 用户名来放开限制,这样子你就可以成功登录了;
(2)如果他必须要限制你的访问权限,不允许你除了登录SFTP外的任何操作,那么他需要在/etc/ssh/sshd_config文件下修改一些信息
Subsystem sftp internal-sftp,通过内部登录SFTP
systemctl restart sshd.service来重启sshd服务