- iptables
- Tables
- Chains
- Target
- firewalld
- 配置实例:
- 把firewalld服务中eno16777728网卡的默认区域修改为external,并在系统重启后生效。分别查看当前与永久模式下的区域名称:
- 把firewalld服务的当前默认区域设置为public:
- 启动/关闭firewalld防火墙服务的应急状况模式,阻断一切网络连接(当远程控制服务器时请慎用):
- 查询public区域是否允许请求SSH和HTTPS协议的流量:
- 把firewalld服务中请求HTTPS协议的流量设置为永久允许,并立即生效:
- 把在firewalld服务中访问8080和8081端口的流量策略设置为允许,但仅限当前生效:
- 把原本访问本机888端口的流量转发到22端口,要且求当前和长期均有效:
- 在firewalld服务中配置一条富规则,使其拒绝192.168.10.0/24网段的所有用户访问本机的ssh服务(22端口):
- 配置实例:
iptables
iptables服务把用于处理或过滤流量的策略条目称之为规则,多条规则可以组成一个规则链,而规则链则依据数据包处理位置的不同进行分类。
Tables
tables allow you to do very specific things with packets.
- The filter table: This is the default and perhaps the most widely used table. It is used to make decisions about whether a packet should be allowed to reach its destination.
- The mangle table: This table allows you to alter packet headers in various ways, such as changing TTL values.
- The nat table: This table allows you to route packets to different hosts on NAT (Network Address Translation) networks by changing the source and destination addresses of packets. It is often used to allow access to services that can’t be accessed directly, because they’re on a NAT network.
- The raw table: iptables is a stateful firewall, which means that packets are inspected with respect to their “state”.
Chains
Now, each of these tables are composed of a few default chains. These chains allow you to filter packets at various points.
- The PREROUTING chain: Rules in this chain apply to packets as they just arrive on the network interface. This chain is present in the nat, mangle and raw tables.
- The INPUT chain: Rules in this chain apply to packets just before they’re given to a local process. This chain is present in the mangle and filter tables.
- The OUTPUT chain: The rules here apply to packets just after they’ve been produced by a process. This chain is present in the raw, mangle, nat and filter tables.
- The FORWARD chain: The rules here apply to any packets that are routed through the current host. This chain is only present in the mangle and filter tables.
- The POSTROUTING chain: The rules in this chain apply to packets as they just leave the network interface. This chain is present in the nat and mangle tables.
