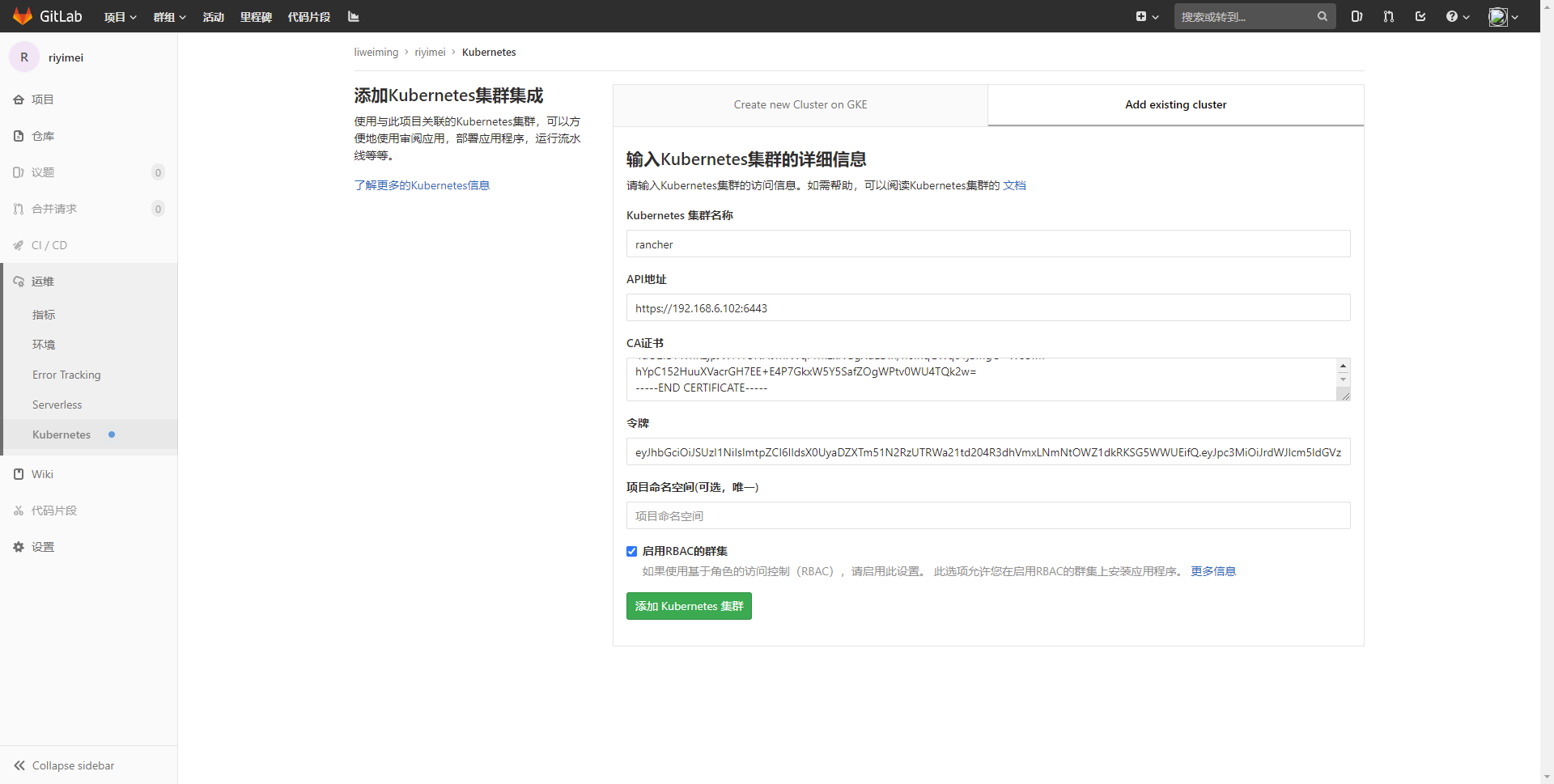
https://www.cnblogs.com/sanduzxcvbnm/p/13844799.html
https://docs.gitlab.com/ee/user/project/clusters/add_remove_clusters.html#add-existing-cluster
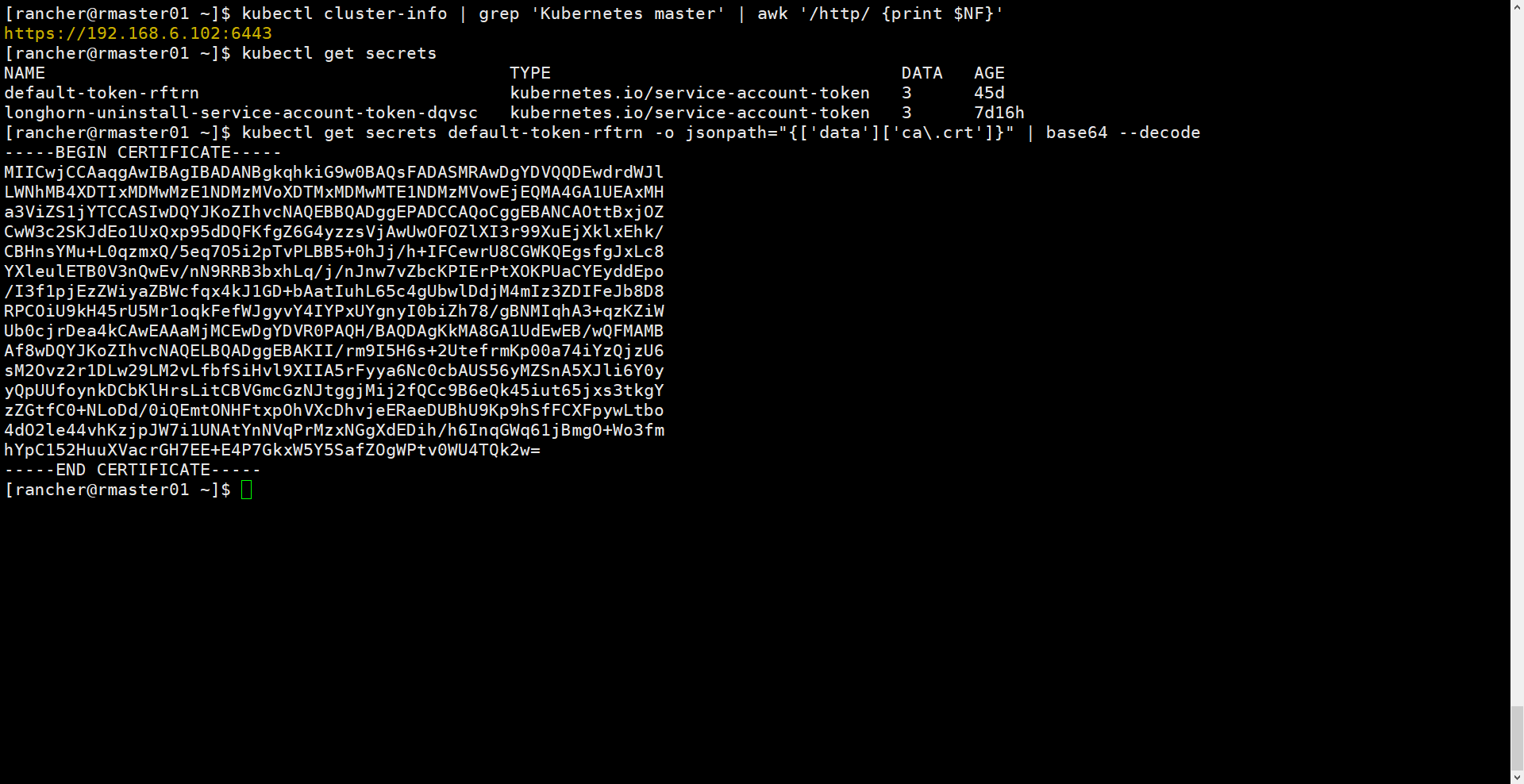
[rancher@rmaster01 ~]$ kubectl cluster-info | grep 'Kubernetes master' | awk '/http/ {print $NF}'https://192.168.6.102:6443[rancher@rmaster01 ~]$ kubectl get secretsNAME TYPE DATA AGEdefault-token-rftrn kubernetes.io/service-account-token 3 45dlonghorn-uninstall-service-account-token-dqvsc kubernetes.io/service-account-token 3 7d16h[rancher@rmaster01 ~]$ kubectl get secrets default-token-rftrn -o jsonpath="{['data']['ca\.crt']}" | base64 --decode-----BEGIN CERTIFICATE-----MIICwjCCAaqgAwIBAgIBADANBgkqhkiG9w0BAQsFADASMRAwDgYDVQQDEwdrdWJlLWNhMB4XDTIxMDMwMzE1NDMzMVoXDTMxMDMwMTE1NDMzMVowEjEQMA4GA1UEAxMHa3ViZS1jYTCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBANCAOttBxjOZCwW3c2SKJdEo1UxQxp