仅支持Linux!
先使用virtualbox安装centos虚拟机,然后ssh。
- runC提供了cli+libcontainer,而containerd依赖了runC,但实际只用到了libcontainer。
- containerd作为一个daemon提供服务。
- cri(containerd cri plugin)作为containerd的client,并作为gRPC Server,向Kubernetes提供服务。
runC是什么
runC的前身实际上是Docker的libcontainer项目演化而来。runC实际上就是libcontainer配上了一个轻型的客户端。
从本质上来说,容器是提供一个与宿主机系统共享内核但与系统中的其它进程资源相隔离的执行环境。Docker通过调用libcontainer包对namespaces、cgroups、capabilities以及文件系统的管理和分配来“隔离”出一个上述执行环境。同样的,runC也是对libcontainer包进行调用,去除了Docker包含的诸如镜像、Volume等高级特性,以最朴素简洁的方式达到符合OCF标准的容器管理实现。
总体而言,从libcontainer项目转变为runC项目至今,其功能和特性并没有太多变化,具体有如下几点。
- 把原先的nsinit移除,放到外面,命令名称改为runC,同样使用cli.go实现,一目了然。
- 按照开放容器标准把原先所有信息混在一起的一个配置文件拆分成config.json和state.json两个。
- 增加了按照开放容器标准设定的容器运行前和停止后执行的hook脚本功能。
- 相比原先的nsinit时期的指令,增加了runc kill命令,用于发送一个SIG_KILL信号给指定容器ID的init进程。
镜像规范与容器运行时规范
runC安装
runC
- go get github.com/opencontainers/runc
- cd /go/src/github.com/opencontainers/runc
-
runC使用
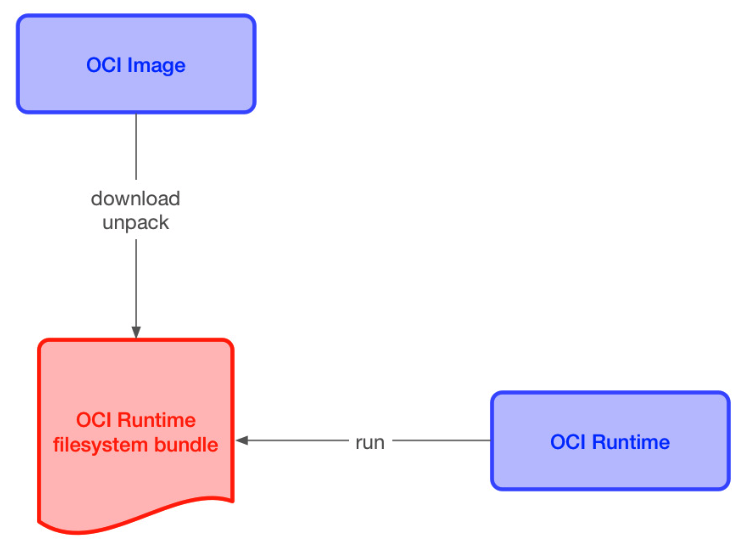
容器镜像组成
https://github.com/opencontainers/runtime-spec/blob/master/bundle.md
config.json: contains configuration data. This REQUIRED file MUST reside in the root of the bundle directory and MUST be named config.json. See config.json for more details.
- container’s root filesystem: the directory referenced by root.path, if that property is set in config.json.