默认的表、链结构示意图
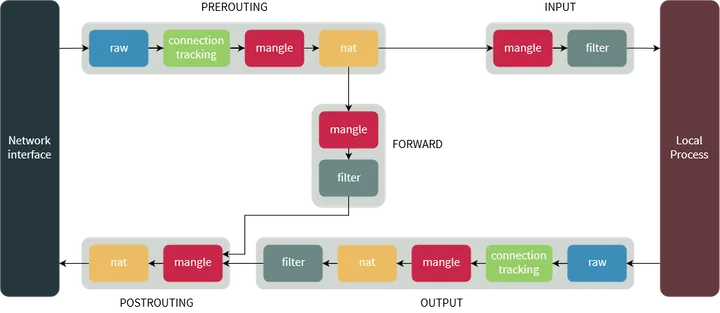
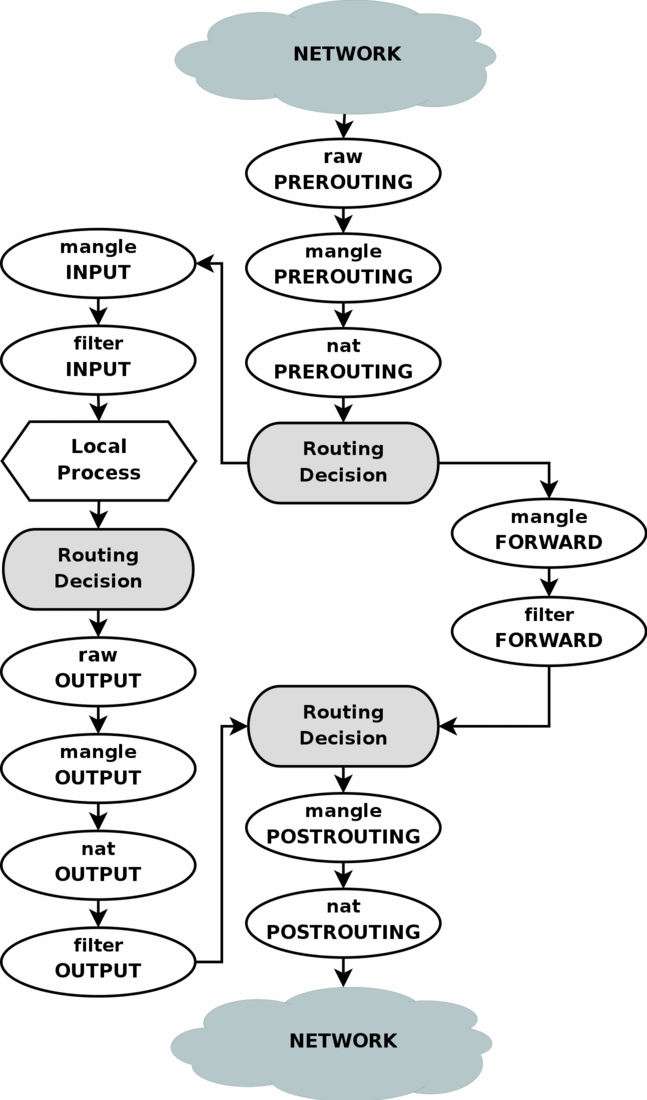
规则链之间的顺序
- 入站:PREROUTING → INPUT
入站的目的地是明确的,即当前主机。
- 出站:OUTPUT → POSTROUTING
出站的源地址是明确的,即当前主机。
转发:PREROUTING → FORWARD → POSTROUTING
当防火墙实现路由转发功能时,即数据流穿越防火墙时,为转发。
Target
- ACCEPT: This causes iptables to accept the packet.
- DROP: iptables drops the packet. To anyone trying to connect to your system, it would appear like the system didn’t even exist.
- REJECT: iptables “rejects” the packet. It sends a “connection reset” packet in case of TCP, or a “destination host unreachable” packet in case of UDP or ICMP.
- Log
配置方式
iptables中基本的命令参数
iptables命令可以根据流量的源地址、目的地址、传输协议、服务类型等信息进行匹配,一旦匹配成功,iptables就会根据策略规则所预设的动作来处理这些流量。
iptables [-t 表名] 选项 [链名] [条件] [-j 控制类型]
iptables命令的几个注意事项
- 不指定表名时,默认指filter表
- 不指定链名时,默认指表内的所有链
- 除非设置链的默认策略,否则必须指定匹配条件
- 选项、链名、控制类型使用大写字母,其余均为小写
| 参数 | 作用 |
|---|---|
| -P | 设置默认策略 |
| -F | 清空规则链 |
| -L | 查看规则链 |
| -A | 在规则链的末尾加入新规则 |
| -I num | 在规则链的头部加入新规则 |
| -D num | 删除某一条规则 |
| -s | 匹配来源地址IP/MASK,加叹号“!”表示除这个IP外 |
| -d | 匹配目标地址 |
| -i网卡名称 | 匹配从这块网卡流入的数据 |
| -o网卡名称 | 匹配从这块网卡流出的数据 |
| -p | 匹配协议,如TCP、UDP、ICMP |
| —dport num,num1:num2 | 匹配目标端口号,num1-num2 范围端口号 |
| —sport num,num1,num2 | 匹配来源端口号,num1和num2 |
查看已有防火墙规则链
[root@linux Desktop]# iptables -LChain INPUT (policy ACCEPT)target prot opt source destinationACCEPT all -- anywhere anywhere ctstate RELATED,ESTABLISHEDACCEPT all -- anywhere anywhereINPUT_direct all -- anywhere anywhereINPUT_ZONES_SOURCE all -- anywhere anywhereINPUT_ZONES all -- anywhere anywhereACCEPT icmp -- anywhere anywhereREJECT all -- anywhere anywhere reject-with icmp-host-prohibitedChain FORWARD (policy ACCEPT)target prot opt source destinationACCEPT all -- anywhere anywhere ctstate RELATED,ESTABLISHEDACCEPT all -- anywhere anywhereFORWARD_direct all -- anywhere anywhereFORWARD_IN_ZONES_SOURCE all -- anywhere anywhereFORWARD_IN_ZONES all -- anywhere anywhereFORWARD_OUT_ZONES_SOURCE all -- anywhere anywhereFORWARD_OUT_ZONES all -- anywhere anywhereACCEPT icmp -- anywhere anywhereREJECT all -- anywhere anywhere reject-with icmp-host-prohibited....
