概述
docker swarm的ingress网络又叫 Ingress Routing Mesh
主要是为了实现把service的服务端口对外发布出去,让其能够被外部网络访问到。
ingress routing mesh是docker swarm网络里最复杂的一部分内容,包括多方面的内容:
- iptables的 Destination NAT流量转发
- Linux bridge, network namespace
- 使用IPVS技术做负载均衡
-
service创建
创建一个service,指定网络是overlay的mynet, 通过-p把端口映射出来
我们使用的镜像containous/whoami是一个简单的web服务,能返回服务器的hostname,和基本的网络信息,比如IP地址vagrant@swarm-manager:~$ docker service create --name web --network mynet -p 8080:80 --replicas 2 containous/whoamia9cn3p0ovg5jcz30rzz89lyfzoverall progress: 2 out of 2 tasks1/2: running [==================================================>]2/2: running [==================================================>]verify: Service convergedvagrant@swarm-manager:~$ docker service lsID NAME MODE REPLICAS IMAGE PORTSa9cn3p0ovg5j web replicated 2/2 containous/whoami:latest *:8080->80/tcpvagrant@swarm-manager:~$ docker service ps webID NAME IMAGE NODE DESIRED STATE CURRENT STATE ERROR PORTSudlzvsraha1x web.1 containous/whoami:latest swarm-worker1 Running Running 16 seconds agomms2c65e5ygt web.2 containous/whoami:latest swarm-manager Running Running 16 seconds agovagrant@swarm-manager:~$
service的访问
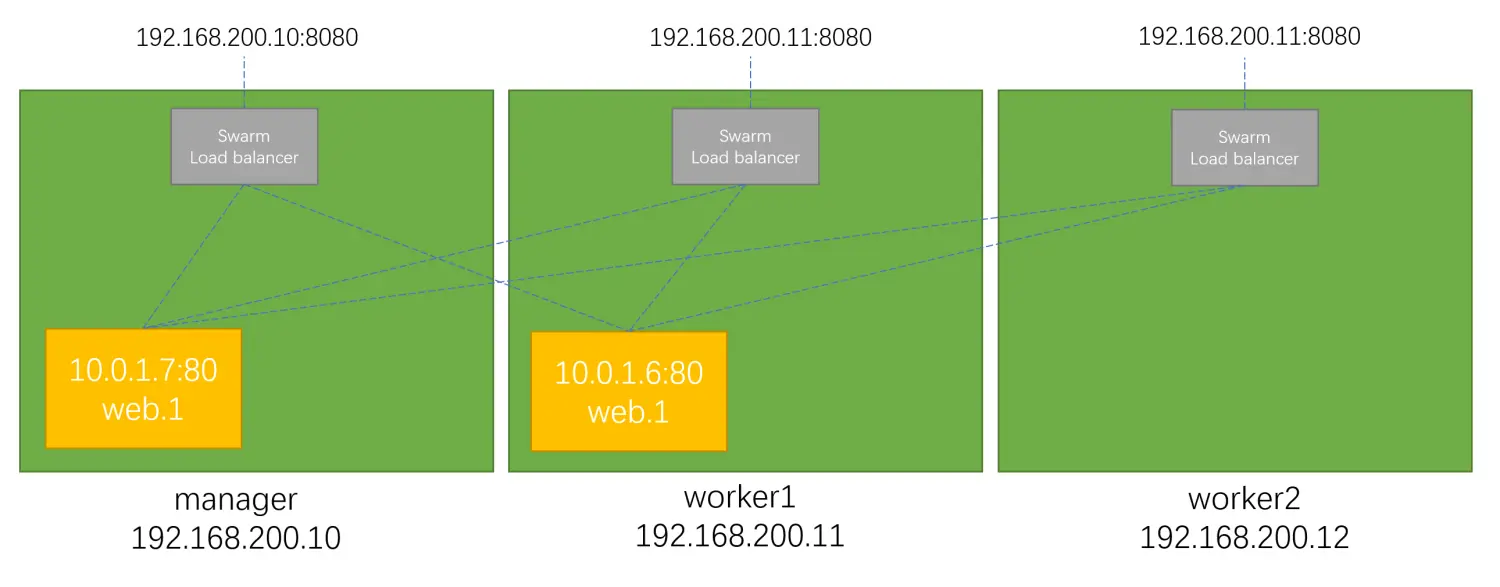
8080这个端口到底映射到哪里了?尝试三个swarm节点的IP加端口8080
可以看到三个节点IP都可以访问,并且回应的容器是不同的(hostname),也就是有负载均衡的效果vagrant@swarm-manager:~$ curl 192.168.200.10:8080Hostname: fdf7c1354507IP: 127.0.0.1IP: 10.0.0.7IP: 172.18.0.3IP: 10.0.1.14RemoteAddr: 10.0.0.2:36828GET / HTTP/1.1Host: 192.168.200.10:8080User-Agent: curl/7.68.0Accept: */*vagrant@swarm-manager:~$ curl 192.168.200.11:8080Hostname: fdf7c1354507IP: 127.0.0.1IP: 10.0.0.7IP: 172.18.0.3IP: 10.0.1.14RemoteAddr: 10.0.0.3:54212GET / HTTP/1.1Host: 192.168.200.11:8080User-Agent: curl/7.68.0Accept: */*vagrant@swarm-manager:~$ curl 192.168.200.12:8080Hostname: c83ee052787aIP: 127.0.0.1IP: 10.0.0.6IP: 172.18.0.3IP: 10.0.1.13RemoteAddr: 10.0.0.4:49820GET / HTTP/1.1Host: 192.168.200.12:8080User-Agent: curl/7.68.0Accept: */*
ingress 数据包的走向
以manager节点为例,数据到底是如何达到service的container的