95dDQFKfgZ6G4yzzsVjAwUwOFOZlXI3r99XuEjXklxEhk/CBHnsYMu+L0qzmxQ/5eq7O5i2pTvPLBB5+0hJj/h+IFCewrU8CGWKQEgsfgJxLc8YXleulETB0V3nQwEv/nN9RRB3bxhLq/j/nJnw7vZbcKPIErPtXOKPUaCYEyddEpo/I3f1pjEzZWiyaZBWcfqx4kJ1GD+bAatIuhL65c4gUbwlDdjM4mIz3ZDIFeJb8D8RPCOiU9kH45rU5Mr1oqkFefWJgyvY4IYPxUYgnyI0biZh78/gBNMIqhA3+qzKZiWUb0cjrDea4kCAwEAAaMjMCEwDgYDVR0PAQH/BAQDAgKkMA8GA1UdEwEB/wQFMAMBAf8wDQYJKoZIhvcNAQELBQADggEBAKII/rm9I5H6s+2UtefrmKp00a74iYzQjzU6sM2Ovz2r1DLw29LM2vLfbfSiHvl9XIIA5rFyya6Nc0cbAUS56yMZSnA5XJli6Y0yyQpUUfoynkDCbKlHrsLitCBVGmcGzNJtggjMij2fQCc9B6eQk45iut65jxs3tkgYzZGtfC0+NLoDd/0iQEmtONHFtxpOhVXcDhvjeERaeDUBhU9Kp9hSfFCXFpywLtbo4dO2le44vhKzjpJW7i1UNAtYnNVqPrMzxNGgXdEDih/h6InqGWq61jBmgO+Wo3fmhYpC152HuuXVacrGH7EE+E4P7GkxW5Y5SafZOgWPtv0WU4TQk2w=-----END CERTIFICATE-----[rancher@rmaster01 ~]$
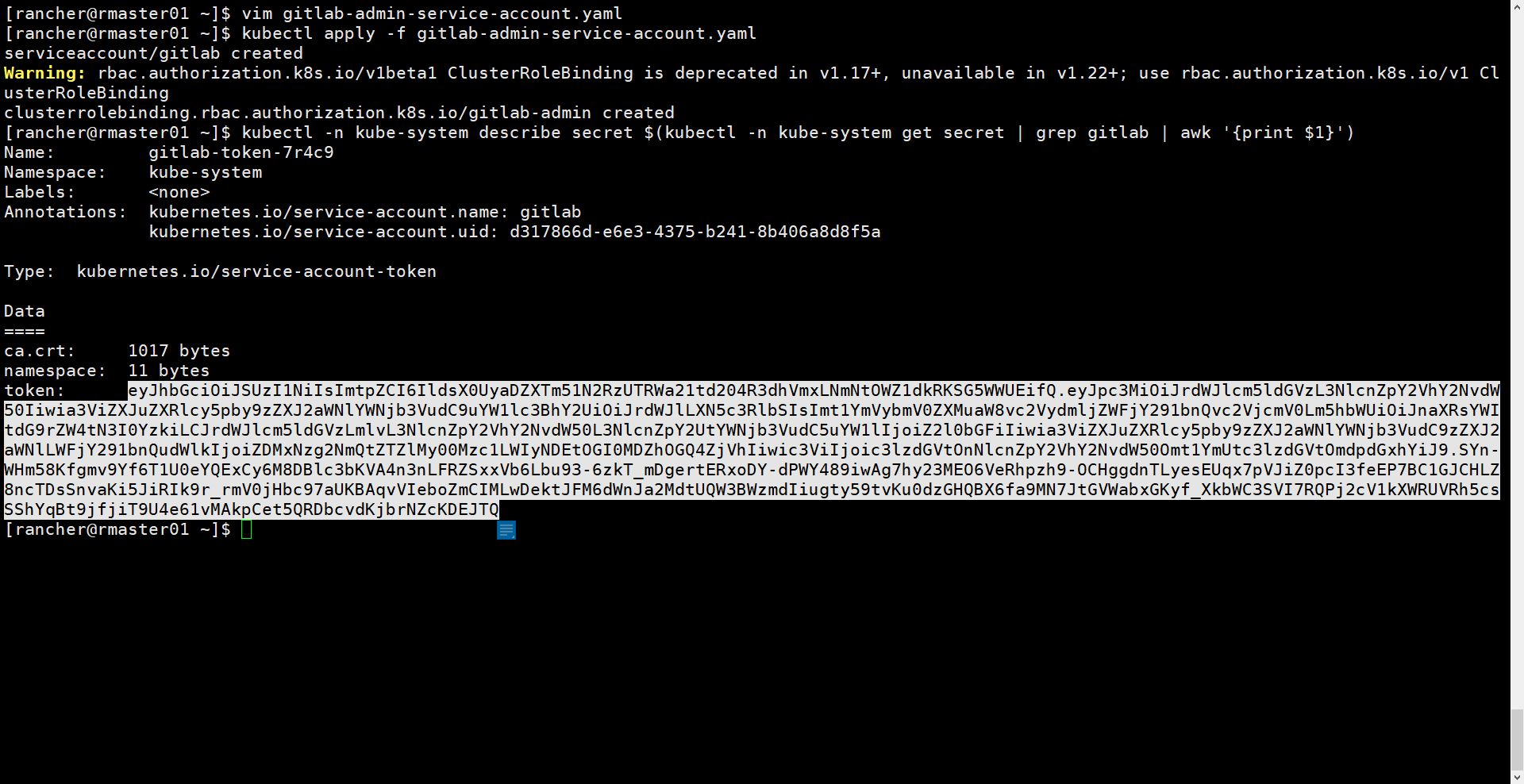
