https://www.iana.org/assignments/service-names-port-numbers/service-names-port-numbers.xhtml
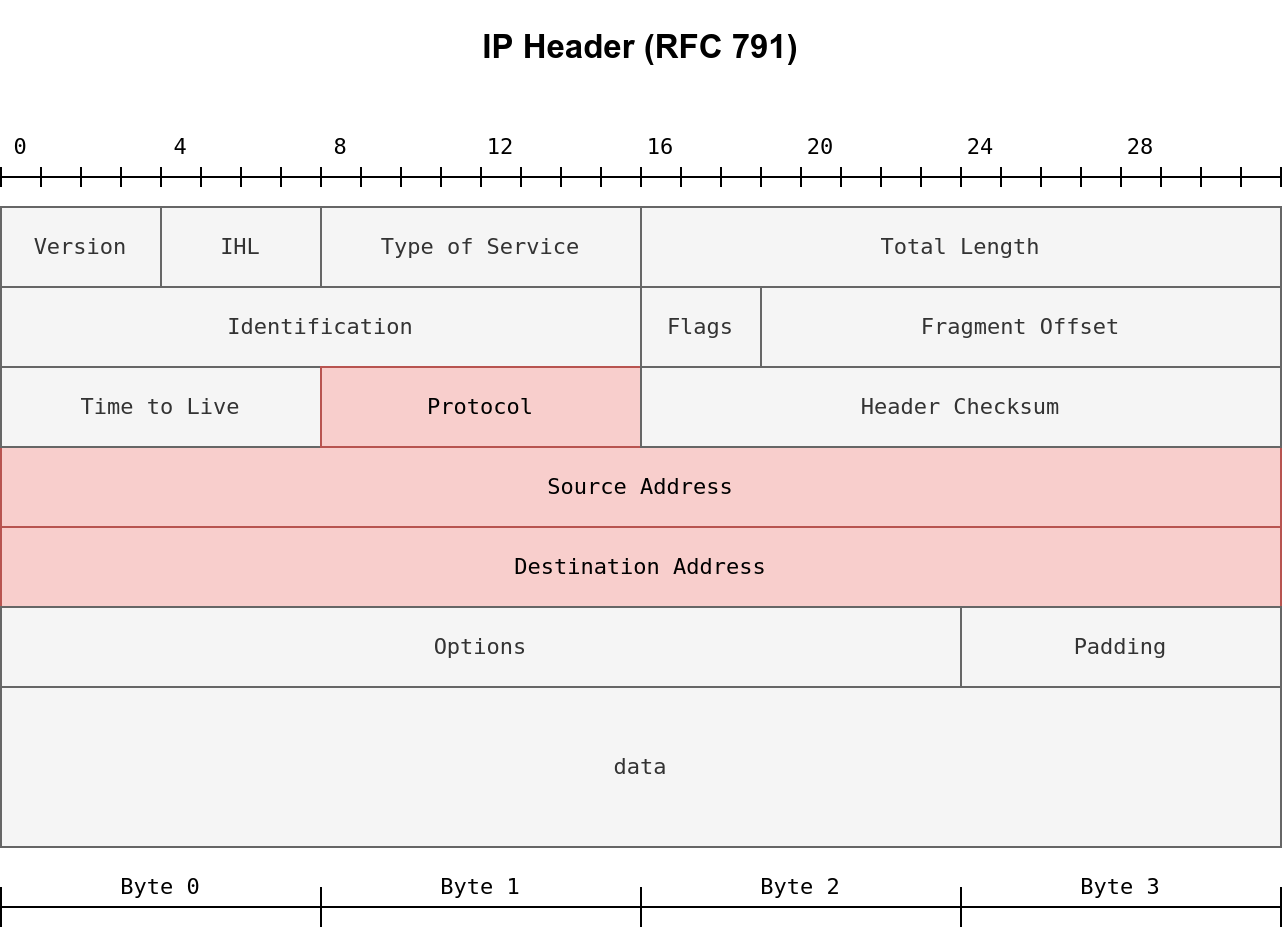
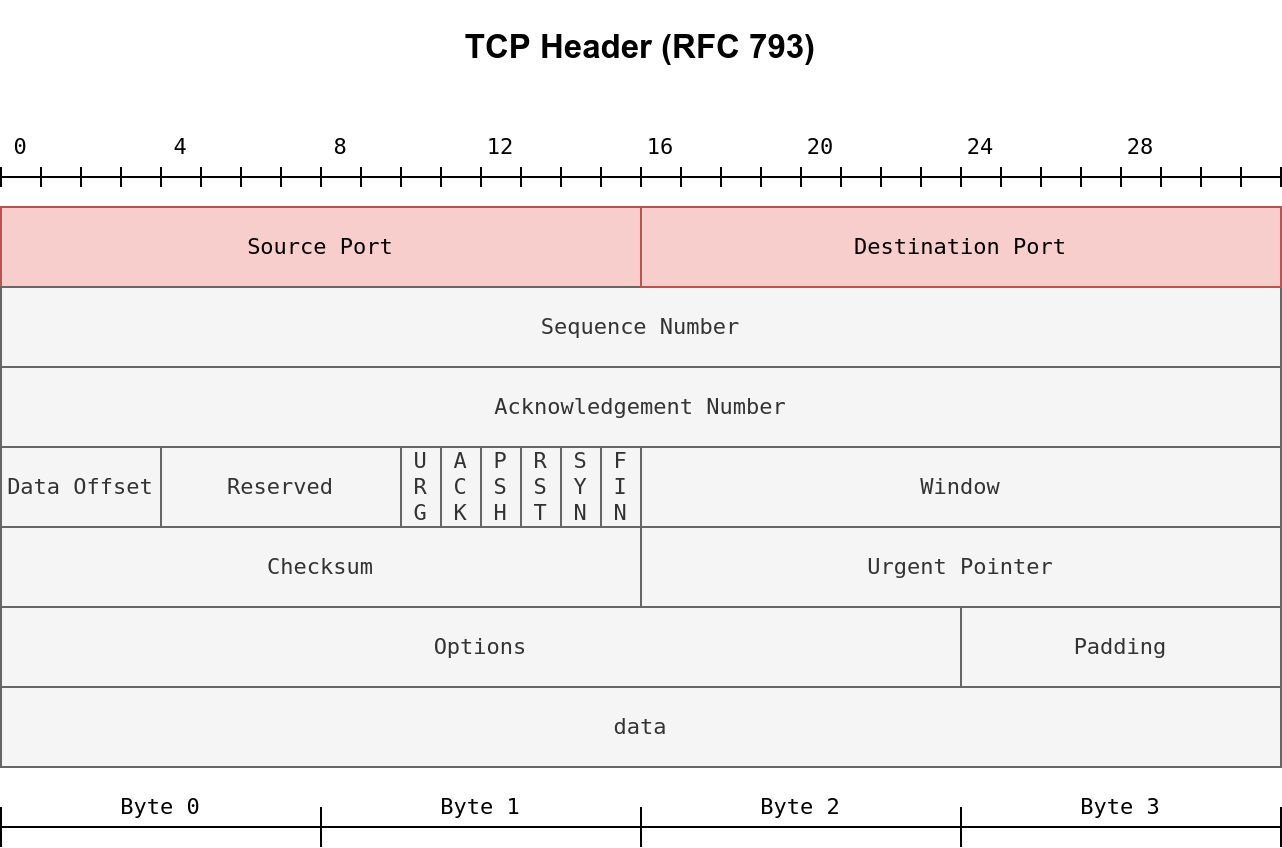
- Evasion via controlling the source MAC/IP/Port
- Evasion via fragmentation, MTU, and data length
- Evasion through modifying header fields
Nmap allows you to hide or spoof the source as you can use:
- Decoy(s)
- Proxy
- Spoofed MAC Address
- Spoofed Source IP Address
- Fixed Source Port Number