清空防火墙规则链
[root@linux Desktop]# iptables -F
[root@linux Desktop]# iptables -L
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
....
将INPUT规则链默认规则设置为拒绝,规则链的默认拒绝动作只能是DROP,而不能是REJECT。
[root@linux Desktop]# iptables -P INPUT DROP
[root@linux Desktop]# iptables -L
Chain INPUT (policy DROP)
target prot opt source destination
放行 ICMP 流量
[root@linux Desktop]# iptables -I INPUT -p icmp -j ACCEPT
[root@linux Desktop]# iptables -L
Chain INPUT (policy DROP)
target prot opt source destination
ACCEPT icmp -- anywhere anywhere
删除放行ICMP流量,修改默认策略为放行
[root@linux Desktop]# iptables -D INPUT 1
[root@linux Desktop]# iptables -P INPUT ACCEPT
[root@linux Desktop]# iptables -L
Chain INPUT (policy ACCEPT)
target prot opt source destination
只允许本网段访问本机22端口
[root@linux Desktop]# iptables -I INPUT -s 172.20.10.0/24 -p tcp --dport 22 -j ACCEPT
[root@linux Desktop]# iptables -A INPUT -p tcp --dport 22 -j REJECT
[root@linux Desktop]# iptables -L
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT tcp -- bogon/24 anywhere tcp dpt:ssh
REJECT tcp -- anywhere anywhere tcp dpt:ssh reject-with icmp-port-unreachable
拒绝所有主机访问本1000-1024端口
[root@linux Desktop]# iptables -A INPUT -p tcp --dport 1000:1024 -j REJECT
[root@linux Desktop]# iptables -A INPUT -p udp --dport 1000:1024 -j REJECT
[root@linux Desktop]# iptables -L
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT tcp -- bogon/24 anywhere tcp dpt:ssh
REJECT tcp -- anywhere anywhere tcp dpt:ssh reject-with icmp-port-unreachable
REJECT tcp -- anywhere anywhere tcp dpts:cadlock2:1024 reject-with icmp-port-unreachable
REJECT udp -- anywhere anywhere udp dpts:cadlock2:1024 reject-with icmp-port-unreachable
保存防火墙规则
[root@linux Desktop]# service iptables save
iptables: Saving firewall rules to /etc/sysconfig/iptables:[ OK ]
黑白名单
[root@localhost ~]# vim /opt/ipfw.w
192.168.1.110
220.121.72.85 ……
[root@localhost ~]# vim /opt/ipfw.b
218.29.30.131
61.45.135.29
121.113.79.81
https://www.booleanworld.com/depth-guide-iptables-linux-firewall/
firewalld
RHEL 7系统中集成了多款防火墙管理工具,其中firewalld(Dynamic Firewall Manager of Linux systems,Linux系统的动态防火墙管理器)服务是默认的防火墙配置管理工具,它拥有基于CLI(命令行界面)和基于GUI(图形用户界面)的两种管理方式。<br /> 相较于传统的防火墙管理配置工具,firewalld支持动态更新技术并加入了区域(zone)的概念。简单来说,区域就是firewalld预先准备了几套防火墙策略集合(策略模板),用户可以根据生产场景的不同而选择合适的策略集合,从而实现防火墙策略之间的快速切换。firewalld中常见的区域名称(默认为public)。<br />firewalld中常用的区域名称及策略规则
| 区域 | 默认策略规则 |
|---|---|
| trusted | 允许所有的数据包 |
| home | 拒绝流入的流量,除非与流出的流量相关;而如果流量与ssh、mdns、ipp-client、amba-client与dhcpv6-client服务相关,则允许流量 |
| internal | 等同于home区域 |
| work | 拒绝流入的流量,除非与流出的流量数相关;而如果流量与ssh、ipp-client与dhcpv6-client服务相关,则允许流量 |
| public | 拒绝流入的流量,除非与流出的流量相关;而如果流量与ssh、dhcpv6-client服务相关,则允许流量 |
| external | 拒绝流入的流量,除非与流出的流量相关;而如果流量与ssh服务相关,则允许流量 |
| dmz | 拒绝流入的流量,除非与流出的流量相关;而如果流量与ssh服务相关,则允许流量 |
| block | 拒绝流入的流量,除非与流出的流量相关 |
| drop | 拒绝流入的流量,除非与流出的流量相关 |
firewall-cmd命令中使用的参数以及作用