[rancher@rmaster01 ~]$ vim gitlab-admin-service-account.yaml[rancher@rmaster01 ~]$ kubectl apply -f gitlab-admin-service-account.yamlserviceaccount/gitlab createdWarning: rbac.authorization.k8s.io/v1beta1 ClusterRoleBinding is deprecated in v1.17+, unavailable in v1.22+; use rbac.authorization.k8s.io/v1 ClusterRoleBindingclusterrolebinding.rbac.authorization.k8s.io/gitlab-admin created[rancher@rmaster01 ~]$ kubectl -n kube-system describe secret $(kubectl -n kube-system get secret | grep gitlab | awk '{print $1}')Name: gitlab-token-7r4c9Namespace: kube-systemLabels: <none>Annotations: kubernetes.io/service-account.name: gitlabkubernetes.io/service-account.uid: d317866d-e6e3-4375-b241-8b406a8d8f5aType: kubernetes.io/service-account-tokenData====ca.crt: 1017 bytesnamespace: 11 bytestoken: eyJhbGciOiJSUzI1NiIsImtpZCI6IldsX0UyaDZXTm51N2RzUTRWa21td204R3dhVmxLNmNtOWZ1dkRKSG5WWUEifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJnaXRsYWItdG9rZW4tN3I0YzkiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiZ2l0bGFiIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiZDMxNzg2NmQtZTZlMy00Mzc1LWIyNDEtOGI0MDZhOGQ4ZjVhIiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50Omt1YmUtc3lzdGVtOmdpdGxhYiJ9.SYn-WHm58Kfgmv9Yf6T1U0eYQExCy6M8DBlc3bKVA4n3nLFRZSxxVb6Lbu93-6zkT_mDgertERxoDY-dPWY489iwAg7hy23MEO6VeRhpzh9-OCHggdnTLyesEUqx7pVJiZ0pcI3feEP7BC1GJCHLZ8ncTDsSnvaKi5JiRIk9r_rmV0jHbc97aUKBAqvVIeboZmCIMLwDektJFM6dWnJa2MdtUQW3BWzmdIiugty59tvKu0dzGHQBX6fa9MN7JtGVWabxGKyf_XkbWC3SVI7RQPj2cV1kXWRUVRh5csSShYqBt9jfjiT9U4e61vMAkpCet5QRDbcvdKjbrNZcKDEJTQ[rancher@rmaster01 ~]$ cat gitlab-admin-service-account.yamlapiVersion: v1kind: ServiceAccountmetadata:name: gitlabnamespace: kube-system---apiVersion: rbac.authorization.k8s.io/v1beta1kind: ClusterRoleBindingmetadata:name: gitlab-adminroleRef:apiGroup: rbac.authorization.k8s.iokind: ClusterRolename: cluster-adminsubjects:- kind: ServiceAccountname: gitlabnamespace: kube-system[rancher@rmaster01 ~]$