创建OCI标准的镜像(Bundle,含config配置文件的规范)
将busybox镜像导出,然后解压缩 ```shellcreate the top most bundle directory
mkdir /mycontainer cd /mycontainer
create the rootfs directory
mkdir rootfs
export busybox via Docker into the rootfs directory
docker export $(docker create busybox) | tar -C rootfs -xvf -
OCI有两个规范,一个是容器运行时规范`runtime-spec`,一个是镜像格式规范`image-spec`。一个镜像,简单来说就是一个打包好的符合OCI规范的`filesystem bundle`。而bundle的话,是包含一个配置文件`config.json`和一个rootfs目录。<br />现在我们有了一个rootfs目录,然后需要创建一个config.json```shellrunc spec
它在当前目录下创建了一个json文件,来描述这个镜像。
对这个文件格式的详细字段介绍,见:https://github.com/opencontainers/runtime-spec/blob/master/config.md
linux特有的配置,见:https://github.com/opencontainers/runtime-spec/blob/master/config-linux.md
如:
terminal(bool, OPTIONAL) specifies whether a terminal is attached to the process, defaults to false.args(array of strings, REQUIRED) with similar semantics to IEEE Std 1003.1-2008execvp‘s argv. This specification extends the IEEE standard in that at least one entry is REQUIRED, and that entry is used with the same semantics asexecvp‘s file.{"ociVersion": "1.0.1-dev","process": {"terminal": true,"user": {"uid": 0,"gid": 0},"args": ["sh"],"env": ["PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin","TERM=xterm"],"cwd": "/","capabilities": {"bounding": ["CAP_AUDIT_WRITE","CAP_KILL","CAP_NET_BIND_SERVICE"],"effective": ["CAP_AUDIT_WRITE","CAP_KILL","CAP_NET_BIND_SERVICE"],"inheritable": ["CAP_AUDIT_WRITE","CAP_KILL","CAP_NET_BIND_SERVICE"],"permitted": ["CAP_AUDIT_WRITE","CAP_KILL","CAP_NET_BIND_SERVICE"],"ambient": ["CAP_AUDIT_WRITE","CAP_KILL","CAP_NET_BIND_SERVICE"]},"rlimits": [{"type": "RLIMIT_NOFILE","hard": 1024,"soft": 1024}],"noNewPrivileges": true},"root": {"path": "rootfs","readonly": true},"hostname": "runc","mounts": [{"destination": "/proc","type": "proc","source": "proc"},{"destination": "/dev","type": "tmpfs","source": "tmpfs","options": ["nosuid","strictatime","mode=755","size=65536k"]},{"destination": "/dev/pts","type": "devpts","source": "devpts","options": ["nosuid","noexec","newinstance","ptmxmode=0666","mode=0620","gid=5"]},{"destination": "/dev/shm","type": "tmpfs","source": "shm","options": ["nosuid","noexec","nodev","mode=1777","size=65536k"]},{"destination": "/dev/mqueue","type": "mqueue","source": "mqueue","options": ["nosuid","noexec","nodev"]},{"destination": "/sys","type": "sysfs","source": "sysfs","options": ["nosuid","noexec","nodev","ro"]},{"destination": "/sys/fs/cgroup","type": "cgroup","source": "cgroup","options": ["nosuid","noexec","nodev","relatime","ro"]}],"linux": {"resources": {"devices": [{"allow": false,"access": "rwm"}]},"namespaces": [{"type": "pid"},{"type": "network"},{"type": "ipc"},{"type": "uts"},{"type": "mount"}],"maskedPaths": ["/proc/kcore","/proc/latency_stats","/proc/timer_list","/proc/timer_stats","/proc/sched_debug","/sys/firmware","/proc/scsi"],"readonlyPaths": ["/proc/asound","/proc/bus","/proc/fs","/proc/irq","/proc/sys","/proc/sysrq-trigger"]}}
启动容器(含运行时规范)
一种方式是直接启动
cd /mycontainer
- runc run 容器名(自己起,要求唯一)
- 启动后直接进入终端,exit后容器被关闭
还有一种方式是分步进行:
想要后台启动的话,需要修改config.json:"terminal": false and "args": ["sleep", "5"].
