一:题目一
创建一个名为deployment-clusterrole的clusterrole,并且对该clusterrole只绑定对Deployment、Daemonset、Statefulset的创建权限。在指定命名空间exam创建一个名为exam-user的serviceaccount,并且将上一步创建clusterrole和该serviceaccount绑定。
通过命令行进行创建clusterrole
[root@master ~]# kubectl create clusterrole -hCreate a ClusterRole.Examples:# Create a ClusterRole named "pod-reader" that allows user to perform "get", "watch" and "list" on podskubectl create clusterrole pod-reader --verb=get,list,watch --resource=pods.............Usage:kubectl create clusterrole NAME --verb=verb --resource=resource.group [--resource-name=resourcename][--dry-run=server|client|none] [options]Use "kubectl options" for a list of global command-line options (applies to all commands).##创建步骤在这里[root@master ~]# kubectl create clusterrole deployment-clusterrole --verb=create --resource=Deployment,Daemonset,Statefulset[root@master ~]# clusterrole.rbac.authorization.k8s.io/deployment-clusterrole created
通过编写yaml来创建
apiVersion: rbac.authorization.k8s.io/v1kind: ClusterRole #kind类型为集群metadata:# "namespace" omitted since ClusterRoles are not namespacedname: secret-readerrules:- apiGroups: [""]resources: ["Deployment,Daemonset,Statefulset"]verbs: ["create"]
创建exam命名空间
[root@master ~]# kubectl create ns exam
创建serviceaccount
[root@master ~]# kubectl create ServiceAccount exam-user
将clusterrole和该serviceaccount绑定
[root@master ~]# kubectl create rolebinding -hCreate a RoleBinding for a particular Role or ClusterRole.Examples:# Create a RoleBinding for user1, user2, and group1 using the admin ClusterRolekubectl create rolebinding admin --clusterrole=admin --user=user1 --user=user2 --group=group1.....................Usage:kubectl create rolebinding NAME --clusterrole=NAME|--role=NAME [--user=username] [--group=groupname][--serviceaccount=namespace:serviceaccountname] [--dry-run=server|client|none] [options]Use "kubectl options" for a list of global command-line options (applies to all commands).进行绑定[root@master ~]# kubectl create rolebinding exam-binding --clusterrole=deployment-clusterrole --serviceaccount=exam:exam-user
通过编写yaml方式绑定
apiVersion: rbac.authorization.k8s.io/v1kind: RoleBindingmetaData:name: deployment-rolebindingnamespaces: examroleRef:apiGroup: rbac.authorization.k8s.io/v1kind: ClusterRolename:deployment-clusterrolesubjecs:- kind: ServiceAccountname: exam-usernamespaces: exam
二:题目二
在default命名空间下使用镜像nginx创建一个工作负载nginx-exam,指定pod运行在master节点,然后以NodePort方式对外暴露10080端口
在default命名空间下创建HPA规则nginx-exam-autoscale来管理上一题的工作负载nginx-exam,要求其Pod副本数在1-10之间动态变化
创建deployment无状态工作负载
[root@master ~]#vi nginx-exam.yamlapiVersion: apps/v1kind: Deploymentmetadata:name: my-nginxnamespace: defaultspec:replicas: 2selector:matchLabels:app: nginxtemplate:metadata:labels:app: nginxspec:nodeName: mastercontainers:- name: nginximage: nginximagePullPolicy: IfNotPresentports:- name: mynginxportcontainerPort: 80
创建svc暴露端口
在写svc前要修改/etc/kubernetes/manifests/kube-apiserver.yaml
在文件中添加这一行,在默认情况下nodeport暴露的端口是30000-32XXX左右所以不包含10080所以要修改文件
- —service-node-port-range=10000-49999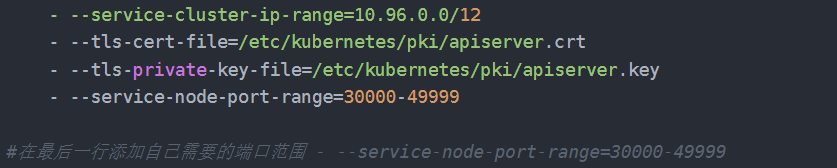
[root@master ~]# svc-deploy.yamlapiVersion: v1kind: Servicemetadata:name: svc-deployspec:selector:app: nginx #标签要选择到上面创建的podtype: NodePortports:- name: myporttargetPort: 80port: 80nodePort: 10080

