https://www.cnblogs.com/huahuot/p/14010374.html
https://www.cnblogs.com/wooya/p/9392142.html
ssh和sftp通过openssh服务ftp加密访问但却和sah服务共用一个端口,安全基线是不符合,特别是通过公网与其他公司文件交互时 ssh的端口就完全被暴露在公网上,就算使用 /etc/hosts.alow限制IP地址访问也会涉及暴露ssh端口的风险,因此需要把sftp从ssh服务里分离出来,只暴露sftp的端口和锁定家目录 这样基于白名单和密钥验证方式部署ftp服务器才能保证安全
1 注释ssh配置文件里的sftp子服务
2 添加sftp服务和配置文件
3 锁定sftp用户家目录
该方式适用于为编译升级过openssh 系统部署 CentOS 7
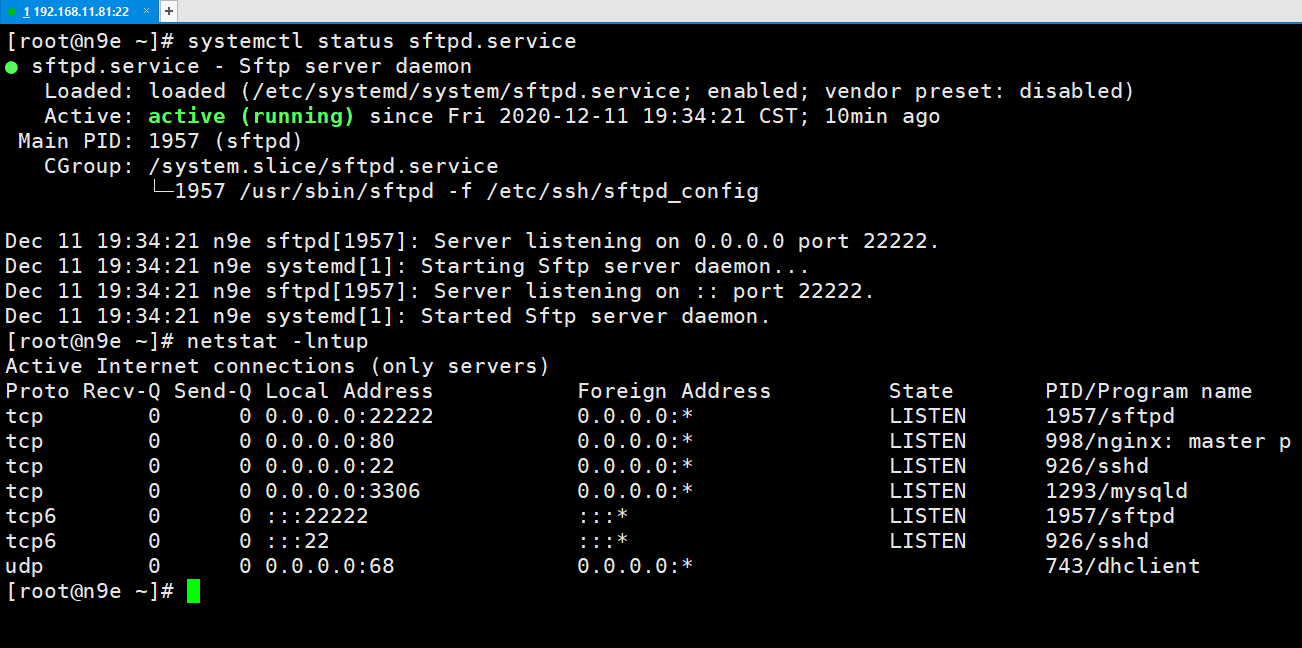
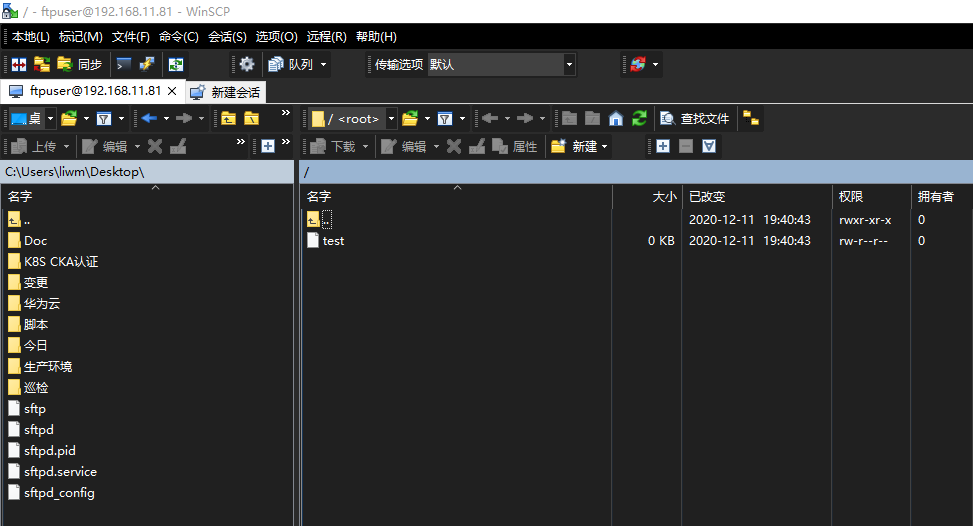
cp /usr/lib/systemd/system/sshd.service /etc/systemd/system/sftpd.servicecp /etc/pam.d/sshd /etc/pam.d/sftpdcp /etc/ssh/sshd_config /etc/ssh/sftpd_configln -sf /usr/sbin/service /usr/sbin/rcsftpdln -sf /usr/sbin/sshd /usr/sbin/sftpdcp /etc/sysconfig/sshd /etc/sysconfig/sftpcp /var/run/sshd.pid /var/run/sftpd.pidcat > /etc/systemd/system/sftpd.service<<EOF[Unit]Description=OpenSSH server daemon#Documentation=man:sshd(8) man:sshd_config(5)Description=Sftp server daemonAfter=network.target sshd-keygen.serviceWants=sshd-keygen.service[Service]Type=notify#EnvironmentFile=/etc/sysconfig/sshd#ExecStart=/usr/sbin/sshd -D $OPTIONSEnvironmentFile=-/etc/sysconfig/sftpdExecStart=/usr/sbin/sftpd -f /etc/ssh/sftpd_configExecReload=/bin/kill -HUP $MAINPIDKillMode=processRestart=on-failureRestartSec=42s[Install]WantedBy=multi-user.targetEOF[root@n9e ~]# grep ^[^#] /etc/pam.d/sftpdauth required pam_tally2.so deny=6 unlock_time=300auth required pam_sepermit.soauth substack password-authauth include postlogin-auth optional pam_reauthorize.so prepareaccount required pam_nologin.soaccount include password-authpassword include password-authsession required pam_selinux.so closesession required pam_loginuid.sosession required pam_selinux.so open env_paramssession required pam_namespace.sosession optional pam_keyinit.so force revokesession include password-authsession include postlogin-session optional pam_reauthorize.so prepare[root@n9e ~]#[root@n9e home]# grep ^[^#] /etc/ssh/sftpd_configcat > /etc/ssh/sftpd_config<<EOFPort 22222HostKey /etc/ssh/ssh_host_rsa_keyHostKey /etc/ssh/ssh_host_ecdsa_keyHostKey /etc/ssh/ssh_host_ed25519_keySyslogFacility AUTHPRIVPermitRootLogin yesAuthorizedKeysFile .ssh/authorized_keysPasswordAuthentication yesChallengeResponseAuthentication noGSSAPIAuthentication yesGSSAPICleanupCredentials noUsePAM yesX11Forwarding yesUseDNS noBanner /etc/issue.netAcceptEnv LANG