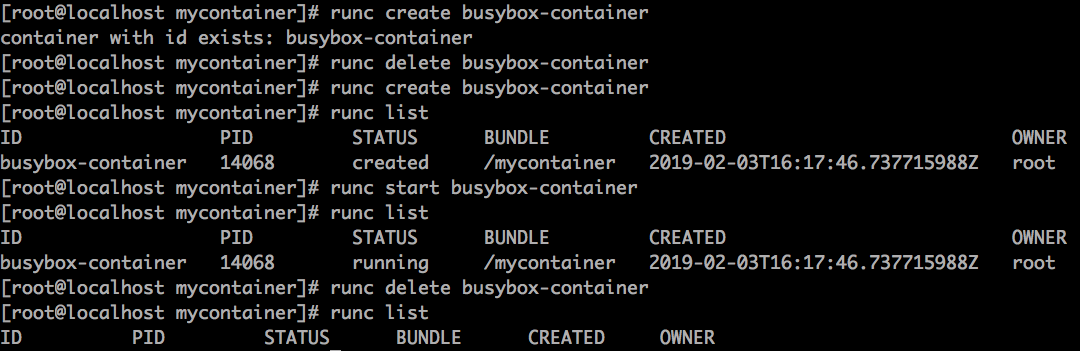
# run as rootcd /mycontainerrunc create mycontainerid# view the container is created and in the "created" staterunc list# start the process inside the containerrunc start mycontainerid# after 5 seconds view that the container has exited and is now in the stopped staterunc list# now delete the containerrunc delete mycontainerid
运行时会在/run/runc下创建一个以容器名为名字的目录,然后下面存放state.json和exec.fifo。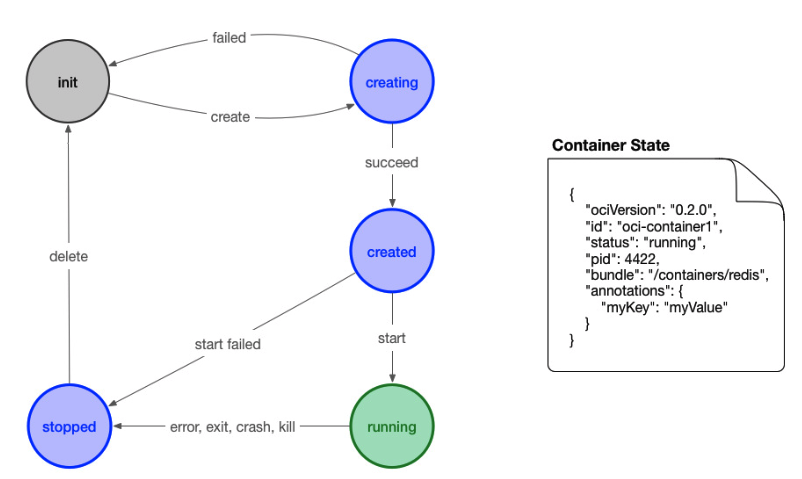
state.json(create后,start前)
state.json文件中包含的具体信息需要有:
- 版本信息:存放OCI标准的具体版本号。
- 容器ID:通常是一个哈希值,也可以是一个易读的字符串。在state.json文件中加入容器ID是为了便于之前提到的运行时hooks只需载入state.json就可以定位到容器,然后检测state.json,发现文件不见了就认为容器关停,再执行相应预定义的脚本操作。
- PID:容器中运行的首个进程在宿主机上的进程号。
- 容器文件目录:存放容器rootfs及相应配置的目录。外部程序只需读取state.json就可以定位到宿主机上的容器文件目录。 标准的容器生命周期应该包含三个基本过程。
- 容器创建:创建包括文件系统、namespaces、cgroups、用户权限在内的各项内容。
- 容器进程的启动:运行容器进程,进程的可执行文件定义在的config.json中,args项。
- 容器暂停:容器实际上作为进程可以被外部程序关停(kill),然后容器标准规范应该包含对容器暂停信号的捕获,并做相应资源回收的处理,避免孤儿进程的出现。
{"id": "busybox","init_process_pid": 14222,"init_process_start": 778857,"created": "2019-02-03T16:55:14.72045592Z","config": {"no_pivot_root": false,"parent_death_signal": 0,"rootfs": "/mycontainer/rootfs","readonlyfs": true,"rootPropagation": 0,"mounts": [{"source": "proc","destination": "/proc","device": "proc","flags": 0,"propagation_flags": null,"data": "","relabel": "","extensions": 0,"premount_cmds": null,"postmount_cmds": null}, {"source": "tmpfs","destination": "/dev","device": "tmpfs","flags": 16777218,"propagation_flags": null,"data": "mode=755,size=65536k","relabel": "","extensions": 0,"premount_cmds": null,"postmount_cmds": null}, {"source": "devpts","destination": "/dev/pts","device": "devpts","flags": 10,"propagation_flags": null,"data": "newinstance,ptmxmode=0666,mode=0620,gid=5","relabel": "","extensions": 0,"premount_cmds": null,"postmount_cmds": null}, {"source": "shm","destination": "/dev/shm","device": "tmpfs","flags": 14,"propagation_flags": null,"data": "mode=1777,size=65536k","relabel": "","extensions": 0,"premount_cmds": null,"postmount_cmds": null}, {"source": "mqueue","destination": "/dev/mqueue","device": "mqueue","flags": 14,"propagation_flags": null,"data": "","relabel": "","extensions": 0,"premount_cmds": null,"postmount_cmds": null}, {"source": "sysfs","destination": "/sys","device": "sysfs","flags": 15,"propagation_flags": null,"data": "","relabel": "","extensions": 0,"premount_cmds": null,"postmount_cmds": null}, {"source": "cgroup","destination": "/sys/fs/cgroup","device": "cgroup","flags": 2097167,"propagation_flags": null,"data": "","relabel": "","extensions": 