vagrant@swarm-manager:~$ sudo iptables -nvL -t natChain PREROUTING (policy ACCEPT 388 packets, 35780 bytes)pkts bytes target prot opt in out source destination296 17960 DOCKER-INGRESS all -- * * 0.0.0.0/0 0.0.0.0/0 ADDRTYPE match dst-type LOCAL21365 1282K DOCKER all -- * * 0.0.0.0/0 0.0.0.0/0 ADDRTYPE match dst-type LOCALChain INPUT (policy ACCEPT 388 packets, 35780 bytes)pkts bytes target prot opt in out source destinationChain OUTPUT (policy ACCEPT 340 packets, 20930 bytes)pkts bytes target prot opt in out source destination8 590 DOCKER-INGRESS all -- * * 0.0.0.0/0 0.0.0.0/0 ADDRTYPE match dst-type LOCAL1 60 DOCKER all -- * * 0.0.0.0/0 !127.0.0.0/8 ADDRTYPE match dst-type LOCALChain POSTROUTING (policy ACCEPT 340 packets, 20930 bytes)pkts bytes target prot opt in out source destination2 120 MASQUERADE all -- * docker_gwbridge 0.0.0.0/0 0.0.0.0/0 ADDRTYPE match src-type LOCAL3 252 MASQUERADE all -- * !docker0 172.17.0.0/16 0.0.0.0/00 0 MASQUERADE all -- * !docker_gwbridge 172.18.0.0/16 0.0.0.0/0Chain DOCKER (2 references)pkts bytes target prot opt in out source destination0 0 RETURN all -- docker0 * 0.0.0.0/0 0.0.0.0/00 0 RETURN all -- docker_gwbridge * 0.0.0.0/0 0.0.0.0/0Chain DOCKER-INGRESS (2 references)pkts bytes target prot opt in out source destination2 120 DNAT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:8080 to:172.18.0.2:8080302 18430 RETURN all -- * * 0.0.0.0/0 0.0.0.0/0
通过iptables,可以看到一条DNAT的规则,所有访问本地8080端口的流量都被转发到 172.18.0.2:8080
那这个172.18.0.2 是什么?
首先 172.18.0.0/16 这个网段是docker_gwbridge的,所以这个地址肯定是连在了docker_gwbridge上。docker network inspect docker_gwbridge可以看到这个网络连接了一个叫ingress-sbox的容器。它的地址就是 172.18.0.2/16
这个ingress-sbox其实并不是一个容器,而是一个网络的命名空间 network namespace, 我们可以通过下面的方式进入到这个命名空间vagrant@swarm-manager:~$ docker run -it --rm -v /var/run/docker/netns:/netns --privileged=true nicolaka/netshoot nsenter --net=/netns/ingress_sbox sh~ # ip a1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00inet 127.0.0.1/8 scope host