| 参数 | 作用 |
|---|---|
| —get-default-zone | 查询默认的区域名称 |
| —set-default-zone=<区域名称> | 设置默认的区域,使其永久生效 |
| —get-zones | 显示可用的区域 |
| —get-services | 显示预先定义的服务 |
| —get-active-zones | 显示当前正在使用的区域与网卡名称 |
| —add-source= | 将源自此IP或子网的流量导向指定的区域 |
| —remove-source= | 不再将源自此IP或子网的流量导向某个指定区域 |
| —add-interface=<网卡名称> | 将源自该网卡的所有流量都导向某个指定区域 |
| —change-interface=<网卡名称> | 将某个网卡与区域进行关联 |
| —list-all | 显示当前区域的网卡配置参数、资源、端口以及服务等信息 |
| —list-all-zones | 显示所有区域的网卡配置参数、资源、端口以及服务等信息 |
| —add-service=<服务名> | 设置默认区域允许该服务的流量 |
| —add-port=<端口号/协议> | 设置默认区域允许该端口的流量 |
| —remove-service=<服务名> | 设置默认区域不再允许该服务的流量 |
| —remove-port=<端口号/协议> | 设置默认区域不再允许该端口的流量 |
| —reload | 让“永久生效”的配置规则立即生效,并覆盖当前的配置规则 |
| —panic-on | 开启应急状况模式 |
| —panic-off | 关闭应急状况模式 |
Firewall 有俩个保存配置的位置,runtime (默认)当前生效,在系统重启后就会失效、Permanent 当前不生效,在重启后一直有效,在配置时。
配置实例:
把firewalld服务中eno16777728网卡的默认区域修改为external,并在系统重启后生效。分别查看当前与永久模式下的区域名称:
[root@linuxprobe ~]# firewall-cmd --permanent --zone=external --change-interface=
eno16777728
success
[root@linuxprobe ~]# firewall-cmd --get-zone-of-interface=eno16777728
public
[root@linuxprobe ~]# firewall-cmd --permanent --get-zone-of-interface=eno16777728
external
把firewalld服务的当前默认区域设置为public:
[root@linuxprobe ~]# firewall-cmd --set-default-zone=public
success
[root@linuxprobe ~]# firewall-cmd --get-default-zone
public
启动/关闭firewalld防火墙服务的应急状况模式,阻断一切网络连接(当远程控制服务器时请慎用):
[root@linuxprobe ~]# firewall-cmd --panic-on
success
[root@linuxprobe ~]# firewall-cmd --panic-off
success
查询public区域是否允许请求SSH和HTTPS协议的流量:
[root@linuxprobe ~]# firewall-cmd --zone=public --query-service=ssh
yes
[root@linuxprobe ~]# firewall-cmd --zone=public --query-service=https
no
把firewalld服务中请求HTTPS协议的流量设置为永久允许,并立即生效:
[root@linuxprobe ~]# firewall-cmd --zone=public --add-service=https
success
[root@linuxprobe ~]# firewall-cmd --permanent --zone=public --add-service=https
success
[root@linuxprobe ~]# firewall-cmd --reload
success
把在firewalld服务中访问8080和8081端口的流量策略设置为允许,但仅限当前生效:
[root@linuxprobe ~]# firewall-cmd --zone=public --add-port=8080-8081/tcp
success
[root@linuxprobe ~]# firewall-cmd --zone=public --list-ports
8080-8081/tcp
把原本访问本机888端口的流量转发到22端口,要且求当前和长期均有效:
流量转发命令格式为firewall-cmd —permanent —zone=<区域> —add-forward-port=port= <源端口号>:proto=<协议>:toport=<目标端口号>:toaddr=<目标IP地址>
[root@linuxprobe ~]# firewall-cmd --permanent --zone=public --add-forward-port=
port=888:proto=tcp:toport=22:toaddr=192.168.10.10
success
[root@linuxprobe ~]# firewall-cmd --reload
success
firewalld中的富规则表示更细致、更详细的防火墙策略配置,它可以针对系统服务、端口号、源地址和目标地址等诸多信息进行更有针对性的策略配置。它的优先级在所有的防火墙策略中也是最高的。
在firewalld服务中配置一条富规则,使其拒绝192.168.10.0/24网段的所有用户访问本机的ssh服务(22端口):
[root@linuxprobe ~]# firewall-cmd --permanent --zone=public --add-rich-rule="rule family="ipv4" source address="192.168.10.0/24" service name="ssh" reject"
success
[root@linuxprobe ~]# firewall-cmd --reload
success