0,"premount_cmds": null,"postmount_cmds": null}],"devices": [{"type": 99,"path": "/dev/null","major": 1,"minor": 3,"permissions": "","file_mode": 438,"uid": 0,"gid": 0,"allow": false}, {"type": 99,"path": "/dev/random","major": 1,"minor": 8,"permissions": "","file_mode": 438,"uid": 0,"gid": 0,"allow": false}, {"type": 99,"path": "/dev/full","major": 1,"minor": 7,"permissions": "","file_mode": 438,"uid": 0,"gid": 0,"allow": false}, {"type": 99,"path": "/dev/tty","major": 5,"minor": 0,"permissions": "","file_mode": 438,"uid": 0,"gid": 0,"allow": false}, {"type": 99,"path": "/dev/zero","major": 1,"minor": 5,"permissions": "","file_mode": 438,"uid": 0,"gid": 0,"allow": false}, {"type": 99,"path": "/dev/urandom","major": 1,"minor": 9,"permissions": "","file_mode": 438,"uid": 0,"gid": 0,"allow": false}],"mount_label": "","hostname": "runc","namespaces": [{"type": "NEWPID","path": ""}, {"type": "NEWNET","path": ""}, {"type": "NEWIPC","path": ""}, {"type": "NEWUTS","path": ""}, {"type": "NEWNS","path": ""}],"capabilities": {"Bounding": ["CAP_AUDIT_WRITE", "CAP_KILL", "CAP_NET_BIND_SERVICE"],"Effective": ["CAP_AUDIT_WRITE", "CAP_KILL", "CAP_NET_BIND_SERVICE"],"Inheritable": ["CAP_AUDIT_WRITE", "CAP_KILL", "CAP_NET_BIND_SERVICE"],"Permitted": ["CAP_AUDIT_WRITE", "CAP_KILL", "CAP_NET_BIND_SERVICE"],"Ambient": ["CAP_AUDIT_WRITE", "CAP_KILL", "CAP_NET_BIND_SERVICE"]},"networks": [{"type": "loopback","name": "","bridge": "","mac_address": "","address": "","gateway": "","ipv6_address": "","ipv6_gateway": "","mtu": 0,"txqueuelen": 0,"host_interface_name": "","hairpin_mode": false}],"routes": null,"cgroups": {"name": "busybox","path": "","scope_prefix": "","Paths": null,"allowed_devices": [{"type": 99,"path": "","major": -1,"minor": -1,"permissions": "m","file_mode": 0,"uid": 0,"gid": 0,"allow": true}, {"type": 98,"path": "","major": -1,"minor": -1,"permissions": "m","file_mode": 0,"uid": 0,"gid": 0,"allow": true}, {"type": 99,"path": "/dev/null","major": 1,"minor": 3,"permissions": "rwm","file_mode": 0,"uid": 0,"gid": 0,"allow": true}, {"type": 99,"path": "/dev/random","major": 1,"minor": 8,"permissions": "rwm","file_mode": 0,"uid": 0,"gid": 0,"allow": true}, {"type": 99,"path": "/dev/full","major": 1,"minor": 7,"permissions": "rwm","file_mode": 0,"uid": 0,"gid": 0,"allow": true}, {"type": 99,"path": "/dev/tty","major": 5,"minor": 0,"permissions": "rwm","file_mode": 0,"uid": 0,"gid": 0,"allow": true}, {"type": 99,"path": "/dev/zero","major": 1,"minor": 5,"permissions": "rwm","file_mode": 0,"uid": 0,"gid": 