LC_CTYPE LC_NUMERIC LC_TIME LC_COLLATE LC_MONETARY LC_MESSAGESAcceptEnv LC_PAPER LC_NAME LC_ADDRESS LC_TELEPHONE LC_MEASUREMENTAcceptEnv LC_IDENTIFICATION LC_ALL LANGUAGEAcceptEnv XMODIFIERSPidFile /var/run/sftpd.pidSubsystem sftp internal-sftpMatch Group sftpX11Forwarding noAllowTcpForwarding noForceCommand internal-sftpChrootDirectory /data/sftp/%uEOF[root@n9e ~]# cat /etc/sysconfig/sftp# Configuration file for the sshd service.# The server keys are automatically generated if they are missing.# To change the automatic creation uncomment and change the appropriate# line. Accepted key types are: DSA RSA ECDSA ED25519.# The default is "RSA ECDSA ED25519"# AUTOCREATE_SERVER_KEYS=""# AUTOCREATE_SERVER_KEYS="RSA ECDSA ED25519"# Do not change this option unless you have hardware random# generator and you REALLY know what you are doingSSH_USE_STRONG_RNG=0# SSH_USE_STRONG_RNG=1[root@n9e ~]#[root@n9e ~]# grep ^[^#] /etc/sysconfig/sftpSSH_USE_STRONG_RNG=0[root@n9e ~]#> /var/run/sftpd.pidsystemctl daemon-reloadsystemctl enable sftpd.servicesystemctl restart sftpd.service锁定家目录:groupadd sftpuseradd -g sftp -s /bin/false mysftppasswd mysftpmkdir -p /data/sftp/mysftpusermod -d /data/sftp/mysftp mysftpchown root:sftp /data/sftp/mysftpchmod 755 /data/sftp/mysftp读写目录:chmod 775 /data/sftp/mysftp-witersystemctl restart sftpd.servicemkdir -p /home/mysftp/.sshchown mysftp:sftp /home/zhangsan/.sshchmod 700 /home/mysftp/.sshcat xxx.pub >/home/mysftp/.ssh/authorized_keyschown mysftp:sftp /home/mysftp/.ssh/authorized_keyschmod 700 /home/mysftp/.ssh/authorized_keys目录的权限设定有两个要点:1、由ChrootDirectory指定的目录开始一直往上到系统根目录为止的目录拥有者都只能是root2、由ChrootDirectory指定的目录开始一直往上到系统根目录为止都不可以具有群组写入权限[root@n9e ~]# ll /data/total 0drwxr-xr-x 5 root root 68 Oct 26 09:05 filebrowserdrwxr-xr-x 3 root root 20 Dec 11 19:23 sftp[root@n9e ~]# cd /data/sftp/[root@n9e sftp]# pwd/data/sftp[root@n9e sftp]# lltotal 0drwxr-xr-x 2 root sftp 6 Dec 11 19:23 mysftp[root@n9e sftp]#[root@n9e sftp]# cd mysftp/[root@n9e mysftp]# ls -ltotal 0[root@n9e mysftp]# touch test[root@n9e mysftp]# lltotal 0-rw-r--r-- 1 root root 0 Dec 11 19:40 test[root@n9e mysftp]#
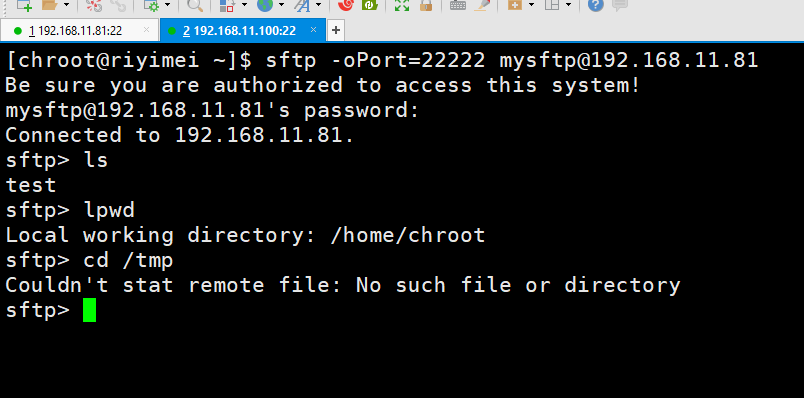