lovalid_lft forever preferred_lft forever8: eth0@if9: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1450 qdisc noqueue state UP group defaultlink/ether 02:42:0a:00:00:02 brd ff:ff:ff:ff:ff:ff link-netnsid 0inet 10.0.0.2/24 brd 10.0.0.255 scope global eth0valid_lft forever preferred_lft foreverinet 10.0.0.5/32 scope global eth0valid_lft forever preferred_lft forever10: eth1@if11: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group defaultlink/ether 02:42:ac:12:00:02 brd ff:ff:ff:ff:ff:ff link-netnsid 1inet 172.18.0.2/16 brd 172.18.255.255 scope global eth1valid_lft forever preferred_lft forever
通过查看地址,发现这个命名空间连接了两个网络,一个eth1是连接了
docker_gwbridge,另外一个eth0连接了ingress这个网络。~ # ip routedefault via 172.18.0.1 dev eth110.0.0.0/24 dev eth0 proto kernel scope link src 10.0.0.2172.18.0.0/16 dev eth1 proto kernel scope link src 172.18.0.2~ # iptables -nvL -t mangleChain PREROUTING (policy ACCEPT 22 packets, 2084 bytes)pkts bytes target prot opt in out source destination12 806 MARK tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:8080 MARK set 0x100Chain INPUT (policy ACCEPT 14 packets, 1038 bytes)pkts bytes target prot opt in out source destination0 0 MARK all -- * * 0.0.0.0/0 10.0.0.5 MARK set 0x100Chain FORWARD (policy ACCEPT 8 packets, 1046 bytes)pkts bytes target prot opt in out source destinationChain OUTPUT (policy ACCEPT 14 packets, 940 bytes)pkts bytes target prot opt in out source destinationChain POSTROUTING (policy ACCEPT 22 packets, 1986 bytes)pkts bytes target prot opt in out source destination~ # ipvsadmIP Virtual Server version 1.2.1 (size=4096)Prot LocalAddress:Port Scheduler Flags-> RemoteAddress:Port Forward Weight ActiveConn InActConnFWM 256 rr-> 10.0.0.6:0 Masq 1 0 0-> 10.0.0.7:0 Masq 1 0 0~ #
通过ipvs做了负载均衡
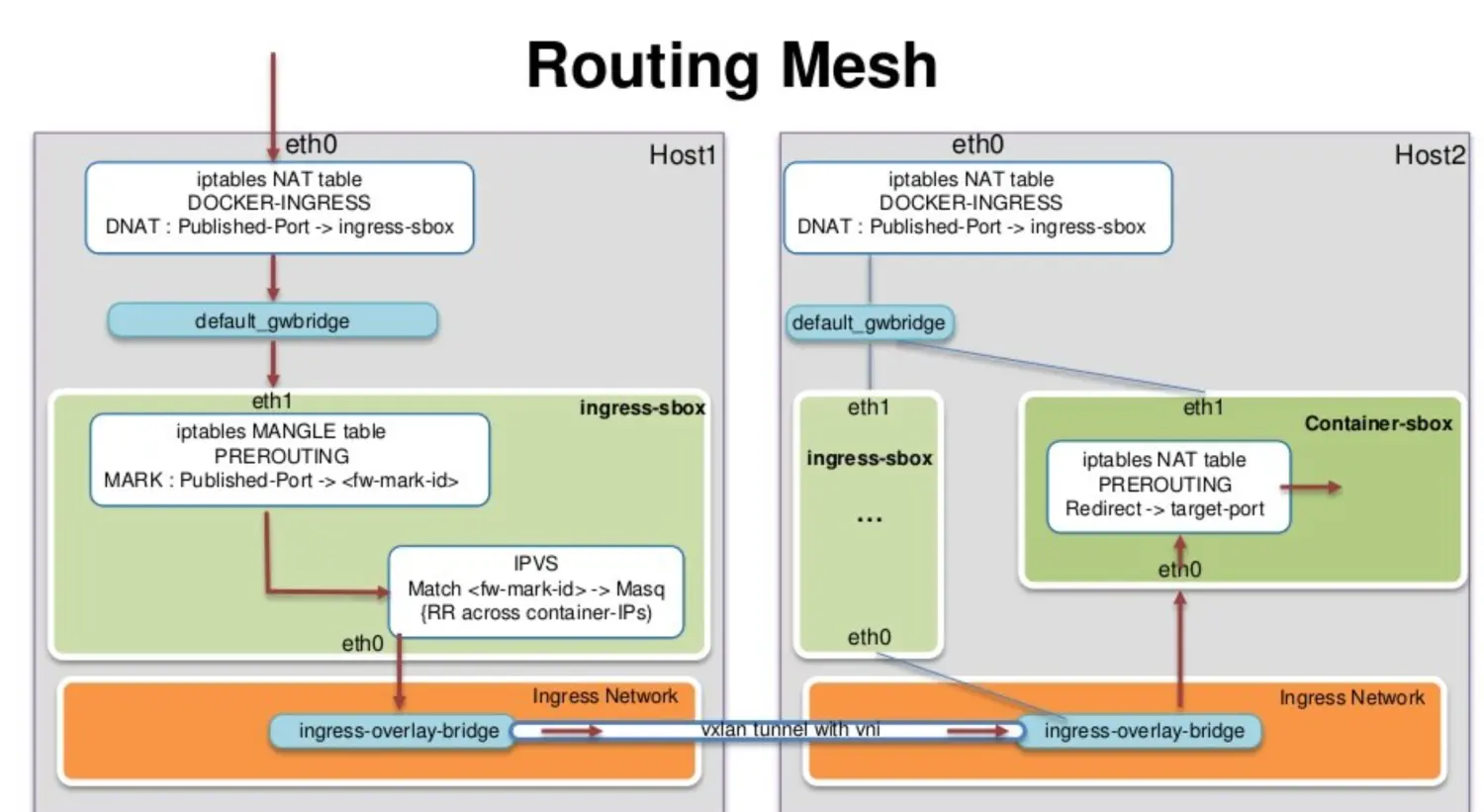
关于这里的负载均衡 这是一个stateless load balancing
- 这是三层的负载均衡,不是四层的 LB is at OSI Layer 3 (TCP), not Layer 4 (DNS)
- 以上两个限制可以通过Nginx或者HAProxy LB proxy解决 (https://docs.docker.com/engine/swarm/ingress/)