0,"allow": true}, {"type": 99,"path": "/dev/urandom","major": 1,"minor": 9,"permissions": "rwm","file_mode": 0,"uid": 0,"gid": 0,"allow": true}, {"type": 99,"path": "/dev/console","major": 5,"minor": 1,"permissions": "rwm","file_mode": 0,"uid": 0,"gid": 0,"allow": true}, {"type": 99,"path": "","major": 136,"minor": -1,"permissions": "rwm","file_mode": 0,"uid": 0,"gid": 0,"allow": true}, {"type": 99,"path": "","major": 5,"minor": 2,"permissions": "rwm","file_mode": 0,"uid": 0,"gid": 0,"allow": true}, {"type": 99,"path": "","major": 10,"minor": 200,"permissions": "rwm","file_mode": 0,"uid": 0,"gid": 0,"allow": true}],"devices": [{"type": 97,"path": "","major": -1,"minor": -1,"permissions": "rwm","file_mode": 0,"uid": 0,"gid": 0,"allow": false}, {"type": 99,"path": "","major": -1,"minor": -1,"permissions": "m","file_mode": 0,"uid": 0,"gid": 0,"allow": true}, {"type": 98,"path": "","major": -1,"minor": -1,"permissions": "m","file_mode": 0,"uid": 0,"gid": 0,"allow": true}, {"type": 99,"path": "/dev/null","major": 1,"minor": 3,"permissions": "rwm","file_mode": 0,"uid": 0,"gid": 0,"allow": true}, {"type": 99,"path": "/dev/random","major": 1,"minor": 8,"permissions": "rwm","file_mode": 0,"uid": 0,"gid": 0,"allow": true}, {"type": 99,"path": "/dev/full","major": 1,"minor": 7,"permissions": "rwm","file_mode": 0,"uid": 0,"gid": 0,"allow": true}, {"type": 99,"path": "/dev/tty","major": 5,"minor": 0,"permissions": "rwm","file_mode": 0,"uid": 0,"gid": 0,"allow": true}, {"type": 99,"path": "/dev/zero","major": 1,"minor": 5,"permissions": "rwm","file_mode": 0,"uid": 0,"gid": 0,"allow": true}, {"type": 99,"path": "/dev/urandom","major": 1,"minor": 9,"permissions": "rwm","file_mode": 0,"uid": 0,"gid": 0,"allow": true}, {"type": 99,"path": "/dev/console","major": 5,"minor": 1,"permissions": "rwm","file_mode": 0,"uid": 0,"gid": 0,"allow": true}, {"type": 99,"path": "","major": 136,"minor": -1,"permissions": "rwm","file_mode": 0,"uid": 0,"gid": 0,"allow": true}, {"type": 99,"path": "","major": 5,"minor": 2,"permissions": "rwm","file_mode": 0,"uid": 0,"gid": 0,"allow": true}, {"type": 99,"path": "","major": 10,"minor": 200,"permissions": "rwm","file_mode": 0,"uid": 0,"gid": 0,"allow": true}],"memory": 0,"memory_reservation": 0,"memory_swap": 0,"kernel_memory": 0,"kernel_memory_tcp": 0,"cpu_shares": 0,"cpu_quota": 0,"cpu_period": 0,"cpu_rt_quota": 0,"cpu_rt_period": 0,"cpuset_cpus": "","cpuset_mems": "","pids_limit": 0,"blkio_weight": 0,"blkio_leaf_weight": 