[chroot@riyimei ~]$ sftp -oPort=22222 -v mysftp@192.168.11.81OpenSSH_7.4p1, OpenSSL 1.0.2k-fips 26 Jan 2017debug1: Reading configuration data /etc/ssh/ssh_configdebug1: /etc/ssh/ssh_config line 58: Applying options for *debug1: Connecting to 192.168.11.81 [192.168.11.81] port 22222.debug1: Connection established.debug1: SELinux support disableddebug1: key_load_public: No such file or directorydebug1: identity file /home/chroot/.ssh/id_rsa type -1debug1: key_load_public: No such file or directorydebug1: identity file /home/chroot/.ssh/id_rsa-cert type -1debug1: key_load_public: No such file or directorydebug1: identity file /home/chroot/.ssh/id_dsa type -1debug1: key_load_public: No such file or directorydebug1: identity file /home/chroot/.ssh/id_dsa-cert type -1debug1: key_load_public: No such file or directorydebug1: identity file /home/chroot/.ssh/id_ecdsa type -1debug1: key_load_public: No such file or directorydebug1: identity file /home/chroot/.ssh/id_ecdsa-cert type -1debug1: key_load_public: No such file or directorydebug1: identity file /home/chroot/.ssh/id_ed25519 type -1debug1: key_load_public: No such file or directorydebug1: identity file /home/chroot/.ssh/id_ed25519-cert type -1debug1: Enabling compatibility mode for protocol 2.0debug1: Local version string SSH-2.0-OpenSSH_7.4debug1: Remote protocol version 2.0, remote software version OpenSSH_7.4debug1: match: OpenSSH_7.4 pat OpenSSH* compat 0x04000000debug1: Authenticating to 192.168.11.81:22222 as 'mysftp'debug1: SSH2_MSG_KEXINIT sentdebug1: SSH2_MSG_KEXINIT receiveddebug1: kex: algorithm: curve25519-sha256debug1: kex: host key algorithm: ecdsa-sha2-nistp256debug1: kex: server->client cipher: chacha20-poly1305@openssh.com MAC: <implicit> compression: nonedebug1: kex: client->server cipher: chacha20-poly1305@openssh.com MAC: <implicit> compression: nonedebug1: kex: curve25519-sha256 need=64 dh_need=64debug1: kex: curve25519-sha256 need=64 dh_need=64debug1: expecting SSH2_MSG_KEX_ECDH_REPLYdebug1: Server host key: ecdsa-sha2-nistp256 SHA256:xvABNXYzwRw/ORT/FVX8uFJ3p4hdc8PcZEdrPFmCGGQdebug1: checking without port identifierThe authenticity of host '[192.168.11.81]:22222 ([192.168.11.81]:22222)' can't be established.ECDSA key fingerprint is SHA256:xvABNXYzwRw/ORT/FVX8uFJ3p4hdc8PcZEdrPFmCGGQ.ECDSA key fingerprint is MD5:8a:50:00:d0:ff:7d:5e:f7:90:80:06:76:02:18:7d:a1.Are you sure you want to continue connecting (yes/no)? yesWarning: Permanently added '[192.168.11.81]:22222' (ECDSA) to the list of known hosts.debug1: rekey after 134217728 blocksdebug1: SSH2_MSG_NEWKEYS sentdebug1: expecting SSH2_MSG_NEWKEYSdebug1: SSH2_MSG_NEWKEYS receiveddebug1: rekey after 134217728 blocksdebug1: SSH2_MSG_EXT_INFO receiveddebug1: kex_input_ext_info: server-sig-algs=<rsa-sha2-256,rsa-sha2-512>debug1: SSH2_MSG_SERVICE_ACCEPT receivedBe sure you are authorized to access this system!debug1: Authentications that can continue: publickey,gssapi-keyex,gssapi-with-mic,passworddebug1: Next authentication method: gssapi-keyexdebug1: No valid Key exchange contextdebug1: Next authentication method: gssapi-with-micdebug1: Unspecified GSS failure. Minor code may provide more informationNo Kerberos credentials available (default cache: KEYRING:persistent:700)debug1: Unspecified GSS failure. Minor code may provide more informationNo Kerberos credentials available (default cache: KEYRING:persistent:700)debug1: Next authentication method: publickeydebug1: Trying private key: /home/chroot/.ssh/id_rsadebug1: Trying private key: /home/chroot/.ssh/id_dsadebug1: Trying private key: /home/chroot/.ssh/id_ecdsadebug1: Trying private key: /home/chroot/.ssh/id_ed25519debug1: Next authentication method: passwordmysftp@192.168.11.81's password:debug1: Authentication succeeded (password).Authenticated to 192.168.11.81 ([192.168.11.81]:22222).debug1: channel 0: new [client-session]debug1: Requesting no-more-sessions@openssh.comdebug1: Entering interactive session.debug1: pledge: networkdebug1: client_input_global_request: rtype hostkeys-00@openssh.com want_reply 0debug1: Sending environment.debug1: Sending env LANG = en_US.UTF-8debug1: Sending subsystem: sftpConnected to 192.168.11.81.sftp> lstestsftp> pwdRemote working directory: /sftp> llssftp> lpwdLocal working directory: /home/chrootsftp> cd /homeCouldn't stat remote file: No such file or directorysftp> cd /dataCouldn't stat remote file: No such file or directorysftp> lstestsftp> lpwdLocal working directory: /home/chrootsftp> llssftp>
设置多用户权限和锁定家目录
PidFile /var/run/sftpd.pidSubsystem sftp internal-sftpMatch Group sftpX11Forwarding noAllowTcpForwarding noForceCommand internal-sftpChrootDirectory /data/sftp/%uMatch User riyimeiX11Forwarding noAllowTcpForwarding noForceCommand internal-sftpChrootDirectory /data/sftp/riyimeiMatch User liwmX11Forwarding noAllowTcpForwarding noForceCommand internal-sftpChrootDirectory /data/sftp/riyimei[root@n9e riyimei]#