0,"blkio_weight_device": null,"blkio_throttle_read_bps_device": null,"blkio_throttle_write_bps_device": null,"blkio_throttle_read_iops_device": null,"blkio_throttle_write_iops_device": null,"freezer": "","hugetlb_limit": null,"oom_kill_disable": false,"memory_swappiness": null,"net_prio_ifpriomap": null,"net_cls_classid_u": 0},"uid_mappings": null,"gid_mappings": null,"mask_paths": ["/proc/kcore", "/proc/latency_stats", "/proc/timer_list", "/proc/timer_stats", "/proc/sched_debug", "/sys/firmware", "/proc/scsi"],"readonly_paths": ["/proc/asound", "/proc/bus", "/proc/fs", "/proc/irq", "/proc/sys", "/proc/sysrq-trigger"],"sysctl": null,"seccomp": null,"Hooks": {"poststart": null,"poststop": null,"prestart": null},"version": "1.0.1-dev","labels": ["bundle=/mycontainer"],"no_new_keyring": false},"rootless": false,"cgroup_paths": {"blkio": "/sys/fs/cgroup/blkio/user.slice/busybox","cpu": "/sys/fs/cgroup/cpu,cpuacct/user.slice/busybox","cpuacct": "/sys/fs/cgroup/cpu,cpuacct/user.slice/busybox","cpuset": "/sys/fs/cgroup/cpuset/busybox","devices": "/sys/fs/cgroup/devices/user.slice/busybox","freezer": "/sys/fs/cgroup/freezer/busybox","hugetlb": "/sys/fs/cgroup/hugetlb/busybox","memory": "/sys/fs/cgroup/memory/user.slice/busybox","name=systemd": "/sys/fs/cgroup/systemd/user.slice/user-0.slice/session-4.scope/busybox","net_cls": "/sys/fs/cgroup/net_cls,net_prio/busybox","net_prio": "/sys/fs/cgroup/net_cls,net_prio/busybox","perf_event": "/sys/fs/cgroup/perf_event/busybox","pids": "/sys/fs/cgroup/pids/busybox"},"namespace_paths": {"NEWIPC": "/proc/14222/ns/ipc","NEWNET": "/proc/14222/ns/net","NEWNS": "/proc/14222/ns/mnt","NEWPID": "/proc/14222/ns/pid","NEWUSER": "/proc/14222/ns/user","NEWUTS": "/proc/14222/ns/uts"},"external_descriptors": ["/dev/pts/0", "/dev/pts/0", "/dev/pts/0"],"intel_rdt_path": ""}
容器运行时的规范,见https://github.com/opencontainers/runtime-spec/blob/master/runtime.md
linux特有的规范,见https://github.com/opencontainers/runtime-spec/blob/master/runtime-linux.md
更多命令
使用 create 命令创建容器
进入到 /tmp/mycontainer 目录中:
$ cd /tmp/mycontainer
然后创建名为 mybusybox 的容器:
$ sudo runc create mybusybox使用 list 命令查看当前存在的容器
$ sudo runc list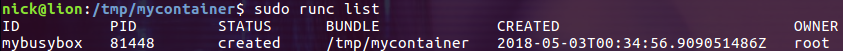
使用 state 命令查看容器的状态
$ sudo runc state mybusybox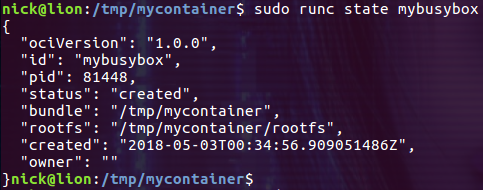
注意图中的 “status”: “created”,当通过 create 成功创建了容器后,容器的状态就是 “created”。
使用 ps 命令看看容器内运行的进程
$ sudo runc ps mybusybox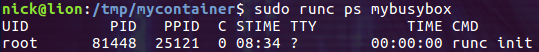
此时 mybusybox 容器内有一个名为 init 的进程在运行。
使用 start 命令执行容器中定义的任务
$ sudo runc start使用 start 命令启动容器后,让我们再用 ps 命令看看容器内运行了什么进程: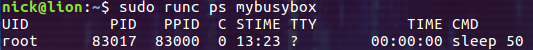
此时我们在 config.json 中定义的 sleep 进程在运行。再用 state 命令看看容器此时的状态,此时已经变成了 running!
使用 exec 命令在容器中执行命令
通过 exec 命令我们可以在处于 created 状态和 running 状态的容器中执行命令:
$ sudo runc exec mybusybox ls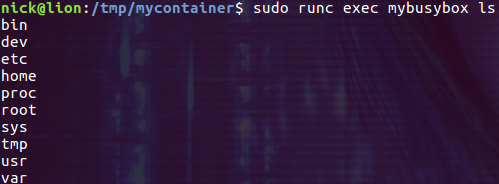
当容器中的用户任务结束后,容器会变成 stopped 状态,这时就不能再通过 exec 执行其它的命令了。
使用 delete 命令删除容器
我们可以通过 delete 命令删除容器,当然,一般情况下是删除 stopped 状态的容器:
$ sudo runc delete mybusybox使用 run 命令创建并运行容器
就像 docker run 命令一样,它会创建容器并运行容器中的命令:
$ sudo runc run mybusybox当容器中的命令退出后容器随即被删除。
使用 kill 命令停止容器中的任务
如果要停止一个容器中正在运行的任务,可以使用 kill 命令:
$ sudo runc kill mybusybox默认它会优雅的结束容器中的进程,但是碰到特殊情况,你就得使用终极信号 9:
$ sudo runc kill mybusybox 9使用 pause 命令暂停容器中的所有进程
我们先启动容器 mybusybox,然后用 pause 命令暂停它:
$ sudo runc pause mybusybox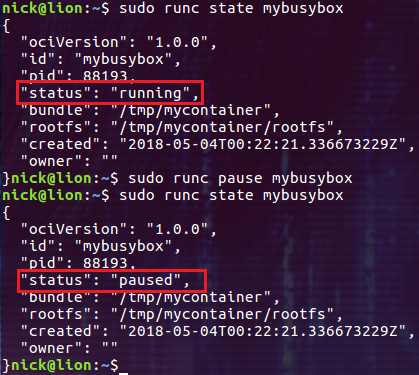
执行 pause 命令后,容器的状态由 running 变成了 paused。然后我们再通过 resume 命令恢复容器中进程的执行:
$ sudo runc resume mybusybox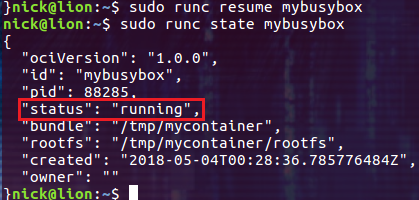
此时容器的状态又恢复到了 running。
使用 events 命令获取容器的资源使用情况
events 命令能够向我们报告容器事件及其资源占用的统计信息:
$ sudo runc events mybusybox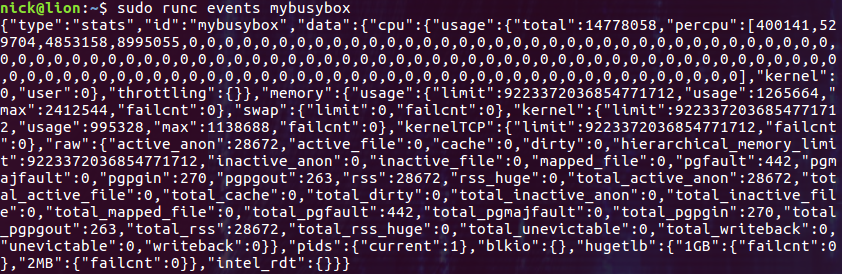
rootless containers
前面我们运行的所有命令都是以 root 权限执行的。能不能以普通用户的权限运行容器呢?答案是可以的,并被称为 rootless。要想以 rootless 的方式运行容器,需要我们在生成容器的配置文件时就为 spec 命令指定 rootless 参数:
$ runc spec —rootless
并且在运行容器时通过 —root 参数指定一个存放容器状态的路径:
$ runc —root /tmp/runc run mybusybox
CLI
USAGE:
runc [global options] command [command options] [arguments…]
VERSION:
1.0.0-rc6+dev
commit: 96ec2177ae841256168fcf76954f7177af9446eb
spec: 1.0.1-dev
COMMANDS:
checkpoint checkpoint a running container
create create a container
delete delete any resources held by the container often used with detached container
events display container events such as OOM notifications, cpu, memory, and IO usage statistics
exec execute new process inside the container
init initialize the namespaces and launch the process (do not call it outside of runc)
kill kill sends the specified signal (default: SIGTERM) to the container’s init process
list lists containers started by runc with the given root
pause pause suspends all processes inside the container
ps ps displays the processes running inside a container
restore restore a container from a previous checkpoint
resume resumes all processes that have been previously paused
run create and run a container
spec create a new specification file
start executes the user defined process in a created container
state output the state of a container
update update container resource constraints
help, h Shows a list of commands or help for one command
GLOBAL OPTIONS:
—debug enable debug output for logging
—log value set the log file path where internal debug information is written (default: “/dev/null”)
—log-format value set the format used by logs (‘text’ (default), or ‘json’) (default: “text”)
—root value root directory for storage of container state (this should be located in tmpfs) (default: “/run/runc”)
—criu value path to the criu binary used for checkpoint and restore (default: “criu”)
—systemd-cgroup enable systemd cgroup support, expects cgroupsPath to be of form “slice:prefix:name” for e.g. “system.slice:runc:434234”
—rootless value ignore cgroup permission errors (‘true’, ‘false’, or ‘auto’) (default: “auto”)
—help, -h show help
—version, -v print the version
标准容器的5个原则
https://github.com/opencontainers/runtime-spec/blob/master/principles.md
- 操作标准化:容器的标准化操作包括使用标准容器创建、启动、停止容器,使用标准文件系统工具复制和创建容器快照,使用标准化网络工具进行下载和上传。
- 内容无关:内容无关指不管针对的具体容器内容是什么,容器标准操作执行后都能产生同样的效果。如容器可以用同样的方式上传、启动,不管是PHP应用还是MySQL数据库服务。
- 基础设施无关:无论是个人的笔记本电脑还是AWS S3,亦或是OpenStack,或者其它基础设施,都应该对支持容器的各项操作。
- 为自动化量身定制:制定容器统一标准,是的操作内容无关化、平台无关化的根本目的之一,就是为了可以使容器操作全平台自动化。
- 工业级交付:制定容器标准一大目标,就是使软件分发可以达到工业级交付成为现实。
镜像格式规范
https://github.com/opencontainers/image-spec/blob/master/spec.md
The OCI Image Media Types document is a starting point to understanding the overall structure of the specification.
The high-level components of the spec include:
- Image Manifest - a document describing the components that make up a container image
- Image Index - an annotated index of image manifests
- Image Layout - a filesystem layout representing the contents of an image
- Filesystem Layer - a changeset that describes a container’s filesystem
- Image Configuration - a document determining layer ordering and configuration of the image suitable for translation into a runtime bundle
- Conversion - a document describing how this translation should occur
- Descriptor - a reference that describes the type, metadata and content address of referenced content
OCI 容器镜像主要包括几块内容:
- 文件系统:以 layer 保存的文件系统,每个 layer 保存了和上层之间变化的部分,layer 应该保存哪些文件,怎么表示增加、修改和删除的文件等
- config 文件:保存了文件系统的层级信息(每个层级的 hash 值,以及历史信息),以及容器运行时需要的一些信息(比如环境变量、工作目录、命令参数、mount 列表),指定了镜像在某个特定平台和系统的配置。比较接近我们使用
docker inspect <image_id>看到的内容 - manifest 文件:镜像的 config 文件索引,有哪些 layer,额外的 annotation 信息,manifest 文件中保存了很多和当前平台有关的信息
index 文件:可选的文件,指向不同平台的 manifest 文件,这个文件能保证一个镜像可以跨平台使用,每个平台拥有不同的 manifest 文件,使用 index 作为索引
参考
- libcontainer分析
- libnetwork分析
- namespace:http://www.sel.zju.edu.cn/?p=556
- cgroup:http://www.sel.zju.edu.cn/?p=573
- image:http://www.sel.zju.edu.cn/?p=549
pouchcontainer:http://www.sel.zju.edu.cn/?p=878
代码仓库
- OCI容器运行时工具:https://github.com/opencontainers/runtime-tools
- OCI容器镜像规范:https://github.com/opencontainers/image-spec
- OCI容器镜像工具:https://github.com/opencontainers/image-tools
- runC:https://github.com/opencontainers/runc
- Go命令行库:https://github.com/urfave/cli
- 《动手写Docker》:https://github.com/xianlubird/mydocker
- mini docker:https://github.com/fireflyc/mini-docker

